PCNSE7 Exam Questions - Online Test
PCNSE7 Premium VCE File

150 Lectures, 20 Hours

It is more faster and easier to pass the by using . Immediate access to the and find the same core area with professionally verified answers, then PASS your exam with a high score now.
Online Paloalto Networks PCNSE7 free dumps demo Below:
NEW QUESTION 1
What are two benefits of nested device groups in Panorama? (Choose two.)
- A. Reuse of the existing Security policy rules and objects
- B. Requires configuring both function and location for every device
- C. All device groups inherit settings form the Shared group
- D. Overwrites local firewall configuration
Answer: BC
NEW QUESTION 2
Which URL Filtering Security Profile action logs the URL Filtering category to the URL Filtering log?
- A. Log
- B. Alert
- C. Allow
- D. Default
Answer: B
Explanation: https://www.paloaltonetworks.com/documentation/70/pan-os/pan-os/url- filtering/url-filtering-profile-actions
NEW QUESTION 3
During the packet flow process, which two processes are performed in application identification? (Choose two.)
- A. Pattern based application identification
- B. Application override policy match
- C. Application changed from content inspection
- D. Session application identified.
Answer: BD
NEW QUESTION 4
Click the Exhibit button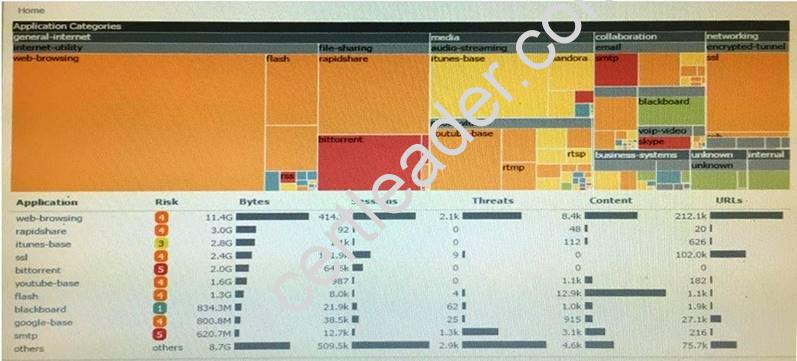
An administrator has noticed a large increase in bittorrent activity. The administrator wants to determine where the traffic is going on the company.
What would be the administrator's next step?
- A. Right-Click on the bittorrent link and select Value from the context menu
- B. Create a global filter for bittorrent traffic and then view Traffic logs.
- C. Create local filter for bittorrent traffic and then view Traffic logs.
- D. Click on the bittorrent application link to view network activity
Answer: D
NEW QUESTION 5
A host attached to ethernet1/3 cannot access the internet. The default gateway is attached to ethernet1/4. After troubleshooting. It is determined that traffic cannot pass from the ethernet1/3 to ethernet1/4. What can be the cause of the problem?
- A. DHCP has been set to Auto.
- B. Interface ethernet1/3 is in Layer 2 mode and interface ethernet1/4 is in Layer 3 mode.
- C. Interface ethernet1/3 and ethernet1/4 are in Virtual Wire Mode.
- D. DNS has not been properly configured on the firewall
Answer: B
NEW QUESTION 6
When a malware-infected host attempts to resolve a known command-and-control server, the traffic matches a security policy with DNS sinhole enabled, generating a traffic log.
What will be the destination IP Address in that log entry?
- A. The IP Address of sinkhole.paloaltonetworks.com
- B. The IP Address of the command-and-control server
- C. The IP Address specified in the sinkhole configuration
- D. The IP Address of one of the external DNS servers identified in the anti-spyware database
Answer: C
Explanation: https://live.paloaltonetworks.com/t5/Management-Articles/How-to-Verify-DNS-Sinkhole-Function-is-Working/ta-p/65864
NEW QUESTION 7
Refer to exhibit.
An organization has Palo Alto Networks NGFWs that send logs to remote monitoring and security management platforms. The network team has reported excessive traffic on the corporate WAN.
How could the Palo Alto Networks NGFW administrator reduce WAN traffic while maintaining support for all existing monitoring platforms?
- A. Forward logs from firewalls only to Panorama and have Panorama forward logs to other external services.
- B. Forward logs from external sources to Panorama for correlation, and from Panorama send them to the NGFW.
- C. Configure log compression and optimization features on all remote firewalls.
- D. Any configuration on an M-500 would address the insufficient bandwidth concerns.
Answer: C
NEW QUESTION 8
In a virtual router, which object contains all potential routes?
- A. MIB
- B. RIB
- C. SIP
- D. FIB
Answer: B
NEW QUESTION 9
When configuring a GlobalProtect Portal, what is the purpose of specifying an Authentication Profile?
