412-79v10 Exam Questions - Online Test
412-79v10 Premium VCE File

150 Lectures, 20 Hours

It is more faster and easier to pass the by using . Immediate access to the and find the same core area with professionally verified answers, then PASS your exam with a high score now.
Free 412-79v10 Demo Online For Microsoft Certifitcation:
NEW QUESTION 1
What is the difference between penetration testing and vulnerability testing?
- A. Penetration testing goes one step further than vulnerability testing; while vulnerability tests check for known vulnerabilities, penetration testing adopts the concept of ‘in-depth ethical hacking’
- B. Penetration testing is based on purely online vulnerability analysis while vulnerability testing engages ethical hackers to find vulnerabilities
- C. Vulnerability testing is more expensive than penetration testing
- D. Penetration testing is conducted purely for meeting compliance standards while vulnerability testing is focused on online scans
Answer: A
NEW QUESTION 2
Which of the following documents helps in creating a confidential relationship between the pen tester and client to protect critical and confidential information or trade secrets?
- A. Penetration Testing Agreement
- B. Rules of Behavior Agreement
- C. Liability Insurance
- D. Non-Disclosure Agreement
Answer: D
NEW QUESTION 3
You are carrying out the last round of testing for your new website before it goes live. The website has
many dynamic pages and connects to a SQL backend that accesses your product inventory in a database. You come across a web security site that recommends inputting the following code into a search field on web pages to check for vulnerabilities:
<script>alert("This is a test.")</script>
When you type this and click on search, you receive a pop-up window that says: "This is a test."
What is the result of this test?
- A. Your website is vulnerable to web bugs
- B. Your website is vulnerable to XSS
- C. Your website is not vulnerable
- D. Your website is vulnerable to SQL injection
Answer: B
NEW QUESTION 4
One needs to run “Scan Server Configuration” tool to allow a remote connection to Nessus from the remote Nessus clients. This tool allows the port and bound interface of the Nessus daemon to be configured.
By default, the Nessus daemon listens to connections on which one of the following?
- A. Localhost (127.0.0.1) and port 1241
- B. Localhost (127.0.0.1) and port 1240
- C. Localhost (127.0.0.1) and port 1246
- D. Localhost (127.0.0.0) and port 1243
Answer: A
NEW QUESTION 5
Output modules allow Snort to be much more flexible in the formatting and presentation of output to its users. Snort has 9 output plug-ins that push out data in different formats. Which one of the following output plug-ins allows alert data to be written in a format easily importable to a database?
- A. unified
- B. csv
- C. alert_unixsock
- D. alert_fast
Answer: B
NEW QUESTION 6
A WHERE clause in SQL specifies that a SQL Data Manipulation Language (DML) statement should only affect rows that meet specified criteria. The criteria are expressed in the form of predicates. WHERE clauses are not mandatory clauses of SQL DML statements, but can be used to limit the number of rows affected by a SQL DML statement or returned by a query.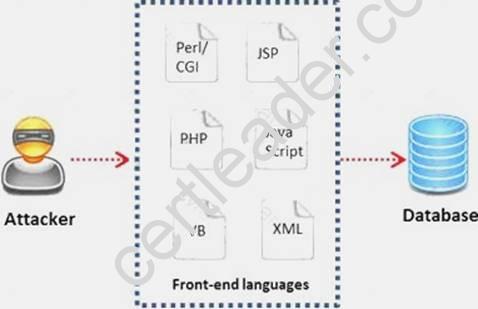
A pen tester is trying to gain access to a database by inserting exploited query statements with a WHERE clause. The pen tester wants to retrieve all the entries from the database using the WHERE clause from a particular table (e.g. StudentTable).
What query does he need to write to retrieve the information?
- A. EXTRACT* FROM StudentTable WHERE roll_number = 1 order by 1000
- B. DUMP * FROM StudentTable WHERE roll_number = 1 AND 1=1—
- C. SELECT * FROM StudentTable WHERE roll_number = '' or '1' = '1‘
- D. RETRIVE * FROM StudentTable WHERE roll_number = 1'#
Answer: C
NEW QUESTION 7
An external intrusion test and analysis identify security weaknesses and strengths of the client's systems and networks as they appear from outside the client's security perimeter, usually from the Internet.
