250-438 Exam Questions - Online Test
250-438 Premium VCE File

150 Lectures, 20 Hours

Examcollection 250-438 Questions are updated and all 250-438 answers are verified by experts. Once you have completely prepared with our 250-438 exam prep kits you will be ready for the real 250-438 exam without a problem. We have Improve Symantec 250-438 dumps study guide. PASSED 250-438 First attempt! Here What I Did.
Online Symantec 250-438 free dumps demo Below:
NEW QUESTION 1
DRAG DROP
What is the correct installation sequence for the components shown here, according to the Symantec Installation Guide? Place the options in the correct installation sequence.
Select and Place:
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 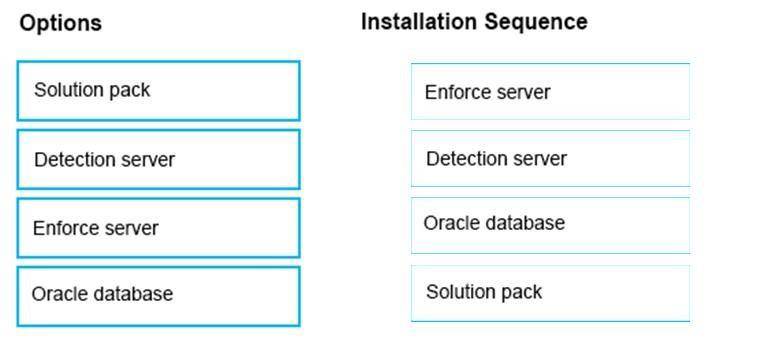
NEW QUESTION 2
What is the default fallback option for the Endpoint Prevent Encrypt response rule?
- A. Block
- B. User Cancel
- C. Encrypt
- D. Notify
Answer: D
NEW QUESTION 3
A compliance officer needs to understand how the company is complying with its data security policies over time. Which report should be compliance officer generate to obtain the compliance information?
- A. Policy report, filtered on date and summarized by policy
- B. Policy Trend report, summarized by policy, then quarter
- C. Policy report, filtered on quarter and summarized by policy
- D. Policy Trend report, summarized by policy, then severity
Answer: A
NEW QUESTION 4
Where should an administrator set the debug levels for an Endpoint Agent?
- A. Setting the log level within the Agent List
- B. Advanced configuration within the Agent settings
- C. Setting the log level within the Agent Overview
- D. Advanced server settings within the Endpoint server
Answer: C
Explanation:
Reference: https://support.symantec.com/en_US/article.TECH248581.html
NEW QUESTION 5
Which action should a DLP administrator take to secure communications between an on-premises Enforce server and detection servers hosted in the Cloud?
- A. Use the built-in Symantec DLP certificate for the Enforce Server, and use the “sslkeytool” utility to create certificates for the detection servers.
- B. Use the built-in Symantec DLP certificate for both the Enforce server and the hosted detection servers.
- C. Set up a Virtual Private Network (VPN) for the Enforce server and the hosted detection servers.
- D. Use the “sslkeytool” utility to create certificates for the Enforce server and the hosted detection servers.
Answer: A
Explanation:
Reference: https://www.symantec.com/connect/articles/sslkeytool-utility-and-server-certificates
NEW QUESTION 6
Which statement accurately describes where Optical Character Recognition (OCR) components must be installed?
- A. The OCR engine must be installed on detection server other than the Enforce server.
- B. The OCR server software must be installed on one or more dedicated (non-detection) Linux servers.
- C. The OCR engine must be directly on the Enforce server.
- D. The OCR server software must be installed on one or more dedicated (non-detection) Windows servers.
Answer: C
Explanation:
Reference: https://help.symantec.com/cs/dlp15.0/DLP/v122760174_v120691346/Setting-up-OCR-Servers?locale=EN_US
NEW QUESTION 7
A DLP administrator is preparing to install Symantec DLP and has been asked to use an Oracle database provided by the Database Administration team. Which SQL *Plus command should the administrator utilize to determine if the database is using a supported version of Oracle?
- A. select database version from <database name>;
- B. select * from db$version;
- C. select * from v$version;
- D. select db$ver from <database name>;
Answer: C
Explanation:
Reference: https://www.symantec.com/connect/forums/new-install-oracle-returns-error
NEW QUESTION 8
Which two technologies should an organization utilize for integration with the Network Prevent products? (choose two.)
- A. Network Tap
- B. Network Firewall
- C. Proxy Server
- D. Mail Transfer Agent
- E. Encryption Appliance
Answer: CD
Explanation:
Reference: https://www.symantec.com/connect/articles/network-prevent
NEW QUESTION 9
What detection technology supports partial contents matching?
- A. Indexed Document Matching (IDM)
- B. Described Content Matching (DCM)
- C. Exact Data Matching (EDM)
- D. Optical Character Recognition (OCR)
Answer: A
Explanation:
Reference: https://help.symantec.com/cs/dlp15.1/DLP/v115965297_v125428396/Mac-agent-detection-technologies?locale=EN_US
NEW QUESTION 10
Under the “System Overview” in the Enforce management console, the status of a Network Monitor detection server is shown as “Running Selected.” The Network Monitor server’s event logs indicate that the packet capture and filereader processes are crashing.
