412-79v10 Exam Questions - Online Test
412-79v10 Premium VCE File

150 Lectures, 20 Hours

We provide which are the best for clearing 412-79v10 test, and to get certified by EC-Council EC-Council Certified Security Analyst (ECSA) V10. The covers all the knowledge points of the real 412-79v10 exam. Crack your EC-Council 412-79v10 Exam with latest dumps, guaranteed!
EC-Council 412-79v10 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
What is the target host IP in the following command?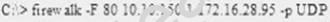
- A. Firewalk does not scan target hosts
- B. 172.16.28.95
- C. This command is using FIN packets, which cannot scan target hosts
- D. 10.10.150.1
Answer: A
NEW QUESTION 2
Timing is an element of port-scanning that can catch one unaware. If scans are taking too long to complete or obvious ports are missing from the scan, various time parameters may need to be adjusted.
Which one of the following scanned timing options in NMAP’s scan is useful across slow WAN links or to hide the scan?
- A. Paranoid
- B. Sneaky
- C. Polite
- D. Normal
Answer: C
NEW QUESTION 3
Identify the person who will lead the penetration-testing project and be the client point of contact.
- A. Database Penetration Tester
- B. Policy Penetration Tester
- C. Chief Penetration Tester
- D. Application Penetration Tester
Answer: C
NEW QUESTION 4
Which vulnerability assessment phase describes the scope of the assessment, identifies and ranks the critical assets, and creates proper information protection procedures such as effective planning, scheduling, coordination, and logistics?
- A. Threat-Assessment Phase
- B. Pre-Assessment Phase
- C. Assessment Phase
- D. Post-Assessment Phase
Answer: B
NEW QUESTION 5
Which of the following reports provides a summary of the complete pen testing process, its outcomes, and recommendations?
- A. Vulnerability Report
- B. Executive Report
- C. Client-side test Report
- D. Host Report
Answer: B
NEW QUESTION 6
What sort of vulnerability assessment approach starts by building an inventory of protocols found on the machine?
- A. Inference-based Assessment
- B. Service-based Assessment Solutions
- C. Product-based Assessment Solutions
- D. Tree-based Assessment
Answer: A
NEW QUESTION 7
Which of the following pen testing reports provides detailed information about all the tasks performed during penetration testing?
- A. Client-Side Test Report
- B. Activity Report
- C. Host Report
- D. Vulnerability Report
Answer: A
NEW QUESTION 8
Which of the following is the range for assigned ports managed by the Internet Assigned Numbers Authority (IANA)?
- A. 3001-3100
- B. 5000-5099
- C. 6666-6674
- D. 0 – 1023
Answer: D
NEW QUESTION 9
Which one of the following log analysis tools is used for analyzing the server’s log files?
- A. Performance Analysis of Logs tool
- B. Network Sniffer Interface Test tool
- C. Ka Log Analyzer tool
- D. Event Log Tracker tool
Answer: C
NEW QUESTION 10
Kyle is performing the final testing of an application he developed for the accounting department. His last round of testing is to ensure that the program is as secure as possible. Kyle runs the following command. What is he testing at this point?
include <stdio.h>
#include <string.h>
int main(int argc, char *argv[])
{
char buffer[10]; if (argc < 2)
{
fprintf(stderr, "USAGE: %s stringn", argv[0]); return 1;
}
strcpy(buffer, argv[1]); return 0;
}
- A. Buffer overflow
- B. Format string bug
- C. Kernal injection
- D. SQL injection
Answer: A
NEW QUESTION 11
HTTP protocol specifies that arbitrary binary characters can be passed within the URL by using %xx notation, where 'xx' is the
- A. ASCII value of the character
- B. Binary value of the character
- C. Decimal value of the character
- D. Hex value of the character
Answer: D
NEW QUESTION 12
Which one of the following is a command line tool used for capturing data from the live network and copying those packets to a file?
- A. Wireshark: Capinfos
- B. Wireshark: Tcpdump
- C. Wireshark: Text2pcap
- D. Wireshark: Dumpcap
Answer: D
NEW QUESTION 13
Simon is a former employee of Trinitron XML Inc. He feels he was wrongly terminated and wants to hack into his former company's network. Since Simon remembers some of the server names, he attempts to run the AXFR and IXFR commands using DIG. What is Simon trying to accomplish here?
- A. Enumerate all the users in the domain
- B. Perform DNS poisoning
- C. Send DOS commands to crash the DNS servers
- D. Perform a zone transfer
Answer: D
NEW QUESTION 14
You are trying to locate Microsoft Outlook Web Access Default Portal using Google search on the Internet. What search string will you use to locate them?
- A. intitle:"exchange server"
- B. outlook:"search"
- C. locate:"logon page"
- D. allinurl:"exchange/logon.asp"
Answer: D
NEW QUESTION 15
Harold is a security analyst who has just run the rdisk /s command to grab the backup SAM file on a computer. Where should Harold navigate on the computer to find the file?
- A. %systemroot%LSA
- B. %systemroot%repair
- C. %systemroot%system32driversetc
- D. %systemroot%system32LSA
Answer: B
NEW QUESTION 16
Which one of the following tools of trade is a commercial shellcode and payload generator written in Python by Dave Aitel?
- A. Microsoft Baseline Security Analyzer (MBSA)
- B. CORE Impact
- C. Canvas
- D. Network Security Analysis Tool (NSAT)
Answer: C
NEW QUESTION 17
Julia is a senior security analyst for Berber Consulting group. She is currently working on a contract for a small accounting firm in Florida. They have given her permission to perform social engineering attacks on the company to see if their in-house training did any good. Julia calls the main number for the accounting firm and talks to the receptionist. Julia says that she is an IT technician from the company's main office in Iowa.
She states that she needs the receptionist's network username and password to troubleshoot a problem they are having. Julia says that Bill Hammond, the CEO of the company, requested this information. After hearing the name of the CEO, the receptionist gave Julia all the information she asked for.
What principal of social engineering did Julia use?
- A. Reciprocation
- B. Friendship/Liking
- C. Social Validation
- D. Scarcity
Answer: A
NEW QUESTION 18
Which of the following protocols cannot be used to filter VoIP traffic?
- A. Media Gateway Control Protocol (MGCP)
- B. Real-time Transport Control Protocol (RTCP)
- C. Session Description Protocol (SDP)
- D. Real-Time Publish Subscribe (RTPS)
Answer: D
NEW QUESTION 19
A framework is a fundamental structure used to support and resolve complex issues. The framework that delivers an efficient set of technologies in order to develop applications which are more secure in using Internet and Intranet is:
- A. Microsoft Internet Security Framework
- B. Information System Security Assessment Framework (ISSAF)
- C. Bell Labs Network Security Framework
- D. The IBM Security Framework
Answer: A
NEW QUESTION 20
Identify the policy that defines the standards for the organizational network connectivity and security standards for computers that are connected in the organizational network.
- A. Information-Protection Policy
- B. Special-Access Policy
- C. Remote-Access Policy
- D. Acceptable-Use Policy
Answer: C
P.S. DumpSolutions now are offering 100% pass ensure 412-79v10 dumps! All 412-79v10 exam questions have been updated with correct answers: https://www.dumpsolutions.com/412-79v10-dumps/ (201 New Questions)
- Refined 412-79v10 Dumps 2021
- EC-Council 412-79v10 Practice Test 2021
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (11-20)
- How Many Questions Of 312-50v12 Exam Topics
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (291-300)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (1-10)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (221-230)
- Best Quality 212-89 Lab 2021
- Pinpoint EC-Council 712-50 Exam Question Online
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (141-150)

