350-701 Exam Questions - Online Test
350-701 Premium VCE File

150 Lectures, 20 Hours

we provide Accurate Cisco 350-701 brain dumps which are the best for clearing 350-701 test, and to get certified by Cisco Implementing and Operating Cisco Security Core Technologies. The 350-701 Questions & Answers covers all the knowledge points of the real 350-701 exam. Crack your Cisco 350-701 Exam with latest dumps, guaranteed!
Check 350-701 free dumps before getting the full version:
NEW QUESTION 1
Which Cisco product provides proactive endpoint protection and allows administrators to centrally manage the deployment?
- A. NGFW
- B. AMP
- C. WSA
- D. ESA
Answer: B
NEW QUESTION 2
Refer to the exhibit.
What does the number 15 represent in this configuration?
- A. privilege level for an authorized user to this router
- B. access list that identifies the SNMP devices that can access the router
- C. interval in seconds between SNMPv3 authentication attempts
- D. number of possible failed attempts until the SNMPv3 user is locked out
Answer: B
NEW QUESTION 3
Which flaw does an attacker leverage when exploiting SQL injection vulnerabilities?
- A. user input validation in a web page or web application
- B. Linux and Windows operating systems
- C. database
- D. web page images
Answer: C
Explanation:
Reference: https://tools.cisco.com/security/center/resources/sql_injection
NEW QUESTION 4
DRAG DROP
Drag and drop the capabilities from the left onto the correct technologies on the right.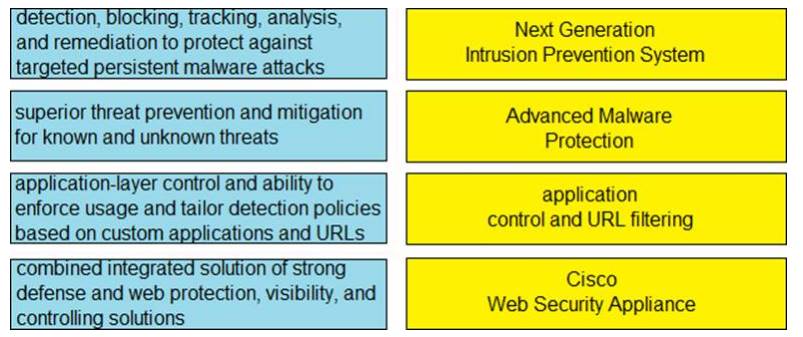
Solution:
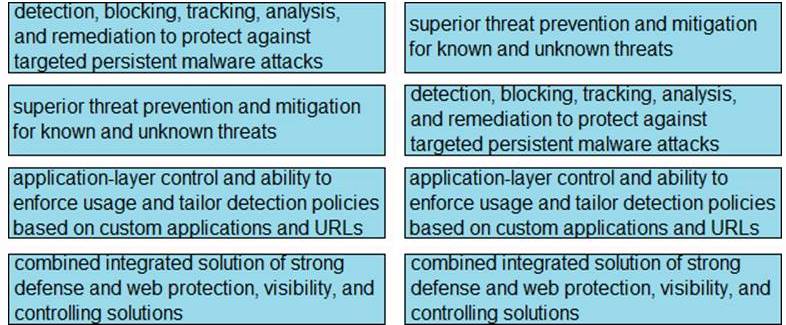
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 5
Which benefit does endpoint security provide the overall security posture of an organization?
- A. It streamlines the incident response process to automatically perform digital forensics on the endpoint.
- B. It allows the organization to mitigate web-based attacks as long as the user is active in the domain.
- C. It allows the organization to detect and respond to threats at the edge of the network.
- D. It allows the organization to detect and mitigate threats that the perimeter security devices do not detect.
Answer: D
NEW QUESTION 6
What is a required prerequisite to enable malware file scanning for the Secure Internet Gateway?
- A. Enable IP Layer enforcement.
- B. Activate the Advanced Malware Protection license
- C. Activate SSL decryption.
- D. Enable Intelligent Proxy.
Answer: D
NEW QUESTION 7
What is the difference between deceptive phishing and spear phishing?
- A. Deceptive phishing is an attacked aimed at a specific user in the organization who holds a C-level role.
- B. A spear phishing campaign is aimed at a specific person versus a group of people.
- C. Spear phishing is when the attack is aimed at the C-level executives of an organization.
- D. Deceptive phishing hijacks and manipulates the DNS server of the victim and redirects the user to a false webpage.
Answer: B
NEW QUESTION 8
Which feature is supported when deploying Cisco ASAv within AWS public cloud?
- A. multiple context mode
- B. user deployment of Layer 3 networks
- C. IPv6
- D. clustering
Answer: B
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/asa96/asav/quick-start-book/asav-96-qsg/asav-aws.html
NEW QUESTION 9
Which deployment model is the most secure when considering risks to cloud adoption?
- A. public cloud
- B. hybrid cloud
- C. community cloud
- D. private cloud
Answer: D
NEW QUESTION 10
What two mechanisms are used to redirect users to a web portal to authenticate to ISE for guest services? (Choose two.)
- A. TACACS+
- B. central web auth
- C. single sign-on
- D. multiple factor auth
- E. local web auth
Answer: BE
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/ise/2-2/admin_guide/b_ise_admin_guide_22/b_ise_admin_guide_22_chapter_01110.html
NEW QUESTION 11
Which SNMPv3 configuration must be used to support the strongest security possible?
