312-50v11 Exam Questions - Online Test
312-50v11 Premium VCE File

150 Lectures, 20 Hours

Act now and download your EC-Council 312-50v11 test today! Do not waste time for the worthless EC-Council 312-50v11 tutorials. Download Up to the immediate present EC-Council Certified Ethical Hacker Exam (CEH v11) exam with real questions and answers and begin to learn EC-Council 312-50v11 with a classic professional.
Check 312-50v11 free dumps before getting the full version:
NEW QUESTION 1
What is one of the advantages of using both symmetric and asymmetric cryptography in SSL/TLS?
- A. Symmetric algorithms such as AES provide a failsafe when asymmetric methods fail.
- B. Asymmetric cryptography is computationally expensive in compariso
- C. However, it is well-suited to securely negotiate keys for use with symmetric cryptography.
- D. Symmetric encryption allows the server to securely transmit the session keys out-of-band.
- E. Supporting both types of algorithms allows less-powerful devices such as mobile phones to use symmetric encryption instead.
Answer: D
NEW QUESTION 2
Within the context of Computer Security, which of the following statements describes Social Engineering best?
- A. Social Engineering is the act of publicly disclosing information
- B. Social Engineering is the means put in place by human resource to perform time accounting
- C. Social Engineering is the act of getting needed information from a person rather than breaking into a system
- D. Social Engineering is a training program within sociology studies
Answer: C
NEW QUESTION 3
DNS cache snooping is a process of determining if the specified resource address is present in the DNS cache records. It may be useful during the examination of the network to determine what software update resources are used, thus discovering what software is installed.
What command is used to determine if the entry is present in DNS cache?
- A. nslookup -fullrecursive update.antivirus.com
- B. dnsnooping –rt update.antivirus.com
- C. nslookup -norecursive update.antivirus.com
- D. dns --snoop update.antivirus.com
Answer: C
NEW QUESTION 4
A company’s policy requires employees to perform file transfers using protocols which encrypt traffic. You suspect some employees are still performing file transfers using unencrypted protocols because the employees do not like changes. You have positioned a network sniffer to capture traffic from the laptops used by employees in the data ingest department. Using Wireshark to examine the captured traffic, which command can be used as display filter to find unencrypted file transfers?
- A. tcp.port = = 21
- B. tcp.port = 23
- C. tcp.port = = 21 | | tcp.port = =22
- D. tcp.port ! = 21
Answer: A
NEW QUESTION 5
Nathan is testing some of his network devices. Nathan is using Macof to try and flood the ARP cache of these switches.
If these switches' ARP cache is successfully flooded, what will be the result?
- A. The switches will drop into hub mode if the ARP cache is successfully flooded.
- B. If the ARP cache is flooded, the switches will drop into pix mode making it less susceptible to attacks.
- C. Depending on the switch manufacturer, the device will either delete every entry in its ARP cache or reroute packets to the nearest switch.
- D. The switches will route all traffic to the broadcast address created collisions.
Answer: A
NEW QUESTION 6
Which of the following tools performs comprehensive tests against web servers, including dangerous files and CGIs?
- A. Nikto
- B. John the Ripper
- C. Dsniff
- D. Snort
Answer: A
NEW QUESTION 7
What term describes the amount of risk that remains after the vulnerabilities are classified and the countermeasures have been deployed?
- A. Residual risk
- B. Impact risk
- C. Deferred risk
- D. Inherent risk
Answer: A
NEW QUESTION 8
One of your team members has asked you to analyze the following SOA record. What is the version? Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600 3600 604800 2400.) (Choose four.)
- A. 200303028
- B. 3600
- C. 604800
- D. 2400
- E. 60
- F. 4800
Answer: A
NEW QUESTION 9
Susan has attached to her company's network. She has managed to synchronize her boss's sessions with that of the file server. She then intercepted his traffic destined for the server, changed it the way she wanted to and then placed it on the server in his home directory.
What kind of attack is Susan carrying on?
- A. A sniffing attack
- B. A spoofing attack
- C. A man in the middle attack
- D. A denial of service attack
Answer: C
NEW QUESTION 10
A regional bank hires your company to perform a security assessment on their network after a recent data breach. The attacker was able to steal financial data from the bank by compromising only a single server. Based on this information, what should be one of your key recommendations to the bank?
- A. Place a front-end web server in a demilitarized zone that only handles external web traffic
- B. Require all employees to change their anti-virus program with a new one
- C. Move the financial data to another server on the same IP subnet
- D. Issue new certificates to the web servers from the root certificate authority
Answer: A
NEW QUESTION 11
Which of the following tools can be used for passive OS fingerprinting?
