CAS-004 Exam Questions - Online Test
CAS-004 Premium VCE File

150 Lectures, 20 Hours

Our pass rate is high to 98.9% and the similarity percentage between our CAS-004 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the CompTIA CAS-004 exam in just one try? I am currently studying for the CompTIA CAS-004 exam. Latest CompTIA CAS-004 Test exam practice questions and answers, Try CompTIA CAS-004 Brain Dumps First.
Online CompTIA CAS-004 free dumps demo Below:
NEW QUESTION 1
Clients are reporting slowness when attempting to access a series of load-balanced APIs that do not require authentication. The servers that host the APIs are showing heavy CPU utilization. No alerts are found on the WAFs sitting in front of the APIs. Which of the following should a security engineer recommend to BEST remedy the performance issues in a timely manner?
- A. Implement rate limiting on the API.
- B. Implement geoblocking on the WAF.
- C. Implement OAuth 2.0 on the API.
- D. Implement input validation on the API.
Answer: C
NEW QUESTION 2
A security engineer has been asked to close all non-secure connections from the corporate network. The engineer is attempting to understand why the corporate
UTM will not allow users to download email via IMAPS. The engineer formulates a theory and begins testing by creating the firewall ID 58, and users are able to download emails correctly by using IMAP instead. The network comprises three VLANs:
The security engineer looks at the UTM firewall rules and finds the following:
Which of the following should the security engineer do to ensure IMAPS functions properly on the corporate user network?
- A. Contact the email service provider and ask if the company IP is blocked.
- B. Confirm the email server certificate is installed on the corporate computers.
- C. Make sure the UTM certificate is imported on the corporate computers.
- D. Create an IMAPS firewall rule to ensure email is allowed.
Answer: C
NEW QUESTION 3
DRAG DROP
An organization is planning for disaster recovery and continuity of operations. INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding. Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button. Select and Place: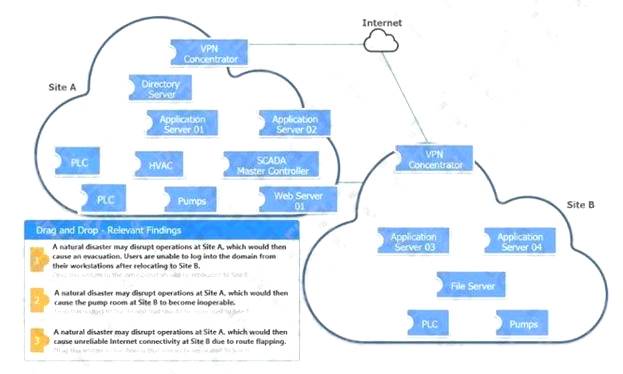
A.
- A.
Answer: A
NEW QUESTION 4
A junior developer is informed about the impact of new malware on an Advanced RISC Machine (ARM) CPU, and the code must be fixed accordingly. Based on the debug, the malware is able to insert itself in another process memory location.
Which of the following technologies can the developer enable on the ARM architecture to prevent this type of malware?
- A. Execute never
- B. No-execute
- C. Total memory encryption
- D. Virtual memory encryption
Answer: A
Explanation:
Reference: https://developer.arm.com/documentation/102433/0100/Stack-smashing-and-execution-permissions
NEW QUESTION 5
Ransomware encrypted the entire human resources fileshare for a large financial institution. Security operations personnel were unaware of the activity until it was too late to stop it. The restoration will take approximately four hours, and the last backup occurred 48 hours ago. The management team has indicated that the RPO for a disaster recovery event for this data classification is 24 hours.
Based on RPO requirements, which of the following recommendations should the management team make?
- A. Leave the current backup schedule intact and pay the ransom to decrypt the data.
- B. Leave the current backup schedule intact and make the human resources fileshare read-only.
- C. Increase the frequency of backups and create SIEM alerts for IOCs.
- D. Decrease the frequency of backups and pay the ransom to decrypt the data.
Answer: C
NEW QUESTION 6
A security analyst is performing a vulnerability assessment on behalf of a client. The analyst must define what constitutes a risk to the organization. Which of the following should be the analyst’s FIRST action?
- A. Create a full inventory of information and data assets.
- B. Ascertain the impact of an attack on the availability of crucial resources.
- C. Determine which security compliance standards should be followed.
- D. Perform a full system penetration test to determine the vulnerabilities.
Answer: C
NEW QUESTION 7
A satellite communications ISP frequently experiences outages and degraded modes of operation over one of its legacy satellite links due to the use of deprecated hardware and software. Three days per week, on average, a contracted company must follow a checklist of 16 different high-latency commands that must be run in serial to restore nominal performance. The ISP wants this process to be automated.
Which of the following techniques would be BEST suited for this requirement?
- A. Deploy SOAR utilities and runbooks.
- B. Replace the associated hardware.
