412-79v10 Exam Questions - Online Test
412-79v10 Premium VCE File

150 Lectures, 20 Hours

Exam Code: 412-79v10 (), Exam Name: EC-Council Certified Security Analyst (ECSA) V10, Certification Provider: EC-Council Certifitcation, Free Today! Guaranteed Training- Pass 412-79v10 Exam.
Online EC-Council 412-79v10 free dumps demo Below:
NEW QUESTION 1
Which one of the following is a supporting tool for 802.11 (wireless) packet injections, it spoofs 802.11 packets to verify whether the access point is valid or not?
- A. Airsnort
- B. Aircrack
- C. Airpwn
- D. WEPCrack
Answer: C
NEW QUESTION 2
Which of the following statement holds true for TCP Operation?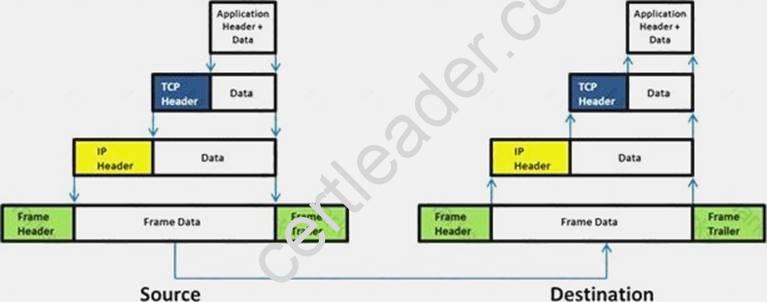
- A. Port numbers are used to know which application the receiving host should pass the data to
- B. Sequence numbers are used to track the number of packets lost in transmission
- C. Flow control shows the trend of a transmitting host overflowing the buffers in the receiving host
- D. Data transfer begins even before the connection is established
Answer: D
NEW QUESTION 3
Which of the following is not the SQL injection attack character?
- A. $
- B. PRINT
- C. #
- D. @@variable
Answer: A
NEW QUESTION 4
Identify the correct formula for Return on Investment (ROI).
- A. ROI = ((Expected Returns – Cost of Investment) / Cost of Investment) * 100
- B. ROI = (Expected Returns + Cost of Investment) / Cost of Investment
- C. ROI = (Expected Returns Cost of Investment) / Cost of Investment
- D. ROI = ((Expected Returns + Cost of Investment) / Cost of Investment) * 100
Answer: C
NEW QUESTION 5
Rules of Engagement (ROE) document provides certain rights and restriction to the test team for performing the test and helps testers to overcome legal, federal, and policy-related restrictions to use different penetration testing tools and techniques.
What is the last step in preparing a Rules of Engagement (ROE) document?
- A. Conduct a brainstorming session with top management and technical teams
- B. Decide the desired depth for penetration testing
- C. Conduct a brainstorming session with top management and technical teams
- D. Have pre-contract discussions with different pen-testers
Answer: C
NEW QUESTION 6
Identify the injection attack represented in the diagram below: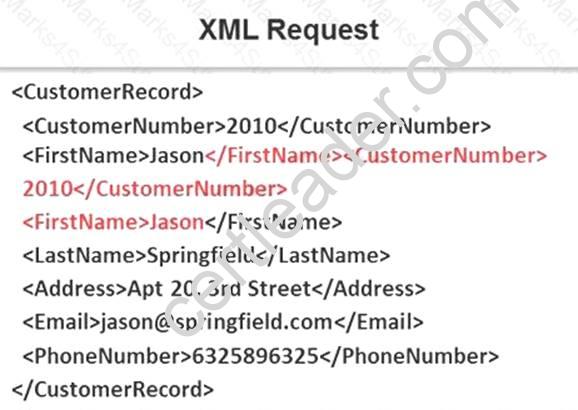
- A. XPath Injection Attack
- B. XML Request Attack
- C. XML Injection Attack
- D. Frame Injection Attack
Answer: C
NEW QUESTION 7
Tyler is setting up a wireless network for his business that he runs out of his home. He has followed all the directions from the ISP as well as the wireless router manual. He does not have any encryption set and the SSID is being broadcast.
On his laptop, he can pick up the wireless signal for short periods of time, but then the connection drops and the signal goes away. Eventually the wireless signal shows back up, but drops intermittently.
What could be Tyler issue with his home wireless network?
- A. 2.4 Ghz Cordless phones
- B. Satellite television
- C. CB radio
- D. Computers on his wired network
Answer: A
NEW QUESTION 8
Which of the following is developed to address security concerns on time and reduce the misuse or threat of attacks in an organization?
