SAP-C01 Exam Questions - Online Test
SAP-C01 Premium VCE File

150 Lectures, 20 Hours

Your success in Amazon-Web-Services SAP-C01 is our sole target and we develop all our SAP-C01 braindumps in a way that facilitates the attainment of this target. Not only is our SAP-C01 study material the best you can find, it is also the most detailed and the most updated. SAP-C01 Practice Exams for Amazon-Web-Services Amazon-Web-Services Other Exam SAP-C01 are written to the highest standards of technical accuracy.
Also have SAP-C01 free dumps questions for you:
NEW QUESTION 1
A Solutions Architect is designing a multi-account structure that has 10 existing accounts. The design must meet the following requirements: Consolidate all accounts into one organization.
Consolidate all accounts into one organization. Allow full access to the Amazon EC2 service from the master account and the secondary accounts.
Allow full access to the Amazon EC2 service from the master account and the secondary accounts.  Minimize the effort required to add additional secondary accounts.
Minimize the effort required to add additional secondary accounts.
Which combination of steps should be included in the solution? (Choose two.)
- A. Create an organization from the master accoun
- B. Send invitations to the secondary accounts from the master accoun
- C. Accept the invitations and create an OU.
- D. Create an organization from the master accoun
- E. Send a join request to the master account from each secondary accoun
- F. Accept the requests and create an OU.
- G. Create a VPC peering connection between the master account and the secondary account
- H. Accept the request for the VPC peering connection.
- I. Create a service control policy (SCP) that enables full EC2 access, and attach the policy to the OU.
- J. Create a full EC2 access policy and map the policy to a role in each accoun
- K. Trust every other account to assume the role.
Answer: AD
Explanation:
There is a concept of Permission Boundary vs Actual IAM Policies That is, we have a concept of "Allow" vs "Grant". In terms of boundaries, we have the following three boundaries: 1. SCP 2. User/Role boundaries 3. Session boundaries (ex. AssumeRole ... ) In terms of actual permission granting, we have the following: 1. Identity Policies 2. Resource Policies
NEW QUESTION 2
A company has deployed an application to multiple environments in AWS, including production and testing. The company has separate accounts for production and testing, and users are allowed to create additional application users for team members or services, as needed. The Security team has asked the Operations team for better isolation between production and testing with centralized controls on security credentials and improved management of permissions between environments.
Which of the following options would MOST securely accomplish this goal?
- A. Create a new AWS account to hold user and service accounts, such as an identity accoun
- B. Create users and groups in the identity accoun
- C. Create roles with appropriate permissions in the production and testing account
- D. Add the identity account to the trust policies for the roles.
- E. Modify permissions in the production and testing accounts to limit creating new IAM users to members of the Operations tea
- F. Set a strong IAM password policy on each accoun
- G. Create new IAM users and groups in each account to limit developer access to just the services required to complete their job function.
- H. Create a script that runs on each account that checks user accounts for adherence to a security policy.Disable any user or service accounts that do not comply.
- I. Create all user accounts in the production accoun
- J. Create roles for access in the production account and testing account
- K. Grant cross-account access from the production account to the testing account.
Answer: A
Explanation:
https://aws.amazon.com/blogs/security/how-to-centralize-and-automate-iam-policy-creation-in-sandbox-develop
NEW QUESTION 3
A company is adding a new approved external vendor that only supports IPv6 connectivity. The company’s backend systems sit in the private subnet of an Amazon VPC. The company uses a NAT gateway to allow these systems to communicate with external vendors over IPv4. Company policy requires systems that communicate with external vendors use a security group that limits access to only approved external vendors. The virtual private cloud (VPC) uses the default network ACL.
The Systems Operator successfully assigns IPv6 addresses to each of the backend systems. The Systems Operator also updates the outbound security group to include the IPv6 CIDR of the external vendor (destination). The systems within the VPC are able to ping one another successfully over IPv6. However, these systems are unable to communicate with the external vendor.
What changes are required to enable communication with the external vendor?
- A. Create an IPv6 NAT instanc
- B. Add a route for destination 0.0.0.0/0 pointing to the NAT instance.
- C. Enable IPv6 on the NAT gatewa
- D. Add a route for destination ::/0 pointing to the NAT gateway.
- E. Enable IPv6 on the internet gatewa
- F. Add a route for destination 0.0.0.0/0 pointing to the IGW.