What is a possible cause for the Network Monitor server being in this state?
- A. There is insufficient disk space on the Network Monitor server.
- B. The Network Monitor server’s certificate is corrupt or missing.
- C. The Network Monitor server’s license file has expired.
- D. The Enforce and Network Monitor servers are running different versions of DLP.
Answer: D
NEW QUESTION 11
A divisional executive requests a report of all incidents generated by a particular region, summarized by department. What does the DLP administrator need to configure to generate this report?
- A. Custom attributes
- B. Status attributes
- C. Sender attributes
- D. User attributes
Answer: A
NEW QUESTION 12
Which two locations can Symantec DLP scan and perform Information Centric Encryption (ICE) actions on? (Choose two.)
- A. Exchange
- B. Jiveon
- C. File store
- D. SharePoint
- E. Confluence
Answer: CD
Explanation:
Reference: https://www.symantec.com/content/dam/symantec/docs/data-sheets/information-centric-encryption-en.pdf
NEW QUESTION 13
Which two Network Discover/Cloud Storage targets apply Information Centric Encryption as policy response rules?
- A. Microsoft Exchange
- B. Windows File System
- C. SQL Databases
- D. Microsoft SharePoint
- E. Network File System (NFS)
Answer: AD
NEW QUESTION 14
Which two components can perform a file system scan of a workstation? (Choose two.)
- A. Endpoint Server
- B. DLP Agent
- C. Network Prevent for Web Server
- D. Discover Server
- E. Enforce Server
Answer: BD
NEW QUESTION 15
Which detection server is available from Symantec as a hardware appliance?
- A. Network Prevent for Email
- B. Network Discover
- C. Network Monitor
- D. Network Prevent for Web
Answer: D
Explanation:
Reference: https://help.symantec.com/cs/dlp15.0/DLP/v122938258_v120691346/Setting-up-the-DLP-S500-Appliance?locale=EN_US
NEW QUESTION 16
A DLP administrator determines that the SymantecDLPProtectIncidents folder on the Enforce server contains. BAD files dated today, while other. IDC files are flowing in and out of the Incidents directory. Only .IDC files larger than 1MB are turning to .BAD files.
What could be causing only incident data smaller than 1MB to persist while incidents larger than 1MB change to .BAD files?
- A. A corrupted policy was deployed.
- B. The Enforce server’s hard drive is out of space.
- C. A detection server has excessive filereader restarts.
- D. Tablespace is almost full.
Answer: D
NEW QUESTION 17
Which Network Prevent action takes place when the Network Incident list shows the message is “Modified”?
- A. Remove attachments from an email
- B. Obfuscate text in the body of an email
- C. Add one or more SMTP headers to an email
- D. Modify content from the body of an email
Answer: C
NEW QUESTION 18
How should a DLP administrator change a policy so that it retains the original file when an endpoint incident has detected a “copy to USB device” operation?
- A. Add a “Limit Incident Data Retention” response rule with “Retain Original Message” option selected.
- B. Modify the agent config.db to include the file
- C. Modify the “Endpoint_Retain_Files.int” setting in the Endpoint server configuration
- D. Modify the agent configuration and select the option “Retain Original Files”
Answer: A
NEW QUESTION 19
What is the correct order for data in motion when a customer has integrated their CloudSOC and DLP solutions?
- A. User > CloudSOC Gatelet > DLP Cloud Detection Service > Application
- B. User > Enforce > Application
- C. User > Enforce > CloudSOC > Application
- D. User > CloudSOC Gatelet > Enforce > Application
Answer: C
NEW QUESTION 20
Which two Infrastructure-as-a-Service providers are supported for hosting Cloud Prevent for Office 365? (Choose two.)
- A. Any customer-hosted private cloud
- B. Amazon Web Services
- C. AT&T
- D. Verizon
- E. Rackspace
Answer: BE
NEW QUESTION 21
An administrator is unable to log in to the Enforce management console as “sysadmin”. Symantec DLP is configured to use Active Directory authentication. The administrator is a member of two roles: “sysadmin” and “remediator.” How should the administrator log in to the Enforce console with the “sysadmin” role?
- A. sysadminusername
- B. sysadminusername@domain
- C. domainusername
- D. usernamesysadmin
Answer: C
NEW QUESTION 22
What detection server type requires a minimum of two physical network interface cards?
- A. Network Prevent for Web
- B. Network Prevent for Email
- C. Network Monitor
- D. Cloud Detection Service (CDS)
Answer: A
NEW QUESTION 23
......
100% Valid and Newest Version 250-438 Questions & Answers shared by Thedumpscentre.com, Get Full Dumps HERE: https://www.thedumpscentre.com/250-438-dumps/ (New 70 Q&As)

