NSE4_FGT-6.4 Exam Questions - Online Test
NSE4_FGT-6.4 Premium VCE File

150 Lectures, 20 Hours

We provide real NSE4_FGT-6.4 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass Fortinet NSE4_FGT-6.4 Exam quickly & easily. The NSE4_FGT-6.4 PDF type is available for reading and printing. You can print more and practice many times. With the help of our Fortinet NSE4_FGT-6.4 dumps pdf and vce product and material, you can easily pass the NSE4_FGT-6.4 exam.
Online NSE4_FGT-6.4 free questions and answers of New Version:
NEW QUESTION 1
View the exhibit: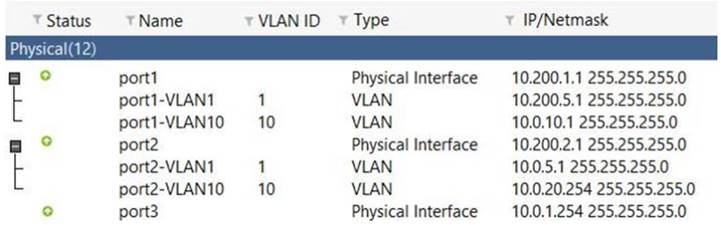
Which the FortiGate handle web proxy traffic rue? (Choose two.)
- A. Broadcast traffic received in port1-VLAN10 will not be forwarded to port2-VLAN10.
- B. port-VLAN1 is the native VLAN for the port1 physical interface.
- C. port1-VLAN10 and port2-VLAN10 can be assigned to different VDOMs.
- D. Traffic between port1-VLAN1 and port2-VLAN1 is allowed by default.
Answer: AC
NEW QUESTION 2
Which certificate value can FortiGate use to determine the relationship between the issuer and the certificate?
- A. Subject Key Identifiervalue
- B. SMMIE Capabilitiesvalue
- C. Subjectvalue
- D. Subject Alternative Namevalue
Answer: C
NEW QUESTION 3
Why does FortiGate keep TCP sessions in the session table for some seconds even after both sides (client and server) have terminated the session?
- A. To remove the NAT operation.
- B. To generate logs
- C. To finish any inspection operations.
- D. To allow for out-of-order packets that could arrive after the FIN/ACK packets.
Answer: D
NEW QUESTION 4
Refer to the exhibit.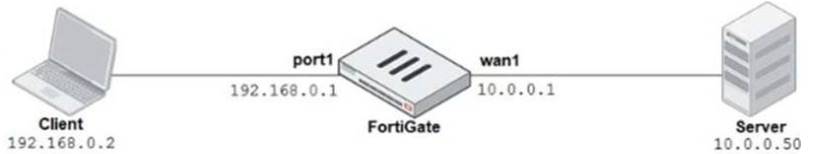
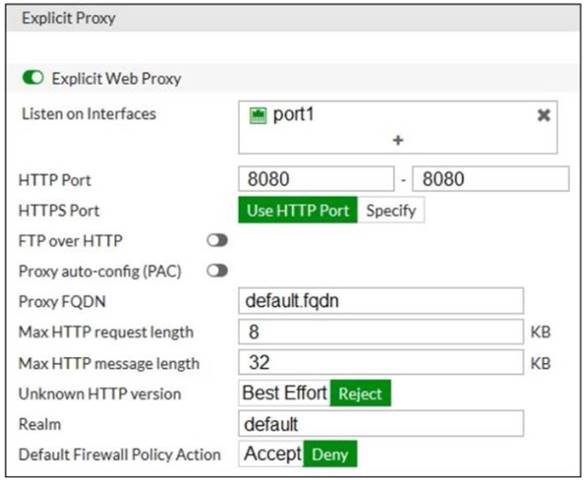
The exhibits show a network diagram and the explicit web proxy configuration.
In the commanddiagnose sniffer packet, what filter can you use to capture the traffic between the client and the explicit web proxy?
- A. ‘host 192.168.0.2 and port 8080’
- B. ‘host 10.0.0.50 and port 80’
- C. ‘host 192.168.0.1 and port 80’
- D. ‘host 10.0.0.50 and port 8080’
Answer: A
NEW QUESTION 5
Which statement about the IP authentication header (AH) used by IPsec is true?
- A. AH does not provide any data integrity or encryption.
- B. AH does not support perfect forward secrecy.
- C. AH provides data integrity bur no encryption.
- D. AH provides strong data integrity but weak encryption.
Answer: C
NEW QUESTION 6
Which three statements about a flow-based antivirus profile are correct? (Choose three.)
