HCISPP Exam Questions - Online Test
HCISPP Premium VCE File

150 Lectures, 20 Hours

It is more faster and easier to pass the ISC2 HCISPP exam by using Realistic ISC2 HealthCare Information Security and Privacy Practitioner questuins and answers. Immediate access to the Regenerate HCISPP Exam and find the same core area HCISPP questions with professionally verified answers, then PASS your exam with a high score now.
Check HCISPP free dumps before getting the full version:
NEW QUESTION 1
A multiple payer system is more cumbersome than a single payer system for all of the following reasons except:
- A. There are numerous health plans, which is difficult for providers to handle
- B. Payments are not standardized across health plans
- C. Some healthcare services are covered for people in the north, but not in the south
- D. Government programs required extensive documentation proving services were provided before paying providers
Answer: C
NEW QUESTION 2
Are there penalties under HIPPA?
- A. No penalties
- B. HIPPA calls for severe civil and criminal penalties for noncompliance, including: -- fines up to $25k for multiple violations of the same standard in a calendar year -- fines up to $250k and/or imprisonment up to 10 years for knowing misuse of individually identifiable health information.
- C. HIPPA calls for severe civil and criminal penalties for noncompliance, includes: -- fines up to 50k for multiple violations of the same standard in a calendar year -- fines up to $500k and/or imprisonment up to 10 years for knowing misuse of individually identifiable health information
- D. HIPPA calls for severe civil and criminal penalties for noncompliance, including: -- fines up to $100 for multiple violations of the same standard in a calendar year -- fines up to $750k and/or imprisonment up to 20 years for knowing misuse of individually identifiable health information
Answer: B
NEW QUESTION 3
An important principle of defense in depth is that achieving information security requires a balanced focus on which PRIMARY elements?
- A. Development, testing, and deployment
- B. Prevention, detection, and remediation
- C. People, technology, and operations
- D. Certification, accreditation, and monitoring
Answer: C
NEW QUESTION 4
What is a credential for Coders?
- A. AAPC
- B. ASPCA
- C. AHIMA
Answer: A
NEW QUESTION 5
When assessing an organization’s security policy according to standards established by the International Organization for Standardization (ISO) 27001 and 27002, when can management responsibilities be defined?
- A. Only when assets are clearly defined
- B. Only when standards are defined
- C. Only when controls are put in place
- D. Only procedures are defined
Answer: A
NEW QUESTION 6
Which of the following represents the GREATEST risk to data confidentiality?
- A. Network redundancies are not implemented
- B. Security awareness training is not completed
- C. Backup tapes are generated unencrypted
- D. Users have administrative privileges
Answer: C
NEW QUESTION 7
Which of the following is the PRIMARY risk with using open source software in a commercial software construction?
- A. Lack of software documentation
- B. License agreements requiring release of modified code
- C. Expiration of the license agreement
- D. Costs associated with support of the software
Answer: D
NEW QUESTION 8
Drag the following Security Engineering terms on the left to the BEST definition on the right.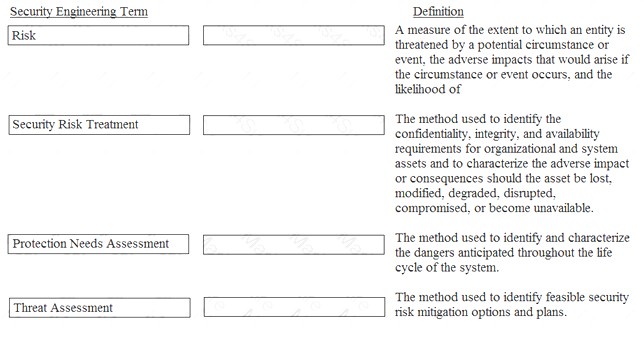
Solution:
Risk - A measure of the extent to which an entity is threatened by a potential circumstance of event, the adverse impacts that would arise if the circumstance or event occurs, and the likelihood of occurrence.
Protection Needs Assessment - The method used to identify the confidentiality, integrity, and availability requirements for organizational and system assets and to characterize the adverse impact or consequences should be asset be lost, modified, degraded, disrupted, compromised, or become unavailable.
Threat assessment - The method used to identify and characterize the dangers anticipated throughout the life cycle of the system.
Security Risk Treatment - The method used to identify feasible security risk mitigation options and plans.
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 9
Flemming discovered The Cannon of Medicine.
- A. True
- B. False
Answer: B
NEW QUESTION 10
Why did physicians remain independent of corporate settings even after the medical profession became well recognized?
- A. Hospitals were unable to pay high enough salaries to physicians.
- B. Physicians disliked salary arrangements.
- C. Licensure laws had not yet been passed.
- D. Physicians who took up practice in a corporate setting were castigated by the medical profession.
Answer: D
NEW QUESTION 11
Which of the following is a potential risk when a program runs in privileged mode?
- A. It may serve to create unnecessary code complexity
- B. It may not enforce job separation duties
- C. It may create unnecessary application hardening
- D. It may allow malicious code to be inserted
Answer: D
NEW QUESTION 12
Which is NOT an element of Security Awareness Training?
