AZ-303 Exam Questions - Online Test
AZ-303 Premium VCE File

150 Lectures, 20 Hours

Passleader AZ-303 Questions are updated and all AZ-303 answers are verified by experts. Once you have completely prepared with our AZ-303 exam prep kits you will be ready for the real AZ-303 exam without a problem. We have Rebirth Microsoft AZ-303 dumps study guide. PASSED AZ-303 First attempt! Here What I Did.
Online Microsoft AZ-303 free dumps demo Below:
NEW QUESTION 1
You are planning the move of App1 to Azure. You create a network security group (NSG).
You need to recommend a solution to provide users with access to App1. What should you recommend?
- A. Create an outgoing security rule for port 443 from the Interne
- B. Associate the NSG to all the subnets.
- C. Create an incoming security rule for port 443 from the Interne
- D. Associate the NSG to all the subnets.
- E. Create an incoming security rule for port 443 from the Interne
- F. Associate the NSG to the subnet that contains the web servers.
- G. Create an outgoing security rule for port 443 from the Interne
- H. Associate the NSG to the subnet that contains the web servers.
Answer: C
Explanation:
As App1 is public-facing we need an incoming security rule, related to the access of the web servers. Scenario: You have a public-facing application named App1. App1 is comprised of the following three tiers: a SQL database, a web front end, and a processing middle tier.
Each tier is comprised of five virtual machines. Users access the web front end by using HTTPS only.
NEW QUESTION 2
You have an Azure Container Registry and an Azure container instance.
You pull an image from the registry, and then update the local copy of the image.
You need to ensure that the updated image can be deployed to the container instance. The solution must ensure that you can deploy the updated image or the previous version of the image.
What should you do?
- A. Run the docker image push command and specify the tag parameter.
- B. Run the az image copy command and specify the tag paramete
- C. Run the az aks update command and specify the attach-acr parameter.
- D. Run the kubect1 apply command and specify the dry-run parameter.
Answer: B
NEW QUESTION 3
Your company has an Azure Container Registry named Registry1.
You have an Azure virtual machine named Server1 that runs Windows Server 2019. From Server1, you create a container image named image1.
You need to add image1 to Registry1.
Which command should you run on Server1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
An Azure container registry stores and manages private Docker container images, similar to the way Docker Hub stores public Docker images. You can use the Docker command-line interface (Docker CLI) for login, push, pull, and other operations on your container registry.
Reference:
https://docs.microsoft.com/en-us/azure/container-registry/container-registry-get-started-docker-cli https://docs.docker.com/engine/reference/commandline/push/
NEW QUESTION 4
You have three Azure SQL Database servers shown in the following table.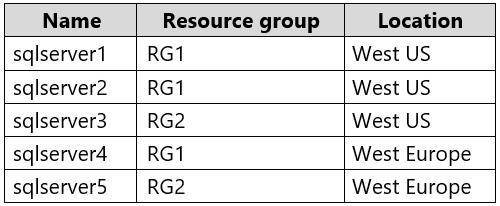
You plan to specify sqlserver1 as the primary server in a failover group. Which servers can be used as a secondary server?
- A. sqlserver4 and sqlserver5 only
- B. sqlserver2 and sqlserver3 only
- C. sqlserver1 and sqlserver3 only
- D. sqlserver2 and sqlserver4 only
Answer: D
Explanation:
The Resource Group must be the same.
The secondary server can have another location.
The secondary server cannot be the same as the primary server. Reference:
https://docs.microsoft.com/en-us/azure/azure-sql/database/auto-failover-group-configure
NEW QUESTION 5
You have an Azure logic app named App1 and an Azure Service Bus queue named Queue1.
You need to ensure that App1 can read messages from Queue1. App1 must authenticate by using Azure Active Directory (Azure AD).
What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.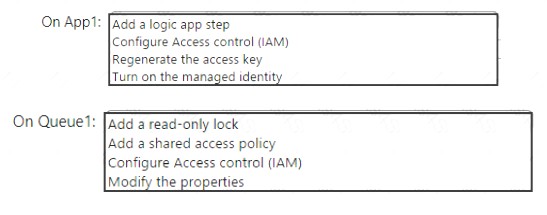
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
On App1: Turn on the managed identity
To use Service Bus with managed identities, you need to assign the identity the role and the appropriate scope. The procedure in this section uses a simple application that runs under a managed identity and accesses Service Bus resources.
Once the application is created, follow these steps:  Go to Settings and select Identity.