- A. IPS engine handles the process as a standalone.
- B. FortiGate buffers the whole file but transmits to the client simultaneously.
- C. If the virus is detected, the last packet is delivered to the client.
- D. Optimized performance compared to proxy-based inspection.
- E. Flow-based inspection uses a hybrid of scanning modes available in proxy-based inspection.
Answer: CDE
NEW QUESTION 7
Which two protocol options are available on the CLI but not on the GUI when configuring an SD-WAN Performance SLA? (Choose two.)
- A. DNS
- B. ping
- C. udp-echo
- D. TWAMP
Answer: AC
NEW QUESTION 8
Refer to the exhibit.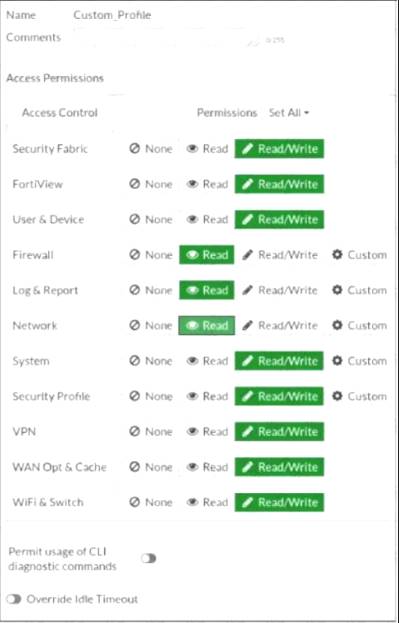
Based on the administrator profile settings, what permissions must the administrator set to run the diagnose firewall auth list CLI command on FortiGate?
- A. Custom permission for Network
- B. Read/Write permission for Log & Report
- C. CLI diagnostics commands permission
- D. Read/Write permission for Firewall
Answer: A
NEW QUESTION 9
Which statement regarding the firewall policy authentication timeout is true?
- A. It is an idle timeou
- B. The FortiGate considers a user to be “idle” if it does not see any packets coming from the user’s source IP.
- C. It is a hard timeou
- D. The FortiGate removes the temporary policy for a user’s source IP address after this timer has expired.
- E. It is an idle timeou
- F. The FortiGate considers a user to be “idle” if it does not see any packets coming from the user’s source MAC.
- G. It is a hard timeou
- H. The FortiGate removes the temporary policy for a user’s source MAC address after this timer has expired.
Answer: A
NEW QUESTION 10
A network administrator is configuring a new IPsec VPN tunnel on FortiGate. The remote peer IP address is dynamic, in addition, the remote peer does not support a dynamic DNS update service. What type of remote gateway should tie administrator configure on FortiGate for the new IPsec VPN tunnel to work?
- A. Static IP Address
- B. Dialup User
- C. Dynamic DNS
- D. Pre-shared Key
Answer: C
NEW QUESTION 11
What types of traffic and attacks can be blocked by a web application firewall (WAF) profile? (Choose three.)
- A. Traffic to botnetservers
- B. Traffic to inappropriate web sites
- C. Server information disclosure attacks
- D. Credit card data leaks
- E. SQL injection attacks
Answer: ACE
NEW QUESTION 12
Which two statements are correct regarding FortiGate FSSO agentless polling mode? (Choose two.)
- A. FortiGate points the collector agent to use a remote LDAP server.
- B. FortiGate uses the AD server as the collector agent.
- C. FortiGate uses the SMB protocol to read the event viewer logs from the DCs.
- D. FortiGate queries AD by using the LDAP to retrieve user group information.
Answer: CD
NEW QUESTION 13
Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
- A. The collector agent uses a Windows API to query DCs for user logins.
- B. NetAPI polling can increase bandwidth usage in large networks.
- C. The collector agent must search security event logs.
- D. The NetSessionEnum functionis user] to track user logouts.
