200-201 Exam Questions - Online Test
200-201 Premium VCE File

150 Lectures, 20 Hours

Proper study guides for Up to date Cisco Understanding Cisco Cybersecurity Operations Fundamentals certified begins with Cisco 200-201 preparation products which designed to deliver the Realistic 200-201 questions by making you pass the 200-201 test at your first time. Try the free 200-201 demo right now.
Check 200-201 free dumps before getting the full version:
NEW QUESTION 1
Which category relates to improper use or disclosure of PII data?
- A. legal
- B. compliance
- C. regulated
- D. contractual
Answer: C
NEW QUESTION 2
A network engineer discovers that a foreign government hacked one of the defense contractors in their home country and stole intellectual property. What is the threat agent in this situation?
- A. the intellectual property that was stolen
- B. the defense contractor who stored the intellectual property
- C. the method used to conduct the attack
- D. the foreign government that conducted the attack
Answer: D
NEW QUESTION 3
While viewing packet capture data, an analyst sees that one IP is sending and receiving traffic for multiple devices by modifying the IP header.
Which technology makes this behavior possible?
- A. encapsulation
- B. TOR
- C. tunneling
- D. NAT
Answer: D
NEW QUESTION 4
A malicious file has been identified in a sandbox analysis tool.
Which piece of information is needed to search for additional downloads of this file by other hosts?
- A. file type
- B. file size
- C. file name
- D. file hash value
Answer: D
NEW QUESTION 5
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
- A. detection and analysis
- B. post-incident activity
- C. vulnerability management
- D. risk assessment
- E. vulnerability scoring
Answer: AB
NEW QUESTION 6
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email. When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
- A. social engineering
- B. eavesdropping
- C. piggybacking
- D. tailgating
Answer: A
NEW QUESTION 7
Refer to the exhibit.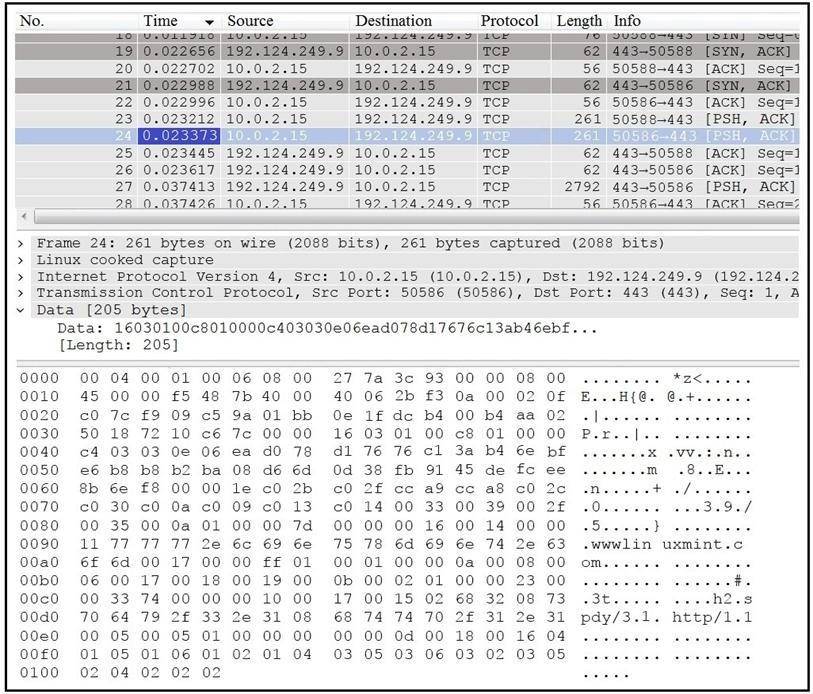
Which application protocol is in this PCAP file?
- A. SSH
- B. TCP
- C. TLS
- D. HTTP
Answer: B
NEW QUESTION 8
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
- A. The computer has a HIPS installed on it.
- B. The computer has a NIPS installed on it.
- C. The computer has a HIDS installed on it.
- D. The computer has a NIDS installed on it.
Answer: C
NEW QUESTION 9
Which evasion technique is indicated when an intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources?
- A. resource exhaustion
- B. tunneling
- C. traffic fragmentation
- D. timing attack
Answer: A
NEW QUESTION 10
Which two elements are used for profiling a network? (Choose two.)
