156-915.77 Exam Questions - Online Test
156-915.77 Premium VCE File

150 Lectures, 20 Hours

It is impossible to pass CheckPoint 156-915.77 exam without any help in the short term. Come to Certleader soon and find the most advanced, correct and guaranteed CheckPoint 156-915.77 practice questions. You will get a surprising result by our Improve Check Point Certified Security Expert Update Blade practice guides.
Online CheckPoint 156-915.77 free dumps demo Below:
NEW QUESTION 1
What is the syntax for uninstalling a package using newpkg?
- A. -u <pathname of package>
- B. -i <full pathname of package>
- C. -S <pathname of package>
- D. newpkg CANNOT be used to uninstall a package
Answer: D
NEW QUESTION 2
Your company has the requirement that SmartEvent reports should show a detailed and accurate view of network activity but also performance should be guaranteed. Which actions should be taken to achieve that?
1) Use same hard drive for database directory, log files, and temporary directory.
2) Use Consolidation Rules.
3) Limit logging to blocked traffic only.
4) Use Multiple Database Tables.
- A. 2, 4
- B. 1, 3, 4
- C. 1, 2, 4
- D. 1, 2
Answer: A
NEW QUESTION 3
Which operating systems are supported by a Check Point Security Gateway on an open server? Select MOST complete list.
- A. Sun Solaris, Red Hat Enterprise Linux, Check Point SecurePlatform, IPSO, Microsoft Windows
- B. Check Point GAiA and SecurePlatform, and Microsoft Windows
- C. Check Point GAiA, Microsoft Windows, Red Hat Enterprise Linux, Sun Solaris, IPSO
- D. Check Point GAiA and SecurePlatform, IPSO, Sun Solaris, Microsoft Windows
Answer: B
NEW QUESTION 4
CORRECT TEXT
Fill in the blank. To remove site-to-site IKE and IPSEC keys you would enter command ____ and select the option to delete all IKE and IPSec SA’s.
Solution:
vpn tu
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 5
An internal host initiates a session to the Google.com website and is set for Hide NAT behind the Security Gateway. The initiating traffic is an example of .
- A. client side NAT
- B. source NAT
- C. destination NAT
- D. None of these
Answer: B
NEW QUESTION 6
In the Rule Base displayed, user authentication in Rule 4 is configured as fully automatic. Eric is a member of the LDAP group, MSD_Group.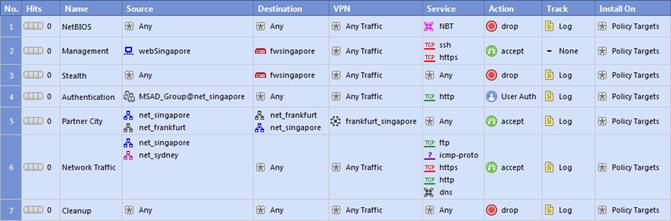
What happens when Eric tries to connect to a server on the Internet?
- A. None of these things will happen.
- B. Eric will be authenticated and get access to the requested server.
- C. Eric will be blocked because LDAP is not allowed in the Rule Base.
- D. Eric will be dropped by the Stealth Rule.
Answer: D
NEW QUESTION 7
Your R77 primary Security Management Server is installed on GAiA. You plan to schedule the Security Management Server to run fw logswitch automatically every 48 hours. How do you create this schedule?
- A. On a GAiA Security Management Server, this can only be accomplished by configuring the command fw logswitch via the cron utility.
- B. Create a time object, and add 48 hours as the interva
- C. Open the primary Security Management Server object’s Logs and Masters window, enable Schedule log switch, and select the Time object.
- D. Create a time object, and add 48 hours as the interva
- E. Open the Security Gateway object's Logs and Masters window, enable Schedule log switch, and select the Time object.
- F. Create a time object, and add 48 hours as the interva
- G. Select that time object’s Global Properties > Logs and Masters window, to schedule a logswitch.
Answer: B
NEW QUESTION 8
CORRECT TEXT
Fill in the blank with a numeric value. The default port number for standard TCP connections with the LDAP server is
Solution:
389
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 9
To qualify as an Identity Awareness enabled rule, which column MAY include an Access Role?
- A. Source
- B. Track
- C. User
- D. Action
Answer: A
NEW QUESTION 10
How do you configure the Security Policy to provide user access to the Captive Portal through an external (Internet) interface?
- A. Change the gateway settings to allow Captive Portal access via an external interface.
- B. No action is necessar
- C. This access is available by default.
- D. Change the Identity Awareness settings under Global Properties to allow Captive Portal access on all interfaces.
- E. Change the Identity Awareness settings under Global Properties to allow Captive Portal access for an external interface.
Answer: A
NEW QUESTION 11
Which of the following CLISH commands would you use to set the admin user's shell to bash?
- A. set user admin shell bash
- B. set user admin shell /bin/bash
- C. set user admin shell = /bin/bash
- D. set user admin /bin/bash
Answer: B
NEW QUESTION 12
CORRECT TEXT
To stop acceleration on a GAiA Security Gateway, enter command:
Solution:
fwaccel off
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 13
Which of the following commands can provide the most complete restoration of a R77 configuration?
- A. upgrade_import
- B. cpinfo -recover
- C. cpconfig
- D. fwm dbimport -p <export file>
Answer: A
NEW QUESTION 14
Which Check Point tool allows you to open a debug file and see the VPN packet exchange details.
- A. PacketDebug.exe
- B. VPNDebugger.exe
- C. IkeView.exe
- D. IPSECDebug.exe
Answer: C
NEW QUESTION 15
You are running a R77 Security Gateway on GAiA. In case of a hardware failure, you have a server with the exact same hardware and firewall version installed. What back up method could be used to quickly put the secondary firewall into production?
- A. manual backup
- B. upgrade_export
- C. backup
- D. snapshot
Answer: D
NEW QUESTION 16
......
100% Valid and Newest Version 156-915.77 Questions & Answers shared by Certshared, Get Full Dumps HERE: https://www.certshared.com/exam/156-915.77/ (New 203 Q&As)

