2V0-41.23 Exam Questions - Online Test
2V0-41.23 Premium VCE File

150 Lectures, 20 Hours

Proper study guides for Latest VMware VMware NSX 4.x Professional certified begins with VMware 2V0-41.23 preparation products which designed to deliver the Validated 2V0-41.23 questions by making you pass the 2V0-41.23 test at your first time. Try the free 2V0-41.23 demo right now.
Free 2V0-41.23 Demo Online For VMware Certifitcation:
NEW QUESTION 1
Which of the two following characteristics about NAT64 are true? (Choose two.)
- A. NAT64 is stateless and requires gateways to be deployed in active-standby mode.
- B. NAT64 is supported on Tier-1 gateways only.
- C. NAT64 is supported on Tier-0 and Tier-1 gateways.
- D. NAT64 requires the Tier-1 gateway to be configured in active-standby mode.
- E. NAT64 requires the Tier-1 gateway to be configured in active-active mode.
Answer: CD
Explanation:
https://docs.vmware.com/en/VMware-NSX/4.1/administration/GUID-69604E49-BC8B-4777-BFD8-B98F8D1F
NEW QUESTION 2
Which three data collection sources are used by NSX Network Detection and Response to create correlations/Intrusion campaigns? (Choose three.)
- A. Files and anti-malware (lie events from the NSX Edge nodes and the Security Analyzer
- B. East-West anti-malware events from the ESXi hosts
- C. Distributed Firewall flow data from the ESXi hosts
- D. IDS/IPS events from the ESXi hosts and NSX Edge nodes
- E. Suspicious Traffic Detection events from NSX Intelligence
Answer: ADE
Explanation:
The correct answers are A. Files and anti-malware (file) events from the NSX Edge nodes and the Security Analyzer, D. IDS/IPS events from the ESXi hosts and NSX Edge nodes, and E. Suspicious Traffic Detection events from NSX Intelligence. According to the VMware NSX Documentation3, these are the three data collection sources that are used by NSX Network Detection and Response to create correlations/intrusion campaigns.
The other options are incorrect or not supported by NSX Network Detection and Response. East-West anti-malware events from the ESXi hosts are not collected by NSX Network Detection and
Response3. Distributed Firewall flow data from the ESXi hosts are not used for correlation/intrusion
campaigns by NSX Network Detection and Response3.
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.2/administration/GUID-14BBE50D-9931-4719-8F
NEW QUESTION 3
An architect receives a request to apply distributed firewall in a customer environment without making changes to the network and vSphere environment. The architect decides to use Distributed Firewall on VDS.
Which two of the following requirements must be met in the environment? (Choose two.)
- A. vCenter 8.0 and later
- B. NSX version must be 3.2 and later
- C. NSX version must be 3.0 and later
- D. VDS version 6.6.0 and later
Answer: BD
Explanation:
Distributed Firewall on VDS is a feature of NSX-T Data Center that allows users to install Distributed Security for vSphere Distributed Switch (VDS) without the need to deploy an NSX Virtual Distributed Switch (N-VDS). This feature provides NSX security capabilities such as Distributed Firewall (DFW), Distributed IDS/IPS, Identity Firewall, L7 App ID, FQDN Filtering, NSX Intelligence, and NSX Malware Prevention. To enable this feature, the following requirements must be met in the environment: The NSX version must be 3.2 and later1. This is the minimum version that supports Distributed Security for VDS.
The NSX version must be 3.2 and later1. This is the minimum version that supports Distributed Security for VDS. The VDS version must be 6.6.0 and later1. This is the minimum version that supports the NSX host preparation operation that activates the DFW with the default rule set to allow.
The VDS version must be 6.6.0 and later1. This is the minimum version that supports the NSX host preparation operation that activates the DFW with the default rule set to allow.
References: Overview of NSX IDS/IPS and NSX Malware Prevention
Overview of NSX IDS/IPS and NSX Malware Prevention
NEW QUESTION 4
An NSX administrator would like to create an L2 segment with the following requirements:
• L2 domain should not exist on the physical switches.
• East/West communication must be maximized as much as possible.
Which type of segment must the administrator choose?
- A. VLAN
- B. Overlay
- C. Bridge
- D. Hybrid
Answer: B
Explanation:
An overlay segment is a layer 2 broadcast domain that is implemented as a logical construct in the NSX-T Data Center software. Overlay segments do not require any configuration on the physical switches, and they allow for optimal east/west communication between workloads on different ESXi hosts. Overlay segments use the Geneve protocol to encapsulate and decapsulate traffic between the hosts. Overlay segments are created and managed by the NSX Manager.
