JN0-1332 Exam Questions - Online Test
JN0-1332 Premium VCE File

150 Lectures, 20 Hours

Our pass rate is high to 98.9% and the similarity percentage between our JN0-1332 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the Juniper JN0-1332 exam in just one try? I am currently studying for the Juniper JN0-1332 exam. Latest Juniper JN0-1332 Test exam practice questions and answers, Try Juniper JN0-1332 Brain Dumps First.
Free JN0-1332 Demo Online For Juniper Certifitcation:
NEW QUESTION 1
You are designing an IP camera solution for your warehouse You must block command and control servers from communicating with the cameras. In this scenario. which two products would you need to include in your design? (Choose two)
- A. SRX Series device
- B. Security Director
- C. Juniper ATP Cloud
- D. IPS
Answer: CD
NEW QUESTION 2
When designing security for the service provider WAN. you are asked to implement unicast reverse path forwarding (uRPF) in this scenario. on which interfaces would you choose to implement loose mode uRPF?
- A. On interfaces where the best forwarding path fee routes is through the receiving interface
- B. On interfaces that are user access interfaces
- C. On interfaces where all data originates on the same network as that of the router interface
- D. On interfaces that participate in multihomes environments
Answer: B
NEW QUESTION 3
What are two reasons for using a cSRX instance over a vSRX instance? (Choose two )
- A. cSRX instances launch faster than vSRX instances
- B. cSRX instances share the host OS unlike vSRX instances.
- C. A cSRX instance uses more memory but uses less disk space than a vSRX instance
- D. A cSRX instance supports more features than a vSRX instance
Answer: C
NEW QUESTION 4
You are asked to segment the networks connected to an SRX Series device into distinct logical groups with different security requirements.
How would you accomplish this task?
- A. Define different NAT policies for each network segment.
- B. Define different security policies for each network segment.
- C. Define different intrusion prevention policies for each network segment.
- D. Define different security zones for each network segment
Answer: B
NEW QUESTION 5
You must implement a security solution that uses a central database to authenticate devices without EAP-M05 based on their network interface address. Which solution will accomplish this task'?
- A. static MAC bypass
- B. MAC RADIUS
- C. 802.1X single secure
- D. 802.1X multiple
Answer: C
NEW QUESTION 6
You must design a separate network within your trust network with added security and separation. What is the common name for this type of network?
- A. guest
- B. DMZ
- C. enclave
- D. trust
Answer: C
NEW QUESTION 7
You are a security architect for a small managed service provider. The marketing team has proposed providing firewall services to the customers.
The requirements for the solution are shown below
-- The customer must be able 10 manage their own security device.
-- You must provide segmentation using Layer 2 and Layer 3.
-- You need to implement dynamic routing
-- You need to provide UTM services
in this scenario. which product would you select to provide the firewall services?
- A. cSRX
- B. vSRX
- C. vMX
- D. vQFX
Answer: D
NEW QUESTION 8
Which automation language would you use to create on-box and off-box scripts for SRX Series devices?
- A. Python
- B. Pert
- C. Java
- D. Ruby
Answer: D
NEW QUESTION 9
When considering data center security. which aspect represents the weakest link?
- A. IPS signatures
- B. application software bugs
- C. firewall performance
- D. people
Answer: A
NEW QUESTION 10
When designing the security for a service provider core router, you are asked to add a firewall fitter on the to0 interface in this scenario, which two protocols would you want to allow through the filter? (Choose two.)
- A. LLDP
- B. SSH
- C. BGP
- D. STP
Answer: AC
NEW QUESTION 11
When using Contra! networking, security policies are distributed as access control list to which component?
- A. vSwith
- B. vSRX
- C. vMX
- D. vRouter
Answer: D
NEW QUESTION 12
You must secure network access by requiring users to log in through an HTTP browser, while also allowing printers to connect to the network using MAC address validation. What will satisfy these requirements?
- A. 802. IX multiple supplicant
- B. MAC RADIUS
- C. captive portal
- D. guest VLAN
Answer: B
NEW QUESTION 13
Refer to the exhibit.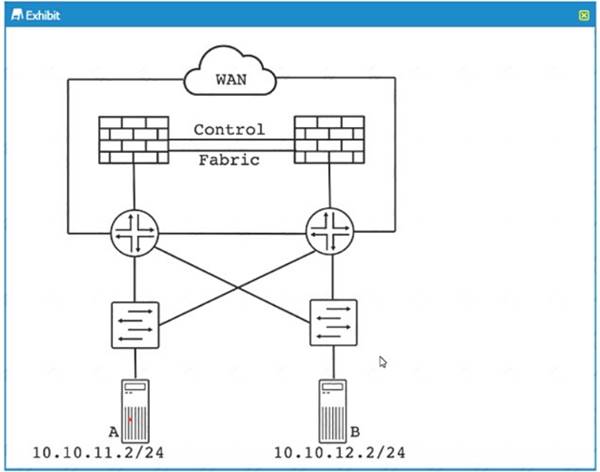
The SRX Series devices are decoyed in an off-path active/passive Cluster configuration
What are two advantages of this deployment model over an active-'active duster configuration' (Choose two)
- A. load-balancing of east/west traffic
- B. load-balancing of north/south traffic
- C. reduced latency
- D. reduced fabric link traffic
Answer: CD
NEW QUESTION 14
A new virus is sheading across the Internet, with the potential to affect your customer's network
Which two statements describe how Policy Enforcer interacts with other devices to ensure that the network is protected in this scenario? (Choose two.)
- A. Policy Enforcer pulls security intelligence feeds from Juniper ATP Cloud to apply to SRX Series devices
- B. Policy Enforcer pulls security policies from Juniper ATP cloud and apples them to SRX Series devices
- C. Policy Enforcer automates the enrollment of SRX Series devices with Jumper ATP Cloud
- D. Security Director pulls security intelligence feeds from Juniper ATP Cloud and applies them to Policy Enforcer
Answer: B
NEW QUESTION 15
You are designing a service provider network. As part of your design you must ensure that the OSPF, BGP, and RSVP protocol communications are secured using the same authentication method. Which authentication protocol will accomplish this task?
- A. HMAC-MD5
- B. simple authentication
- C. SHA-RSA
- D. SHA-256
Answer: B
NEW QUESTION 16
As part of your design to secure a service provider WAN. you are asked to design a destination-based remote triggered black hole (RTBH) solution What arc two reasons for using this design? (Choose two)
- A. The attack is focused on a single IP address
- B. You do not know the source address of DDoS packets
- C. The attack comes from a limited number of source IP addresses
- D. You want to ensure that the destination IP remains reachable
Answer: D
NEW QUESTION 17
......
Thanks for reading the newest JN0-1332 exam dumps! We recommend you to try the PREMIUM Certleader JN0-1332 dumps in VCE and PDF here: https://www.certleader.com/JN0-1332-dumps.html (65 Q&As Dumps)
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (51-60)
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (61-70)
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (71-80)
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (171-180)
- [2021-New] Juniper JN0-633 Dumps With Update Exam Questions (41-50)
- What Realistic JN0-1332 Free Exam Is
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (171-180)
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (91-100)
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (101-110)
- [2021-New] Juniper JN0-633 Dumps With Update Exam Questions (91-100)

