300-375 Exam Questions - Online Test
300-375 Premium VCE File

150 Lectures, 20 Hours

It is impossible to pass Cisco 300-375 exam without any help in the short term. Come to Actualtests soon and find the most advanced, correct and guaranteed Cisco 300-375 practice questions. You will get a surprising result by our Most up-to-date Securing Cisco Wireless Enterprise Networks practice guides.
NEW QUESTION 1
Which method does a Cisco switch use to authenticate a Cisco lightweight access point that is acting as a 802.1x supplicant?
- A. 802.1X
- B. EAP-FAST with anonymous PAC provisioning
- C. a password only
- D. a username and password
Answer: B
NEW QUESTION 2
A network engineer must segregate all iPads on the guest WLAN to a separate VLAN. How does the engineer accomplish this task without using ISE?
- A. Use 802.1x authentication to profile the devices.
- B. Create a local policy on the WLC.
- C. Use an mDNS profile for the iPad device.
- D. Enable RADIUS DHCP profiling on the WLAN.
Answer: B
NEW QUESTION 3
On which two ports does the RADIUS server maintain a database and listen for incoming authentication and accounting requests? (Choose two.)
- A. UDP 1900
- B. UDP port 1812
- C. TCP port 1812
- D. TCP port 1813
- E. UDP port 1813
Answer: BE
NEW QUESTION 4
A customer wants to allow employees to easily onboard their devices to the wireless network. Which process can be configured on Cisco ISE to support this requirement?
- A. self registration guest portal
- B. client provisioning
- C. native supplicant provisioning
- D. local web auth
Answer: B
NEW QUESTION 5


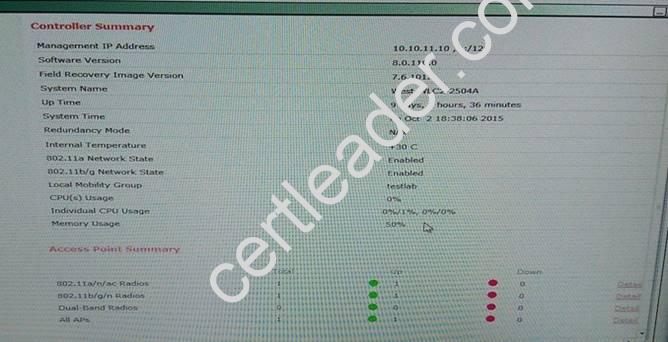
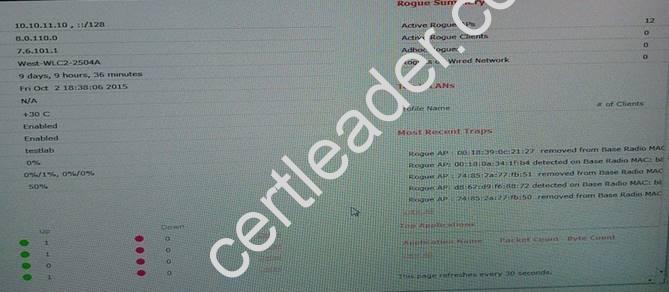