- G. Create an egress-only internet gatewa
- H. Add a route for destination ::/0 pointing to the gateway.
Answer: D
Explanation:
https://docs.aws.amazon.com/vpc/latest/userguide/egress-only-internet-gateway.html
NEW QUESTION 4
A company runs a dynamic mission-critical web application that has an SLA of 99.99%. Global application users access the application 24/7. The application is currently hosted on premises and routinely fails to meet its SLA, especially when millions of users access the application concurrently. Remote users complain of latency.
How should this application be redesigned to be scalable and allow for automatic failover at the lowest cost?
- A. Use Amazon Route 53 failover routing with geolocation-based routin
- B. Host the website on automatically scaled Amazon EC2 instances behind an Application Load Balancer with an additional Application Load Balancer and EC2 instances for the application layer in each regio
- C. Use a Multi-AZ deployment with MySQL as the data layer.
- D. Use Amazon Route 53 round robin routing to distribute the load evenly to several regions with health check
- E. Host the website on automatically scaled Amazon ECS with AWS Fargate technology containers behind a Network Load Balancer, with an additional Network Load Balancer and Fargate containers for the application layer in each regio
- F. Use Amazon Aurora replicas for the data layer.
- G. Use Amazon Route 53 latency-based routing to route to the nearest region with health check
- H. Host the website in Amazon S3 in each region and use Amazon API Gateway with AWS Lambda for the application laye
- I. Use Amazon DynamoDB global tables as the data layer with Amazon DynamoDB Accelerator (DAX) for caching.
- J. Use Amazon Route 53 geolocation-based routin
- K. Host the website on automatically scaled AWS Fargate containers behind a Network Load Balancer with an additional Network Load Balancer and Fargate containers for the application layer in each regio
- L. Use Amazon Aurora Multi-Master for Aurora MySQL as the data layer.
Answer: C
Explanation:
https://aws.amazon.com/getting-started/projects/build-serverless-web-app-lambda-apigateway-s3-dynamodb-co
NEW QUESTION 5
A company is building an AWS landing zone and has asked a Solutions Architect to design a multi-account access strategy that will allow hundreds of users to use corporate credentials to access the AWS Console. The company is running a Microsoft Active Directory and users will use an AWS Direct Connect connection to connect to AWS. The company also wants to be able to federate to third-party services and providers, including custom applications.
Which solution meets the requirements by using the LEAST amount of management overhead?
- A. Connect the Active Directory to AWS by using single sign-on and an Active Directory Federation Services (AD FS) with SAML 2.0, and then configure the identity Provider (IdP) system to use form-based authenticatio
- B. Build the AD FS portal page with corporate branding, and integrate third-party applications that support SAML 2.0 as required.
- C. Create a two-way Forest trust relationship between the on-premises Active Directory and the AWS Directory Servic
- D. Set up AWS Single Sign-On with AWS Organization
- E. Use single sign-on integrations for connections with third-party applications.
- F. Configure single sign-on by connecting the on-premises Active Directory using the AWS Directory Service AD Connecto
- G. Enable federation to the AWS services and accounts by using the IAM applications and services linking functio
- H. Leverage third-party single sign-on as needed.
- I. Connect the company’s Active Directory to AWS by using AD FS and SAML 2.0. Configure the AD FS claim rule to leverage Regex and a common Active Directory naming convention for the security group to allow federation of all AWS account
- J. Leverage third-party single sign-on as needed, and add it to the AD FS server.
Answer: D
Explanation:
https://aws.amazon.com/blogs/security/aws-federated-authentication-with-active-directory-federation-services-a
NEW QUESTION 6
A company wants to ensure that the workloads for each of its business units have complete autonomy and a minimal blast radius in AWS. The Security team must be able to control access to the resources and services in the account to ensure that particular services are not used by the business units.
How can a Solutions Architect achieve the isolation requirements?
- A. Create individual accounts for each business unit and add the account to an OU in AWS Organizations.Modify the OU to ensure that the particular services are blocke
- B. Federate each account with an IdP, and create separate roles for the business units and the Security team.
- C. Create individual accounts for each business uni
- D. Federate each account with an IdP and create separate roles and policies for business units and the Security team.
- E. Create one shared account for the entire compan
- F. Create separate VPCs for each business uni
- G. Create individual IAM policies and resource tags for each business uni
- H. Federate each account with an IdP, and create separate roles for the business units and the Security team.
