350-701 Exam Questions - Online Test
350-701 Premium VCE File

150 Lectures, 20 Hours

We provide real 350-701 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass Cisco 350-701 Exam quickly & easily. The 350-701 PDF type is available for reading and printing. You can print more and practice many times. With the help of our Cisco 350-701 dumps pdf and vce product and material, you can easily pass the 350-701 exam.
Free 350-701 Demo Online For Cisco Certifitcation:
NEW QUESTION 1
What does the Cloudlock Apps Firewall do to mitigate security concerns from an application perspective?
- A. It allows the administrator to quarantine malicious files so that the application can function, just not maliciously.
- B. It discovers and controls cloud apps that are connected to a company’s corporate environment.
- C. It deletes any application that does not belong in the network.
- D. It sends the application information to an administrator to act on.
Answer: B
Explanation:
Reference: https://www.cisco.com/c/en/us/products/security/cloudlock/index.html#~features
NEW QUESTION 2
Refer to the exhibit.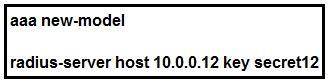
Which statement about the authentication protocol used in the configuration is true?
- A. The authentication request contains only a password
- B. The authentication request contains only a username
- C. The authentication and authorization requests are grouped in a single packet.
- D. There are separate authentication and authorization request packets.
Answer: C
NEW QUESTION 3
In which cloud services model is the tenant responsible for virtual machine OS patching?
- A. IaaS
- B. UCaaS
- C. PaaS
- D. SaaS
Answer: A
Explanation:
Reference: https://www.cmswire.com/cms/information-management/cloud-service-models-iaas-saas-paas-how-microsoft-office-365-azure-fit-in-021672.php
NEW QUESTION 4
What is a language format designed to exchange threat intelligence that can be transported over the TAXII protocol?
- A. STIX
- B. XMPP
- C. pxGrid
- D. SMTP
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/web_security/scancenter/administrator/guide/b_ScanCenter_Administrator_Guide/b_ScanCenter_Administrator_Guide_chapter_0100011.pdf
NEW QUESTION 5
An engineer is configuring AMP for endpoints and wants to block certain files from executing. Which outbreak control method is used to accomplish this task?
- A. device flow correlation
- B. simple detections
- C. application blocking list
- D. advanced custom detections
Answer: C
NEW QUESTION 6
Which two preventive measures are used to control cross-site scripting? (Choose two.)
- A. Enable client-side scripts on a per-domain basis.
- B. Incorporate contextual output encoding/escaping.
- C. Disable cookie inspection in the HTML inspection engine.
- D. Run untrusted HTML input through an HTML sanitization engine.
- E. SameSite cookie attribute should not be used.
Answer: AB
NEW QUESTION 7
Refer to the exhibit.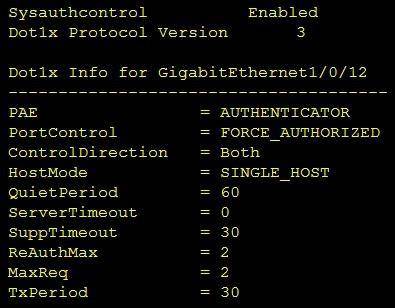
Which command was used to display this output?
- A. show dot1x all
- B. show dot1x
- C. show dot1x all summary
- D. show dot1x interface gi1/0/12
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_8021x/configuration/xe-3se/3850/sec-user-8021x-xe-3se-3850-book/config-ieee-802x-pba.html
NEW QUESTION 8
Which statement about IOS zone-based firewalls is true?
- A. An unassigned interface can communicate with assigned interfaces
- B. Only one interface can be assigned to a zone.
- C. An interface can be assigned to multiple zones.
- D. An interface can be assigned only to one zone.
Answer: D
Explanation:
Reference: https://www.cisco.com/c/en/us/support/docs/security/ios-firewall/98628-zone-design-guide.html
NEW QUESTION 9
Which two features are used to configure Cisco ESA with a multilayer approach to fight viruses and malware? (Choose two.)
- A. Sophos engine
- B. white list
- C. RAT
- D. outbreak filters
- E. DLP
Answer: AD
NEW QUESTION 10
What is the difference between deceptive phishing and spear phishing?
- A. Deceptive phishing is an attacked aimed at a specific user in the organization who holds a C-level role.
- B. A spear phishing campaign is aimed at a specific person versus a group of people.
- C. Spear phishing is when the attack is aimed at the C-level executives of an organization.
- D. Deceptive phishing hijacks and manipulates the DNS server of the victim and redirects the user to a false webpage.
Answer: B
NEW QUESTION 11
What is a characteristic of Dynamic ARP Inspection?
- A. DAI determines the validity of an ARP packet based on valid IP to MAC address bindings from the DHCP snooping binding database.
- B. In a typical network, make all ports as trusted except for the ports connecting to switches, which are untrusted.
- C. DAI associates a trust state with each switch.
- D. DAI intercepts all ARP requests and responses on trusted ports only.
Answer: A
NEW QUESTION 12
Which command enables 802.1X globally on a Cisco switch?