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.2/administration/GUID-316E5027-E588-455C-88
NEW QUESTION 5
Which field in a Tier-1 Gateway Firewall would be used to allow access for a collection of trustworthy web sites?
- A. Source
- B. Profiles -> Context Profiles
- C. Destination
- D. Profiles -> L7 Access Profile
Answer: D
Explanation:
The field in a Tier-1 Gateway Firewall that would be used to allow access for a collection of trustworthy web sites is Profiles -> L7 Access Profile. This field allows the user to create a Layer 7 access profile that defines list of allowed or blocked URLs based on categories, reputation, or custom entries1. The user can then apply the L7 access profile to a firewall rule to control the traffic based on the URL filtering criteria1. The other options are incorrect because they are not related to URL filtering. The Source field specifies the source IP address or group of the firewall rule1. The Destination field specifies the destination IP address or group of the firewall rule1. The Profiles -> Context Profiles field allows the user to create a context profile that defines a list of application signatures or attributes that can be used to identify and classify network
traffic1. References: Gateway Firewall
NEW QUESTION 6
An NSX administrator is using ping to check connectivity between VM1 running on ESXi1 to VM2 running on ESXi2. The ping tests fails. The administrator knows the maximum transmission unit size on the physical switch is 1600.
Which command does the administrator use to check the VMware kernel ports for tunnel end point communication?
- A. esxcli network diag ping -I vmk0O -H <destination IP address>
- B. vmkping ++netstack=geneve -d -s 1572 <destination IP address>
- C. esxcli network diag ping -H <destination IP address>
- D. vmkping ++netstack=vxlan -d -s 1572 <destination IP address>
Answer: B
Explanation:
The command vmkping ++netstack=geneve -d -s 1572 <destination IP address> is used to check the VMwar kernel ports for tunnel end point communication. This command uses the geneve netstack, which is the default netstack for NSX-T. The -d option sets the DF (Don’t Fragment) bit in the IP header, which prevents the packet from being fragmented by intermediate routers. The -s 1572 option sets the packet size to 1572 bytes, which is the maximum payload size for a geneve encapsulated packet with an MTU of 1600 bytes.
The <destination IP address> is the IP address of the remote ESXi host or VM. References: : VMware NS Data Center Installation Guide, page 19. : VMware Knowledge Base: Testing MTU with the vmkping command (1003728). : VMware NSX-T Data Center Administration Guide, page 102.
NEW QUESTION 7
Refer to the exhibit.
An administrator configured NSX Advanced Load Balancer to redistribute the traffic between the web servers. However, requests are sent to only one server
Which of the following pool configuration settings needs to be adjusted to resolve the problem? Mark the correct answer by clicking on the image.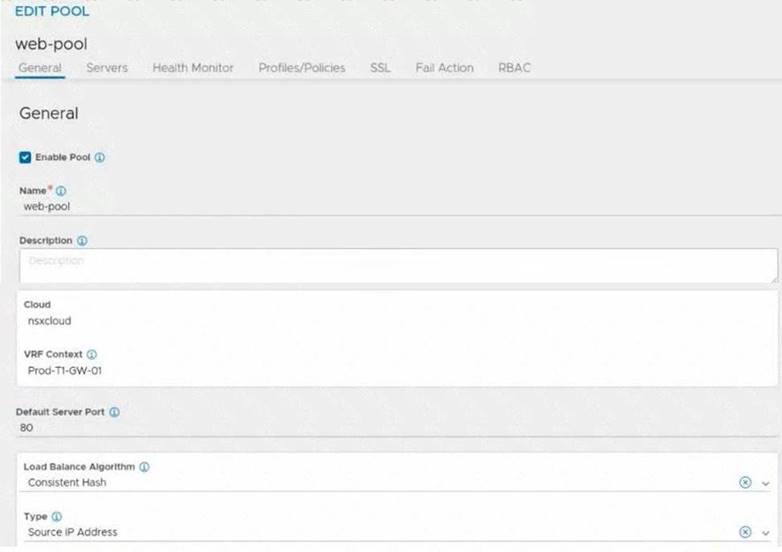
Solution:
Load Balancing Algorithm
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 8
Which command on ESXI is used to verify the Local Control Plane connectivity with Central Control Plane?