- A. session duration
- B. total throughput
- C. running processes
- D. listening ports
- E. OS fingerprint
Answer: DE
NEW QUESTION 11
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different bank account number?
- A. integrity
- B. confidentiality
- C. availability
- D. scope
Answer: A
NEW QUESTION 12
What is the difference between statistical detection and rule-based detection models?
- A. Rule-based detection involves the collection of data in relation to the behavior of legitimate users over a period of time
- B. Statistical detection defines legitimate data of users over a period of time and rule-based detection defines it on an IF/THEN basis
- C. Statistical detection involves the evaluation of an object on its intended actions before it executes that behavior
- D. Rule-based detection defines legitimate data of users over a period of time and statistical detection defines it on an IF/THEN basis
Answer: B
NEW QUESTION 13
Which piece of information is needed for attribution in an investigation?
- A. proxy logs showing the source RFC 1918 IP addresses
- B. RDP allowed from the Internet
- C. known threat actor behavior
- D. 802.1x RADIUS authentication pass arid fail logs
Answer: C
NEW QUESTION 14
Which list identifies the information that the client sends to the server in the negotiation phase of the TLS handshake?
- A. ClientStart, ClientKeyExchange, cipher-suites it supports, and suggested compression methods
- B. ClientStart, TLS versions it supports, cipher-suites it supports, and suggested compression methods
- C. ClientHello, TLS versions it supports, cipher-suites it supports, and suggested compression methods
- D. ClientHello, ClientKeyExchange, cipher-suites it supports, and suggested compression methods
Answer: C
NEW QUESTION 15
What is a difference between inline traffic interrogation and traffic mirroring?
- A. Inline inspection acts on the original traffic data flow
- B. Traffic mirroring passes live traffic to a tool for blocking
- C. Traffic mirroring inspects live traffic for analysis and mitigation
- D. Inline traffic copies packets for analysis and security
Answer: B
NEW QUESTION 16
Which two compliance frameworks require that data be encrypted when it is transmitted over a public network?
(Choose two.)
- A. PCI
- B. GLBA
- C. HIPAA
- D. SOX
- E. COBIT
Answer: AC
NEW QUESTION 17
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
- A. ransomware communicating after infection
- B. users downloading copyrighted content
- C. data exfiltration
- D. user circumvention of the firewall
Answer: D
NEW QUESTION 18
Refer to the exhibit.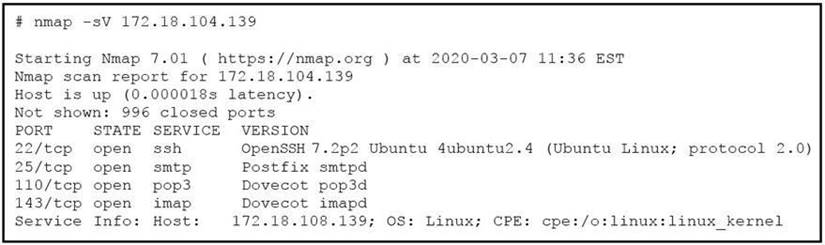
What does the output indicate about the server with the IP address 172.18.104.139?
- A. open ports of a web server
- B. open port of an FTP server
- C. open ports of an email server
- D. running processes of the server
Answer: C
NEW QUESTION 19
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
- A. application identification number
- B. active process identification number
- C. runtime identification number
- D. process identification number
Answer: D
NEW QUESTION 20
......
Recommend!! Get the Full 200-201 dumps in VCE and PDF From 2passeasy, Welcome to Download: https://www.2passeasy.com/dumps/200-201/ (New 98 Q&As Version)
- [2021-New] Cisco 400-101 Dumps With Update Exam Questions (171-180)
- Latest Designing Cisco Data Center Infrastructure (DCID) 300-610 Dumps Questions
- [2021-New] Cisco 300-101 Dumps With Update Exam Questions (41-50)
- [2021-New] Cisco 300-207 Dumps With Update Exam Questions (71-80)
- Top Tips Of Replace 300-435 Prep
- [2021-New] Cisco 200-125 Dumps With Update Exam Questions (2-11)
- [2021-New] Cisco 200-105 Dumps With Update Exam Questions (21-30)
- [2021-New] Cisco 400-051 Dumps With Update Exam Questions (101-110)
- [2021-New] Cisco 200-355 Dumps With Update Exam Questions (10-19)
- [2021-New] Cisco 400-251 Dumps With Update Exam Questions (11-20)

