1z0-1085-20 Exam Questions - Online Test
1z0-1085-20 Premium VCE File

150 Lectures, 20 Hours

Proper study guides for Most up-to-date Oracle Oracle Cloud Infrastructure Foundations 2020 Associate certified begins with Oracle 1z0-1085-20 preparation products which designed to deliver the Actual 1z0-1085-20 questions by making you pass the 1z0-1085-20 test at your first time. Try the free 1z0-1085-20 demo right now.
Online 1z0-1085-20 free questions and answers of New Version:
NEW QUESTION 1
Which statement about the Oracle Cloud Infrastructure (OCI) shared-security model is true?
- A. You are responsible for securing all data that you place in OCI
- B. You are not responsible for any aspect of security in OCI
- C. You are responsible for securing the hypervisor within OCI compute service
- D. You are responsible for managing security controls within the physical OCI network
Answer: A
Explanation:
Oracle Cloud Infrastructure offers best-in-class security technology and operational processes to secure its enterprise cloud services. However, for you to securely run your workloads in Oracle Cloud Infrastructure, you must be aware of your security and compliance responsibilities. By design, Oracle provides security of cloud infrastructure and operations (cloud operator access controls, infrastructure security patching, and so on), and you are responsible for securely configuring your cloud resources. Security in the cloud is a shared responsibility between you and Oracle.
In a shared, multi-tenant compute environment, Oracle is responsible for the security of the underlying cloud infrastructure (such as data-center facilities, and hardware and software systems) and you are responsible for securing your workloads and configuring your services (such as compute, network, storage, and database) securely.
In a fully isolated, single-tenant, bare metal server with no Oracle software on it, your responsibility increases as you bring the entire software stack (operating systems and above) on which you deploy your applications. In this environment, you are responsible for securing your workloads, and configuring your services (compute, network, storage, database) securely, and ensuring that the software components that you run on the bare metal servers are configured, deployed, and managed securely.
The responsibilities can be divided as:
NEW QUESTION 2
A customer is looking to migrate their old database backups from their on-premises data center to Oracle Cloud Infrastructure (OCI). Which OCI service is the most cost-effective?
- A. Block Volume
- B. Archive Storage
- C. File Storage
- D. Object Storage (standard)
Answer: B
Explanation:
Archive storage is the most cost effective for archive data
NEW QUESTION 3
Which describes a key benefit of using Oracle Cloud Infrastructure (OCI)?
- A. With OCI, you can only run Java based workloads on bare metal.
- B. With OCI, you can run only cloud-native workloads.
- C. Only bare metal workloads are supported on OCI.
- D. OCI offers consistent performance with a predictable pricing model.
Answer: D
Explanation:
https://www.oracle.com/in/cloud/pricing.html
- OCI offers consistent performance with a predictable pricing model - is the best suited answer.
- Only bare metal workloads are supported in OCI - False, since you can work with VMs etc too
- With OCI, you can run cloud native workloads - False, since you can work with on-premise by connecting it to OCI too.
- With OCI, you can only run Java based workloads on bare metal - False since Java is not the only programming language supported by OCI.
NEW QUESTION 4
What does compute instance horizonal scaling mean?
- A. stopping/starting the instance
- B. backing up data to object storage
- C. adding additional compute instances
- D. changing compute instance size
Answer: C
Explanation:
Cloud Horizontal Scaling refers to provisioning additional servers to meet your needs, often splitting workloads between servers to limit the number of requests any individual server is getting. In a cloud-based environment, this would mean adding additional instances instead of moving to a larger instance size.
Cloud Vertical Scaling refers to adding more CPU or memory to an existing server, or replacing one server with a more powerful server.
NEW QUESTION 5
Which offers the lowest pricing for storage (per GB)?
- A. Oracle Cloud Infrastructure Object Storage (standard tier)
- B. Oracle Cloud Infrastructure Block Volume
- C. Oracle Cloud Infrastructure Archive Storage
- D. Oracle Cloud Infrastructure File Storage
Answer: C
Explanation:
Oracle Cloud Infrastructure Archive Storage is the lowest pricing for storage (per GB)
NEW QUESTION 6
Your company has deployed a business critical application in Oracle Cloud Infrastructure. What should you do to ensure that your application has the highest level of resilience and availability?
