1D0-61C Exam Questions - Online Test
1D0-61C Premium VCE File

150 Lectures, 20 Hours

Certleader 1D0-61C Questions are updated and all 1D0-61C answers are verified by experts. Once you have completely prepared with our 1D0-61C exam prep kits you will be ready for the real 1D0-61C exam without a problem. We have Far out CIW 1D0-61C dumps study guide. PASSED 1D0-61C First attempt! Here What I Did.
NEW QUESTION 1
Virtualization software transforms the hardware resources of a physical computer to create a fully functional virtual computer that can run its own operating systems and applications. In addition to the CPU and RAM, which hardware resources are used by virtualization software?
- A. Hard disk and USB devices
- B. Hard disk and network devices
- C. Virtual hard disk and network devices
- D. Network devices and secondary storage devices
Answer: B
NEW QUESTION 2
Which of the following is a disadvantage of implementing a Bring Your Own Device (BYOD) policy in a company?
- A. Increased cost for licensing mobile applications
- B. Configuring the corporate e-mail server to work with mobile devices
- C. Inability to control access to company data if the device is stolen or lost
- D. Providing training for employees on how to use mobile devices with company applications
Answer: C
NEW QUESTION 3
When using cloud-based services to host company data, a company’s disaster recovery plan should include strategies for:
- A. Creating redundancy and ensuring there is an exclusive contract with the cloud service provider.
- B. Distributing data and software services across multiple cloud service providers.
- C. Creating redundancy and using multiple cloud service providers.
- D. Using a single well-established cloud service provider.
Answer: C
NEW QUESTION 4
When comparing IPv4 to IPv6, which of the following is an advantage of the IPv6 network addressing scheme?
- A. Larger address space
- B. Shorter address space
- C. High dependence on network routers
- D. Fast and unencrypted network transmissions
Answer: A
NEW QUESTION 5
The capabilities of cellular networks have improved greatly since theiroriginal development for analogvoice phone calls. Most recently, fourth-generation (4G) wireless supports a variety of data-intensive needs.
A benefit of 4G networks is that they:
- A. Use spread-spectrum technology to ensure high transmission rates.
- B. Provide fast transmission rates equivalent to DSL or broadband-cable.
- C. Provide fast transmission rates equivalent to high-speed dial-up connections.
- D. Enable bandwidth throttling, allowing the user access to unrestricted download speeds.
Answer: B
NEW QUESTION 6
Which security issue is most closely associated with wireless networks?
- A. Spoofing
- B. Wardriving
- C. Eavesdropping
- D. Man-in-the-middle
Answer: B
NEW QUESTION 7
Your company is investigating the possibility of moving its customer service management system to a cloud service provider. The sales rep for the cloud service provider has presented many advantages that would benefit your company. What would be a potential drawback of moving the CRM from your current in-house solution?
- A. If your company’s Internet service is interrupted for any reason at any time, you will not have access to the CRM.
- B. More company employees will have access to the system, which could result in unauthorized access to confidential data
- C. Special equipment will need to be purchased and maintained in your office in order to access and maintain the CRM once it is migrated to the hosted cloud service.
- D. Migrating the CRM to the cloud service provider will eliminate several jobs in your customer service department because their job roles will no longer be required.
Answer: A
NEW QUESTION 8
A friend has called you about a possible computer problem because her computer is acting strangely. Sounds play unexpectedly, the monitor turns off suddenly, the hard-drive light flashes constantly, the computer sometimes reboots itself without warning. When you inspect your friend’s system, you notice that several ports are open. Which of the following is most likely the cause of these symptoms?
- A. The computer has been infected with a polymorphic virus.
- B. The computer is experiencing a denial-of-service attack.
- C. The computer has been infected with an illicit server.
- D. The computer has been infected by a worm.
Answer: C
NEW QUESTION 9
Wireless networks are subject to more security issues than standard wired networks. Which wireless security protocol can prevent unauthorized devices from connecting to the wireless network?
- A. WPA2
- B. RSA
- C. AES
- D. DES
Answer: A
NEW QUESTION 10
Disaster recovery planning is considered a best practice for all organizations. It is even more important when cloud-computing services are used. Which of the following should be included as part of a disaster recovery plan for companies that use cloud-based services?
- A. Company organizational chart
- B. Malware and anti-virus software updates
- C. Service-level agreement with a cloud-provider
- D. Inventory of services not dependent on the cloud provider
Answer: C
NEW QUESTION 11
Selena has decided to change a 32-character unique wireless network name on her wireless router to improve network security after a break-in. She is following advice from CERT to make this change in order to avoid attacks from botnets. Which of the following settings would she modify?
- A. Direct Sequence Spread Spectrum (DSSS) signal
- B. Media Access Control (MAC) address
- C. Wi-Fi Protected Access 2 (WPA2)
- D. Service Set Identifier (SSID)
Answer: D
NEW QUESTION 12
Which term describes the practice of actively collecting wireless networking data from companies and individuals?
- A. War driving
- B. Spear phishing
- C. Dictionary attack
- D. Social engineering
Answer: A
NEW QUESTION 13
ABC Company develops itsowndatabase applications. ABC is considering migrating to cloud services to accommodate the company’s growth. What strategy should ABC use to ensure continuous data protection if it begins using cloud services?
- A. Cloud-only solution
- B. Regional systems solution
- C. Location systems solution
- D. Multiple cloud-service providers
Answer: C
NEW QUESTION 14
When a PC computer device wants to communicate with the processor, which system resource does it use?