- I. Create one shared account for the entire compan
- J. Create individual IAM policies and resource tags for each business uni
- K. Federate the account with an IdP, and create separate roles for the business units and the Security team.
Answer: A
NEW QUESTION 7
A company is migrating an application to AWS. It wants to use fully managed services as much as possible during the migration. The company needs to store large, important documents within the application with the following requirements: The data must be highly durable and available.
The data must be highly durable and available. The data must always be encrypted at rest and in transit.
The data must always be encrypted at rest and in transit. The encryption key must be managed by the company and rotated periodically. Which of the following solutions should the Solutions Architect recommend?
The encryption key must be managed by the company and rotated periodically. Which of the following solutions should the Solutions Architect recommend?
- A. Deploy the storage gateway to AWS in file gateway mod
- B. Use Amazon EBS volume encryption using an AWS KMS key to encrypt the storage gateway volumes.
- C. Use Amazon S3 with a bucket policy to enforce HTTPS for connections to the bucket and to enforce server-side encryption and AWS KMS for object encryption.
- D. Use Amazon DynamoDB with SSL to connect to DynamoD
- E. Use an AWS KMS key to encrypt DynamoDB objects at rest.
- F. Deploy instances with Amazon EBS volumes attached to store this dat
- G. Use EBS volume encryption using an AWS KMS key to encrypt the data.
Answer: B
Explanation:
https://aws.amazon.com/blogs/security/how-to-use-bucket-policies-and-apply-defense-in-depth-to-help-secure-y
NEW QUESTION 8
A company has developed a new billing application that will be released in two weeks. Developers are testing the application running on 10 EC2 instances managed by an Auto Scaling group in subnet 172.31.0.0/24 within VPC A with CIDR block 172.31.0.0/16. The Developers noticed connection timeout errors in the application logs while connecting to an Oracle database running on an Amazon EC2 instance in the same region within VPC B with CIDR block 172.50.0.0/16. The IP of the database instance is hard-coded in the application instances.
Which recommendations should a Solutions Architect present to the Developers to solve the problem in a secure way with minimal maintenance and overhead?
- A. Disable the SrcDestCheck attribute for all instances running the application and Oracle Database.Change the default route of VPC A to point ENI of the Oracle Database that has an IP address assigned within the range of 172.50.0.0/26
- B. Create and attach internet gateways for both VPC
- C. Configure default routes to the Internet gateways for both VPC
- D. Assign an Elastic IP for each Amazon EC2 instance in VPC A
- E. Create a VPC peering connection between the two VPCs and add a route to the routing table of VPC A that points to the IP address range of 172.50.0.0/16
- F. Create an additional Amazon EC2 instance for each VPC as a customer gateway; create one virtual private gateway (VGW) for each VPC, configure an end-to-end VPC, and advertise the routes for 172.50.0.0/16
Answer: C
NEW QUESTION 9
A large company experienced a drastic increase in its monthly AWS spend. This is after Developers accidentally launched Amazon EC2 instances in unexpected regions. The company has established practices around least privileges for Developers and controls access to on-premises resources using Active Directory groups. The company now wants to control costs by restricting the level of access that Developers have to the AWS Management Console without impacting their productivity. The company would also like to allow Developers to launch Amazon EC2 in only one region, without limiting access to other services in any region.
How can this company achieve these new security requirements while minimizing the administrative burden on the Operations team?
- A. Set up SAML-based authentication tied to an IAM role that has an AdministrativeAccess managed policy attached to i
- B. Attach a customer managed policy that denies access to Amazon EC2 in each region except for the one required.
- C. Create an IAM user for each Developer and add them to the developer IAM group that has the PowerUserAccess managed policy attached to i
- D. Attach a customer managed policy that allows the Developers access to Amazon EC2 only in the required region.
- E. Set up SAML-based authentication tied to an IAM role that has a PowerUserAccess managed policy and a customer managed policy that deny all the Developers access to any AWS services except AWS Service Catalo
- F. Within AWS Service Catalog, create a product containing only the EC2 resources in the approved region.
- G. Set up SAML-based authentication tied to an IAM role that has the PowerUserAccess managed policy attached to i
- H. Attach a customer managed policy that denies access to Amazon EC2 in each region except for the one required.
Answer: D
Explanation:
The tricks here are: - SAML for AD federation and authentication - PowerUserAccess vs AdministrativeAccess. (PowerUSer has less privilege, which is the required once for developers). Admin, has more rights. The description of "PowerUser access" given by AWS is “Provides full access to AWS services and resources, but does not allow management of Users and groups.”