- A. Deploy the application across multiple Availability Domains and Subnets
- B. Deploy the application across multiple Virtual Cloud Networks
- C. Deploy the application across multiple Regions and Availability Domains
- D. Deploy the application across multiple Availability Domains and Fault Domains
Answer: C
Explanation:
To design a high availability architecture, three key elements should be considered— redundancy, monitoring, and failover:
1) Redundancy means that multiple components can perform the same task. The problem of a single point of failure is eliminated because redundant components can take over a task performed by a component that has failed.
2) Monitoring means checking whether or not a component is working properly.
3) Failover is the process by which a secondary component becomes primary when the primary component fails.
The best practices introduced here focus on these three key elements. Although high availability can be achieved at many different levels, including the application level and the cloud infrastructure level, here we will focus on the cloud infrastructure level.
An Oracle Cloud Infrastructure region is a localized geographic area composed of one or more availability domains, each composed of three fault domains. High availability is ensured by a redundancy of fault domains within the availability domains.
An availability domain is one or more data centers located within a region. Availability domains are isolated from each other, fault tolerant, and unlikely to fail simultaneously. Because availability domains do not share physical infrastructure, such as power or cooling, or the internal availability domain network, a failure that impacts one availability domain is unlikely to impact the availability of others.
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain contains three fault domains. Fault domains let you distribute your instances so that they are not on the same physical hardware within a single availability domain. As a result, an unexpected hardware failure or a Compute hardware maintenance that affects one fault domain does not affect instances in other fault domains. You can optionally specify the fault domain for a new instance at launch time, or you can let the system select one for you.
All the availability domains in a region are connected to each other by a low-latency, high bandwidth network. This predictable, encrypted interconnection between availability domains provides the building blocks for both high availability and disaster recovery.
NEW QUESTION 7
What does compute instance vertical scaling mean?
- A. Providing Fault tolerance
- B. Adding additional compute instances
- C. Enabling Disaster recovery
- D. Changing to a large or smaller shape
Answer: D
Explanation:
Changing the Shape of an Instance (Horizontal Scaling)
You can change the shape of a virtual machine (VM) instance without having to rebuild your instances or redeploy your applications. This lets you scale up your Compute resources for increased performance, or s down to reduce cost.
Autoscaling (vertical scaling)
Autoscaling lets you automatically adjust the number of Compute instances in an instance pool based on performance metrics such as CPU utilization. This helps you provide consistent performance for your end users during periods of high demand, and helps you reduce your costs during periods of low demand.
As load increases, instances are automatically provisioned: the instance pool scales out. As load decreases, instances are automatically removed: the instance pool scales in.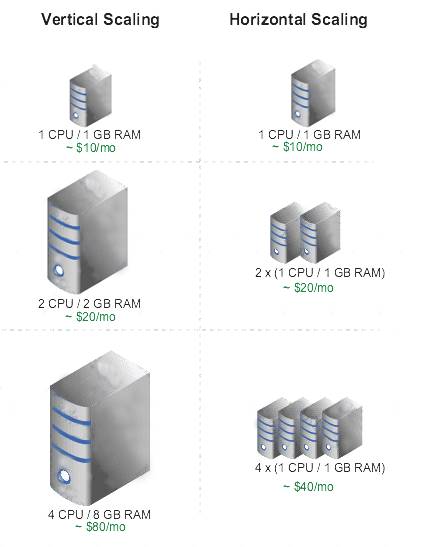
https://docs.cloud.oracle.com/en-us/iaas/Content/Compute/Tasks/resizinginstances.htm
NEW QUESTION 8
You have an application that requires a shared file system. Which of the following services would you use?
- A. File Storage
- B. Archive Storage
- C. Object Storage
- D. Block Volume
Answer: A
Explanation:
Oracle Cloud Infrastructure File Storage service provides a durable, scalable, secure, enterprise-grade network file system. You can connect to a File Storage service file system from any bare metal, virtual machine, or container instance in your Virtual Cloud Network (VCN). You can also access a file system from outside the VCN using Oracle Cloud Infrastructure FastConnect and Internet Protocol security (IPSec) virtual private network (VPN).
Large Compute clusters of thousands of instances can use the File Storage service for high-performance shar storage. Storage provisioning is fully managed and automatic as your use scales from a single byte to exabytes without upfront provisioning.
The File Storage service supports the Network File System version 3.0 (NFSv3) protocol. The service suppo the Network Lock Manager (NLM) protocol for file locking functionality.