A)
B)
C)
D)
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: B
Explanation:
According to the web search results, the command that is used to verify the Local Control Plane (LCP) connectivity with Central Control Plane (CCP) on ESXi is get control-cluster status. This command displays the status of the LCP and CCP components on the ESXi host, such as the LCP agent, CCP client, CCP server, and CCP connection. It also shows the IP address and port number of the CCP server that the LCP agent is connected to. If the LCP agent or CCP client are not running or not connected, it means that there is a problem with the LCP connectivity .
NEW QUESTION 9
When running nsxcli on an ESXi host, which command will show the Replication mode?
- A. get logical-switch <Local-Switch-UUID> status
- B. get logical-switch <Logical-Switch-UUID>
- C. get logical-switches
- D. get logical-switch status
Answer: B
NEW QUESTION 10
What are two valid BGP Attributes that can be used to influence the route path traffic will take? (Choose two.)
- A. AS-Path Prepend
- B. BFD
- C. Cost
- D. MED
Answer: AD
Explanation:  AS-Path Prepend: This attribute allows you to prepend one or more AS numbers to the AS path of a route, making it appear longer and less preferable to other BGP routers. You can use this attribute to manipulate the inbound traffic from your BGP peers by advertising a longer AS path for some routes and a shorter AS path for others .
AS-Path Prepend: This attribute allows you to prepend one or more AS numbers to the AS path of a route, making it appear longer and less preferable to other BGP routers. You can use this attribute to manipulate the inbound traffic from your BGP peers by advertising a longer AS path for some routes and a shorter AS path for others . MED: This attribute stands for Multi-Exit Discriminator and allows you to specify a preference value for a route among multiple exit points from an AS. You can use this attribute to manipulate the outbound traffic to your BGP peers by advertising a lower MED value for some routes and a higher MED value for others .
MED: This attribute stands for Multi-Exit Discriminator and allows you to specify a preference value for a route among multiple exit points from an AS. You can use this attribute to manipulate the outbound traffic to your BGP peers by advertising a lower MED value for some routes and a higher MED value for others .
NEW QUESTION 11
What are two functions of the Service Engines in NSX Advanced Load Balancer? (Choose two.)
- A. It collects real-time analytics from application traffic flows.
- B. It stores the configuration and policies related to load-balancing services.
- C. It performs application load-balancing operations.
- D. It deploys web servers to perform load-balancing operations.
- E. It provides a user interface to perform configuration and management tasks.
Answer: CE
Explanation:
The Service Engines in NSX Advanced Load Balancer are VM-based applications that handle all data plane operations by receiving and executing instructions from the Controller. The Service Engines perform the following functions: They perform application load-balancing operations for all client- and server-facing network interactions. They support various load-balancing algorithms, health monitors, SSL termination, and persistence profiles.
They perform application load-balancing operations for all client- and server-facing network interactions. They support various load-balancing algorithms, health monitors, SSL termination, and persistence profiles. They provide a user interface to perform configuration and management tasks. The user interface is accessible through a web browser or a REST API. The user interface allows the user to create and modify virtual services, pools, health monitors, policies, analytics, and other load-balancing settings
They provide a user interface to perform configuration and management tasks. The user interface is accessible through a web browser or a REST API. The user interface allows the user to create and modify virtual services, pools, health monitors, policies, analytics, and other load-balancing settings
https://docs.vmware.com/en/VMware-Telco-Cloud-Platform/3.0/vmware-telco-cloud-reference-architecture-gui
NEW QUESTION 12
Which table on an ESXi host is used to determine the location of a particular workload for a frame-forwarding decision?
- A. TEP Table
- B. MAC Table
- C. ARP Table
- D. Routing Table
Answer: B
Explanation:
The MAC table on an ESXi host is used to determine the location of a particular workload for a
frame-forwarding decision. The MAC table maps the MAC addresses of the workloads to their corresponding tunnel endpoint (TEP) IP addresses. The TEP IP address identifies the ESXi host where the workload resides. The MAC table is populated by learning the source MAC addresses of the incoming frames from the workloads. The MAC table is also synchronized with other ESXi hosts in the same transport zone by using the NSX Controller.
https://nsx.techzone.vmware.com/resource/nsx-reference-design-guide
NEW QUESTION 13
How is the RouterLink port created between a Tier-1 Gateway and Tier-O Gateway?
- A. Automatically created when Tier-1 is connected with Tier-0 from NSX UI.
- B. Automatically created when Tier-1 is created.
- C. Manually create a Logical Switch and connect to bother Tier-1 and Tier-0 Gateways.
- D. Manually create a Segment and connect to both Tier-1 and Tier-0 Gateways.