NEW QUESTION 10
A company is refactoring an existing web service that provides read and write access to structured data. The service must respond to short but significant spikes in the system load The service must be fault tolerant across multiple AWS Regions.
Which actions should be taken to meet these requirements?
- A. Store the data in Amazon DocumentDB Create a single global Amazon CloudFront distribution with a custom origin built on edge-optimized Amazon API Gateway and AWS Lambda Assign the company's domain as an alternate domain for the distributio
- B. and configure Amazon Route 53 with an alias to the CloudFront distribution
- C. Store the data in replicated Amazon S3 buckets in two Regions Create an Amazon CloudFront distribution in each Region, with custom origins built on Amazon API Gateway and AWS Lambda launched in each Region Assign the company's domain as an alternate domain for both distributions and configure Amazon Route 53 with a failover routing policy between them
- D. Store the data in an Amazon DynamoDB global table in two Regions using on-demand capacity mode In both Regions, run the web service as Amazon ECS Fargate tasks in an Auto Scaling ECS service behind an Application Load Balancer (ALB) In Amazon Route 53, configure an alias record in the company's domain and a Route 53 latency-based routing policy with health checks to distribute traffic between the two ALBs
Answer: A
NEW QUESTION 11
A company is designing a new highly available web application on AWS. The application requires consistent and reliable connectivity from the application servers in AWS to a backend REST API hosted in the company’s on-premises environment. The backend connection between AWS and on-premises will be routed over an AWS Direct Connect connection through a private virtual interface. Amazon Route 53 will be used to manage private DNS records for the application to resolve the IP address on the backend REST API.
Which design would provide a reliable connection to the backend API?
- A. Implement at least two backend endpoints for the backend REST API, and use Route 53 health checks to monitor the availability of each backend endpoint and perform DNS-level failover.
- B. Install a second Direct Connect connection from a different network carrier and attach it to the same virtual private gateway as the first Direct Connect connection.
- C. Install a second cross connect for the same Direct Connect connection from the same network carrier, and join both connections to the same link aggregation group (LAG) on the same private virtual interface.
- D. Create an IPSec VPN connection routed over the public internet from the on-premises data center to AWS and attach it to the same virtual private gateway as the Direct Connect connection.
Answer: A
NEW QUESTION 12
A company has a single AWS master billing account, which is the root of the AWS Organizations hierarchy. The company has multiple AWS accounts within this hierarchy, all organized into organization units (OUs). More OUS and AWS accounts will continue to be created as other parts of the business migrate applications to AWS. These business units may need to use different AWS services. The Security team is implementing the following requirements for all current and future AWS accounts.
* Control policies must be applied across all accounts to prohibit AWS servers.
* Exceptions to the control policies are allowed based on valid use cases. Which solution will meet these requirements with minimal optional overhead?
- A. Use an SCP in Organizations to implement a deny list of AWS server
- B. Apply this SCP at the leve
- C. For any specific exceptions for an OU, create a new SCP for that OU and add the required AWS services the allow list.
- D. Use an SCP In organizations to implement a deny list of AWS servic
- E. Apply this SCP at the root level and each O
- F. Remove the default AWS managed SCP from the root level and all OU level
- G. For any specific exceptions, modify the SCP attached to that OU, and add the required AWS required services to the allow list.
- H. Use an SCP in Organization to implement a deny list of AWS servic
- I. Apply this SCP at each OU leve
- J. Leave the default AWS managed SCP at the root level For any specific executions for an OU, create a new SCP for that OU.
- K. Use an SCP in Organizations to implement an allow list of AWS service
- L. Apply this SCP at the root leve
- M. Remove the default AWS managed SCP from the root level and all OU level
- N. For any specific exceptions for an OU, modify the SCP attached to that OU, and add the required AWS services to the allow list.
Answer: B
NEW QUESTION 13
A Development team is deploying new APIs as serverless applications within a company. The team is currently using the AWS Management Console to provision Amazon API Gateway, AWS Lambda, and Amazon DynamoDB resources. A Solutions Architect has been tasked with automating the future deployments of these serverless APIs.
How can this be accomplished?
- A. Use AWS CloudFormation with a Lambda-backed custom resource to provision API Gatewa
- B. Use the AWS::DynamoDB::Table and AWS::Lambda::Function resources to create the Amazon DynamoDB table and Lambda function
- C. Write a script to automate the deployment of the CloudFormation template.
