312-49v9 Exam Questions - Online Test
312-49v9 Premium VCE File

150 Lectures, 20 Hours

Act now and download your EC-Council 312-49v9 test today! Do not waste time for the worthless EC-Council 312-49v9 tutorials. Download Up to the immediate present EC-Council ECCouncil Computer Hacking Forensic Investigator (V9) exam with real questions and answers and begin to learn EC-Council 312-49v9 with a classic professional.
Free 312-49v9 Demo Online For EC-Council Certifitcation:
NEW QUESTION 1
This organization maintains a database of hash signatures for known software
- A. International Standards Organization
- B. Institute of Electrical and Electronics Engineers
- C. National Software Reference Library
- D. American National standards Institute
Answer: C
NEW QUESTION 2
When an investigator contacts by telephone the domain administrator or controller listed by a whois lookup to request all e-mails sent and received for a user account be preserved, what U.S.C. statute authorizes this phone call and obligates the ISP to preserve e-mail records?
- A. Title 18, Section 1030
- B. Title 18, Section 2703(d)
- C. Title 18, Section Chapter 90
- D. Title 18, Section 2703(f)
Answer: D
Explanation:
18 U.S.C. § 1029 Fraud and Related Activity in Connection with Access Devices 18 U.S.C. § 1030 Fraud and Related Activity in Connection with Computers
18 U.S.C. § 2703 Required Disclosure of Customer Communications Records 18 U.S.C. § 2703(d) Requirements for Court Order
18 U.S.C. § 2703(f) Requirement to Preserve Evidence
NEW QUESTION 3
Which of the following statements does not support the case assessment?
- A. Review the case investigator's request for service
- B. Identify the legal authority for the forensic examination request
- C. Do not document the chain of custody
- D. Discuss whether other forensic processes need to be performed on the evidence
Answer: C
NEW QUESTION 4
What will the following command produce on a website login page? SELECT email, passwd, login_id, full_name FROM members WHERE email = 'someone@somehwere.com';
DROP TABLE members; --'
- A. Retrieves the password for the first user in the members table
- B. This command will not produce anything since the syntax is incorrect
- C. Deletes the entire members table
- D. Inserts the Error! Reference source not foun
- E. email address into the members table
Answer: C
Explanation:
The third line deletes the table named members.
NEW QUESTION 5
When searching through file headers for picture file formats, what should be searched to find a JPEG file in hexadecimal format?
- A. FF D8 FF E0 00 10
- B. FF FF FF FF FF FF
- C. FF 00 FF 00 FF 00
- D. EF 00 EF 00 EF 00
Answer: A
NEW QUESTION 6
When the operating system marks cluster as used, but does not allocate them to any file, such clusters are known as ____.
- A. Lost clusters
- B. Bad clusters
- C. Empty clusters
- D. Unused clusters
Answer: A
NEW QUESTION 7
Lance wants to place a honeypot on his network. Which of the following would be your recommendations?
- A. Use a system that has a dynamic addressing on the network
- B. Use a system that is not directly interacing with the router
- C. Use it on a system in an external DMZ in front of the firewall
- D. It doesn’t matter as all replies are faked
Answer: D
NEW QUESTION 8
International Mobile Equipment Identifier (IMEI) is a 15-dlgit number that indicates the manufacturer, model type, and country of approval for GSM devices. The first eight digits of an IMEI number that provide information about the model and origin of the mobile device is also known as:
- A. Type Allocation Code (TAC)
- B. Device Origin Code (DOC)
- C. Manufacturer identification Code (MIC)
- D. Integrated Circuit Code (ICC)
Answer: A
NEW QUESTION 9
Law enforcement officers are conducting a legal search for which a valid warrant was obtained. While conducting the search, officers observe an item of evidence for an unrelated crime that was not included in the warrant. The item was clearly visible to the officers and immediately identified as evidence. What is the term used to describe how this evidence is admissible?
- A. Plain view doctrine
- B. Corpus delicti
- C. Locard Exchange Principle
- D. Ex Parte Order
Answer: A
NEW QUESTION 10
Which of the following log injection attacks uses white space padding to create unusual log entries?