- A. dot1x system-auth-control
- B. dot1x pae authenticator
- C. authentication port-control auto
- D. aaa new-model
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/routers/nfvis/switch_command/b-nfvis-switch-command-reference/802_1x_commands.html
NEW QUESTION 13
Which two capabilities does TAXII support? (Choose two.)
- A. exchange
- B. pull messaging
- C. binding
- D. correlation
- E. mitigating
Answer: BC
NEW QUESTION 14
The main function of northbound APIs in the SDN architecture is to enable communication between which two areas of a network?
- A. SDN controller and the cloud
- B. management console and the SDN controller
- C. management console and the cloud
- D. SDN controller and the management solution
Answer: D
NEW QUESTION 15
An administrator wants to ensure that all endpoints are compliant before users are allowed access on the corporate network. The endpoints must have the corporate antivirus application installed and be running the latest build of Windows 10. What must the administrator implement to ensure that all devices are compliant before they are allowed on the network?
- A. Cisco Identity Services Engine and AnyConnect Posture module
- B. Cisco Stealthwatch and Cisco Identity Services Engine integration
- C. Cisco ASA firewall with Dynamic Access Policies configured
- D. Cisco Identity Services Engine with PxGrid services enabled
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect46/administration/guide/b_AnyConnect_Administrator_Guide_4-6/configure-posture.html
NEW QUESTION 16
What are the two most commonly used authentication factors in multifactor authentication? (Choose two.)
- A. biometric factor
- B. time factor
- C. confidentiality factor
- D. knowledge factor
- E. encryption factor
Answer: AD
NEW QUESTION 17
What is a characteristic of traffic storm control behavior?
- A. Traffic storm control drops all broadcast and multicast traffic if the combined traffic exceeds the level within the interval.
- B. Traffic storm control cannot determine if the packet is unicast or broadcast.
- C. Traffic storm control monitors incoming traffic levels over a 10-second traffic storm control interval.
- D. Traffic storm control uses the Individual/Group bit in the packet source address to determine if the packet is unicast or broadcast.
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/routers/7600/ios/12-1E/configuration/guide/storm.html
NEW QUESTION 18
What is a required prerequisite to enable malware file scanning for the Secure Internet Gateway?
- A. Enable IP Layer enforcement.
- B. Activate the Advanced Malware Protection license
- C. Activate SSL decryption.
- D. Enable Intelligent Proxy.
Answer: D
NEW QUESTION 19
Which SNMPv3 configuration must be used to support the strongest security possible?
- A. asa-host(config)#snmp-server group myv3 v3 priv asa-host(config)#snmp-server user andy myv3 auth sha cisco priv des ciscXXXXXXXX asa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy
- B. asa-host(config)#snmp-server group myv3 v3 noauth asa- host(config)#snmp-server user andy myv3 auth sha cisco priv aes 256 ciscXXXXXXXX asa- host(config)#snmp-server host inside 10.255.254.1 version 3 andy
- C. asa-host(config)#snmp- server group myv3 v3 noauth asa-host(config)#snmp-server user andy myv3 auth sha cisco priv 3des ciscXXXXXXXXasa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy
- D. asa- host(config)#snmp-server group myv3 v3 priv asa-host(config)#snmp-server user andy myv3 auth sha cisco priv aes 256 ciscXXXXXXXX asa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy
Answer: D
NEW QUESTION 20
On which part of the IT environment does DevSecOps focus?
- A. application development
- B. wireless network
- C. data center
- D. perimeter network
Answer: A
NEW QUESTION 21
Which two prevention techniques are used to mitigate SQL injection attacks? (Choose two.)
- A. Check integer, float, or Boolean string parameters to ensure accurate values.
- B. Use prepared statements and parameterized queries.
- C. Secure the connection between the web and the app tier.
- D. Write SQL code instead of using object-relational mapping libraries.
- E. Block SQL code execution in the web application database login.
Answer: AB
Explanation:
Reference: https://en.wikipedia.org/wiki/SQL_injection
NEW QUESTION 22
......
P.S. Easily pass 350-701 Exam with 102 Q&As Simply pass Dumps & pdf Version, Welcome to Download the Newest Simply pass 350-701 Dumps: https://www.simply-pass.com/Cisco-exam/350-701-dumps.html (102 New Questions)
- [2021-New] Cisco 100-105 Dumps With Update Exam Questions (71-80)
- [2021-New] Cisco 200-355 Dumps With Update Exam Questions (1-10)
- [2021-New] Cisco 100-105 Dumps With Update Exam Questions (121-130)
- Printable Cisco 820-605 Study Guide Online
- [2021-New] Cisco 400-051 Dumps With Update Exam Questions (21-30)
- [2021-New] Cisco 640-916 Dumps With Update Exam Questions (61-70)
- [2021-New] Cisco 200-125 Dumps With Update Exam Questions (4-13)
- [2021-New] Cisco 200-355 Dumps With Update Exam Questions (2-11)
- [2021-New] Cisco 300-320 Dumps With Update Exam Questions (161-169)
- [2021-New] Cisco 400-101 Dumps With Update Exam Questions (14-23)