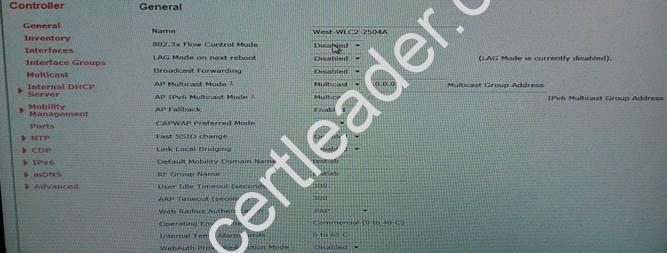

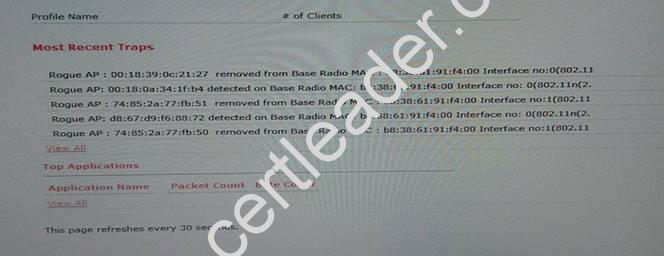
- A. Mastered
- B. Not Mastered
Answer: A
Explanation:
Please refer the link below in Explanation to configure this simulation.
Example:
Use this link to configure all the steps for this simulation : http://www.cisco.com/c/en/us/support/docs/wireless-mobility/wireless-lan-wlan/116880-configwpa2- psk-00.html
NEW QUESTION 6
Refer to the exhibit.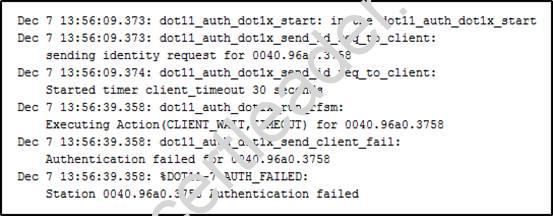
A client reports being unable to log into the wireless network, which uses PEAPv2. Which two issues appear in the output? (Choose two.)
- A. There is a problem with the client supplicant.
- B. The AP has the incorrect RADIUS server address.
- C. The AP has lost IP connectivity to the authentication server.
- D. The EAP client timeout value should be increased.
- E. The authentication server is misconfigured on the controller.
- F. The authentication server is misconfigured in the WLA
Answer: AD
NEW QUESTION 7
During the EAP process and specifically related to the logon session, which encrypted key is sent from the RADIUS server to the access point?
- A. WPA key
- B. encryption key
- C. session key
- D. shared secret key
Answer: C
NEW QUESTION 8
An engineer is troubleshooting rogue access points that are showing up in Cisco Prime Infrastructure. What is the maximum number of Aps the engineer can use to contain an identified rogue access point in the WLC?
- A. 3
- B. 4
- C. 6
- D. 5
Answer: B
Explanation:
https://www.cisco.com/c/en/us/td/docs/wireless/controller/7-
4/configuration/guides/consolidated/b_cg74_CONSOLIDATED/b_cg74_CONSOLIDATED_chapter_010 111001.html
NEW QUESTION 9
MFP is enabled globally on a WLAN with default settings on single controller wireless network. Older client devices are disconnected from the network during a deauthentication attack. What is the
cause of this issue?
- A. The client devices do not support WPA.
- B. The client devices do not support CCXv5.
- C. The MFP on the WLAN is set to optional
- D. The NTP server is not configured on the controlle
Answer: C
NEW QUESTION 10
An engineer is considering an MDM integration with Cisco ISE to assist with security for lost devices. Which two functions of MDM increase security for lost devices that access data from the network? (Choose two.)
- A. PIN enforcement
- B. Jailbreak/root detection
- C. data wipe
- D. data encryption
- E. data loss prevention
Answer: AC
NEW QUESTION 11
Refer to the exhibit. You are configuring an autonomous AP for 802.1x access to a wired infrastructure. What does the command do?
- A. It enables the AP to override the authentication timeout on the RADIUS server.
- B. It configures how long the AP must wait for a client to reply to an EAP/dot1x message before the authentication fails.
- C. It enables the supplicant to override the authentication timeout on the client
- D. It configures how long the RADIUS server must wait for supplicant to reply to an EAP/dot1x message before the authentication fails.
Answer: C
NEW QUESTION 12
When a wireless client uses WPA2 AES, which keys are created at the end of the four way handshake process between the client and the access point?
- A. AES key, TKIP key, WEP key
- B. AES key, WPA2 key, PMK
- C. KCK, KEK, TK
- D. KCK, KEK, MIC key
Answer: A
NEW QUESTION 13
After receiving an alert regarding a rogue AP, a network engineer logs into Cisco Prime and looks at the floor map where the AP that detected the rogue is located. The map is synchronized with a mobility services engine that determines the rogue device is actually inside the campus. The engineer determines the rogue to be a security threat and decides to stop it from broadcasting inside the enterprise wireless network. What is the fastest way to disable the rogue?
- A. Go to the location the rogue device is indicated to be and disable the power.
- B. Create an SSID on WLAN controller resembling the SSID of the rogue to spoof it and disable clients from connecting to it.
- C. Classify the rogue as malicious in Cisco Prime.
- D. Update the status of the rogue in Cisco Prime to containe
Answer: C
NEW QUESTION 14
An engineer is configuring a new mobility anchor for a WLAN on the CLI with the config wlan mobility anchor add 3 10.10.10.10 command, but the command is failing. Which two conditions must be met to be able to enter this command? (Choose two.)
- A. The anchor controller IP address must be within the management interface subnet.
- B. The anchor controller must be in the same mobility group.
- C. The WLAN must be enabled.
- D. The mobility group keepalive must be configured.