Go to Settings and select Identity. Select the Status to be On.
Select the Status to be On. Select Save to save the setting.
Select Save to save the setting.
On Queue1: Configure Access Control (IAM)
Azure Active Directory (Azure AD) authorizes access rights to secured resources through role-based access control (RBAC). Azure Service Bus defines a set of built-in RBAC roles that encompass common sets of permissions used to access Service Bus entities and you can also define custom roles for accessing the data.
Assign RBAC roles using the Azure portal
In the Azure portal, navigate to your Service Bus namespace. Select Access Control (IAM) on the left menu to display access control settings for the namespace. If you need to create a Service Bus namespace.
Select the Role assignments tab to see the list of role assignments. Select the Add button on the toolbar and then select Add role assignment.
Reference:
https://docs.microsoft.com/en-us/azure/service-bus-messaging/authenticate-application https://docs.microsoft.com/en-us/azure/service-bus-messaging/service-bus-managed-service-identity
NEW QUESTION 6
You have an Azure Active Directory (Azure AD) tenant that contains the user groups shown in the following table.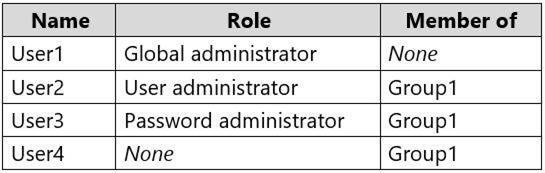
You enable self-service password reset (SSPR) for Group1.
You configure the Notifications settings as shown in the following exhibit.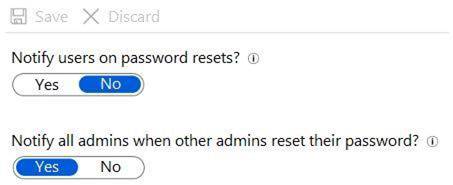
For each of the following statements, select Yes if the statement is true. Otherwise, select No.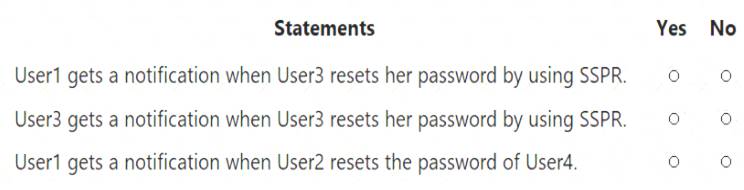
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Box 1: Yes
Notify all admins when other admins reset their passwords: Yes. Box 2: No
Notify users on password resets: No. Box 3: No Notify users on password resets
Notify users on password resets
If this option is set to Yes, then users resetting their password receive an email notifying them that their password has been changed. The email is sent via the SSPR portal to their primary and alternate email addresses that are on file in Azure AD. No one else is notified of the reset event. Notify all admins when other admins reset their passwords
Notify all admins when other admins reset their passwords
If this option is set to Yes, then all administrators receive an email to their primary email address on file in Azure AD. The email notifies them that another administrator has changed their password by using SSPR.
Example: There are four administrators in an environment. Administrator A resets their password by using SSPR. Administrators B, C, and D receive an email alerting them of the password reset.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-sspr-howitworks https://docs.microsoft.com/en-us/azure/active-directory/authentication/tutorial-enable-sspr
NEW QUESTION 7
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company is deploying an on-premises application named Appl. Users will access App1 by using a URL of https://app1.contoso.com. You register App1 in Azure Active Directory (Azure AD) and publish Appl by using the Azure AD Application Proxy. You need to ensure that Appl appears in the My Apps portal for all the users.
Solution: You create an offer for App1 and publish the offer to Azure Marketplace.
- A. Yes
- B. No
Answer: A
NEW QUESTION 8
You have an Azure subscription named Subscription1 that is used by several departments at your company. Subscription1 contains the resources in the following table.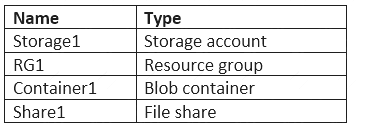
Another administrator deploys a virtual machine named VM1 and an Azure Storage account named Storage2 by using a single Azure Resource Manager template.
You need to view the template used for the deployment.
From which blade can you view the template that was used for the deployment?