- D. Use the AWS Serverless Application Model to define the resource
- E. Upload a YAML template and application files to the code repositor
- F. Use AWS CodePipeline to connect to the code repository and to create an action to build using AWS CodeBuil
- G. Use the AWS CloudFormation deployment provider in CodePipeline to deploy the solution.
- H. Use AWS CloudFormation to define the serverless applicatio
- I. Implement versioning on the Lambda functions and create aliases to point to the version
- J. When deploying, configure weights to implement shifting traffic to the newest version, and gradually update the weights as traffic moves over.
- K. Commit the application code to the AWS CodeCommit code repositor
- L. Use AWS CodePipeline and connect to the CodeCommit code repositor
- M. Use AWS CodeBuild to build and deploy the Lambda functions using AWS CodeDeplo
- N. Specify the deployment preference type in CodeDeploy to gradually shift traffic over to the new version.
Answer: B
Explanation:
https://aws-quickstart.s3.amazonaws.com/quickstart-trek10-serverless-enterprise-cicd/doc/serverless-cicd-for-th https://aws.amazon.com/quickstart/architecture/serverless-cicd-for-enterprise/
NEW QUESTION 14
A Solutions Architect needs to design a highly available application that will allow authenticated users to stay connected to the application even when there are underlying failures
Which solution will meet these requirements?
- A. Deploy the application on Amazon EC2 instances Use Amazon Route 53 to forward requests to the EC2 Instances Use Amazon DynamoDB to save the authenticated connection details
- B. Deploy the application on Amazon EC2 instances in an Auto Scaling group Use an internet-facing Application Load Balancer to handle requests Use Amazon DynamoDB to save the authenticated connection details
- C. Deploy the application on Amazon EC2 instances in an Auto Scaling group Use an internet-facing Application Load Balancer on the front end Use EC2 instances to save the authenticated connectiondetails
- D. Deploy the application on Amazon EC2 instances in an Auto Scaling group Use an internet-facing Application Load Balancer on the front end Use EC2 instances hosting a MySQL database to save the authenticated connection details
Answer: B
NEW QUESTION 15
During an audit a Security team discovered that a Development team was putting IAM user secret access keys in their code and then committing it to an AWS CodeCommit repository The Security team wants to automatically find and remediate instances of this security vulnerability
Which solution will ensure that the credentials are appropriately secured automatically?
- A. Run a script rightly using AWS Systems Manager Run Command to search (or credentials on thedevelopment instances It found, use AWS Secrets Manager to rotate the credentials
- B. Use a scheduled AWS Lambda function to download and scan the application code from CodeCommit If credentials are found generate new credentials and store them in AWS KMS
- C. Configure Amazon Macie to scan for credentials in CodeCommit repositories If credentials are found, trigger an AWS Lambda function to disable the credentials and notify the user
- D. Configure a CodeCommit trigger to invoke an AWS Lambda function to scan new code submissions for credentials lf credentials are found, disable them in AWS IAM and notify the user
Answer: C
NEW QUESTION 16
A company is using AWS to run an internet-facing production application written in Node.js. The Development team is responsible for pushing new versions of their software directly to production. The application software is updated multiple times a day. The team needs guidance from a Solutions Architect to help them deploy the software to the production fleet quickly and with the least amount of disruption to the service.
Which option meets these requirements?
- A. Prepackage the software into an AMI and then use Auto Scaling to deploy the production flee
- B. For software changes, update the AMI and allow Auto Scaling to automatically push the new AMI to production.
- C. Use AWS CodeDeploy to push the prepackaged AMI to productio
- D. For software changes, reconfigure CodeDeploy with new AMI identification to push the new AMI to the production fleet.
- E. Use AWS Elastic Beanstalk to host the production applicatio
- F. For software changes, upload the new application version to Elastic Beanstalk to push this to the production fleet using a blue/green deployment method.
- G. Deploy the base AMI through Auto Scaling and bootstrap the software using user dat
- H. For software changes, SSH to each of the instances and replace the software with the new version.
