350-901 Exam Questions - Online Test
350-901 Premium VCE File

150 Lectures, 20 Hours

Want to know Examcollection 350-901 Exam practice test features? Want to lear more about Cisco Developing Applications using Cisco Core Platforms & APIs certification experience? Study 100% Guarantee Cisco 350-901 answers to Renew 350-901 questions at Examcollection. Gat a success with an absolute guarantee to pass Cisco 350-901 (Developing Applications using Cisco Core Platforms & APIs) test on your first attempt.
Free demo questions for Cisco 350-901 Exam Dumps Below:
NEW QUESTION 1
An organization manages a large cloud-deployed application that employs a microservices architecture across multiple data centers. Reports have received about application slowness. The container orchestration logs show that faults have been raised in a variety of containers that caused them to fail and then spin up brand new instances.
Which two actions can improve the design of the application to identify the faults? (Choose two.)
- A. Automatically pull out the container that fails the most over a time period.
- B. Implement a tagging methodology that follows the application execution from service to service.
- C. Add logging on exception and provide immediate notification.
- D. Do a write to the datastore every time there is an application failure.
- E. Implement an SNMP logging system with alerts in case a network link is slow.
Answer: BC
NEW QUESTION 2
While developing an application following the 12-factor app methodology, which approach should be used in the application for logging?
- A. Write a log to a file in the application directory.
- B. Write a log to a file in /var/log.
- C. Write the logs buffered to stdout.
- D. Write the logs unbuffered to stdout.
Answer: D
NEW QUESTION 3
Which snippet presents the correct API call to configure, secure, and enable an SSID using the Meraki API?
- A.
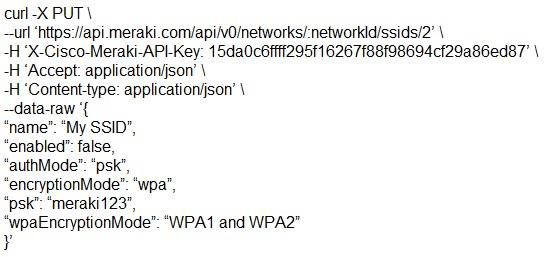
- B.

- C.
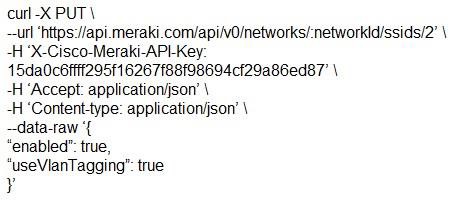
- D.
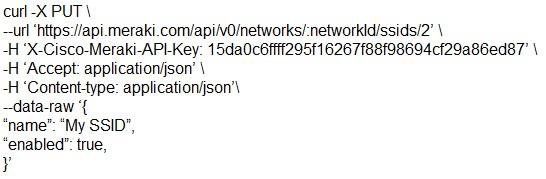
Answer: B
NEW QUESTION 4
Which two statements describe advantages of static code analysis over unit tests? (Choose two.)
- A. It checks for potential tainted data where input is not checked.
- B. It enforces proper coding standards and style.
- C. It performs a quick analysis of whether tests will pass or fail when run.
- D. It checks for race conditions in threaded applications.
- E. It estimates the performance of the code when run.
Answer: BC
NEW QUESTION 5
Refer to the exhibit. Which two functions are performed by the load balancer when it handles traffic originating from the Internet destined to an application hosted on the file server farm? (Choose two.)
- A. Terminate the TLS over the UDP connection from the router and originate an HTTPS connection to the selected server.
- B. Terminate the TLS over the UDP connection from the router and originate an HTTP connection to the selected server.
- C. Terminate the TLS over the TCP connection from the router and originate an HTTP connection to the selected server.
- D. Terminate the TLS over the TCP connection from the router and originate an HTTPS connection to the selected server.
- E. Terminate the TLS over the SCTP connection from the router and originate an HTTPS connection to the selected server.
Answer: DE
NEW QUESTION 6
The response from a server includes the header ETag: W/”7eb8b94419e371767916ef13e0d6e63d”. Which statement is true?
- A. The ETag has a Strong validator directive.
- B. The ETag has a Weak validator directive, which is an optional directive.
- C. The ETag has a Weak validator directive, which is a mandatory directive.