- A. To enable Gateway authentication to the Portal
- B. To enable Portal authentication to the Gateway
- C. To enable user authentication to the Portal
- D. To enable client machine authentication to the Portal
Answer: C
Explanation: The additional options of Browser and Satellite enable you to specify the authentication profile to use for specific scenarios. Select Browser to specify the authentication profile to use to authenticate a user accessing the portal from a web browser with the intent of downloading the GlobalProtect agent (Windows and Mac). Select Satellite to specify the authentication profile to use to authenticate the satellite. Referencehttps://www.paloaltonetworks.com/documentation/71/pan-os/web-interface-help/globalprotect/network-globalprotect-portals
NEW QUESTION 10
A company has a web server behind a Palo Alto Networks next-generation firewall that it wants to make accessible to the public at 1.1.1.1. The company has decided to configure a destination NAT Policy rule.
Given the following zone information:
•DMZ zone: DMZ-L3
•Public zone: Untrust-L3
•Guest zone: Guest-L3
•Web server zone: Trust-L3
•Public IP address (Untrust-L3): 1.1.1.1
•Private IP address (Trust-L3): 192.168.1.50
What should be configured as the destination zone on the Original Packet tab of NAT Policy rule?
- A. Untrust-L3
- B. DMZ-L3
- C. Guest-L3
- D. Trust-L3
Answer: A
NEW QUESTION 11
Which three file types can be forwarded to WildFire for analysis as a part of the basic WildFire service? (Choose three.)
- A. .dll
- B. .exe
- C. .src
- D. .apk
- E. .pdf
- F. .jar
Answer: DEF
NEW QUESTION 12
An administrator encountered problems with inbound decryption. Which option should the administrator investigate as part of triage?
- A. Security policy rule allowing SSL to the target server
- B. Firewall connectivity to a CRL
- C. Root certificate imported into the firewall with “Trust” enabled
- D. Importation of a certificate from an HSM
Answer: A
NEW QUESTION 13
A firewall administrator has completed most of the steps required to provision a standalone Palo Alto Networks Next-Generation Firewall. As a final step, the administrator wants to test one of the security policies.
Which CLI command syntax will display the rule that matches the test?
- A. test security -policy- match source <ip_address> destination <IP_address> destination port <port number> protocol <protocol number
- B. show security rule source <ip_address> destination <IP_address> destination port <portnumber> protocol <protocol number>
- C. test security rule source <ip_address> destination <IP_address> destination port <port number> protocol <protocol number>
- D. show security-policy-match source <ip_address> destination <IP_address> destination port <port number> protocol <protocol number>test security-policy-match source
Answer: A
Explanation: test security-policy-match source <source IP> destination <destination IP> protocol <protocol number>
https://live.paloaltonetworks.com/t5/Management-Articles/How-to-Test-Which-Security- Policy-Applies-to-a-Traffic-Flow/ta-p/53693
NEW QUESTION 14
Only two Trust to Untrust allow rules have been created in the Security policy Rule1 allows google-base
Rule2 allows youtube-base
The youtube-base App-ID depends on google-base to function. The google-base App-ID implicitly uses SSL and web-browsing. When user try to accesss https://www.youtube.com in a web browser, they get an error indecating that the server cannot be found.
Which action will allow youtube.com display in the browser correctly?
- A. Add SSL App-ID to Rule1
- B. Create an additional Trust to Untrust Rule, add the web-browsing, and SSL App-ID's to it
- C. Add the DNS App-ID to Rule2
- D. Add the Web-browsing App-ID to Rule2
Answer: C
NEW QUESTION 15
An administrator has left a firewall to use the default port for all management services. Which three functions are performed by the dataplane? (Choose three.)
- A. WildFire updates
- B. NAT
- C. NTP
- D. antivirus
- E. File blocking
Answer: ABC
NEW QUESTION 16
Palo Alto Networks maintains a dynamic database of malicious domains.
Which two Security Platform components use this database to prevent threats? (Choose two)
- A. Brute-force signatures
- B. BrightCloud Url Filtering
- C. PAN-DB URL Filtering
- D. DNS-based command-and-control signatures
Answer: CD
Recommend!! Get the Full PCNSE7 dumps in VCE and PDF From 2passeasy, Welcome to Download: https://www.2passeasy.com/dumps/PCNSE7/ (New 176 Q&As Version)
- Paloalto Networks PCNSE7 Exam Questions and Answers 2021
- [2021-New] Paloalto Networks PCNSE6 Dumps With Update Exam Questions (31-40)
- Approved PCNSE7 Free Practice Questions 2021
- [2021-New] Paloalto Networks PCNSE6 Dumps With Update Exam Questions (51-60)
- [2021-New] Paloalto Networks PCNSE6 Dumps With Update Exam Questions (61-70)
- Paloalto Networks PCNSE7 Dumps 2021
- [2021-New] Paloalto Networks PCNSE6 Dumps With Update Exam Questions (1-10)
- Certified PCNSE7 Braindumps 2021
- [2021-New] Paloalto Networks PCNSE6 Dumps With Update Exam Questions (11-20)
- Realistic PCNSE7 Exam Questions and Answers 2021