Answer: C
NEW QUESTION 17
An enterprise company is using a multi-account AWS strategy There are separate accounts tor development staging and production workloads To control costs and improve governance the following requirements have been defined:
• The company must be able to calculate the AWS costs tor each project
• The company must be able to calculate the AWS costs tor each environment development staging and production
• Commonly deployed IT services must be centrally managed
• Business units can deploy pre-approved IT services only
• Usage of AWS resources in the development account must be limited
Which combination of actions should be taken to meet these requirements? (Select THREE )
- A. Apply environment, cost center, and application name tags to all taggable resources
- B. Configure custom budgets and define thresholds using Cost Explorer
- C. Configure AWS Trusted Advisor to obtain weekly emails with cost-saving estimates
- D. Create a portfolio for each business unit and add products to the portfolios using AWS CloudFormation in AWS Service Catalog
- E. Configure a billing alarm in Amazon CloudWatch.
- F. Configure SCPs in AWS Organizations to allow services available using AWS
Answer: CEF
NEW QUESTION 18
A company wants to manage the costs associated with a group of 20 applications that are critical, by migrating to AWS. The applications are a mix of Java and Node.js spread across different instance clusters. The company wants to minimize costs while standardizing by using a single deployment methodology. Most of the applications are part of month-end processing routines with a small number of concurrent users, but they are occasionally run at other times. Average application memory consumption is less than 1 GB, though some applications use as much as 2.5 GB of memory during peak processing. The most important application in the group is a billing report written in Java that accesses multiple data sources and often for several hours.
Which is the MOST cost-effective solution?
- A. Deploy a separate AWS Lambda function for each applicatio
- B. Use AWS CloudTrail logs and Amazon CloudWatch alarms to verify completion of critical jobs.
- C. Deploy Amazon ECS containers on Amazon EC2 with Auto Scaling configured for memory utilization of 75%. Deploy an ECS task for each application being migrated with ECS task scalin
- D. Monitor services and hosts by using Amazon CloudWatch.
- E. Deploy AWS Elastic Beanstalk for each application with Auto Scaling to ensure that all requests have sufficient resource
- F. Monitor each AWS Elastic Beanstalk deployment with using CloudWatch alarms.
- G. Deploy a new amazon EC2 instance cluster that co-hosts all applications by using EC2 Auto Scaling and Application Load Balancer
- H. Scale cluster size based on a custom metric set on instance memory utilizatio
- I. Purchase 3-year Reserved instance reservations equal to the GroupMaxSize parameter of the Auto Scaling group.
Answer: C
NEW QUESTION 19
A company wants to replace its call system with a solution built using AWS managed services. The company call center would like the solution to receive calls, create contact flows, and scale to handle growth projections. The call center would also like the solution to use deep learning capabilities to recognize the intent of the callers and handle basic tasks, reducing the need to speak an agent. The solution should also be able to query business applications and provide relevant information back to calls as requested.
Which services should the Solution Architect use to build this solution? (Choose three.)
- A. Amazon Rekognition to identity who is calling.
- B. Amazon Connect to create a cloud-based contact center.
- C. Amazon Alexa for Business to build conversational interface.
- D. AWS Lambda to integrate with internal systems.
- E. Amazon Lex to recognize the intent of the caller.
- F. Amazon SQS to add incoming callers to a queue.
Answer: BDE
NEW QUESTION 20
A company used Amazon EC2 instances to deploy a web fleet to host a blog site. The EC2 instances are behind an Application Load Balancer (ALB) and are configured in an Auto Scaling group. The web application stores all blog content on an Amazon EFS volume.
The company recently added a feature for bloggers to add video to their posts, attracting 10 times the previous user traffic. At peak times of day, users report buffering and timeout issues while attempting to reach the site or watch videos.
Which is the MOST cost-efficient and scalable deployment that will resolve the issues for users?
- A. Reconfigure Amazon EFS to enable maximum I/O.
- B. Update the blog site to use instance store volumes for storag
- C. Copy the site contents to the volumes at launch and to Amazon S3 at shutdown.
- D. Configure an Amazon CloudFront distributio
- E. Point the distribution to an S3 bucket, and migrate the videos from EFS to Amazon S3.
- F. Set up an Amazon CloudFront distribution for all suite contents, and point the distribution at the ALB.
Answer: C
Explanation:
https://aws.amazon.com/premiumsupport/knowledge-center/cloudfront-https-connection-fails/
NEW QUESTION 21
A company’s application is increasingly popular and experiencing latency because of high volume reads on the database server.
The service has the following properties: A highly available REST API hosted in one region using Application Load Balancer (ALB) with auto scaling.
