H12-711_V3.0 Exam Questions - Online Test
H12-711_V3.0 Premium VCE File

150 Lectures, 20 Hours

Act now and download your HUAWEI H12-711_V3.0 test today! Do not waste time for the worthless HUAWEI H12-711_V3.0 tutorials. Download Improved HUAWEI HCIA-Security V3.0 exam with real questions and answers and begin to learn HUAWEI H12-711_V3.0 with a classic professional.
Free H12-711_V3.0 Demo Online For HUAWEI Certifitcation:
NEW QUESTION 1
Which of the following options is correct regarding the actions of the security policy and the description of the security profile? (multiple choice)
- A. Prohibited if the action of the security policy is"prohibit", the device will discard this traffic, and will not perform content security checks in the future.
- B. The security profile can take effect even if the action is allowed under the security policy
- C. The security profile must be applied under the security policy whose action is Allowed to take effect.
- D. If the security policy action is"allow", the traffic will not match the security profile
Answer: AC
NEW QUESTION 2
Huawei's Agile-Controller products belong to _______ in the HiSec solution.[fill in the blank]
Solution:
control
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 3
Which of the following options is not a passive means of obtaining information? ( )[Multiple choice]*
- A. port scan
- B. port mirroring
- C. capture packets
- D. collect log education
Answer: C
NEW QUESTION 4
The world's first worm-"Morris Worm"Make people realize that with the deepening of people's dependence on computers, the possibility of computer network being attacked is also increasing, and it is necessary to establish a sound emergency response system
- A. True
- B. False
Answer: A
NEW QUESTION 5
in configurationGRE Tunnelinterface,DestinationThe address generally refers to which of the following parameters?
- A. localTunnelinterfaceIPaddress
- B. Local external network egressIPaddress
- C. External network egressIPaddress
- D. PeerTunnelinterfaceIPaddress
Answer: C
NEW QUESTION 6
Which of the following is not a key technology of antivirus software?
- A. Shelling technology
- B. self protection
- C. format the disk
- D. Update virus database in real time
Answer: C
NEW QUESTION 7
In symmetric encryption algorithms, the _______ algorithm is used over a data communication channel, browser or network link.[fill in the blank]*
Solution:
Stream Encryption
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 8
Which of the following options are at risk from traffic-based attacks? (multiple choice)
- A. network down
- B. Server down
- C. data stolen
- D. The web page has been tampered with
Answer: AB
NEW QUESTION 9
Please match the whole worm attack process and attack description.[fill in the blank]*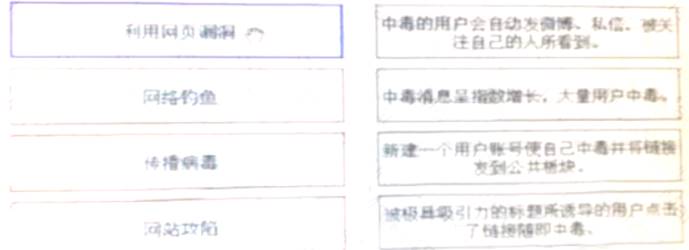
Solution:
Exploiting web page loopholes: Create a new user account to poison yourself and post the link to the public section, Phishing: Users induced by attractive titles click on the link and then get poisoned, and rebroadcast the virus: Poisoned users will automatically post Weibo , private messages, and are seen by people who follow them. Website compromise: Poisoning news is growing exponentially. A large number of users are poisoned)
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 10
aboutSSL VPNdescription, which of the following is correct?
- A. Can be used without a client
- B. yesIPlayer to encrypt
- C. existNATcrossing problem
- D. No authentication required
Answer: A
NEW QUESTION 11
existUSGIn the series firewalls, which of the following commands can be used to queryNATconversion result?
- A. display nat translation
- B. display firewall session table
- C. display current nat
- D. display firewall nat translation
Answer: B
NEW QUESTION 12
aboutNATThe configuration commands for the address pool are as follows:no-patThe meaning of the parameters is: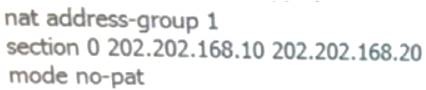
- A. no address translation
- B. port multiplexing
- C. Do not translate source ports
- D. Do not convert destination port
Answer: C
NEW QUESTION 13
Which of the following protocols can guarantee the confidentiality of data transmission? (multiple choice)
- A. Telnet
- B. SSH
- C. FTP
- D. HTTPS
Answer: BD
NEW QUESTION 14
Which of the following descriptions of the firewall log is wrong?
- A. The log level Emergency is the most severe level
- B. Alert log level indicates a major abnormality of the device, requiring immediate action
- C. According to the severity level or urgency of the informatio
- D. The log can be divided into 8 level
- E. Themore serious the information, the greater the log level value.
- F. The ebug log level indicates that it is general information about the normal operation of the device, and the user does not need to pay attention
Answer: D
NEW QUESTION 15
After the firewall detects an intrusion, the administrator can view the intrusion log information in the firewall business log or ( ) log. (fill in the blank
Solution:
System
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 16
Which of the following are the basic functions of antivirus software? (multiple choice)
- A. virus protection
- B. Find viruses
- C. remove virus
- D. replication virus
Answer: ABC
NEW QUESTION 17
Please sort the following digital envelope encryption and decryption process correctly.
- A. uses B's public key to encrypt the symmetric key to generate a digital envelope
- B. After receiving the encrypted information from A, B uses its own private key to open the digital envelope to obtain the symmetric key.
- C. uses a symmetric key to encrypt the plaintext to generate ciphertext information.
- D. B uses the symmetric key to decrypt the ciphertext information to obtain the original plaintext.
- E. A sends the digital envelope and cipher text information to B
Answer: ABCDE
NEW QUESTION 18
When IPSec VPN uses tunnel mode to encapsulate packets, which of the following is not within the encryption scope of the ESP security protocol? ( )[Multiple choice]*
- A. ESP Header
- B. TCP Header
- C. Raw IP Header
- D. ESP Tail
Answer: A
NEW QUESTION 19
......
P.S. Downloadfreepdf.net now are offering 100% pass ensure H12-711_V3.0 dumps! All H12-711_V3.0 exam questions have been updated with correct answers: https://www.downloadfreepdf.net/H12-711_V3.0-pdf-download.html (492 New Questions)
- Practical H12-221 Free Practice Questions 2021
- HUAWEI H19-308 Exam Questions 2021
- A Review Of Approved H12-711 Prep
- All About Printable H12-811_V1.0 Exam Price
- The Secret Of HUAWEI H12-811_V1.0 Latest Exam
- What Simulation H12-811_V1.0 Free Practice Test Is
- The Leading Guide To H12-711_V3.0 Test Question
- Certified H12-211 Exam Questions 2021
- Free H12-221 Exam Questions and Answers 2021
- HUAWEI H12-221 Study Guides 2021