Answer: A
Explanation:
The RouterLink port is automatically created when a Tier-1 Gateway is connected with a Tier-0 Gateway from the NSX UI1. The RouterLink port is a logical interface that is assigned an IP address and is associated with a physical or virtual interface. The RouterLink port acts as an end point of the IPSec tunnel and routes traffic between the Tier-1 Gateway and the Tier-0 Gateway2. The other options are incorrect because they involve manual creation of logical switches or segments, which are not required for RouterLink port
creation. References: Configure NSX for Virtual Networking from vSphere Client, Virtual Private Networ (VPN)
NEW QUESTION 14
Refer to the exhibits.
Drag and drop the NSX graphic element icons on the left found in an NSX Intelligence visualization graph to Its correct description on the right.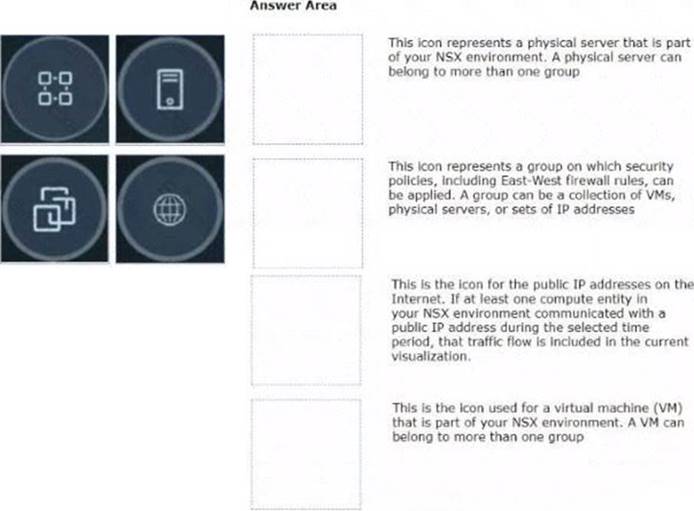
Solution:
https://docs.vmware.com/en/VMware-NSX-Intelligence/4.0/user-guide/GUID-DC78552B-2CC4-410D-A6C9-3
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 15
Which two of the following features are supported for the Standard NSX Application Platform Deployment? (Choose two.)
- A. NSX Intrusion Detection and Prevention
- B. NSX Intelligence
- C. NSX Network Detection and Response
- D. NSX Malware Prevention Metrics
- E. NSX Intrinsic Security
Answer: CD
Explanation:
The NSX Application Platform Deployment features are divided into three form factors: Evaluation, Standard, and Advanced. Each form factor determines which NSX features can be activated or installed on the platform1. The Evaluation form factor supports only NSX Intelligence, which provides network visibility and analytics for NSX-T environments2. The Standard form factor supports both NSX Intelligence and NSX Network Detection and Response, which provides network threat detection and response capabilities for
NSX-T environments3. The Advanced form factor supports all four features: NSX Intelligence, NSX Network Detection and Response, NSX Malware Prevention, and NSX Metrics1.
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.2/nsx-application-platform/GUID-85CD2728-8081
NEW QUESTION 16
An administrator has connected two virtual machines on the same overlay segment. Ping between both virtual machines is successful. What type of network boundary does this represent?
- A. Layer 2 VPN
- B. Layer 2 bridge
- C. Layer 2 broadcast domain
- D. Layer 3 route
Answer: C
Explanation:
An overlay segment is a logical construct that provides Layer 2 connectivity between virtual machines that are attached to it. An overlay segment can span multiple hosts and can be extended across different subnets or locations using Geneve encapsulation3. Therefore, two virtual machines on the same overlay segment belong to the same Layer 2 broadcast domain, which means they can communicate with each other using their MAC addresses without requiring any routing. The other options are incorrect because they involve Layer 3 or higher network boundaries, which require routing or tunneling to connect different
segments. References: VMware NSX Documentation
NEW QUESTION 17
What should an NSX administrator check to verify that VMware Identity Manager Integration Is successful?
- A. From VMware Identity Manager the status of the remote access application must be green.
- B. From the NSX UI the status of the VMware Identity Manager Integration must be "Enabled".
- C. From the NSX CLI the status of the VMware Identity Manager Integration must be "Configured".
- D. From the NSX UI the URI in the address bar must have "locaNfatse" part of it.
Answer: B
Explanation:
From the NSX UI the status of the VMware Identity Manager Integration must be “Enabled”. According to the VMware NSX Documentation1, after configuring VMware Identity Manager integration, you can validate the functionality by checking the status of the integration in the NSX UI. The status should be “Enabled” if the integration is successful. The other options are either incorrect or not relevant.