- A. Container1
- B. VM1
- C. Storage2
- D. RG1
Answer: D
NEW QUESTION 9
You need to identify the storage requirements for Contoso.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.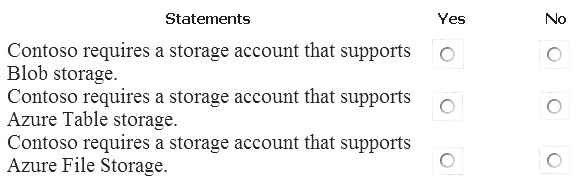
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Box 1: Yes
Contoso is moving the existing product blueprint files to Azure Blob storage.
Use unmanaged standard storage for the hard disks of the virtual machines. We use Page Blobs for these. Box 2: No
Box 3: No
NEW QUESTION 10
You have a hierarchy of management groups and Azure subscriptions as shown in the following table.
You create the Azure resources shown in the following table.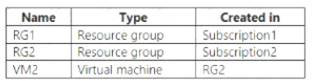
You assign roles to users as shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 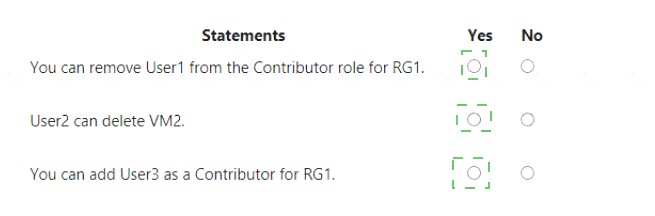
NEW QUESTION 11
You have an Azure subscription that contains an Azure key vault named KeyVault1 and the virtual machines shown in the following table.
KeyVault1 has an access policy that provides several users with Create Key permissions. You need to ensure that the users can only register secrets in KeyVault1 from VM1. What should you do?
- A. Create a network security group (NSG) that is linked to Subnet1.
- B. Configure the Firewall and virtual networks settings for KeyVault1.
- C. Modify the access policy for KeyVault1.
- D. Configure KeyVault1 to use a hardware security module (HSM).
Answer: C
Explanation:
You grant data plane access by setting Key Vault access policies for a key vault. Note 1: Grant our VM’s system-assigned managed identity access to the Key Vault. Select Access policies and click Add new.
Select Access policies and click Add new. In Configure from template, select Secret Management.
In Configure from template, select Secret Management. Choose Select Principal, and in the search field enter the name of the VM you created earlier. Select the VM in the result list and click Select.
Choose Select Principal, and in the search field enter the name of the VM you created earlier. Select the VM in the result list and click Select. Click OK to finishing adding the new access policy, and OK to finish access policy selection.
Click OK to finishing adding the new access policy, and OK to finish access policy selection.
Note 2: Access to a key vault is controlled through two interfaces: the management plane and the data plane. The management plane is where you manage Key Vault itself. Operations in this plane include creating and deleting key vaults, retrieving Key Vault properties, and updating access policies. The data plane is where you work with the data stored in a key vault. You can add, delete, and modify keys, secrets, and certificates.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/tutorial-windows-vm https://docs.microsoft.com/en-us/azure/key-vault/general/secure-your-key-vault2
NEW QUESTION 12
You have an Azure SQL database named Db1 that runs on an Azure SQL server named SQLserver1. You need to ensure that you can use the query editor on the Azure portal to query Db1.
What should you do?
- A. Modify the Advanced Data Security settings of Db1
- B. Configure the Firewalls and virtual networks settings for SQLserver1
- C. Copy the ADO.NET connection string of Db1 and paste the string to the query editor
- D. Approve private endpoint connections for SQLserver1
Answer: B
Explanation:
Reference:
https://docs.microsoft.com/en-us/azure/sql-database/sql-database-connect-query-portal
NEW QUESTION 13
You have an application named App1 that does not support Azure Active Directory (Azure AD) authentication.
You need to ensure that App1 can send messages to an Azure Service Bus queue. The solution must prevent Appl from listening to the queue.
What should you do?
- A. Modify the locks of the Queue
- B. Configure Access control (IAM) for the Service Bus
- C. Configure Access control (IAM) for the queue.
- D. Add a shared access policy to the queue
Answer: D
Explanation:
There are two ways to authenticate and authorize access to Azure Service Bus resources: Azure Activity Directory (Azure AD) and Shared Access Signatures (SAS).
Each Service Bus namespace and each Service Bus entity has a Shared Access Authorization policy made up of rules.
