412-79v10 Exam Questions - Online Test
412-79v10 Premium VCE File

150 Lectures, 20 Hours

Your success in is our sole target and we develop all our in a way that facilitates the attainment of this target. Not only is our material the best you can find, it is also the most detailed and the most updated. for EC-Council 412-79v10 are written to the highest standards of technical accuracy.
Free demo questions for EC-Council 412-79v10 Exam Dumps Below:
NEW QUESTION 1
DNS information records provide important data about:
- A. Phone and Fax Numbers
- B. Location and Type of Servers
- C. Agents Providing Service to Company Staff
- D. New Customer
Answer: B
NEW QUESTION 2
You work as an IT security auditor hired by a law firm in Boston to test whether you can gain access to sensitive information about the company clients. You have rummaged through their trash and found very little information.
You do not want to set off any alarms on their network, so you plan on performing passive foot printing against their Web servers. What tool should you use?
- A. Nmap
- B. Netcraft
- C. Ping sweep
- D. Dig
Answer: B
NEW QUESTION 3
Jessica works as systems administrator for a large electronics firm. She wants to scan her network quickly to detect live hosts by using ICMP ECHO Requests. What type of scan is Jessica going to perform?
- A. Smurf scan
- B. Tracert
- C. Ping trace
- D. ICMP ping sweep
Answer: D
NEW QUESTION 4
Vulnerability assessment is an examination of the ability of a system or application, including current security procedures and controls, to withstand assault. It recognizes, measures, and classifies security vulnerabilities in a computer system, network, and communication channels.
A vulnerability assessment is used to identify weaknesses that could be exploited and predict the effectiveness of additional security measures in protecting information resources from attack.
Which of the following vulnerability assessment technique is used to test the web server infrastructure for any misconfiguration and outdated content?
- A. Passive Assessment
- B. Host-based Assessment
- C. External Assessment
- D. Application Assessment
Answer: D
NEW QUESTION 5
After passively scanning the network of Department of Defense (DoD), you switch over to active scanning to identify live hosts on their network. DoD is a large organization and should respond to any number of scans. You start an ICMP ping sweep by sending an IP packet to the broadcast address.
Only five hosts responds to your ICMP pings; definitely not the number of hosts you were expecting. Why did this ping sweep only produce a few responses?
- A. A switched network will not respond to packets sent to the broadcast address
- B. Only IBM AS/400 will reply to this scan
- C. Only Unix and Unix-like systems will reply to this scan
- D. Only Windows systems will reply to this scan
Answer: C
NEW QUESTION 6
Which among the following information is not furnished by the Rules of Engagement (ROE) document?
- A. Techniques for data collection from systems upon termination of the test
- B. Techniques for data exclusion from systems upon termination of the test
- C. Details on how data should be transmitted during and after the test
- D. Details on how organizational data is treated throughout and after the test
Answer: A
NEW QUESTION 7
Today, most organizations would agree that their most valuable IT assets reside within applications and databases. Most would probably also agree that these are areas that have the weakest levels of security, thus making them the prime target for malicious activity from system administrators, DBAs, contractors, consultants, partners, and customers.
Which of the following flaws refers to an application using poorly written encryption code to securely encrypt and store sensitive data in the database and allows an attacker to steal or modify weakly protected data such as credit card numbers, SSNs, and other authentication credentials?
- A. SSI injection attack
- B. Insecure cryptographic storage attack
- C. Hidden field manipulation attack
- D. Man-in-the-Middle attack
Answer: B
NEW QUESTION 8
After passing her CEH exam, Carol wants to ensure that her network is completely secure. She implements a DMZ, statefull firewall, NAT, IPSEC, and a packet filtering firewall. Since all security measures were taken, none of the hosts on her network can reach the Internet.
Why is that?
- A. IPSEC does not work with packet filtering firewalls
- B. NAT does not work with IPSEC
- C. NAT does not work with statefull firewalls
- D. Statefull firewalls do not work with packet filtering firewalls
Answer: B
NEW QUESTION 9
The objective of social engineering pen testing is to test the strength of human factors in a security chain within the organization. It is often used to raise the level of security awareness among employees.
The tester should demonstrate extreme care and professionalism during a social engineering pen test as it might involve legal issues such as violation of privacy and may result in an embarrassing situation for the organization.
Which of the following methods of attempting social engineering is associated with bribing, handing out gifts, and becoming involved in a personal relationship to befriend someone inside the company?
- A. Accomplice social engineering technique
- B. Identity theft
- C. Dumpster diving
- D. Phishing social engineering technique
Answer: A
NEW QUESTION 10
Which of the following contents of a pen testing project plan addresses the strengths, weaknesses, opportunities, and threats involved in the project?