Answer: A
NEW QUESTION 14
Refer to the exhibit.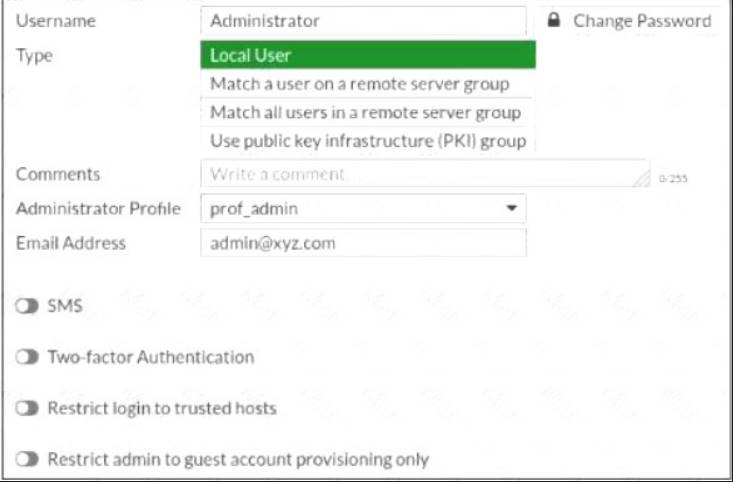
The global settings on a FortiGate device must be changed to align with company security policies. What does the Administrator account need to access the FortiGate global settings?
- A. Change password
- B. Enable restrict access to trusted hosts
- C. Change Administrator profile
- D. Enable two-factor authentication
Answer: D
NEW QUESTION 15
View the exhibit.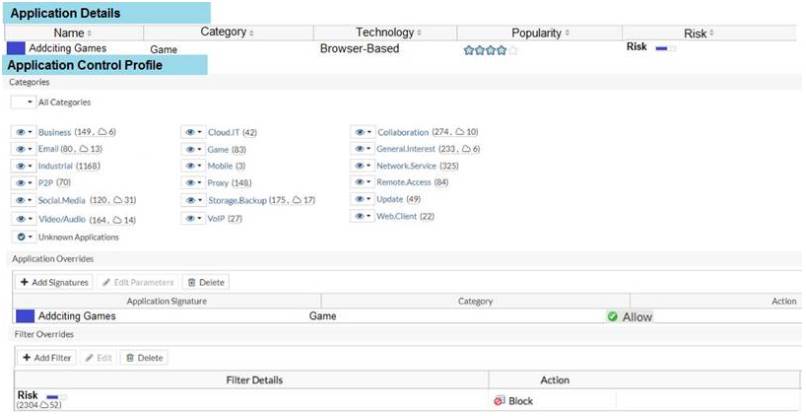
A user behind the FortiGate is trying to go to http://www.addictinggames.com (Addicting Games). Based on this configuration, which statement is true?
- A. Addicting.Games is allowed based on the Application Overrides configuration.
- B. Addicting.Games is blocked on the Filter Overrides configuration.
- C. Addicting.Games can be allowed only if the Filter Overrides actions is set to Exempt.
- D. Addcting.Games is allowed based on the Categories configuration.
Answer: A
NEW QUESTION 16
Refer to the web filter raw logs.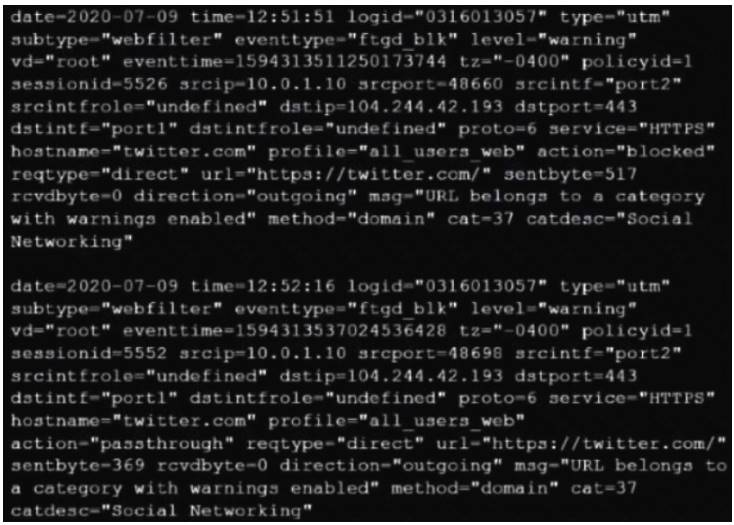
Based on the raw logs shown in the exhibit, which statement is correct?
- A. Social networking web filter category is configured with the action set to authenticate.
- B. The action on firewall policy ID 1 is set to warning.
- C. Access to the social networking web filter category was explicitly blocked to all users.
- D. The name of the firewall policy is all_users_web.
Answer: D
NEW QUESTION 17
Which two statements about antivirus scanning mode are true? (Choose two.)
- A. In proxy-based inspection mode, files bigger than the buffer size are scanned.
- B. In flow-based inspection mod
- C. FortiGate buffers the file, but also simultaneously transmits it to the client.
- D. In proxy-based inspection mode, antivirus scanning buffers the whole file for scanning, before sending it to the client.