- A. Word wrap abuse attack
- B. HTML injection attack
- C. Terminal injection attack
- D. Timestamp injection attack
Answer: A
NEW QUESTION 11
Volatile information can be easily modified or lost when the system is shut down or rebooted. It helps to determine a logical timeline of the security incident and the users who would be responsible.
- A. True
- B. False
Answer: A
NEW QUESTION 12
Why is it a good idea to perform a penetration test from the inside?
- A. It is never a good idea to perform a penetration test from the inside
- B. It is easier to hack from the inside
- C. Because 70% of attacks are from inside the organization
- D. To attack a network from a hacker's perspective
Answer: C
NEW QUESTION 13
You are called in to assist the police in an investigation involving a suspected drug dealer. The police searched the suspect house after aYou are called in to assist the police in an investigation involving a suspected drug dealer. The police searched the suspect? house after a warrant was obtained and they located a floppy disk in the suspect bedroom. The disk contains several files, but they appear to be passwordwarrant was obtained and they located a floppy disk in the suspect? bedroom. The disk contains several files, but they appear to be password protected. What are two common
methods used by password cracking software that you could use to obtain the password?
- A. Limited force and library attack
- B. Brute force and dictionary attack
- C. Maximum force and thesaurus attack
- D. Minimum force and appendix attack
Answer: B
NEW QUESTION 14
When a file is deleted by Windows Explorer or through the MS-DOS delete command, the operating system inserts ____ in the first letter position of the filename in the FAT database.
- A. A Capital X
- B. A Blank Space
- C. The Underscore Symbol
- D. The lowercase Greek Letter Sigma (s)
Answer: D
Explanation:
When a file is deleted, the first byte is replaced with 0xE5 to marked the file as deleted or erased, and is the same for FAT12/16/32. An 0xE5 translates also to a ASCII 229, a “O” with a tilde.
However, using the greek alphabet (see: http://www.ascii.ca/iso8859.7.htm) the ASCII code 229 is “the lowercase Greek Letter Epsilon, and Ascii code 243 is Lower case Greek Letter Sigma.
http://chexed.com/ComputerTips/asciicodes.php says that Ascii 229 is Lowercase Greek Letter Sigma
So, although D looks like the correct answer here, it may require more understanding of the underlying intent of the question.
NEW QUESTION 15
Why should you never power on a computer that you need to acquire digital evidence from?
- A. When the computer boots up, files are written to the computer rendering the data nclean?When the computer boots up, files are written to the computer rendering the data ?nclean
- B. When the computer boots up, the system cache is cleared which could destroy evidence
- C. When the computer boots up, data in the memory buffer is cleared which could destroy evidenceWhen the computer boots up, data in the memory? buffer is cleared which could destroy evidence
- D. Powering on a computer has no affect when needing to acquire digital evidence from it
Answer: A
NEW QUESTION 16
All Blackberry email is eventually sent and received through what proprietary RIM-operated mechanism?
- A. Blackberry Message Center
- B. Microsoft Exchange
- C. Blackberry WAP gateway
- D. Blackberry WEP gateway
Answer: A
NEW QUESTION 17
Tyler is setting up a wireless network for his business that he runs out of his home. He has followed all the directions from the ISP as well as the wireless router manual. He does not have any encryption set and the SSID is being broadcast. On his laptop, he can pick up the wireless signal for short periods of time, but then the connection drops and the signal goes away. Eventually the wireless signal shows back up, but drops intermittently. What could be Tyler issue with his home wireless network?