- D. The ETag has a Strong validator directive, which it is incorrectly formatted.
Answer: B
NEW QUESTION 7
How should a web application be designed to work on a platform where up to 1000 requests per second can be served?
- A. Use algorithms like random early detection to deny excessive requests.
- B. Set a per-user limit (for example, 5 requests/minute/user) and deny the requests from the users who have reached the limit.
- C. Only 1000 user connections are allowed; further connections are denied so that all connected users can be served.
- D. All requests are saved and processed one by one so that all users can be served eventually.
Answer: D
NEW QUESTION 8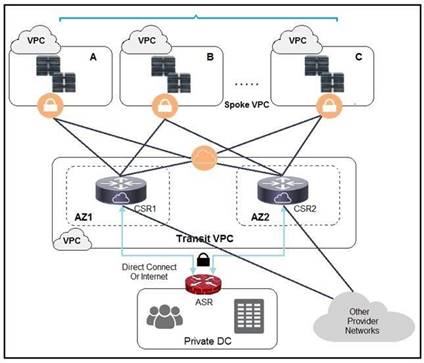
Refer to the exhibit. A company has extended networking from the data center to the cloud through Transit VPC. Which two statements describe the benefits of this approach? (Choose two.)
- A. Dynamic routing combined with multi-AZ- deployment creates a robust network infrastructure.
- B. VPC virtual gateways provide highly available connections to virtual networks.
- C. Dedicated VPC simplifies load balancing by combining internal and external web services.
- D. VPC virtual gateways provide more secure connections to virtual networks.
- E. Dedicated VPC simplifies routing by not combining this service with other shared services.
Answer: BD
NEW QUESTION 9
An automated solution is needed to configure VMs in numerous cloud provider environments to connect the environments to an SDWAN. The SDWAN edge VM is provided as an image in each of the relevant clouds and can be given an identity and all required configuration via cloud-init without needing to log into the VM once online.
Which configuration management and/or automation tooling is needed for this solution?
- A. Ansible
- B. Ansible and Terraform
- C. NSO
- D. Terraform
- E. Ansible and NSO
Answer: E
NEW QUESTION 10
A developer needs to configure an environment to orchestrate and configure. Which two tools should be used for each task? (Choose two.)
- A. Puppet for orchestration
- B. Terraform for orchestration
- C. Terraform for configuration
- D. Ansible for orchestration
- E. Ansible for configuration
Answer: BE
NEW QUESTION 11
The UCS Python SDK includes modules for Service Profile template creation. Which two UCS Service Profile template types are supported? (Choose two.)
- A. initial-template
- B. updating-template
- C. abstract-template
- D. attached-template
- E. base-template
Answer: AB
NEW QUESTION 12
Into which two areas are AppDynamics APIs categorized? (Choose two.)
- A. application-centric
- B. analytics-events
- C. database-visibility
- D. platform-side
- E. agent-side
Answer: DE
NEW QUESTION 13
Which HTTP status code indicates that a client application is experiencing intentional rate limiting by the server?
- A. 202
- B. 401
- C. 429
- D. 503
Answer: C
NEW QUESTION 14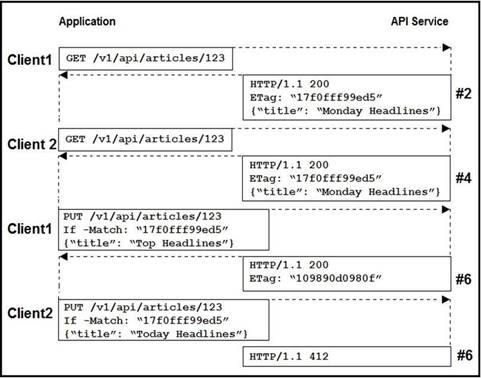
Refer to the exhibit. Two editors are concurrently updating an article’s headline from their mobile devices. What results from this scenario based on this REST API sequence?