The goal of an external intrusion test and analysis is to demonstrate the existence of known vulnerabilities that could be exploited by an external attacker.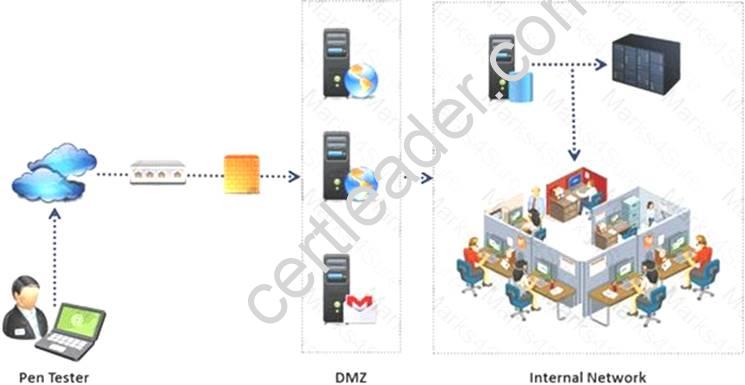
During external penetration testing, which of the following scanning techniques allow you to determine a port’s state without making a full connection to the host?
- A. XMAS Scan
- B. SYN scan
- C. FIN Scan
- D. NULL Scan
Answer: B
NEW QUESTION 8
What are placeholders (or markers) in an HTML document that the web server will dynamically replace with data just before sending the requested documents to a browser?
- A. Server Side Includes
- B. Sort Server Includes
- C. Server Sort Includes
- D. Slide Server Includes
Answer: A
NEW QUESTION 9
Transmission Control Protocol (TCP) is a connection-oriented four layer protocol. It is responsible for breaking messages into segments, re-assembling them at the destination station, and re-sending. Which one of the following protocols does not use the TCP?
- A. Reverse Address Resolution Protocol (RARP)
- B. HTTP (Hypertext Transfer Protocol)
- C. SMTP (Simple Mail Transfer Protocol)
- D. Telnet
Answer: A
NEW QUESTION 10
What is the maximum value of a “tinyint” field in most database systems?
- A. 222
- B. 224 or more
- C. 240 or less
- D. 225 or more
Answer: D
NEW QUESTION 11
Which of the following statements is true about Multi-Layer Intrusion Detection Systems (mIDSs)?
- A. Decreases consumed employee time and increases system uptime
- B. Increases detection and reaction time
- C. Increases response time
- D. Both Decreases consumed employee time and increases system uptime and Increases response time
Answer: A
NEW QUESTION 12
The Internet is a giant database where people store some of their most private information on the cloud, trusting that the service provider can keep it all safe. Trojans, Viruses, DoS attacks, website defacement, lost computers, accidental publishing, and more have all been sources of major leaks over the last 15 years.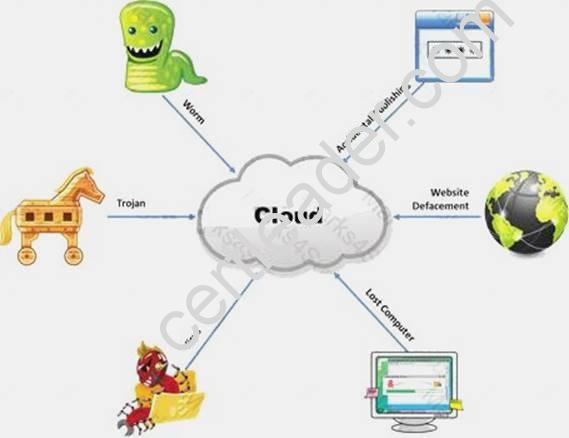
What is the biggest source of data leaks in organizations today?