Oracle Cloud Infrastructure File Storage employs 5-way replicated storage, located in different fault domain to provide redundancy for resilient data protection. Data is protected with erasure encoding.
The File Storage service uses the "eventual overwrite" method of data eradication. Files are created in the fil system with a unique encryption key. When you delete a single file, its associated encryption key is eradicated, making the file inaccessible. When you delete an entire file system, the file system is marked as inaccessible. The service systematically traverses deleted files and file systems, frees all the used space, and eradicates all residual files.
Use the File Storage service when your application or workload includes big data and analytics, media processing, or content management, and you require Portable Operating System Interface (POSIX)-compliant file system access semantics and concurrently accessible storage. The File Storage service is designed to meet the needs of applications and users that need an enterprise file system across a wide range of use cases, including the following:
NEW QUESTION 9
A customer wants to use Oracle Cloud Infrastructure (OCI) for storing application backups which can be stored based on business needs.
Which OCI storage service can be used to meet the requirement?
- A. File Storage
- B. Block Volume
- C. Archive Storage
- D. Object Storage (standard)
Answer: D
Explanation:
Oracle Cloud Infrastructure offers two distinct storage class tiers to address the need for both performant, frequently accessed "hot" storage, and less frequently accessed "cold" storage. Storage tiers help you maximize performance where appropriate and minimize costs where possible.
1) Use Object Storage for data to which you need fast, immediate, and frequent access. Data accessibility an performance justifies a higher price to store data in the Object Storage tier.
2) Use Archive Storage for data to which you seldom or rarely access, but that must be retained and preserve for long periods of time. The cost efficiency of the Archive Storage tier offsets the long lead time required to access the data. For more information, see Overview of Archive Storage.
The Oracle Cloud Infrastructure Object Storage service is an internet-scale, high-performance storage platform that offers reliable and cost-efficient data durability. The Object Storage service can store an unlimited amount
of unstructured data of any content type, including analytic data and rich content, like images and videos.
With Object Storage, you can safely and securely store or retrieve data directly from the internet or from within the cloud platform. Object Storage offers multiple management interfaces that let you easily manage storage at scale. The elasticity of the platform lets you start small and scale seamlessly, without experiencing any degradation in performance or service reliability.
Object Storage is a regional service and is not tied to any specific compute instance. You can access data from anywhere inside or outside the context of the Oracle Cloud Infrastructure, as long you have internet connectivity and can access one of the Object Storage endpoints. Authorization and resource limits are discussed later in this topic.
Object Storage also supports private access from Oracle Cloud Infrastructure resources in a VCN through
a service gateway. A service gateway allows connectivity to the Object Storage public endpoints from private IP addresses in private subnets. For example, you can back up DB systems to an Object Storage bucket over the Oracle Cloud Infrastructure backbone instead of over the internet. You can optionally use IAM policies to control which VCNs or ranges of IP addresses can access Object Storage. See Access to Oracle Services: Service Gateway for details.
Object Storage is Always Free eligible. For more information about Always Free resources, including additional capabilities and limitations, see Oracle Cloud Infrastructure Free Tier.
The following list summarizes some of the ways that you can use Object Storage.
NEW QUESTION 10
A new customer has logged into Oracle Cloud Infrastructure (OCI) as an administrator for the first time. The admin would like to deploy infrastructure. What is the first step they must take in order to accomplish this task?
- A. File a service request for access to each additional region.
- B. Use API endpoints to create resources in the desired region.
- C. Subscribe to the desired region.
- D. Navigate to the desired region and begin creating resources.
Answer: C
Explanation:
When you sign up for Oracle Cloud Infrastructure, Oracle creates a tenancy for you in one region. This is
your home region. Your home region is where your IAM resources are defined. When you subscribe to another region, your IAM resources are available in the new region, however, the master definitions reside in your home region and can only be changed there.
When you subscribe your tenancy to a new region, all the policies from your home region are enforced in the new region. If you want to limit access for groups of users to specific regions, you can write policies to grant access to specific regions only.
NEW QUESTION 11
Which Oracle Cloud Infrastructure service can you use to assess user security of your Oracle databases?