- A. Vulnerabilities checklists
- B. Configuration checklists
- C. Action Plan
- D. Testing Plan
Answer: A
NEW QUESTION 9
Which one of the following 802.11 types has WLAN as a network support?
- A. 802.11b
- B. 802.11-Legacy
- C. 802.11n
- D. 802.11g
Answer: C
NEW QUESTION 10
Attackers create secret accounts and gain illegal access to resources using backdoor while bypassing the authentication procedures. Creating a backdoor is a where an attacker obtains remote access to a computer on a network.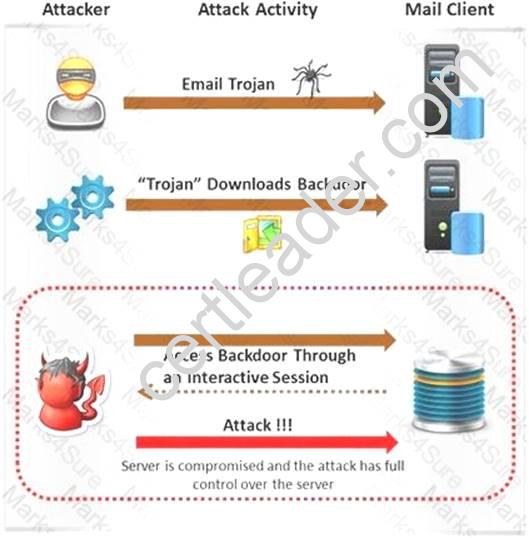
Which of the following techniques do attackers use to create backdoors to covertly gather critical information about a target machine?
- A. Internal network mapping to map the internal network of the target machine
- B. Port scanning to determine what ports are open or in use on the target machine
- C. Sniffing to monitor all the incoming and outgoing network traffic
- D. Social engineering and spear phishing attacks to install malicious programs on the target machine
Answer: D
NEW QUESTION 11
A Demilitarized Zone (DMZ) is a computer host or small network inserted as a “neutral zone” between a company’s private network and the outside public network. Usage of a protocol within a DMZ environment is highly variable based on the specific needs of an organization.
Privilege escalation, system is compromised when the code runs under root credentials, and DoS attacks are the basic weakness of which one of the following Protocol?
- A. Lightweight Directory Access Protocol (LDAP)
- B. Simple Network Management Protocol (SNMP)
- C. Telnet
- D. Secure Shell (SSH)
Answer: D
NEW QUESTION 12
Firewall and DMZ architectures are characterized according to its design. Which one of the following architectures is used when routers have better high-bandwidth data stream handling capacity?
- A. Weak Screened Subnet Architecture
- B. "Inside Versus Outside" Architecture
- C. "Three-Homed Firewall" DMZ Architecture
- D. Strong Screened-Subnet Architecture
Answer: A
NEW QUESTION 13
You are running known exploits against your network to test for possible vulnerabilities. To test the strength of your virus software, you load a test network to mimic your production network. Your software successfully blocks some simple macro and encrypted viruses.
You decide to really test the software by using virus code where the code rewrites itself entirely and the signatures change from child to child, but the functionality stays the same. What type of virus is this that you are testing?
- A. Metamorphic
- B. Oligomorhic
- C. Polymorphic
- D. Transmorphic
Answer: A
NEW QUESTION 14
Paulette works for an IT security consulting company that is currently performing an audit for the firm
ACE Unlimited. Paulette's duties include logging on to all the company's network equipment to ensure IOS versions are up-to-date and all the other security settings are as stringent as possible.
Paulette presents the following screenshot to her boss so he can inform the clients about necessary changes need to be made. From the screenshot, what changes should the client company make?
Exhibit: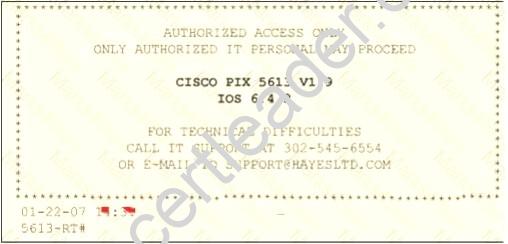
- A. The banner should not state "only authorized IT personnel may proceed"
- B. Remove any identifying numbers, names, or version information
- C. The banner should include the Cisco tech support contact information as well
- D. The banner should have more detail on the version numbers for the network equipment
Answer: B
NEW QUESTION 15
Snort, an open source network-based intrusion detection sensor, is the most widely installed NIDS in the world. It can be configured to run in the four modes. Which one of the following modes reads the packets off the network and displays them in a continuous stream on the console (screen)?
