312-50v11 Exam Questions - Online Test
312-50v11 Premium VCE File

150 Lectures, 20 Hours

Exambible 312-50v11 Questions are updated and all 312-50v11 answers are verified by experts. Once you have completely prepared with our 312-50v11 exam prep kits you will be ready for the real 312-50v11 exam without a problem. We have Updated EC-Council 312-50v11 dumps study guide. PASSED 312-50v11 First attempt! Here What I Did.
Free 312-50v11 Demo Online For EC-Council Certifitcation:
NEW QUESTION 1
“........is an attack type for a rogue Wi-Fi access point that appears to be a legitimate one offered on the premises, but actually has been set up to eavesdrop on wireless communications. It is the wireless version of the phishing scam. An attacker fools wireless users into connecting a laptop or mobile phone to a tainted hot-spot by posing as a legitimate provider. This type of attack may be used to steal the passwords of
unsuspecting users by either snooping the communication link or by phishing, which involves setting up a fraudulent web site and luring people there.”
Fill in the blank with appropriate choice.
- A. Evil Twin Attack
- B. Sinkhole Attack
- C. Collision Attack
- D. Signal Jamming Attack
Answer: A
NEW QUESTION 2
A new wireless client is configured to join a 802.11 network. This client uses the same hardware and software as many of the other clients on the network. The client can see the network, but cannot connect. A wireless packet sniffer shows that the Wireless Access Point (WAP) is not responding to the association requests being sent by the wireless client. What is a possible source of this problem?
- A. The WAP does not recognize the client’s MAC address
- B. The client cannot see the SSID of the wireless network
- C. Client is configured for the wrong channel
- D. The wireless client is not configured to use DHCP
Answer: A
NEW QUESTION 3
Switches maintain a CAM Table that maps individual MAC addresses on the network to physical ports on the switch.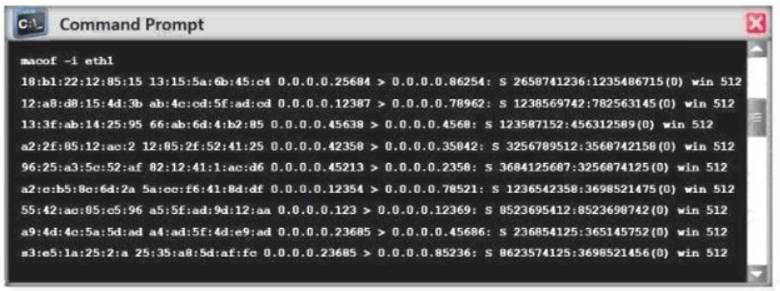
In MAC flooding attack, a switch is fed with many Ethernet frames, each containing different source MAC addresses, by the attacker. Switches have a limited memory for mapping various MAC addresses to physical ports. What happens when the CAM table becomes full?
- A. Switch then acts as hub by broadcasting packets to all machines on the network
- B. The CAM overflow table will cause the switch to crash causing Denial of Service
- C. The switch replaces outgoing frame switch factory default MAC address of FF:FF:FF:FF:FF:FF
- D. Every packet is dropped and the switch sends out SNMP alerts to the IDS port
Answer: A
NEW QUESTION 4
When a normal TCP connection starts, a destination host receives a SYN (synchronize/start) packet from a source host and sends back a SYN/ACK (synchronize acknowledge). The destination host must then hear an ACK (acknowledge) of the SYN/ACK before the connection is established. This is referred to as the "TCP three-way handshake." While waiting for the ACK to the SYN ACK, a connection queue of finite size on the destination host keeps track of connections waiting to be completed. This queue typically empties quickly since the ACK is expected to arrive a few milliseconds after the SYN ACK.
How would an attacker exploit this design by launching TCP SYN attack?
- A. Attacker generates TCP SYN packets with random destination addresses towards a victim host
- B. Attacker floods TCP SYN packets with random source addresses towards a victim host
- C. Attacker generates TCP ACK packets with random source addresses towards a victim host
- D. Attacker generates TCP RST packets with random source addresses towards a victim host
Answer: B
NEW QUESTION 5
Under what conditions does a secondary name server request a zone transfer from a primary name server?
- A. When a primary SOA is higher that a secondary SOA
- B. When a secondary SOA is higher that a primary SOA
- C. When a primary name server has had its service restarted
- D. When a secondary name server has had its service restarted
- E. When the TTL falls to zero
Answer: A
NEW QUESTION 6
As a Certified Ethical Hacker, you were contracted by a private firm to conduct an external security assessment through penetration testing.
What document describes the specifics of the testing, the associated violations, and essentially protects both the organization’s interest and your liabilities as a tester?
