H12-711_V3.0 Exam Questions - Online Test
H12-711_V3.0 Premium VCE File

150 Lectures, 20 Hours

Our pass rate is high to 98.9% and the similarity percentage between our H12-711_V3.0 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the HUAWEI H12-711_V3.0 exam in just one try? I am currently studying for the HUAWEI H12-711_V3.0 exam. Latest HUAWEI H12-711_V3.0 Test exam practice questions and answers, Try HUAWEI H12-711_V3.0 Brain Dumps First.
Free demo questions for HUAWEI H12-711_V3.0 Exam Dumps Below:
NEW QUESTION 1
Regarding the description of vulnerability scanning, which of the following is false?
- A. Vulnerability scanning is a network-based technology for remotely monitoring the security performance vulnerabilities of target networks or hosts, and can be used to conduct simulated attack experiments and security audits.
- B. Vulnerability scanning is used to detect whether there are vulnerabilities in the target host system, generally scanning the target host for specific vulnerabilities
- C. Vulnerability scanning is a passive preventive measure that can effectively avoid hacker attacks
- D. can be based onpingScan and port scan results for vulnerability scanning
Answer: C
NEW QUESTION 2
Using the ______ method of the Web proxy, the virtual gateway will encrypt the real URL that the user wants to access, and can adapt to different terminal types.[fill in the blank]*
Solution:
web rewrite
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 3
existIPSec VPNIn the transmission mode, which part of the encrypted data packet is?
- A. Network layer and upper layer data packets
- B. OriginalIPheader
- C. newIPheader
- D. Transport layer and upper layer data packets
Answer: D
NEW QUESTION 4
______ is a flaw in the specific implementation of hardware, software, protocols, or system security policies that could enable an attacker to gain unauthorized access or compromise a system.[fill in the blank]*
Solution:
Vulnerability
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 5
The CA certificate is the certificate of the CA itself. If there is no multi-level CA in the PKI system, the original certificate of the CA is a self-signed certificate; if there are multiple levels of CA, it will form a CA hierarchy. The top CA is the root CA, which has A CA' self-signed certificate.
- A. True
- B. False
Answer: A
NEW QUESTION 6
whenUSGWhich of the following logs can be viewed when the series firewall hard disk is in place? (multiple choice)
- A. Operation log
- B. business log
- C. Alarm information
- D. Threat log
Answer: ABCD
NEW QUESTION 7
Which of the following options is not included in the processing method adopted by the firewall for the matched authentication data flow?
- A. Portali certification
- B. Certification-free
- C. WeChat authentication
- D. not certified
Answer: D
NEW QUESTION 8
existUSGConfigure on the system firewallNAT Server, will produceserver-mapTable, which of the following is not part of this representation?
- A. PurposeIP
- B. destination port number
- C. agreement number
- D. sourceIP
Answer: D
NEW QUESTION 9
"Implement security monitoring and management of information and information systems to prevent illegal use of information and information systems", in order to achieve which feature in information security?
- A. confidentiality
- B. controllability
- C. non-repudiation
- D. integrity
Answer: B
NEW QUESTION 10
Which of the following options belongs to Tier 2VPNTechnology?
- A. SSL VPN
- B. L2TP VPN
- C. GRE VPN
- D. IPSec VPN
Answer: B
NEW QUESTION 11
Applying for special funds for emergency response and purchasing emergency response software and hardware equipment belong to the work content of which stage of the network's complete emergency response?
- A. preparation stage
- B. Inhibition stage
- C. response phase
- D. recovery phase
Answer: A
NEW QUESTION 12
aboutNATAddress translation, which of the following statements is europium false??
- A. sourceNATconfiguration in technologyNATaddress pool, you can configure only one address poolIPaddress
- B. Address translation can be provided in the local area network according to the needs of usersFTP,WWW,Telnetand other services
- C. Some application layer protocols carry in the dataIPaddress information, make themNATWhen modifying the data in the upper layerIPAddress information
- D. for some non-TCP,UDPprotocol (such asICMP,PPTP), cannot doNATconvert
Answer: D
NEW QUESTION 13
Execute the command on the firewall and display the above information. Which of the following descriptions is correct? (multiple choice)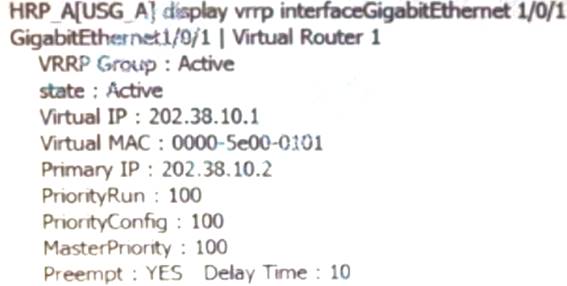
- A. this firewallVGMPgroup status isActive
- B. this firewallG1/0/1virtual interfaceIPaddress is202.38.10.2
- C. this firewallVRIDfor1ofVRRPThe priority of the backup group is100
- D. When the main deviceUSG_AWill not switch in the event of a failure
Answer: ABC
NEW QUESTION 14
Which of the following options are available inwindowsDo you do it in the advanced settings of the firewall? (multiple choice)
- A. Restore defaults
- B. Change notification rules
- C. Set up connection security rules
- D. Set up inbound and outbound rules
Answer: ABCD
NEW QUESTION 15
How many IPSec SAs need to be established to encapsulate P packets using the AH+ESP protocol?
- A. 2
- B. 1
- C. 4
- D. 3
Answer: A
NEW QUESTION 16
Which of the following does not belong toLINUXoperating system?
- A. CentOS
- B. RedHat
- C. Ubuntu
- D. MAC OS
Answer: D
NEW QUESTION 17
aboutNATConfiguration statement, which of the following is false?
- A. Configure sources in transparent modeNAT, the firewall does not supporteasy-ipWay
- B. in the address poolIPaddress can beNATserverpublic networkIPaddress overlap
- C. in the networkVoIPWhen doing business, no configuration is requiredNATALG
- D. Firewall does not supportESPandAHmessageNAPTconvert
Answer: D
NEW QUESTION 18
Because the server is a kind of computer, we can use our personal computer as a server in the enterprise.
- A. True
- B. False
Answer: B
NEW QUESTION 19
......
100% Valid and Newest Version H12-711_V3.0 Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/H12-711_V3.0-dumps.html (New 492 Q&As)
- Renew H12-711_V3.0 Practice For HCIA-Security V3.0 Certification
- The Most Up-to-date Guide To H12-711_V3.0 Exam Question
- The Leading Guide To H12-711_V3.0 Test Question
- Precise H19-308 Dumps 2021
- What Tested H12-711_V3.0 Dump Is
- 100% Correct H12-211 Dumps 2021
- HUAWEI H12-311 Ebook 2021
- HUAWEI H12-221 Braindumps 2021
- Top Tips Of Up To The Minute H12-711_V3.0 Practice Test
- A Review Of Approved H12-711 Prep