Reference:
https://docs.microsoft.com/en-us/azure/service-bus-messaging/service-bus-authentication-and-authorization https://docs.microsoft.com/en-us/azure/service-bus-messaging/service-bus-sas
NEW QUESTION 14
You have an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains the users shown in the following table.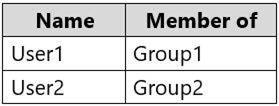
The tenant contains computers that run Windows 10. The computers are configured as shown in the following table.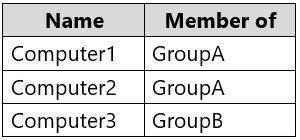
You enable Enterprise State Roaming in contoso.com for Group1 and GroupA.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Enterprise State Roaming provides users with a unified experience across their Windows devices and reduces the time needed for configuring a new device.
Box 1: Yes
Box 2: No
Box 3: Yes References:
https://docs.microsoft.com/en-us/azure//////active-directory/devices/enterprise-state-roaming-overview
NEW QUESTION 15
You plan to create an Azure Storage account in the Azure region of East US 2. You need to create a storage account that meets the following requirements: Replicates synchronously
Replicates synchronously Remains available if a single data center in the region fails
Remains available if a single data center in the region fails
How should you configure the storage account? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Box 1: Zone-redundant storage (ZRS)
Zone-redundant storage (ZRS) replicates your data synchronously across three storage clusters in a single region.
LRS would not remain available if a data center in the region fails GRS and RA GRS use asynchronous replication.
Box 2: StorageV2 (general purpose V2) ZRS only support GPv2.
References:
https://docs.microsoft.com/en-us/azure/storage/common/storage-redundancy https://docs.microsoft.com/en-us/azure/storage/common/storage-redundancy-zrs
NEW QUESTION 16
You have an Azure subscription that contains two virtual networks named VNet1 and VNet2. Virtual machines connect to the virtual networks.
The virtual networks have the address spaces and the subnets configured as shown in the following table.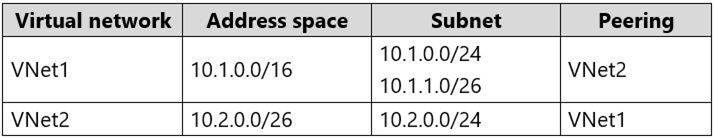
You need to add the address space of 10.33.0.0/16 to VNet1. The solution must ensure that the hosts on VNet1 and VNet2 can communicate.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Step 1: Remove peering between Vnet1 and VNet2.
You can't add address ranges to, or delete address ranges from a virtual network's address space once a virtual network is peered with another virtual network. To add or remove address ranges, delete the peering, add or remove the address ranges, then re-create the peering. Step 2: Add the 10.44.0.0/16 address space to VNet1. Step 3: Recreate peering between VNet1 and VNet2 References:
https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-manage-peering
NEW QUESTION 17
Note: This question is part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more
than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
A user named Admin1 attempts to create an access review from the Azure Active Directory admin center and discovers that the Access reviews settings are unavailable. Admin1 discovers that all the other Identity Governance settings are available.
Admin1 is assigned the User administrator, Compliance administrator, and Security administrator roles. You need to ensure that Admin1 can create access reviews in contoso.com.
Solution: You create an access package. Does this meet the goal?
- A. Yes
- B. No
Answer: B
Explanation:
You do not use access packages for Identity Governance. Instead use Azure AD Privileged Identity Management.
Note: PIM essentially helps you manage the who, what, when, where, and why for resources that you care about. Key features of PIM include:
Conduct access reviews to ensure users still need roles References:
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure https://docs.microsoft.com/en-us/azure/active-directory/governance/entitlement-management-overview
NEW QUESTION 18
The developers at your company request that you create databases in Azure Cosmos DB as shown in the following table.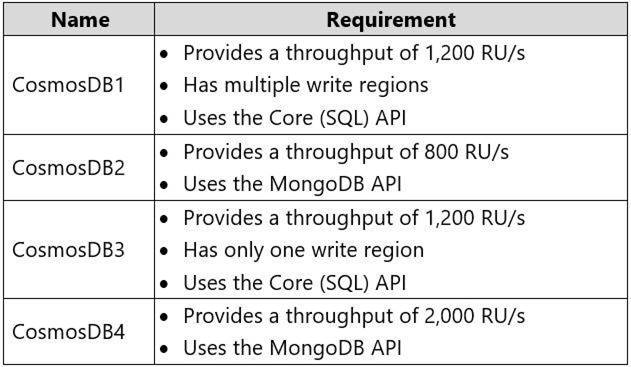
You need to create the Azure Cosmos DB databases to meet the developer request. The solution must minimize costs.
What are two possible ways to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. Create three Azure Cosmos DB accounts, one for the databases that use the Core (SQL) API, one for CosmosDB2, and one for CosmosDB4.