- A. Weak passwords and lack of identity management
- B. Insufficient IT security budget
- C. Rogue employees and insider attacks
- D. Vulnerabilities, risks, and threats facing Web sites
Answer: C
NEW QUESTION 13
Mason is footprinting an organization to gather competitive intelligence. He visits the company's website for contact information and telephone numbers but does not find any. He knows the entire staff directory was listed on their website 12 months. How can he find the directory?
- A. Visit Google’s search engine and view the cached copy
- B. Crawl and download the entire website using the Surfoffline tool and save them to his computer
- C. Visit the company's partners’ and customers' website for this information
- D. Use Way Back Machine in Archive.org web site to retrieve the Internet archive
Answer: D
NEW QUESTION 14
A framework for security analysis is composed of a set of instructions, assumptions, and limitations to analyze and solve security concerns and develop threat free applications.
Which of the following frameworks helps an organization in the evaluation of the company’s information security with that of the industrial standards?
- A. Microsoft Internet Security Framework
- B. Information System Security Assessment Framework
- C. The IBM Security Framework
- D. Nortell’s Unified Security Framework
Answer: B
NEW QUESTION 15
The term social engineering is used to describe the various tricks used to fool people (employees, business partners, or customers) into voluntarily giving away information that would not normally be known to the general public.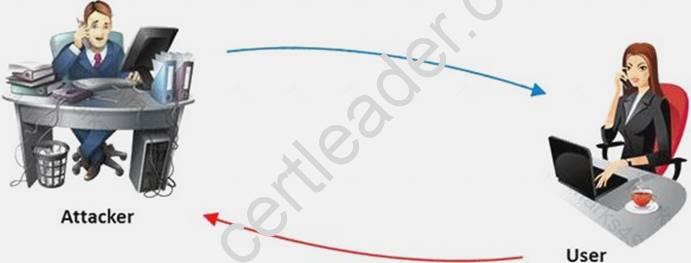
What is the criminal practice of social engineering where an attacker uses the telephone system in an attempt to scam the user into surrendering private information?
- A. Phishing
- B. Spoofing
- C. Tapping
- D. Vishing
Answer: D
NEW QUESTION 16
Software firewalls work at which layer of the OSI model?
- A. Data Link
- B. Network
- C. Transport
- D. Application
Answer: A
NEW QUESTION 17
An attacker injects malicious query strings in user input fields to bypass web service authentication mechanisms and to access back-end databases. Which of the following attacks is this?
- A. Frame Injection Attack
- B. LDAP Injection Attack
- C. XPath Injection Attack
- D. SOAP Injection Attack
Answer: D
NEW QUESTION 18
Which of the following is not a characteristic of a firewall?
- A. Manages public access to private networked resources
- B. Routes packets between the networks
- C. Examines all traffic routed between the two networks to see if it meets certain criteria
- D. Filters only inbound traffic but not outbound traffic
Answer: D
NEW QUESTION 19
Michael works for Kimball Construction Company as senior security analyst. As part of yearly security audit, Michael scans his network for vulnerabilities. Using Nmap, Michael conducts XMAS scan and most of the ports scanned do not give a response. In what state are these ports?
- A. Filtered
- B. Stealth
- C. Closed
- D. Open
Answer: D
NEW QUESTION 20
An antenna is a device that is designed to transmit and receive the electromagnetic waves that are generally called radio waves. Which one of the following types of antenna is developed from waveguide technology?
- A. Leaky Wave Antennas
- B. Aperture Antennas
- C. Reflector Antenna
- D. Directional Antenna
Answer: B
P.S. Easily pass 412-79v10 Exam with 201 Q&As Certstest Dumps & pdf Version, Welcome to Download the Newest Certstest 412-79v10 Dumps: https://www.certstest.com/dumps/412-79v10/ (201 New Questions)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (321-330)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (61-70)
- [2021-New] EC-Council 312-50v10 Dumps With Update Exam Questions (7-16)
- [2021-New] EC-Council 312-50v9 Dumps With Update Exam Questions (11-20)
- Real 412-79v10 Braindumps 2021
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (161-170)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (311-320)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (261-270)
- The Most Recent Guide To 312-49v9 Actual Test
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (111-120)