- A. asa-host(config)#snmp-server group myv3 v3 priv asa-host(config)#snmp-server user andy myv3 auth sha cisco priv des ciscXXXXXXXX asa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy
- B. asa-host(config)#snmp-server group myv3 v3 noauth asa- host(config)#snmp-server user andy myv3 auth sha cisco priv aes 256 ciscXXXXXXXX asa- host(config)#snmp-server host inside 10.255.254.1 version 3 andy
- C. asa-host(config)#snmp- server group myv3 v3 noauth asa-host(config)#snmp-server user andy myv3 auth sha cisco priv 3des ciscXXXXXXXXasa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy
- D. asa- host(config)#snmp-server group myv3 v3 priv asa-host(config)#snmp-server user andy myv3 auth sha cisco priv aes 256 ciscXXXXXXXX asa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy
Answer: D
NEW QUESTION 12
When web policies are configured in Cisco Umbrella, what provides the ability to ensure that domains are blocked when they host malware, command and control, phishing, and more threats?
- A. Application Control
- B. Security Category Blocking
- C. Content Category Blocking
- D. File Analysis
Answer: B
Explanation:
Reference: https://support.umbrella.com/hc/en-us/articles/115004563666-Understanding-Security-Categories
NEW QUESTION 13
An engineer is configuring a Cisco ESA and wants to control whether to accept or reject email messages to a recipient address. Which list contains the allowed recipient addresses?
- A. SAT
- B. BAT
- C. HAT
- D. RAT
Answer: D
NEW QUESTION 14
On which part of the IT environment does DevSecOps focus?
- A. application development
- B. wireless network
- C. data center
- D. perimeter network
Answer: A
NEW QUESTION 15
An engineer configured a new network identity in Cisco Umbrella but must verify that traffic is being routed through the Cisco Umbrella network. Which action tests the routing?
- A. Ensure that the client computers are pointing to the on-premises DNS servers.
- B. Enable the Intelligent Proxy to validate that traffic is being routed correctly.
- C. Add the public IP address that the client computers are behind to a Core Identity.
- D. Browse to http://welcome.umbrella.com/ to validate that the new identity is working.
Answer: B
NEW QUESTION 16
Which two behavioral patterns characterize a ping of death attack? (Choose two.)
- A. The attack is fragmented into groups of 16 octets before transmission.
- B. The attack is fragmented into groups of 8 octets before transmission.
- C. Short synchronized bursts of traffic are used to disrupt TCP connections.
- D. Malformed packets are used to crash systems.
- E. Publicly accessible DNS servers are typically used to execute the attack.
Answer: BD
Explanation:
Reference: https://en.wikipedia.org/wiki/Ping_of_death
NEW QUESTION 17
What is the primary role of the Cisco Email Security Appliance?
- A. Mail Submission Agent
- B. Mail Transfer Agent
- C. Mail Delivery Agent
- D. Mail User Agent
Answer: B
NEW QUESTION 18
What is a characteristic of Cisco ASA Netflow v9 Secure Event Logging?
- A. It tracks flow-create, flow-teardown, and flow-denied events.
- B. It provides stateless IP flow tracking that exports all records of a specific flow.
- C. It tracks the flow continuously and provides updates every 10 seconds.
- D. Its events match all traffic classes in parallel.
Answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/asa92/configuration/general/asa-general-cli/monitor-nsel.html
NEW QUESTION 19
When wired 802.1X authentication is implemented, which two components are required? (Choose two.)
- A. authentication server: Cisco Identity Service Engine
- B. supplicant: Cisco AnyConnect ISE Posture module
- C. authenticator: Cisco Catalyst switch
- D. authenticator: Cisco Identity Services Engine
- E. authentication server: Cisco Prime Infrastructure
Answer: AC
Explanation:
Reference: https://www.lookingpoint.com/blog/ise-series-802.1x
NEW QUESTION 20
Which feature within Cisco Umbrella allows for the ability to inspect secure HTTP traffic?
- A. File Analysis
- B. SafeSearch
- C. SSL Decryption
- D. Destination Lists
Answer: C
NEW QUESTION 21
......
P.S. 2passeasy now are offering 100% pass ensure 350-701 dumps! All 350-701 exam questions have been updated with correct answers: https://www.2passeasy.com/dumps/350-701/ (337 New Questions)
- Latest Designing Cisco Data Center Infrastructure (DCID) 300-610 Dumps Questions
- [2021-New] Cisco 300-115 Dumps With Update Exam Questions (5-15)
- [2021-New] Cisco 300-320 Dumps With Update Exam Questions (101-110)
- [2021-New] Cisco 300-206 Dumps With Update Exam Questions (101-110)
- [2021-New] Cisco 400-051 Dumps With Update Exam Questions (8-17)
- [2021-New] Cisco 200-355 Dumps With Update Exam Questions (151-160)
- The Secret Of Cisco 400-007 Exam Topics
- [2021-New] Cisco 400-101 Dumps With Update Exam Questions (10-19)
- Tested 640-692 Questions Pool 2021
- [2021-New] Cisco 200-355 Dumps With Update Exam Questions (91-100)