- A. The article is marked as “Conflicted”
- B. The article headline is “Monday Headlines”
- C. The article headline is “Today Headlines”
- D. The article headline is “Top Headlines”
Answer: B
NEW QUESTION 15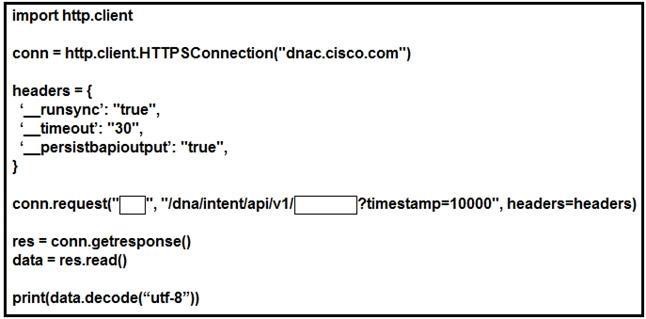
Refer to the exhibit. Which configuration of method and parameter retrieves the health of a laptop connected to the network from Cisco DNA Center?
- A. PUT; network-health;
- B. GET; client-health;
- C. GET; network-device;
- D. POST; network-device;
Answer: C
NEW QUESTION 16
On a Cisco Catalyst 9300 Series Switch, the guest shell is being used to create a service within a container. Which change is needed to allow the service to have external access?
- A. Apply ip nat overload on VirtualPortGroup0.
- B. Apply ip nat inside on Interface VirtualPortGroup0.
- C. Apply ip nat outside on Interface VirtualPortGroup0.
- D. Apply ip nat inside on Interface GigabitEthernet1.
Answer: B
NEW QUESTION 17
Which statement about microservices architecture is true?
- A. Applications are written in a single unit.
- B. It is a complex application composed of multiple independent parts.
- C. It is often a challenge to scale individual parts.
- D. A single faulty service can bring the whole application down.
Answer: B
NEW QUESTION 18
Refer to the exhibit. An Intersight API is being used to query RackUnit resources that have a tag keyword set to “Site”. What is the expected output of this command?
- A. list of all resources that have a tag with the keyword “Site”
- B. error message because the Value field was not specified
- C. error message because the tag filter should be lowercase
- D. list of all sites that contain RackUnit tagged compute resources
Answer: A
NEW QUESTION 19
A developer has created an application based on customer requirements. The customer needs to run the application with the minimum downtime. Which design approach regarding high-availability applications, Recovery Time Objective, and Recovery Point Objective must be taken?
- A. Active/passive results in lower RTO and RP
- B. For RPO, data synchronization between the two data centers must be timely to allow seamless request flow.
- C. Active/passive results in lower RTO and RP
- D. For RPO, data synchronization between the two data centers does not need to be timely to allow seamless request flow.
- E. Active/active results in lower RTO and RP
- F. For RPO, data synchronization between the two data centers does not need to be timely to allow seamless request flow.
- G. Active/active results in lower RTO and RP
- H. For RPO, data synchronization between the two data centers must be timely to allow seamless request flow.
Answer: A
NEW QUESTION 20
Refer to the exhibit. Which key value pair from the ios_ntp Ansible module creates an NTP server peer?
- A. state: present
- B. state: True
- C. config: present
- D. config: True
Answer: A
NEW QUESTION 21
Refer to the exhibit. The cURL POST request creates an OAuth access token for authentication with FDM API requests. What is the purpose of the file “@token_data” that cURL is handling?
- A. This file is a container to log possible error responses in the request.
- B. This file is given as input to store the access token received from FDM.
- C. This file is used to send authentication related headers.
- D. This file contains raw data that is needed for token authentication.
Answer: B
NEW QUESTION 22
......
Recommend!! Get the Full 350-901 dumps in VCE and PDF From Dumps-files.com, Welcome to Download: https://www.dumps-files.com/files/350-901/ (New 0 Q&As Version)
- [2021-New] Cisco 200-355 Dumps With Update Exam Questions (131-140)
- [2021-New] Cisco 200-355 Dumps With Update Exam Questions (141-150)
- [2021-New] Cisco 352-001 Dumps With Update Exam Questions (41-50)
- [2021-New] Cisco 300-320 Dumps With Update Exam Questions (1-10)
- [2021-New] Cisco 200-105 Dumps With Update Exam Questions (1-10)
- [2021-New] Cisco 300-075 Dumps With Update Exam Questions (51-60)
- [2021-New] Cisco 100-105 Dumps With Update Exam Questions (41-50)
- [2021-New] Cisco 642-035 Dumps With Update Exam Questions (11-20)
- [2021-New] Cisco 300-101 Dumps With Update Exam Questions (61-66)
- [2021-New] Cisco 300-115 Dumps With Update Exam Questions (81-88)