- A. CB radio
- B. 2.4Ghz Cordless phones
- C. Satellite television
- D. Computers on his wired network
Answer: B
NEW QUESTION 18
Jack Smith is a forensics investigator who works for Mason Computer Investigation Services. He is investigating a computer that was infected by Ramen Virus.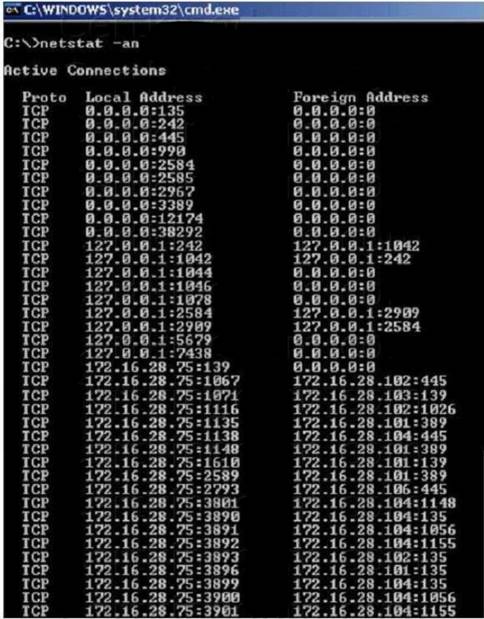
He runs the netstat command on the machine to see its current connections. In the following screenshot, what do the 0.0.0.0 IP addresses signify?
- A. Those connections are established
- B. Those connections are in listening mode
- C. Those connections are in closed/waiting mode
- D. Those connections are in timed out/waiting mode
Answer: B
NEW QUESTION 19
If you plan to startup a suspect’s computer, you must modify the ____ to ensure that you do not contaminate or alter data on the suspect’s hard drive by booting to the hard drive.
- A. deltree command
- B. CMOS
- C. Boot.sys
- D. Scandisk utility
- E. boot.ini
Answer: E
Explanation:
The OS isn’t specified, but if this was a Windows OS, then this would be boot.ini
The answer is CMOS. The startup of a computer is the boot sequence, and the boot sequence is defined in the CMOS. The common occurrence is to boot off a floppy, and you need to see that the floppy (usually the A drive) is first in the sequence. If you don’t, and the hard drive is first, then booting the system wil boot the hard drive and alter the evidence.
NEW QUESTION 20
What is a first sector ("sector zero") of a hard disk?
- A. Master boot record
- B. System boot record
- C. Secondary boot record
- D. Hard disk boot record
Answer: A
NEW QUESTION 21
Who is responsible for the following tasks?
? Secure the scene and ensure that it is maintained In a secure state until the Forensic Team advises
? Make notes about the scene that will eventually be handed over to the Forensic Team
- A. Non-Laboratory Staff
- B. System administrators
- C. Local managers or other non-forensic staff
- D. Lawyers
Answer: A
NEW QUESTION 22
Which of the following filesystem is used by Mac OS X?
- A. EFS
- B. HFS+
- C. EXT2
- D. NFS
Answer: B
Explanation:
EFS (Encrypting File System) is part of NTFS and used on Windows EXT2 is used on Linux NFS (Network File System) is for access to a network file system over TCP/IP
NEW QUESTION 23
What is the First Step required in preparing a computer for forensics investigation?
- A. Do not turn the computer off or on, run any programs, or attempt to access data on a computer
- B. Secure any relevant media
- C. Suspend automated document destruction and recycling policies that may pertain to any relevant media or users at Issue
- D. Identify the type of data you are seeking, the Information you are looking for, and the urgency level of the examination
Answer: A
NEW QUESTION 24
What must an investigator do before disconnecting an iPod from any type of computer?
- A. Unmount the iPod
- B. Mount the iPod
- C. Disjoin the iPod
- D. Join the iPod
Answer: A
NEW QUESTION 25
Which of the following email headers specifies an address for mailer-generated errors, like "no such user" bounce messages, to go to (instead of the sender's address)?
- A. Errors-To header
- B. Content-Transfer-Encoding header
- C. Mime-Version header
- D. Content-Type header
Answer: A
NEW QUESTION 26
What binary coding is used most often for e-mail purposes?
- A. SMTP
- B. Uuencode
- C. IMAP
- D. MIME
Answer: D
NEW QUESTION 27
......
P.S. Easily pass 312-49v9 Exam with 209 Q&As Dumps-hub.com Dumps & pdf Version, Welcome to Download the Newest Dumps-hub.com 312-49v9 Dumps: https://www.dumps-hub.com/312-49v9-dumps.html (209 New Questions)
- The Secret Of EC-Council 312-75 Exam Dumps
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (111-120)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (1-10)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (51-60)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (341-350)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (191-200)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (171-180)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (191-200)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (261-270)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (241-250)