- A. Service Level Agreement
- B. Project Scope
- C. Rules of Engagement
- D. Non-Disclosure Agreement
Answer: C
NEW QUESTION 7
The tools which receive event logs from servers, network equipment, and applications, and perform analysis and correlation on those logs, and can generate alarms for security relevant issues, are known as what?
- A. network Sniffer
- B. Vulnerability Scanner
- C. Intrusion prevention Server
- D. Security incident and event Monitoring
Answer: D
NEW QUESTION 8
Study the snort rule given below and interpret the rule. alert tcp any any --> 192.168.1.0/24 111 (content:"|00 01 86 a5|"; msG. "mountd access";)
- A. An alert is generated when a TCP packet is generated from any IP on the 192.168.1.0 subnet and destined to any IP on port 111
- B. An alert is generated when any packet other than a TCP packet is seen on the network and destined for the 192.168.1.0 subnet
- C. An alert is generated when a TCP packet is originated from port 111 of any IP address to the 192.168.1.0 subnet
- D. An alert is generated when a TCP packet originating from any IP address is seen on the network and destined for any IP address on the 192.168.1.0 subnet on port 111
Answer: D
NEW QUESTION 9
In the context of password security, a simple dictionary attack involves loading a dictionary file (a text file full of dictionary words) into a cracking application such as L0phtCrack or John the Ripper, and running it against user accounts located by the application. The larger the word and word fragment selection, the more effective the dictionary attack is. The brute force method is the most inclusive, although slow. It usually tries every possible letter and number combination in its automated exploration. If you would use both brute force and dictionary methods combined together to have variation of words, what would you call such an attack?
- A. Full Blown
- B. Thorough
- C. Hybrid
- D. BruteDics
Answer: C
NEW QUESTION 10
How can you determine if an LM hash you extracted contains a password that is less than 8 characters long?
- A. There is no way to tell because a hash cannot be reversed
- B. The right most portion of the hash is always the same
- C. The hash always starts with AB923D
- D. The left most portion of the hash is always the same
- E. A portion of the hash will be all 0's
Answer: B
NEW QUESTION 11
Which of the following tools can be used to perform a zone transfer?
- A. NSLookup
- B. Finger
- C. Dig
- D. Sam Spade
- E. Host
- F. Netcat
- G. Neotrace
Answer: ACDE
NEW QUESTION 12
Study the following log extract and identify the attack.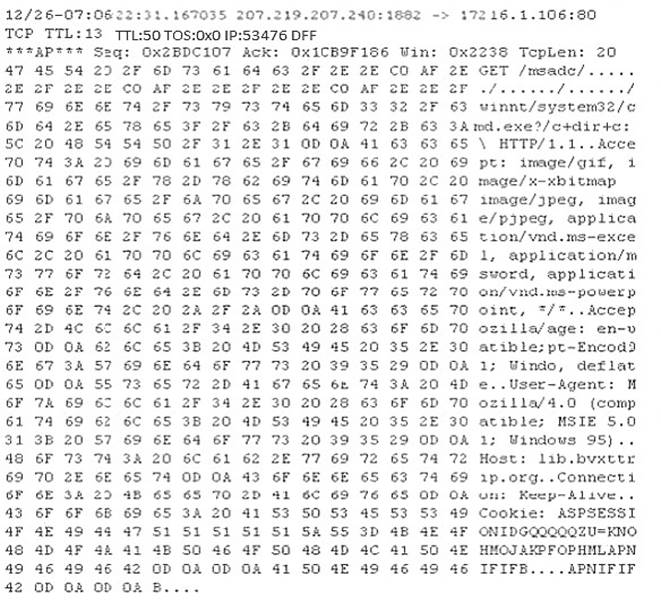
- A. Hexcode Attack
- B. Cross Site Scripting
- C. Multiple Domain Traversal Attack
- D. Unicode Directory Traversal Attack
Answer: D
NEW QUESTION 13
Eve is spending her day scanning the library computers. She notices that Alice is using a computer whose port 445 is active and listening. Eve uses the ENUM tool to enumerate Alice machine. From the command prompt, she types the following command.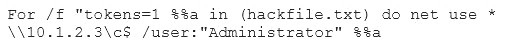
What is Eve trying to do?