- A. Oracle Data Safe
- B. Oracle Data Guard
- C. Audit Vault and Database Firewall option for Oracle Database Enterprise Edition
- D. Audit Service
Answer: A
Explanation:
Oracle Data Safe is a unified control center for your Oracle databases which helps you understand the sensitivity of your data, evaluate risks to data, mask sensitive data, implement and monitor security controls, assess user security, monitor user activity, and address data security compliance requirements.
Whether you’re using an Autonomous Database or an Oracle DB system, Oracle Data Safe delivers essential
data security capabilities as a service on Oracle Cloud Infrastructure.
NEW QUESTION 12
Which Oracle Cloud Infrastructure (OCI) service can be used to protect sensitive and regulated data in OCI database services?
- A. Oracle Data Guard
- B. OCI Audit
- C. Oracle Data Safe
- D. OCI OS management
Answer: C
Explanation:
Oracle Data Safe is a unified control center for your Oracle databases which helps you understand the sensitivity of your data, evaluate risks to data, mask sensitive data, implement and monitor security controls, assess user security, monitor user activity, and address data security compliance requirements.
Whether you’re using an Autonomous Database or an Oracle DB system, Oracle Data Safe delivers essential data security capabilities as a service on Oracle Cloud Infrastructure.
Features of Oracle Data Safe:
Oracle Data Safe provides the following set of features for protecting sensitive and regulated data in Oracle Cloud databases, all in a single, easy-to-use management console:
1) Security Assessment helps you assess the security of your cloud database configurations. It analyzes database configurations, user accounts, and security controls, and then reports the findings with recommendations for remediation activities that follow best practices to reduce or mitigate risk.
2) User Assessment helps you assess the security of your database users and identify high risk users. It reviews information about your users in the data dictionary on your target databases, and calculates a risk score for
each user. For example, it evaluates the user types, how users are authenticated, the password policies assigned to each user, and how long it has been since each user has changed their password. It also provides a direct link to audit records related to each user. With this information, you can then deploy appropriate security controls and policies.
3) Data Discovery helps you find sensitive data in your cloud databases. You tell Data Discovery what kind of sensitive data to search for, and it inspects the actual data in your database and its data dictionary, and then returns to you a list of sensitive columns. By default, Data Discovery can search for a wide variety of sensitive data pertaining to identification, biographic, IT, financial, healthcare, employment, and academic information.
4) Data Masking provides a way for you to mask sensitive data so that the data is safe for non-production purposes. For example, organizations often need to create copies of their production data to support development and test activities. Simply copying the production data exposes sensitive data to new users. To avoid a security risk, you can use Data Masking to replace the sensitive data with realistic, but fictitious data.
5) Activity Auditing lets you audit user activity on your databases so you can monitor database usage and be alerted of unusual database activities.
NEW QUESTION 13
You want to leverage a managed Real Application Cluster (RAC) offering in Oracle Cloud Infrastructure. which OCI Managed database service would you choose?
- A. Autonomous Transaction Processing (shared)
- B. VM DB System
- C. Autonomous Data Warehousing (shared)
- D. Bare Metal DB Systems
Answer: B
Explanation:
There are 2 types of DB systems on virtual machines: A 1-node VM DB system consists of one VM.
A 2-node VM DB system consists of two VMs clustered with RAC enabled.
NEW QUESTION 14
Which Oracle Cloud Infrastructure (OCI) database solution will be most economical for a customer looking to have the elasticity of the cloud with minimal administration and maintenance effort for their DBA team?
- A. OCI Bare Metal DB Systems
- B. OCI Virtual Machine DB Systems
- C. OCI Exadata DB Systems.
- D. OCI Autonomous Database
Answer: C
Explanation:
Exadata DB systems allow you to leverage the power of Exadata within the Oracle Cloud Infrastructure. An Exadata DB system consists of a base system, quarter rack, half rack, or full rack of compute nodes and storage servers, tied together by a high-speed, low-latency InfiniBand network and intelligent Exadata software. You can configure automatic backups, optimize for different workloads, and scale up the system to meet increased demands.
Oracle now offers the Zero Downtime Migration service, a quick and easy way to move on-premises Oracle Databases and Oracle Cloud Infrastructure Classic databases to Oracle Cloud Infrastructure. You can migrate databases to the following types of Oracle Cloud Infrastructure systems: Exadata, Exadata Cloud@Customer, bare metal, and virtual machine.