- A. nmap
- B. tcpdump
- C. tracert
- D. ping
Answer: B
NEW QUESTION 12
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c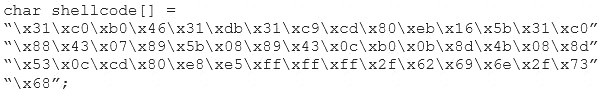
What is the hexadecimal value of NOP instruction?
- A. 0x60
- B. 0x80
- C. 0x70
- D. 0x90
Answer: D
NEW QUESTION 13
A hacker is an intelligent individual with excellent computer skills and the ability to explore a computer’s software and hardware without the owner’s permission. Their intention can either be to simply gain knowledge or to illegally make changes.
Which of the following class of hacker refers to an individual who works both offensively and defensively at various times?
- A. White Hat
- B. Suicide Hacker
- C. Gray Hat
- D. Black Hat
Answer: C
NEW QUESTION 14
Why containers are less secure that virtual machines?
- A. Host OS on containers has a larger surface attack.
- B. Containers may full fill disk space of the host.
- C. A compromise container may cause a CPU starvation of the host.
- D. Containers are attached to the same virtual network.
Answer: A
NEW QUESTION 15
What two conditions must a digital signature meet?
- A. Has to be the same number of characters as a physical signature and must be unique.
- B. Has to be unforgeable, and has to be authentic.
- C. Must be unique and have special characters.
- D. Has to be legible and neat.
Answer: B
NEW QUESTION 16
An Intrusion Detection System (IDS) has alerted the network administrator to a possibly malicious sequence of packets sent to a Web server in the network’s external DMZ. The packet traffic was captured by the IDS and saved to a PCAP file. What type of network tool can be used to determine if these packets are genuinely malicious or simply a false positive?
- A. Protocol analyzer
- B. Network sniffer
- C. Intrusion Prevention System (IPS)
- D. Vulnerability scanner
Answer: A
NEW QUESTION 17
In this attack, a victim receives an e-mail claiming from PayPal stating that their account has been disabled and confirmation is required before activation. The attackers then scam to collect not one but two credit card numbers, ATM PIN number and other personal details. Ignorant users usually fall prey to this scam. Which of the following statement is incorrect related to this attack?
- A. Do not reply to email messages or popup ads asking for personal or financial information
- B. Do not trust telephone numbers in e-mails or popup ads
- C. Review credit card and bank account statements regularly
- D. Antivirus, anti-spyware, and firewall software can very easily detect these type of attacks
- E. Do not send credit card numbers, and personal or financial information via e-mail
Answer: D
NEW QUESTION 18
Which command can be used to show the current TCP/IP connections?
- A. Netsh
- B. Netstat
- C. Net use connection
- D. Net use
Answer: A
NEW QUESTION 19
CompanyXYZ has asked you to assess the security of their perimeter email gateway. From your office in New York, you craft a specially formatted email message and send it across the Internet to an employee of CompanyXYZ. The employee of CompanyXYZ is aware of your test. Your email message looks like this:
From: jim_miller@companyxyz.com
To: michelle_saunders@companyxyz.com Subject: Test message Date: 4/3/2017 14:37
The employee of CompanyXYZ receives your email message.
This proves that CompanyXYZ’s email gateway doesn’t prevent what?
- A. Email Masquerading
- B. Email Harvesting
- C. Email Phishing
- D. Email Spoofing
Answer: D
NEW QUESTION 20
What does a firewall check to prevent particular ports and applications from getting packets into an organization?
- A. Transport layer port numbers and application layer headers
- B. Presentation layer headers and the session layer port numbers
- C. Network layer headers and the session layer port numbers
- D. Application layer port numbers and the transport layer headers
Answer: A
NEW QUESTION 21
......
P.S. Easily pass 312-50v11 Exam with 254 Q&As Allfreedumps.com Dumps & pdf Version, Welcome to Download the Newest Allfreedumps.com 312-50v11 Dumps: https://www.allfreedumps.com/312-50v11-dumps.html (254 New Questions)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (21-30)
- High quality 412-79v10 Exam Questions 2021
- The Secret Of EC-Council 312-75 Exam Dumps
- Real 412-79v10 Braindumps 2021
- EC-Council 412-79v10 Practice Test 2021
- Best Quality 212-89 Lab 2021
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (191-200)
- [2021-New] EC-Council 312-50v9 Dumps With Update Exam Questions (11-20)
- [2021-New] EC-Council 312-50v10 Dumps With Update Exam Questions (7-16)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (231-240)