- A. Eve is trying to connect as a user with Administrator privileges
- B. Eve is trying to enumerate all users with Administrative privileges
- C. Eve is trying to carry out a password crack for user Administrator
- D. Eve is trying to escalate privilege of the null user to that of Administrator
Answer: C
NEW QUESTION 14
Which type of sniffing technique is generally referred as MiTM attack?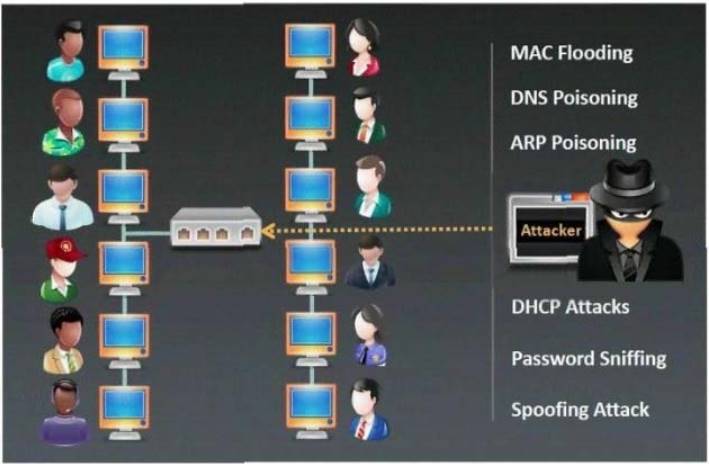
- A. Password Sniffing
- B. ARP Poisoning
- C. Mac Flooding
- D. DHCP Sniffing
Answer: B
NEW QUESTION 15
Which of the following represents the initial two commands that an IRC client sends to join an IRC network?
- A. USER, NICK
- B. LOGIN, NICK
- C. USER, PASS
- D. LOGIN, USER
Answer: A
NEW QUESTION 16
The network administrator at Spears Technology, Inc has configured the default gateway Cisco router's access-list as below:
You are hired to conduct security testing on their network.
You successfully brute-force the SNMP community string using a SNMP crack tool.
The access-list configured at the router prevents you from establishing a successful connection. You want to retrieve the Cisco configuration from the router. How would you proceed?
- A. Use the Cisco's TFTP default password to connect and download the configuration file
- B. Run a network sniffer and capture the returned traffic with the configuration file from the router
- C. Run Generic Routing Encapsulation (GRE) tunneling protocol from your computer to the router masking your IP address
- D. Send a customized SNMP set request with a spoofed source IP address in the range -192.168.1.0
Answer: BD
NEW QUESTION 17
The collection of potentially actionable, overt, and publicly available information is known as
- A. Open-source intelligence
- B. Real intelligence
- C. Social intelligence
- D. Human intelligence
Answer: A
NEW QUESTION 18
You went to great lengths to install all the necessary technologies to prevent hacking attacks, such as expensive firewalls, antivirus software, anti-spam systems and intrusion detection/prevention tools in your company's network. You have configured the most secure policies and tightened every device on your network. You are confident that hackers will never be able to gain access to your network with complex security system in place.
Your peer, Peter Smith who works at the same department disagrees with you.
He says even the best network security technologies cannot prevent hackers gaining access to the network because of presence of "weakest link" in the security chain.
What is Peter Smith talking about?
- A. Untrained staff or ignorant computer users who inadvertently become the weakest link in your securitychain
- B. "zero-day" exploits are the weakest link in the security chain since the IDS will not be able to detect these attacks
- C. "Polymorphic viruses" are the weakest link in the security chain since the Anti-Virus scanners will not be able to detect these attacks
- D. Continuous Spam e-mails cannot be blocked by your security system since spammers use different techniques to bypass the filters in your gateway
Answer: A
NEW QUESTION 19
The network team has well-established procedures to follow for creating new rules on the firewall. This includes having approval from a manager prior to implementing any new rules. While reviewing the firewall configuration, you notice a recently implemented rule but cannot locate manager approval for it. What would be a good step to have in the procedures for a situation like this?
- A. Have the network team document the reason why the rule was implemented without prior manager approval.
- B. Monitor all traffic using the firewall rule until a manager can approve it.
- C. Do not roll back the firewall rule as the business may be relying upon it, but try to get manager approval as soon as possible.
- D. Immediately roll back the firewall rule until a manager can approve it
Answer: D
NEW QUESTION 20
Log monitoring tools performing behavioral analysis have alerted several suspicious logins on a Linux server occurring during non-business hours. After further examination of all login activities, it is noticed that none of the logins have occurred during typical work hours. A Linux administrator who is investigating this problem realizes the system time on the Linux server is wrong by more than twelve hours. What protocol used on Linux servers to synchronize the time has stopped working?
- A. Time Keeper
- B. NTP
- C. PPP
- D. OSPP
Answer: B
NEW QUESTION 21
......
Thanks for reading the newest 312-50v11 exam dumps! We recommend you to try the PREMIUM Thedumpscentre.com 312-50v11 dumps in VCE and PDF here: https://www.thedumpscentre.com/312-50v11-dumps/ (254 Q&As Dumps)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (151-160)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (221-230)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (191-200)
- Real 412-79v10 Braindumps 2021
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (61-70)
- Best Quality 212-89 Lab 2021
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (321-330)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (111-120)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (441-449)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (161-170)