- E. In flow-based inspection mode, files bigger than the buffer size are scanned.
Answer: CD
NEW QUESTION 18
Refer to the exhibit.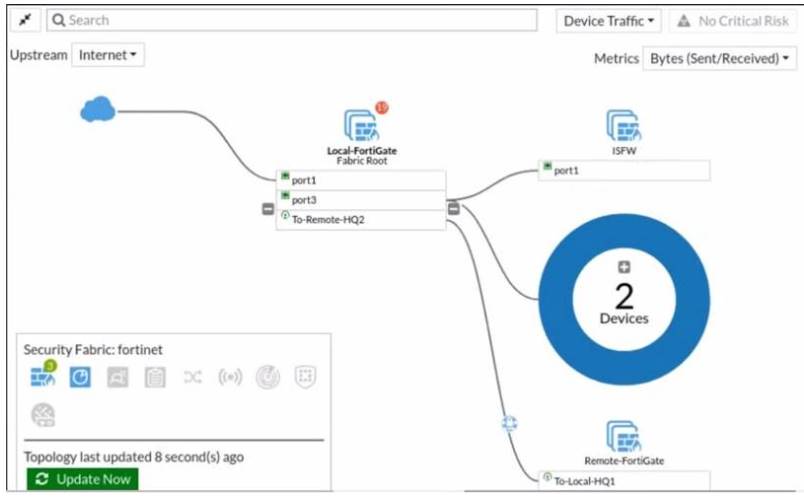
Given the security fabric topology shown in the exhibit, which two statements are true? (Choose two.)
- A. This security fabric topology is a logical topology view.
- B. There are 19 security recommendations for the security fabric.
- C. There are five devices that are part of the security fabric.
- D. Device detection is disabled on all FortiGate devices.
Answer: AD
NEW QUESTION 19
Refer to the exhibit showing a debug flow output.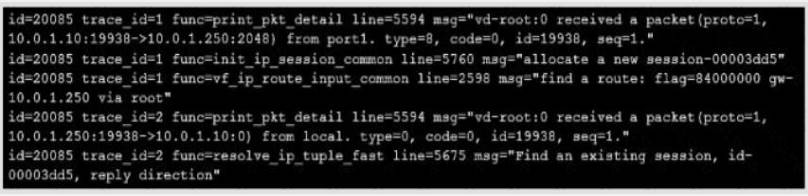
Which two statements about the debug flow output are correct? (Choose two.)
- A. The debug flow is of ICMP traffic.
- B. A firewall policy allowed the connection.
- C. A new traffic session is created.
- D. The default route is required to receive a reply.
Answer: B
NEW QUESTION 20
Which statements best describe auto discovery VPN (ADVPN). (Choose two.)
- A. It requires the use of dynamic routing protocols so that spokes can learn the routes to other spokes.
- B. ADVPN is only supported with IKEv2.
- C. Tunnels are negotiated dynamically between spokes.
- D. Every spoke requires a static tunnel to be configured to other spokes so that phase 1 and phase 2 proposals are defined in advance.
Answer: AC
NEW QUESTION 21
Which of the following SD-WAN load –balancing method use interface weight value to distribute traffic? (Choose two.)
- A. Source IP
- B. Spillover
- C. Volume
- D. Session
Answer: CD
NEW QUESTION 22
......
P.S. Dumps-hub.com now are offering 100% pass ensure NSE4_FGT-6.4 dumps! All NSE4_FGT-6.4 exam questions have been updated with correct answers: https://www.dumps-hub.com/NSE4_FGT-6.4-dumps.html (94 New Questions)
- [2021-New] Fortinet NSE4 Dumps With Update Exam Questions (61-66)
- Top Tips Of Renewal NSE5_FMG-6.0 Pdf Exam
- Up To The Immediate Present NSE4_FGT-6.4 Exam For Fortinet NSE 4 - FortiOS 6.4 Certification
- [2021-New] Fortinet NSE4 Dumps With Update Exam Questions (61-66)
- [2021-New] Fortinet NSE7 Dumps With Update Exam Questions (1-10)
- [2021-New] Fortinet NSE7 Dumps With Update Exam Questions (1-10)
- [2021-New] Fortinet NSE5 Dumps With Update Exam Questions (21-30)
- [2021-New] Fortinet NSE5 Dumps With Update Exam Questions (51-60)
- [2021-New] Fortinet NSE4 Dumps With Update Exam Questions (51-60)
- All About Realistic NSE6_FAC-6.4 Free Samples