- A. Project Goal
- B. Success Factors
- C. Objectives
- D. Assumptions
Answer: D
NEW QUESTION 11
Choose the correct option to define the Prefix Length.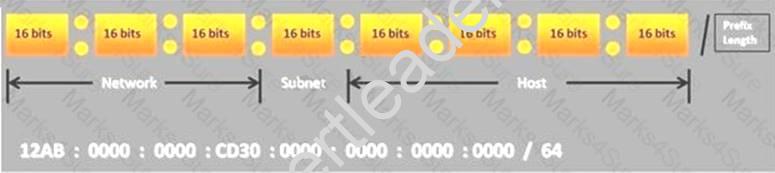
- A. Prefix Length = Subnet + Host portions
- B. Prefix Length = Network + Host portions
- C. Prefix Length = Network + Subnet portions
- D. Prefix Length = Network + Subnet + Host portions
Answer: C
NEW QUESTION 12
Terri works for a security consulting firm that is currently performing a penetration test on First National Bank in Tokyo. Terri's duties include bypassing firewalls and switches to gain access to the network. Terri sends an IP packet to one of the company's switches with ACK bit and the source address of her machine set.
What is Terri trying to accomplish by sending this IP packet?
- A. Poison the switch's MAC address table by flooding it with ACK bits
- B. Enable tunneling feature on the switch
- C. Trick the switch into thinking it already has a session with Terri's computer
- D. Crash the switch with a DoS attack since switches cannot send ACK bits
Answer: C
NEW QUESTION 13
Which of the following is the objective of Gramm-Leach-Bliley Act?
- A. To ease the transfer of financial information between institutions and banks
- B. To protect the confidentiality, integrity, and availability of data
- C. To set a new or enhanced standards for all U.
- D. public company boards, management and public accounting firms
- E. To certify the accuracy of the reported financial statement
Answer: A
NEW QUESTION 14
Firewall is an IP packet filter that enforces the filtering and security policies to the flowing network traffic. Using firewalls in IPv6 is still the best way of protection from low level attacks at the network and transport layers.
Which one of the following cannot handle routing protocols properly?
- A. “Internet-router-firewall-net architecture”
- B. “Internet-firewall-router-net architecture”
- C. “Internet-firewall/router(edge device)-net architecture”
- D. “Internet-firewall -net architecture”
Answer: B
NEW QUESTION 15
Meyer Electronics Systems just recently had a number of laptops stolen out of their office. On these laptops contained sensitive corporate information regarding patents and company strategies.
A month after the laptops were stolen, a competing company was found to have just developed products that almost exactly duplicated products that Meyer produces.
What could have prevented this information from being stolen from the laptops?
- A. SDW Encryption
- B. EFS Encryption
- C. DFS Encryption
- D. IPS Encryption
Answer: B
NEW QUESTION 16
If a web application sends HTTP cookies as its method for transmitting session tokens, it may be vulnerable which of the following attacks?
- A. Parameter tampering Attack
- B. Sql injection attack
- C. Session Hijacking
- D. Cross-site request attack
Answer: D
NEW QUESTION 17
From where can clues about the underlying application environment can be collected?
- A. From source code
- B. From file types and directories
- C. From executable file
- D. From the extension of the file
Answer: D
NEW QUESTION 18
Which of the following scan option is able to identify the SSL services?
- A. –sS
- B. –sV
- C. –sU
- D. –sT
Answer: B
NEW QUESTION 19
A wireless intrusion detection system (WIDS) monitors the radio spectrum for the presence of unauthorized, rogue access points and the use of wireless attack tools.
The system monitors the radio spectrum used by wireless LANs, and immediately alerts a systems administrator whenever a rogue access point is detected. Conventionally it is achieved by comparing the MAC address of the participating wireless devices.
Which of the following attacks can be detected with the help of wireless intrusion detection system (WIDS)?
- A. Social engineering
- B. SQL injection
- C. Parameter tampering
- D. Man-in-the-middle attack
Answer: D
NEW QUESTION 20
Windows stores user passwords in the Security Accounts Manager database (SAM), or in the Active Directory database in domains. Passwords are never stored in clear text; passwords are hashed and the results are stored in the SAM.
NTLM and LM authentication protocols are used to securely store a user's password in the SAM database using different hashing methods.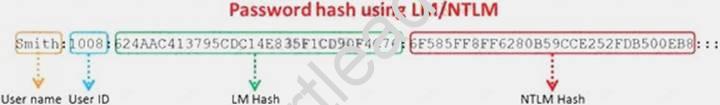
The SAM file in Windows Server 2008 is located in which of the following locations?
- A. c:windowssystem32configSAM
- B. c:windowssystem32driversSAM
- C. c:windowssystem32SetupSAM
- D. c:windowssystem32BootSAM
Answer: D
Recommend!! Get the Full 412-79v10 dumps in VCE and PDF From Dumpscollection, Welcome to Download: http://www.dumpscollection.net/dumps/412-79v10/ (New 201 Q&As Version)
- [2021-New] EC-Council 312-50v9 Dumps With Update Exam Questions (1-10)
- How Many Questions Of 312-50v11 Free Dumps
- [2021-New] EC-Council 312-50v10 Dumps With Update Exam Questions (7-16)
- [2021-New] EC-Council 312-50v9 Dumps With Update Exam Questions (31-40)
- [2021-New] EC-Council 312-50v9 Dumps With Update Exam Questions (31-40)
- [2021-New] EC-Council 312-50v9 Dumps With Update Exam Questions (21-30)
- [2021-New] EC-Council 312-50v9 Dumps With Update Exam Questions (11-20)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (111-120)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (121-130)
- The Secret Of EC-Council 312-85 Dumps