Zero Downtime Migration leverages Oracle Active Data Guard to create a standby instance of your database in an Oracle Cloud Infrastructure system. You switch over only when you are ready, and your source database remains available as a standby. Use the Zero Downtime Migration service to migrate databases individually or
at the fleet level. See Move to Oracle Cloud Using Zero Downtime Migration for more information.
NEW QUESTION 15
Which is NOT considered a security resource within Oracle Cloud Infrastructure?
- A. Network Security Group
- B. Web Application Firewall
- C. File Storage Service
- D. Security Lists
Answer: C
Explanation:
Oracle Cloud Infrastructure File Storage service provides a durable, scalable, secure, enterprise-grade netwo file system. You can connect to a File Storage service file system from any bare metal, virtual machine, or container instance in your Virtual Cloud Network (VCN).
You can control the access of the file system from FSS by applying some security rules and others but the services it self not related to security but it related to shared storage
NEW QUESTION 16
A banking platform has been re-designed to a microservices based architecture using Docker containers for deployment.
Which service can you use to deploy containers on Oracle Cloud Infrastructure (OCI)?
- A. Container Engine for Kubernetes (OKE)
- B. Streaming Service
- C. API Gateway
- D. File Storage Service
Answer: A
Explanation:
Oracle Cloud Infrastructure Container Engine for Kubernetes is a fully-managed, scalable, and highly available service that you can use to deploy your containerized applications to the cloud. Use Container Engine for Kubernetes (sometimes abbreviated to just OKE) when your development team wants to reliably build, deploy, and manage cloud-native applications. You specify the compute resources that your applications require, and Container Engine for Kubernetes provisions them on Oracle Cloud Infrastructure in an existing OCI tenancy.
Container Engine for Kubernetes uses Kubernetes - the open-source system for automating deployment, scaling, and management of containerized applications across clusters of hosts. Kubernetes groups the containers that make up an application into logical units (called pods) for easy management and discovery.
You can access Container Engine for Kubernetes to define and create Kubernetes clusters using the Console and the REST API. You can access the clusters you create using the Kubernetes command line (kubectl), the Kubernetes Dashboard, and the Kubernetes API.
Container Engine for Kubernetes is integrated with Oracle Cloud Infrastructure Identity and Access Management (IAM), which provides easy authentication with native Oracle Cloud Infrastructure identity
functionality.
NEW QUESTION 17
Which Oracle Cloud Infrastructure (OCI) service can send you an alert when you might exceed your spending threshold?
- A. Budgets
- B. Monitoring
- C. Streaming
- D. Events
Answer: A
Explanation:
Budgets can be used to set thresholds for your Oracle Cloud Infrastructure spending. You can set alerts on your budget to let you know when you might exceed your budget, and you can view all of your budgets and spending from one single place in the Oracle Cloud Infrastructure console.
NEW QUESTION 18
You run 5 Oracle Cloud Infrastructure (OCI) Virtual Machine instances on an OCI dedicated virtual host. Ho will this deployment be billed?
- A. Only the dedicated virtual machine host will be billed
- B. The dedicated virtual machine host and the boot volumes of each instance will be billed
- C. The dedicated virtual machine host all 5 instances, and the boot volume of each instance will be billed
- D. All 5 instances will be billed on the basis of the number of OCPUs
Answer: B
Explanation:
You must create a dedicated virtual machine host before you can place any instances on it. When creating th dedicated virtual machine host, you select an availability domain and fault domain to launch it in. All the VM instances that you place on the host will subsequently be created in this availability domain and fault domain. You also select a compartment when you create the dedicated virtual machine host, but you can move the host to a new compartment later without impacting any of the instances placed on it. You can also create the instances in a different compartment than the dedicated virtual machine host, or move them to difference compartments after they have been launched.
You are billed for the dedicated virtual machine host as soon as you create it, but you are not billed for any of the individual VM instances you place on it. You will still be billed for image licensing costs if they apply to the image you are using for the VM instances.
Read more: https://docs.cloud.oracle.com/en-us/iaas/Content/Compute/Concepts/dedicatedvmhosts.htm
NEW QUESTION 19
Which CANNOT be used with My Oracle Support (MOS)?