- A. Packet Sniffer Mode
- B. Packet Logger Mode
- C. Network Intrusion Detection System Mode
- D. Inline Mode
Answer: A
NEW QUESTION 16
One of the steps in information gathering is to run searches on a company using complex keywords in Google.
Which search keywords would you use in the Google search engine to find all the PowerPoint presentations containing information about a target company, ROCHESTON?
- A. ROCHESTON fileformat:+ppt
- B. ROCHESTON ppt:filestring
- C. ROCHESTON filetype:ppt
- D. ROCHESTON +ppt:filesearch
Answer: C
NEW QUESTION 17
Transmission control protocol accepts data from a data stream, divides it into chunks, and adds a TCP header creating a TCP segment. The TCP header is the first 24 bytes of a TCP segment that contains the parameters and state of an end-to-end TCP socket. It is used to track the state of communication between two TCP endpoints.
For a connection to be established or initialized, the two hosts must synchronize. The synchronization requires each side to send its own initial sequence number and to receive a confirmation of exchange in an acknowledgment (ACK) from the other side
The below diagram shows the TCP Header format: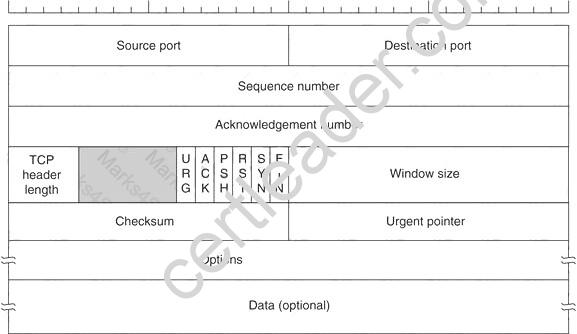
- A. 16 bits
- B. 32 bits
- C. 8 bits
- D. 24 bits
Answer: B
NEW QUESTION 18
SQL injection attack consists of insertion or "injection" of either a partial or complete SQL query via the data input or transmitted from the client (browser) to the web application. A successful SQL injection attack can:
i) Read sensitive data from the database
iii) Modify database data (insert/update/delete)
iii) Execute administration operations on the database (such as shutdown the DBMS)
iV) Recover the content of a given file existing on the DBMS file system or write files into the file system
v) Issue commands to the operating system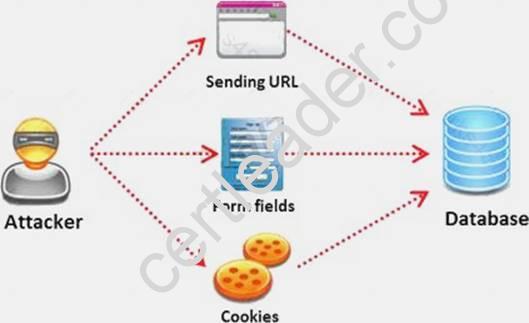
Pen tester needs to perform various tests to detect SQL injection vulnerability. He has to make a list of all input fields whose values could be used in crafting a SQL query, including the hidden fields of POST requests and then test them separately, trying to interfere with the query and to generate an error.
In which of the following tests is the source code of the application tested in a non-runtime environment to detect the SQL injection vulnerabilities?
- A. Automated Testing
- B. Function Testing
- C. Dynamic Testing
- D. Static Testing
Answer: D
NEW QUESTION 19
NTP protocol is used to synchronize the system clocks of computers with a remote time server or time source over a network. Which one of the following ports is used by NTP as its transport layer?
- A. TCP port 152
- B. UDP port 177
- C. UDP port 123
- D. TCP port 113
Answer: C
NEW QUESTION 20
Which of the following methods is used to perform server discovery?
- A. Banner Grabbing
- B. Who is Lookup
- C. SQL Injection
- D. Session Hijacking
Answer: B
Recommend!! Get the Full 412-79v10 dumps in VCE and PDF From Certshared, Welcome to Download: https://www.certshared.com/exam/412-79v10/ (New 201 Q&As Version)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (21-30)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (111-120)
- [2021-New] EC-Council 312-50v10 Dumps With Update Exam Questions (2-11)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (131-140)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (51-60)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (31-40)
- [2021-New] EC-Council 312-50v9 Dumps With Update Exam Questions (21-30)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (11-20)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (11-20)
- The Most Recent Guide To 312-49v9 Actual Test