A highly available REST API hosted in one region using Application Load Balancer (ALB) with auto scaling. A MySQL database hosted on an Amazon EC2 instance in a single Availability Zone.
A MySQL database hosted on an Amazon EC2 instance in a single Availability Zone.
The company wants to reduce latency, increase in-region database read performance, and have multi-region disaster recovery capabilities that can perform a live recovery automatically without any data or performance loss (HA/DR).
Which deployment strategy will meet these requirements?
- A. Use AWS CloudFormation StackSets to deploy the API layer in two region
- B. Migrate the database to an Amazon Aurora with MySQL database cluster with multiple read replicas in one region and a read replica in a different region than the source database cluste
- C. Use Amazon Route 53 health checks to trigger a DNS failover to the standby region if the health checks to the primary load balancer fai
- D. In the event of Route 53 failover, promote the cross-region database replica to be the master and build out new read replicas in the standby region.
- E. Use Amazon ElastiCache for Redis Multi-AZ with an automatic failover to cache the database readquerie
- F. Use AWS OpsWorks to deploy the API layer, cache layer, and existing database layer in two region
- G. In the event of failure, use Amazon Route 53 health checks on the database to trigger a DNS failover to the standby region if the health checks in the primary region fai
- H. Back up the MySQL database frequently, and in the event of a failure in an active region, copy the backup to the standby region and restore the standby database.
- I. Use AWS CloudFormation StackSets to deploy the API layer in two region
- J. Add the database to an Auto Scaling grou
- K. Add a read replica to the database in the second regio
- L. Use Amazon Route 53 health checks on the database to trigger a DNS failover to the standby region if the health checks in the primary region fai
- M. Promote the cross-region database replica to be the master and build out new read replicas in the standby region.
- N. Use Amazon ElastiCache for Redis Multi-AZ with an automatic failover to cache the database read querie
- O. Use AWS OpsWorks to deploy the API layer, cache layer, and existing database layer in two region
- P. Use Amazon Route 53 health checks on the ALB to trigger a DNS failover to the standby region if the health checks in the primary region fai
- Q. Back up the MySQL database frequently, and in the event of a failure in an active region, copy the backup to the standby region and restore the standby database.
Answer: A
NEW QUESTION 22
A company will several AWS accounts is using AWS Organizations and service control policies (SCPs). An Administrator created the following SCP and has attached it to an organizational unit (OU) that contains AWS account 1111-1111-1111: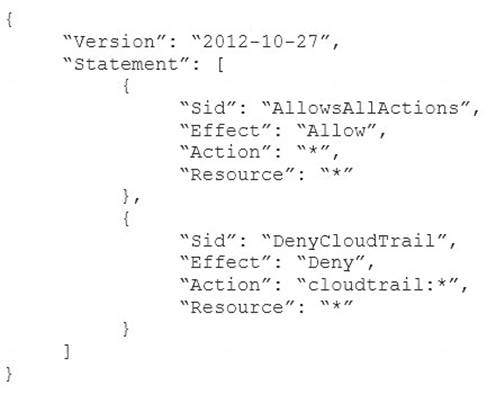
Developers working in account 1111-1111-1111 complain that they cannot create Amazon S3 buckets. How should the Administrator address this problem?
- A. Add s3:CreateBucket with “Allow” effect to the SCP.
- B. Remove the account from the OU, and attach the SCP directly to account 1111-1111-1111.
- C. Instruct the Developers to add Amazon S3 permissions to their IAM entities.
- D. Remove the SCP from account 1111-1111-1111.
Answer: C
NEW QUESTION 23
......
Recommend!! Get the Full SAP-C01 dumps in VCE and PDF From Dumpscollection, Welcome to Download: http://www.dumpscollection.net/dumps/SAP-C01/ (New 179 Q&As Version)
- Regenerate SAA-C03 Exam Guide For AWS Certified Solutions Architect - Associate (SAA-C03) Certification
- Amazon-Web-Services SAP-C01 Samples 2021
- Latest ANS-C00 Test Question For AWS Certified Advanced Networking Specialty Exam Certification
- Accurate BDS-C00 Questions 2021
- Avant-garde SCS-C01 Software 2021
- How Many Questions Of DOP-C01 Practice Test
- The Update Guide To DOP-C01 Questions Pool
- Amazon-Web-Services DVA-C01 Vce 2021
- What Best Quality SAA-C02 Free Practice Test Is
- All About Approved DAS-C01 Free Dumps