- B. Create two Azure Cosmos DB accounts, one for CosmosDB2 and CosmosDB4 and one for CosmosDB1 and CosmosDB3.
- C. Create one Azure Cosmos DB account for each database.
- D. Create three Azure Cosmos DB accounts, one for the databases that use the MongoDB API, one for CosmosDB1, and one for CosmosDB3.
Answer: BD
Explanation:
Note:
Microsoft recommends using the same API for all access to the data in a given account.
One throughput provisioned container per subscription for SQL, Gremlin API, and Table accounts. Up to three throughput provisioned collections per subscription for MongoDB accounts.
The throughput provisioned on an Azure Cosmos container is exclusively reserved for that container. The container receives the provisioned throughput all the time.
Reference:
https://docs.microsoft.com/en-us/azure/cosmos-db/set-throughput#set-throughput-on-a-container
NEW QUESTION 19
You have an Azure subscription.
You plan to deploy an app that has a web front end and an application tier.
You need to recommend a load balancing solution that meets the following requirements:  Internet to web tier:
Internet to web tier:
- Provides URL-based routing
- Supports connection draining
- Prevents SQL injection attacks  Web tier to application tier:
Web tier to application tier:
- Provides port forwarding
- Supports HTTPS health probes
- Supports an availability set as a backend pool
Which load balancing solution should you recommend for each tier? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Box 1: An Azure Application Gateway that has a web application firewall (WAF)
Azure Application Gateway offers a web application firewall (WAF) that provides centralized protection of your web applications from common exploits and vulnerabilities. Web applications are increasingly targeted by malicious attacks that exploit commonly known vulnerabilities. SQL injection and cross-site scripting are among the most common attacks.
Application Gateway operates as an application delivery controller (ADC). It offers Secure Sockets Layer (SSL) termination, cookie-based session affinity, round-robin load distribution, content-based routing, ability to host multiple websites, and security enhancements.
Box 2: An internal Azure Standard Load Balancer
The internet to web tier is the public interface, while the web tier to application tier should be internal. Note: When using load-balancing rules with Azure Load Balancer, you need to specify a health probes to
allow Load Balancer to detect the backend endpoint status.
Health probes support the TCP, HTTP, HTTPS protocols. References:
https://docs.microsoft.com/en-us/azure/application-gateway/waf-overview https://docs.microsoft.com/en-us/azure/load-balancer/load-balancer-custom-probe-overview
NEW QUESTION 20
You have an Azure subscription that contains an Azure Log Analytics workspace. You have a resource group that contains 100 virtual machines. The virtual machines run Linux. You need to collect events from the virtual machines to the Log Analytics workspace. Which type of data source should you configure in the workspace?
- A. Syslog
- B. Linux performance counters
- C. custom fields
Answer: A
Explanation:
https://docs.microsoft.com/en-us/azure/azure-monitor/learn/quick-collect-azurevm
Syslog is an event logging protocol that is common to Linux. Applications will send messages that may be stored on the local machine or delivered to a Syslog collector. When the Log Analytics agent for Linux is installed, it configures the local Syslog daemon to forward messages to the agent. The agent then sends the message to Azure Monitor where a corresponding record is created.
Reference:
https://docs.microsoft.com/en-us/azure/azure-monitor/platform/data-sources-custom-logs
NEW QUESTION 21
......
Thanks for reading the newest AZ-303 exam dumps! We recommend you to try the PREMIUM 2passeasy AZ-303 dumps in VCE and PDF here: https://www.2passeasy.com/dumps/AZ-303/ (0 Q&As Dumps)
- Microsoft AZ-100 Free Practice Questions 2021
- [2021-New] Microsoft 70-346 Dumps With Update Exam Questions (21-30)
- [2021-New] Microsoft 70-410 Dumps With Update Exam Questions (31-40)
- [2021-New] Microsoft 70-470 Dumps With Update Exam Questions (161-170)
- [2021-New] Microsoft 70-767 Dumps With Update Exam Questions (31-40)
- [2021-New] Microsoft 70-680 Dumps With Update Exam Questions (291-300)
- [2021-New] Microsoft 70-417 Dumps With Update Exam Questions (51-60)
- [2021-New] Microsoft 70-685 Dumps With Update Exam Questions (51-60)
- [2021-New] Microsoft 70-535 Dumps With Update Exam Questions (4-13)
- Microsoft 70-774 Exam Questions and Answers 2021