- E. The indicated WLAN ID must be present on the controlle
Answer: AB
NEW QUESTION 15
An engineer with ID 338860948 is implementing Cisco Identity-Based Networking on a Cisco AireOS
controller. The engineer has two ACLs on the controller. The first ACL, named BASE_ACL, is applied to the corporate_clients interface on the WLC, which is used for all corporate clients. The second ACL, named HR_ACL, is referenced by ISE in the Human Resources group policy.
Which option is the resulting ACL when a Human Resources user connects?
- A. HR_ACL only
- B. HR_ACL appended with BASE_ACL
- C. BASE_ACL appended with HR_ACL
- D. BASE_ACL only
Answer: A
NEW QUESTION 16
Which attribute on the Cisco WLC v7.0 does RADIUS IETF attribute "Tunnel-Private-Group ID" assign?
- A. ACL
- B. DSCP
- C. QoS
- D. VLAN
Answer: D
NEW QUESTION 17
WPA2 Enterprise with 802.1x is being used for clients to authenticate to a wireless network through
an ACS server. For security reasons, the network engineer wants to ensure only PEAP authentication can be used. The engineer sent instructions to clients on how to configure their supplicants, but users are still in the ACS logs authentication using EAP-FAST. Which option describes the most efficient way the engineer can ensure these users cannot access the network unless the correct authentication mechanism is configured?
- A. Enable AAA override on the SSID, gather the usernames of these users, and disable their RADIUS accounts until they make sure they correctly configured their devices.
- B. Enable AAA override on the SSID and configure an access policy in ACS that denies access to the list of MACs that have used EAP-FAST.
- C. Enable AAA override on the SSID and configure an access policy in ACS that allows access only when the EAP authentication method is PEAP.
- D. Enable AAA override on the SSID and configure an access policy in ACS that puts clients that authenticated using EAP-FAST into a quarantine VLAN.
Answer: D
NEW QUESTION 18
An engineer is adding APs to an existing VoWLAN to allow for location based services. Which option
will the primary change be to the network?
- A. increased transmit power on all APs
- B. moving to a bridging model
- C. AP footprint
- D. cell overlap would decrease
- E. triangulation of devices
Answer: C
NEW QUESTION 19
An engineer is working on a remote site that is configured using FlexConnect. They are worried that the access points will not send RADIUS requests directly to the authentication server is standalone mode. Which command ensures direct authentication using the default ports as defined on the WLC?
- A. config filexconnect group Remote radius server acct add primary 10.10.10.10 1813 Cisco123
- B. config filexconnect group Remote radius server auth add primary 10.10.10.10 1813 Cisco123
- C. config filexconnect group Remote radius server acct add primary 10.10.10.10 1812 Cisco123
- D. config filexconnect group Remote radius server auth add primary 10.10.10.10 1812 Cisco123
Answer: C
NEW QUESTION 20
What is the maximum number of clients that a small branch deployment using a four-member Cisco Catalyst 3850 stack (acting as MC/MA) can support?
- A. 10000
- B. 1000
- C. 500
- D. 2000
- E. 5000
Answer: E
NEW QUESTION 21
A customer is concerned about DOS attacks from a neighboring facility. Which feature can be enabled to help alleviate these concerns and mitigate DOS attacks on a WLAN?
- A. PMF
- B. peer-to-peer blocking
- C. Cisco Centralized Key Management
- D. split tunnel
Answer: A
NEW QUESTION 22
DRAG DROP
A wireless engineer wants to schedule monthly security reports in Cisco Prime infrastructure. Drag and drop the report title from the left onto the expected results when the report is generated on the right.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 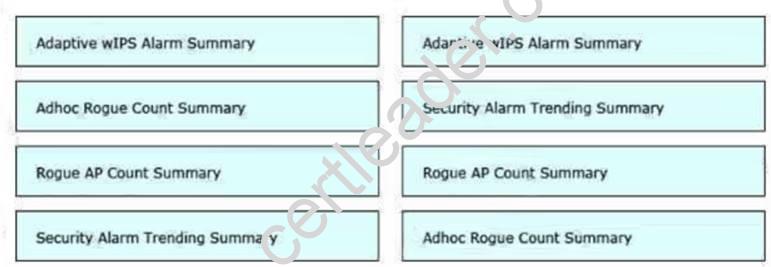
NEW QUESTION 23
......
Recommend!! Get the Full 300-375 dumps in VCE and PDF From Certshared, Welcome to Download: https://www.certshared.com/exam/300-375/ (New 124 Q&As Version)
- All About Real 300-620 Prep
- [2021-New] Cisco 352-001 Dumps With Update Exam Questions (11-20)
- Leading Cisco Mobile Backhaul For Field Engineers 500-240 Test Engine
- [2021-New] Cisco 400-101 Dumps With Update Exam Questions (391-400)
- [2021-New] Cisco 300-207 Dumps With Update Exam Questions (1-10)
- [2021-New] Cisco 400-201 Dumps With Update Exam Questions (21-30)
- Most Recent 642-885 Rapidshare 2021
- Renew 642-889 Testing Material 2021
- [2021-New] Cisco 300-320 Dumps With Update Exam Questions (141-150)
- [2021-New] Cisco 642-996 Dumps With Update Exam Questions (21-30)