NEW QUESTION 18
A customer is preparing to deploy a VMware Kubernetes solution in an NSX environment. What is the minimum MTU size for the UPLINK profile?
- A. 1500
- B. 1550
- C. 1700
- D. 1650
Answer: C
Explanation:
The minimum MTU size for the UPLINK profile is 1700 bytes. This is because the UPLINK profile is used to configure the physical NICs that connect to the NSX-T overlay network. The overlay network uses geneve encapsulation, which adds an overhead of 54 bytes to the original packet. Therefore, to support a standard MTU of 1500 bytes for the inner packet, the outer packet must have an MTU of at least 1554 bytes. However, VMware recommends adding an extra buffer of 146 bytes to account for possible additional headers or VLAN tags. Therefore, the minimum MTU size for the UPLINK profile is 1700 bytes (1554 + 146). References: : VMware NSX-T Data Center Installation Guide, page 23. : VMware NSX-T Data Center Administration Guide, page 102. : VMware NSX-T Data Center Installation Guide, page 24.
NEW QUESTION 19
Which two of the following will be used for Ingress traffic on the Edge node supporting a Single Tier topology? (Choose two.)
- A. Inter-Tier interface on the Tier-0 gateway
- B. Tier-0 Uplink interface
- C. Downlink Interface for the Tier-0 DR
- D. Tier-1 SR Router Port
- E. Downlink Interface for the Tier-1 DR
Answer: BC
Explanation:
The two interfaces that will be used for ingress traffic on the Edge node supporting a Single Tier topology are: B. Tier-0 Uplink interface
B. Tier-0 Uplink interface C. Downlink Interface for the Tier-0 DR
C. Downlink Interface for the Tier-0 DR
The Tier-0 Uplink interface is the interface that connects the Tier-0 gateway to the external network. It is used to receive traffic from the physical router or switch that is the next hop for the Tier-0 gateway. The Tier-0 Uplink interface can be configured with a static IP address or use BGP to exchange routes with the external network.
The Downlink Interface for the Tier-0 DR is the interface that connects the Tier-0 gateway to the workload segments. It is used to receive traffic from the VMs or containers that are attached to the segments. The Downlink Interface for the Tier-0 DR is a logical interface (LIF) that is distributed across all transport nodes that host the segments. The Downlink Interface for the Tier-0 DR has an IP address that acts as the default gateway for the VMs or containers on the segments.
NEW QUESTION 20
Which NSX feature can be leveraged to achieve consistent policy configuration and simplicity across sites?
- A. VRF Lite
- B. Ethernet VPN
- C. NSX MTML5 UI
- D. NSX Federation
Answer: D
Explanation:
According to the VMware NSX Documentation, this is the NSX feature that can be leveraged to achieve consistent policy configuration and simplicity across sites: NSX Federation: This feature allows you to create and manage a global network infrastructure that spans across multiple sites using a single pane of glass. You can use this feature to synchronize policies, segments, gateways, firewalls, VPNs, load balancers, and other network services across sites.
NSX Federation: This feature allows you to create and manage a global network infrastructure that spans across multiple sites using a single pane of glass. You can use this feature to synchronize policies, segments, gateways, firewalls, VPNs, load balancers, and other network services across sites.
NEW QUESTION 21
......
Thanks for reading the newest 2V0-41.23 exam dumps! We recommend you to try the PREMIUM Dumps-files.com 2V0-41.23 dumps in VCE and PDF here: https://www.dumps-files.com/files/2V0-41.23/ (106 Q&As Dumps)
- Improve 2V0-761 Answers 2021
- [2021-New] VMware 2V0-621 Dumps With Update Exam Questions (81-90)
- [2021-New] VMware 2V0-620 Dumps With Update Exam Questions (101-110)
- Best Quality 2V0-731 Exam Questions and Answers 2021
- [2021-New] VMware 2V0-642 Dumps With Update Exam Questions (1-10)
- [2021-New] VMware 2V0-621D Dumps With Update Exam Questions (71-80)
- Regenerate Advanced Design VMware NSX-T Data Center 3V0-42.20 Simulations
- Top Tips Of Avant-garde 2V0-31.20 Dumps Questions
- A Review Of Pinpoint 2V0-41.20 Exam Guide
- Up To The Minute 2V0-41.20 Exam Answers For Professional VMware NSX-T Data Center Certification