- A. I/O
- B. DMA
- C. PIO
- D. IRQ
Answer: D
NEW QUESTION 15
What is the distinguishing difference between a LAN and WAN?
- A. A LAN is a group of networked computers within a confined geographic area.
- B. A WAN is a group of networked computers within a confined geographic area.
- C. A LAN typically provides slower network connection speeds than a WAN.
- D. A WAN is commonly used for intra-office communication.
Answer: A
NEW QUESTION 16
Consider the network configuration shown in the command prompt: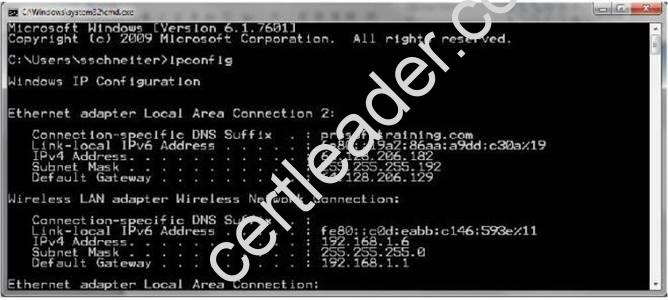
What does the Default Gateway identify?
- A. The file server on the network
- B. The local host on the network
- C. The computer on the network
- D. The router on the network
Answer: D
NEW QUESTION 17
Selena has run out of memory on her phone’s SD card. She has decided to store the files she has accumulated on a third-party cloud service provider’s drives. Which of the following is a typical issue that she may encounter?
- A. The files become corrupted due to an attack from a hacker botnet.
- B. The files become unavailable whenever Internet connectivity is lost.
- C. The files become unavailable because they are being shared with other users.
- D. The files become corrupted because the provider uses a proprietary compression algorithm during transit.
Answer: B
NEW QUESTION 18
Carlos is the Information Technology (IT) administrator for a small company. Over the past year, employees have been using their personal mobile devices and smartphones for business use. This has reduced costs of purchasing new devices for employees. Carlos is now considering whether he should stop supplying employees with company phones and instead require all employees to use their personal smartphones for work. How can Carlos address the most significant security vulnerability?
- A. Develop a robust app to push security updates out to the various mobile OS devices
- B. Create an employee policy that requires employees to keep phones updated to the latest technology
- C. Create a policy that specifies acceptable use, ensuring security measures are in place for mobile devices
- D. Mandate that employees switch to the company’s mobile service provider to ensure security policies are enforced
Answer: C
NEW QUESTION 19
Acme Corp. is a small manufacturing company. To reduceIT infrastructure costs, it uses cloud- based services extensively and strives to have the least amount ofIT equipment onsite. Last year, Acme suffered a failure that resulted in significant down time and data loss. Management has decided to implement a continuous data protection (CDP) solution. Which type of CDP solution best fits Acme’s situation?
- A. Cloud-only solution
- B. Local systems solution
- C. Distributed network services provider
- D. Contracted network services provider
Answer: A
NEW QUESTION 20
Patrick visits his teenage daughter’s social media page and discovers several offensive posts about one of her classmates. After speaking with his daughter, Patrick learns that several other girls in her class are upset with the classmate and have been posting, texting and e-mailing others about the girl. What is the best way for Patrick to help his daughter understand cyberbullying?
- A. He should advise his daughter to ignore the posts, texts and c-mails.
- B. He should explain to his daughter that she is participating in the bullying by accepting others’posts, texts and c-mails.
- C. He should explain to his daughter that the Internet embraces freedom of speech, and anyone is allowed to write anything.
- D. He should advise his daughter to delete all the posts, texts and c-mails she has received, as well as any new ones that appear.
Answer: B
NEW QUESTION 21
Which term describes a compact personal computer that relies on a touch screen forinput, generally uses a solid-state drive instead of a traditional hard disk, and relies on wireless or mobile networks for connectivity?
- A. Tablet
- B. Laptop
- C. Netbook
- D. Portable media player
Answer: A
NEW QUESTION 22
Which of the following is a drawback to using Wired Equivalent Privacy (WEP)?
- A. Wireless network overhead is excessive.
- B. Symmetric-key encryption is susceptible to cracking.
- C. The number of devices that can communicate using WEP is limited.
- D. Encryption and decryption speeds are slower compared to other protocols.
Answer: B
NEW QUESTION 23
......
Recommend!! Get the Full 1D0-61C dumps in VCE and PDF From Surepassexam, Welcome to Download: https://www.surepassexam.com/1D0-61C-exam-dumps.html (New 59 Q&As Version)
- [2021-New] CIW 1D0-437 Dumps With Update Exam Questions (6-15)
- [2021-New] CIW 1D0-435 Dumps With Update Exam Questions (7-16)
- [2021-New] CIW 1D0-610 Dumps With Update Exam Questions (5-14)
- [2021-New] CIW 1D0-520 Dumps With Update Exam Questions (5-14)
- [2021-New] CIW 1D0-435 Dumps With Update Exam Questions (4-13)
- [2021-New] CIW 1D0-571 Dumps With Update Exam Questions (1-10)
- [2021-New] CIW 1D0-437 Dumps With Update Exam Questions (4-13)
- [2021-New] CIW 1D0-435 Dumps With Update Exam Questions (8-17)
- [2021-New] CIW 1D0-571 Dumps With Update Exam Questions (2-11)
- [2021-New] CIW 1D0-610 Dumps With Update Exam Questions (1-10)