- A. Determination that all staff will receive security training
- B. Policy related to documentation of all security training
- C. Procedural issues of who will terminate user access
- D. Training on vulnerabilities of the electronic Protected Health Information policies
Answer: C
Explanation:
Procedural issues of who will terminate user access in not an element of Security Awareness Training.
NEW QUESTION 13
Which is not a "painless" cost control strategy?
- A. Reduction of administrative waste
- B. Use of cost-effective analysis to limit care
- C. Elimination of inappropriate care
- D. Elimination of ineffective care
Answer: B
NEW QUESTION 14
Each healthcare provider MUST have a document that describes how information about the client is used by the agency and when the agency will disclose/release it without the client's authorization.
- A. True
- B. False
Answer: A
NEW QUESTION 15
During the risk assessment phase of the project the CISO discovered that a college within the University is collecting Protected Health Information (PHI) data via an application that was developed in-house. The college collecting this data is fully aware of the regulations for Health Insurance Portability and Accountability Act (HIPAA) and is fully compliant.
What is the best approach for the CISO?
Below are the common phases to creating a Business Continuity/Disaster Recovery (BC/DR) plan. Drag the remaining BC\DR phases to the appropriate corresponding location.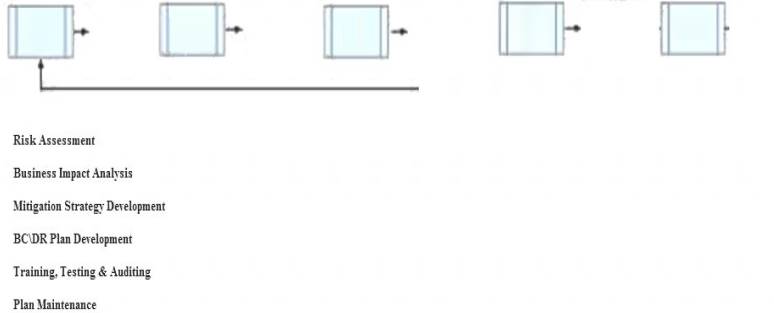
Solution:
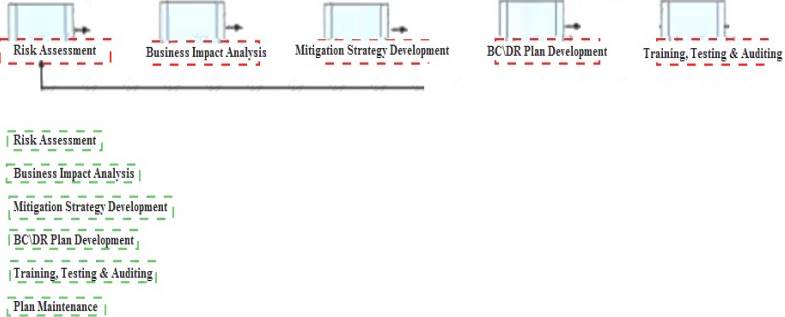
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 16
All of these factors impact the health status of an individual, however, the one exerting the least influence is.
- A. Medical care
- B. Educational level
- C. Income level
- D. Broad socioeconomic factors
Answer: A
NEW QUESTION 17
Medicare and Medicaid programs were created for population groups regarded as.
- A. Elderly
- B. Vulnerable
- C. Underinsured
- D. Politically above
Answer: B
NEW QUESTION 18
Was known for identifying anthrax.
- A. Robert Koch
- B. Edward Jenner
- C. Louis Pasteur
Answer: A
NEW QUESTION 19
If a state or federal law or regulation grants the client greater access to their PHI, then it will preempt HIPAA.
- A. True
- B. False
Answer: A
NEW QUESTION 20
If a person has the ability to access facility of company systems or applications, they have a right to view any information contained in that system or application.
- A. True
- B. False
Answer: B
NEW QUESTION 21
......
Recommend!! Get the Full HCISPP dumps in VCE and PDF From Downloadfreepdf.net, Welcome to Download: https://www.downloadfreepdf.net/HCISPP-pdf-download.html (New 305 Q&As Version)
- The Secret Of ISC2 HCISPP Study Guide
- Exact CISSP-ISSAP Resource 2021
- ISC2 CISSP-ISSEP Dumps 2021
- [2021-New] ISC2 CISSP Dumps With Update Exam Questions (151-160)
- [2021-New] ISC2 CISSP Dumps With Update Exam Questions (1-10)
- [2021-New] ISC2 CISSP Dumps With Update Exam Questions (91-100)
- [2021-New] ISC2 CISSP Dumps With Update Exam Questions (41-50)
- Up To The Immediate Present SSCP Free Practice Exam For System Security Certified Practitioner (SSCP) Certification
- [2021-New] ISC2 CISSP Dumps With Update Exam Questions (71-80)
- [2021-New] ISC2 CISSP Dumps With Update Exam Questions (71-80)