- A. Add or change a tenancy administrator
- B. Request a Service Limit increase
- C. Reset the password or unlock the account for the tenancy administrator
- D. Troubleshoot your resources in an Oracle Cloud Infrastructure Free Trial account
Answer: D
Explanation:
Open a support service request with MOS option is available to paid accounts. Customers using only Always Free resources are not eligible for Oracle Support. Limited support is available to Free Tier accounts with Free Trial credits. After you use all of your credits or after your trial period ends (whichever comes first), you must upgrade to a paid account to access Oracle Support. If you choose not to upgrade and continue to use Always Free Services, you will not be eligible to raise a service request in My Oracle Support.
In addition to support for technical issues, use My Oracle Support if you need to:
· Reset the password or unlock the account for the tenancy administrator
· Add or change a tenancy administrator
· Request a service limit increase
NEW QUESTION 20
You want to migrate mission-critical Oracle E- Business Suite application to Oracle Cloud Infrastructure (OCI) with full control and access to the underlying infrastructure.
Which option meets this requirement?
- A. Replace E-Business Suite with an Oracle SaaS application
- B. OCI Exadata DB Systems and OCI compute instances
- C. OCI Exadata DB Systems and Oracle Functions
- D. Oracle Exadata Cloud at customer, Storage Gateway and API Gateway
Answer: B
NEW QUESTION 21
Which statement about Oracle Cloud Infrastructure (OCI) shared security model is true?
- A. You are responsible for managing security controls within the physical OCI network.
- B. You are not responsible for any aspect of security in OCI.
- C. You are responsible for securing all data that you place in OCI
- D. You are responsible for securing the hypervisor within OCI Compute service.
Answer: C
Explanation:
Oracle Cloud Infrastructure offers best-in-class security technology and operational processes to secure its enterprise cloud services. However, for you to securely run your workloads in Oracle Cloud Infrastructure, you must be aware of your security and compliance responsibilities. By design, Oracle provides security of cloud infrastructure and operations (cloud operator access controls, infrastructure security patching, and so on), and you are responsible for securely configuring your cloud resources. Security in the cloud is a shared responsibility between you and Oracle.
In a shared, multi-tenant compute environment, Oracle is responsible for the security of the underlying cloud infrastructure (such as data-center facilities, and hardware and software systems) and you are responsible for securing your workloads and configuring your services (such as compute, network, storage, and database) securely.
In a fully isolated, single-tenant, bare metal server with no Oracle software on it, your responsibility increases as you bring the entire software stack (operating systems and above) on which you deploy your applications. In this environment, you are responsible for securing your workloads, and configuring your services (compute, network, storage, database) securely, and ensuring that the software components that you run on the bare metal servers are configured, deployed, and managed securely.
More specifically, your and Oracle's responsibilities can be divided into the following areas:
Identity and Access Management (IAM): As with all Oracle cloud services, you should protect your cloud access credentials and set up individual user accounts. You are responsible for managing and reviewing access for your own employee accounts and for all activities that occur under your tenancy. Oracle is responsible for providing effective IAM services such as identity management, authentication, authorization, and auditing.
Workload Security: You are responsible for protecting and securing the operating system and application layers of your compute instances from attacks and compromises. This protection includes patching applications and operating systems, operating system configuration, and protection against malware and network attacks. Oracle is responsible for providing secure images that are hardened and have the latest patches. Also, Oracle makes it simple for you to bring the same third-party security solutions that you use today.
Data Classification and Compliance: You are responsible for correctly classifying and labeling your data and meeting any compliance obligations. Also, you are responsible for auditing your solutions to ensure that they meet your compliance obligations.
Host Infrastructure Security: You are responsible for securely configuring and managing your compute (virtua hosts, containers), storage (object, local storage, block volumes), and platform (database configuration) services. Oracle has a shared responsibility with you to ensure that the service is optimally configured and secured. This responsibility includes hypervisor security and the configuration of the permissions and network access controls required to ensure that hosts can communicate correctly and that devices are able to attach or mount the correct storage devices.
Network Security: You are responsible for securely configuring network elements such as virtual networking, load balancing, DNS, and gateways. Oracle is responsible for providing a secure network infrastructure.
Client and Endpoint Protection: Your enterprise uses various hardware and software systems, such as mobile devices and browsers, to access your cloud resources. You are responsible for securing all clients and endpoints that you allow to access Oracle Cloud Infrastructure services.
Physical Security: Oracle is responsible for protecting the global infrastructure that runs all of the services offered in Oracle Cloud Infrastructure. This infrastructure consists of the hardware, software, networking, and facilities that run Oracle Cloud Infrastructure services.