- C. Provide the contractors with direct access to satellite telemetry data.
- D. Reduce link latency on the affected ground and satellite segments.
Answer: A
NEW QUESTION 8
In preparation for the holiday season, a company redesigned the system that manages retail sales and moved it to a cloud service provider. The new infrastructure did not meet the company’s availability requirements. During a postmortem analysis, the following issues were highlighted:
* 1. International users reported latency when images on the web page were initially loading.
* 2. During times of report processing, users reported issues with inventory when attempting to place orders.
* 3. Despite the fact that ten new API servers were added, the load across servers was heavy at peak times.
Which of the following infrastructure design changes would be BEST for the organization to implement to avoid these issues in the future?
- A. Serve static content via distributed CDNs, create a read replica of the central database and pull reports from there, and auto-scale API servers based on performance.
- B. Increase the bandwidth for the server that delivers images, use a CDN, change the database to a non-relational database, and split the ten API servers across two load balancers.
- C. Serve images from an object storage bucket with infrequent read times, replicate the database across different regions, and dynamically create API servers based on load.
- D. Serve static-content object storage across different regions, increase the instance size on the managed relational database, and distribute the ten API servers across multiple regions.
Answer: A
NEW QUESTION 9
An organization is preparing to migrate its production environment systems from an on-premises environment to a cloud service. The lead security architect is concerned that the organization's current methods for addressing risk may not be possible in the cloud environment.
Which of the following BEST describes the reason why traditional methods of addressing risk may not be possible in the cloud?
- A. Migrating operations assumes the acceptance of all risk.
- B. Cloud providers are unable to avoid risk.
- C. Specific risks cannot be transferred to the cloud provider.
- D. Risks to data in the cloud cannot be mitigated.
Answer: C
Explanation:
Reference: https://arxiv.org/ftp/arxiv/papers/1303/1303.4814.pdf
NEW QUESTION 10
A security analyst is investigating a possible buffer overflow attack. The following output was found on a user’s workstation: graphic.linux_randomization.prg Which of the following technologies would mitigate the manipulation of memory segments?
- A. NX bit
- B. ASLR
- C. DEP
- D. HSM
Answer: B
Explanation:
Reference: http://webpages.eng.wayne.edu/~fy8421/19sp-csc5290/labs/lab2-instruction.pdf (3)
NEW QUESTION 11
An organization is referencing NIST best practices for BCP creation while reviewing current internal organizational processes for mission-essential items. Which of the following phases establishes the identification and prioritization of critical systems and functions?
- A. Review a recent gap analysis.
- B. Perform a cost-benefit analysis.
- C. Conduct a business impact analysis.
- D. Develop an exposure factor matrix.
Answer: C
Explanation:
Reference: https://itsm.ucsf.edu/business-impact-analysis-bia-0
NEW QUESTION 12
The Chief information Officer (CIO) wants to establish a non-banding agreement with a third party that outlines the objectives of the mutual arrangement dealing with data transfers between both organizations before establishing a format partnership .
Which of the follow would MOST likely be used?
- A. MOU
- B. OLA
- C. NDA
- D. SLA
Answer: A
NEW QUESTION 13
A company is preparing to deploy a global service.
Which of the following must the company do to ensure GDPR compliance? (Choose two.)
- A. Inform users regarding what data is stored.
- B. Provide opt-in/out for marketing messages.
- C. Provide data deletion capabilities.
- D. Provide optional data encryption.
- E. Grant data access to third parties.
- F. Provide alternative authentication techniques.
Answer: AB
Explanation:
Reference: https://gdpr.eu/compliance-checklist-us-companies/
NEW QUESTION 14
A company wants to protect its intellectual property from theft. The company has already applied ACLs and DACs. Which of the following should the company use to prevent data theft?
- A. Watermarking
- B. DRM
- C. NDA
- D. Access logging
Answer: D
NEW QUESTION 15
An application developer is including third-party background security fixes in an application. The fixes seem to resolve a currently identified security issue. However, when the application is released to the public, report come In that a previously vulnerability has returned .
Which of the following should the developer integrate into the process to BEST prevent this type of behavior?
- A. Peer review
- B. Regression testing
- C. User acceptance
- D. Dynamic analysis
Answer: A
NEW QUESTION 16
......
P.S. Easily pass CAS-004 Exam with 128 Q&As Surepassexam Dumps & pdf Version, Welcome to Download the Newest Surepassexam CAS-004 Dumps: https://www.surepassexam.com/CAS-004-exam-dumps.html (128 New Questions)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (531-540)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (131-140)
- [2021-New] CompTIA N10-006 Dumps With Update Exam Questions (21-30)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (151-160)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (11-20)
- [2021-New] CompTIA LX0-104 Dumps With Update Exam Questions (51-60)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (10-19)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (151-160)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (81-90)
- Up To The Immediate Present 220-1001 Software 2021

