PCCSA Exam Questions - Online Test
PCCSA Premium VCE File

150 Lectures, 20 Hours

we provide Approved Paloalto-Networks PCCSA free exam questions which are the best for clearing PCCSA test, and to get certified by Paloalto-Networks Palo Alto Networks Certified Cybersecurity Associate. The PCCSA Questions & Answers covers all the knowledge points of the real PCCSA exam. Crack your Paloalto-Networks PCCSA Exam with latest dumps, guaranteed!
Also have PCCSA free dumps questions for you:
NEW QUESTION 1
Which type of attack floods a target with TCP SYN requests?
- A. route table poisoning
- B. reconaissance
- C. denial-of-service
- D. IP spoofing
Answer: C
NEW QUESTION 2
Which data security compliance standard is used to protect card holder data wherever it is processed, stored, or transmitted?
- A. Property Card Industry
- B. Payment Card Industry
- C. Personal Card Industry
- D. Payment Club Industry
Answer: B
NEW QUESTION 3
In which type of cloud computing service does an organization own and control application data, but not the application?
- A. platform as a service
- B. computing as a service
- C. infrastructure as a service
- D. software as a service
Answer: D
NEW QUESTION 4
You discover an infected email attachment that contains software code that attacks a known vulnerability in a popular social networking application. This type of software code belongs to which type of malware category?
- A. social engineering
- B. virus
- C. pharming
- D. exploit
Answer: D
NEW QUESTION 5
Which security component should be used to prevent a malware attack delivered by USB drive?
- A. endpoint security
- B. password security
- C. physical security
- D. firewall security
Answer: C
NEW QUESTION 6
Which two items operate at the network layer in the OSI network model? (Choose two.)
- A. IP address
- B. router
- C. switch
- D. MAC address
Answer: AB
NEW QUESTION 7
Review the exhibit and identify the type of vulnerability or attack that is commonly used against this technology.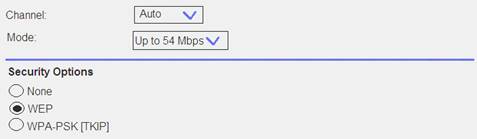
- A. phishing
- B. denial-of-service
- C. code-injection
- D. password cracking
Answer: D
NEW QUESTION 8
Company policy allows employees to access the internet. While searching for office supplies on the internet, a corporate user mistypes a URL, connects to a malicious website, and unknowingly downloads malware.
Which action should have been taken to prevent the malware download but still allow user access to the internet?
- A. deploy a firewall with content filtering capabilities on the corporate perimeter
- B. allow only encrypted HTTPS access to the internet
- C. configure digital certificates for all users to authenticate internet downloads
- D. permit web connections only to TCP port 443
Answer: A
NEW QUESTION 9
Which option lists the correct sequence of a TCP three-way handshake?
- A. SYN, ACK, SYN
- B. SYN, SYN+ACK, ACK
- C. SYN, ACK, FIN
- D. SYN, SYN+ACK, FIN
Answer: B
NEW QUESTION 10
Which two types of SaaS applications are allowed by an IT department? (Choose two.)
- A. tolerated
- B. certified
- C. sanctioned
- D. unsanctioned
Answer: AC
NEW QUESTION 11
Which option describes a characteristic of a distributed denial-of-service attack?
- A. uses multiple types of malware to corrupt system services
- B. uses a single remote host to delete data from multiple target servers
- C. uses a single remote host to flood a target network with traffic
- D. uses a botnet to flood traffic to a target network
Answer: D
NEW QUESTION 12
Match the task for server settings in group mapping with its order in the process.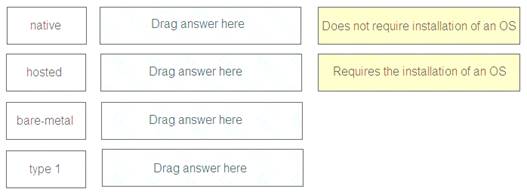
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Native – Requires the installation of an OS Hosted – Requires the installation of an OS
Bare-metal – Does not require installation of an OS Type 1 – Does not require installation of an OS
NEW QUESTION 13
Match the Palo Alto Networks Wild Fire analysis verdict with its definition.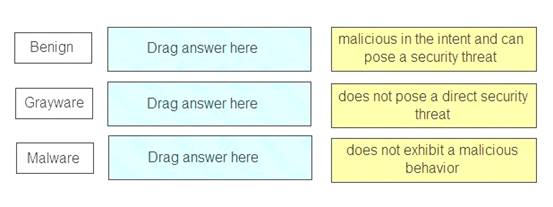
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Benign – does not exhibit a malicious behavior Grayware – does not pose a direct security threat
Malware – malicious in the intent and can pose a security threat References:
NEW QUESTION 14
Which type of malware is self-replicating but must first infect a host program and be executed by a user or process?
- A. vulnerability
- B. worm
- C. exploit
- D. virus
Answer: B
NEW QUESTION 15
Which type of firewall monitors traffic streams from beginning to end?
- A. circuit-level gateway
- B. stateless
- C. stateful
- D. packet filter
Answer: C
NEW QUESTION 16
What is a component of a public key infrastructure?
- A. Key Distribution Center
- B. KDC ticket
- C. SSH key
- D. certificate authority
Answer: D
NEW QUESTION 17
Which protocol converts voice into a digital signal?
- A. IVO
- B. VoIP
- C. SNMP
- D. IGMP
Answer: B
NEW QUESTION 18
Which Palo Alto Networks tool is used to prevent endpoint systems from running malware executables such as viruses, trojans and rootkits?
- A. AutoFocus
- B. Traps
- C. Expedition
- D. App-ID
Answer: B
NEW QUESTION 19
Which security principle describes the practice of giving users the minimum rights to access the resources necessary to do their jobs?
- A. known privilege
- B. least privilege
- C. user privilege
- D. lowest privilege
Answer: B
NEW QUESTION 20
Which type of adversary would commit cybercrimes with the authorization of their country’s government?
- A. state-sponsored
- B. hacktivist
- C. gray hat
- D. white hat
Answer: A
NEW QUESTION 21
......
100% Valid and Newest Version PCCSA Questions & Answers shared by Dumpscollection.com, Get Full Dumps HERE: https://www.dumpscollection.net/dumps/PCCSA/ (New 50 Q&As)