NEW QUESTION 22
Which capability enables you to search, purchase, and start using software in your Oracle Cloud Infrastructure (OCI) tenancy?
- A. OCI Marketplace
- B. OCI OS Management
- C. OCI Resource Manager
- D. OCI Registry
Answer: A
Explanation:
Oracle Cloud Infrastructure Marketplace is an online store that offers solutions specifically for customers of Oracle Cloud Infrastructure. In the Oracle Cloud Infrastructure Marketplace catalog, you can find listings for two types of solutions from Oracle and trusted partners: images and stacks. These listing types include different categories of applications. Also, some listings are free and others require payment.
Images are templates of virtual hard drives that determine the operating system and software to run on an instance. You can deploy image listings on an Oracle Cloud Infrastructure Compute instance. Marketplace also offers stack listings. Stacks represent definitions of groups of Oracle Cloud Infrastructure resources that you can act on as a group. Each stack has a configuration consisting of one or more declarative configuration files. With an image or a stack, you have a customized, more streamlined way of getting started with a publisher's software.
NEW QUESTION 23
Which service level agreement type is NOT offered by Oracle Cloud Infrastructure Compute service?
- A. Data Plane
- B. Performance
- C. Application Plane
- D. Control Plane
Answer: C
Explanation:
Oracle offers several different service level agreements as defined in this section (Service Level Agreements).Service level agreements range from least restrictive (data plane) to more restrictive (control plane) to most restrictive (performance).
NEW QUESTION 24
What two statements regarding the Virtual Cloud Network (VCN) are true?
- A. A single VCN can contain both private and public Subnets.
- B. VCN is a regional resource that span across all the Availability Domains in a Region.
- C. You can only create one VCN per region.
- D. The VCN is the IPSec-based connection with a remote on premises location.
- E. VCN is a global resource that span across all the Regions
Answer: AB
Explanation:
When you work with Oracle Cloud Infrastructure, one of the first steps is to set up a virtual cloud network (VCN) for your cloud resources.
VIRTUAL CLOUD NETWORK (VCN) :
A virtual, private network that you set up in Oracle data centers. It closely resembles a traditional network, with firewall rules and specific types of communication gateways that you can choose to use. A VCN resides in a single Oracle Cloud Infrastructure region and covers a single, contiguous IPv4 CIDR block of your choice. See Allowed VCN Size and Address Ranges. The terms virtual cloud network, VCN, and cloud network are used interchangeably in this documentation. For more information, see VCNs and Subnets.
SUBNETS :
Subdivisions you define in a VCN (for example, 10.0.0.0/24 and 10.0.1.0/24). Subnets contain virtual network interface cards (VNICs), which attach to instances. Each subnet consists of a contiguous range of IP addresses that do not overlap with other subnets in the VCN. You can designate a subnet to exist either in a single availability domainavailability domain
or across an entire region (regional subnets are recommended). Subnets act as a unit of configuration within the VCN: All VNICs in a given subnet use the same route table, security lists, and DHCP options (see the definitions that follow). You can designate a subnet as either public or private when you create it. Private means VNICs in the subnet can't have public IP addresses. Public means VNICs in the subnet can have public IP addresses at your discretion. See Access to the Internet.
NEW QUESTION 25
......
Recommend!! Get the Full 1z0-1085-20 dumps in VCE and PDF From Downloadfreepdf.net, Welcome to Download: https://www.downloadfreepdf.net/1z0-1085-20-pdf-download.html (New 83 Q&As Version)
- [2021-New] Oracle 1z0-060 Dumps With Update Exam Questions (51-60)
- [2021-New] Oracle 1z0-047 Dumps With Update Exam Questions (71-80)
- [2021-New] Oracle 1Z0-591 Dumps With Update Exam Questions (1-10)
- Precise 1Z0-435 Braindumps 2021
- [2021-New] Oracle 1Z0-144 Dumps With Update Exam Questions (11-20)
- [2021-New] Oracle 1z0-060 Dumps With Update Exam Questions (61-70)
- [2021-New] Oracle 1Z0-532 Dumps With Update Exam Questions (1-10)
- How Many Questions Of 1Z0-632 Exams
- [2021-New] Oracle 1Z0-051 Dumps With Update Exam Questions (91-100)
- Oracle 1z0-888 Free Practice Questions 2021

