MS-500 Exam Questions - Online Test
MS-500 Premium VCE File

150 Lectures, 20 Hours

Exam Code: MS-500 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: Microsoft 365 Security Administrator
Certification Provider: Microsoft
Free Today! Guaranteed Training- Pass MS-500 Exam.
Online Microsoft MS-500 free dumps demo Below:
NEW QUESTION 1
You have a Microsoft 365 subscription.
A user reports that changes were made to several files in Microsoft OneDrive.
You need to identify which files were modified by which users in the user’s OneDrive. What should you do?
- A. From the Azure Active Directory admin center, open the audit log
- B. From the OneDrive admin center, select Device access
- C. From Security & Compliance, perform an eDiscovery search
- D. From Microsoft Cloud App Security, open the activity log
Answer: D
Explanation:
Reference:
https://docs.microsoft.com/en-us/cloud-app-security/activity-filters
NEW QUESTION 2
You need to resolve the issue that targets the automated email messages to the IT team. Which tool should you run first?
- A. Synchronization Service Manager
- B. Azure AD Connect wizard
- C. Synchronization Rules Editor
- D. IdFix
Answer: B
Explanation:
References:
https://docs.microsoft.com/en-us/office365/enterprise/fix-problems-with-directory-synchronization
Case Study: 2 Litware, Inc Overview
Litware, Inc. is a financial company that has 1,000 users in its main office in Chicago and 100 users in
a branch office in San Francisco.
Existing Environment
Internal Network Infrastructure
The network contains a single domain forest. The forest functional level is Windows Server 2021. Users are subject to sign-in hour restrictions as defined in Active Directory.
The network has the IP address range shown in the following table.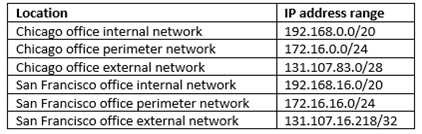
The offices connect by using Multiprotocol Label Switching (MPLS).
The following operating systems are used on the network:
•Windows Server 2021
•Windows 10 Enterprise
•Windows 8.1 Enterprise
The internal network contains the systems shown in the following table.
Litware uses a third-party email system.
Cloud Infrastructure
Litware recently purchased Microsoft 365 subscription licenses for all users.
Microsoft Azure Active Directory (Azure AD) Connect is installed and uses the default authentication settings. User accounts are not yet synced to Azure AD.
You have the Microsoft 365 users and groups shown in the following table.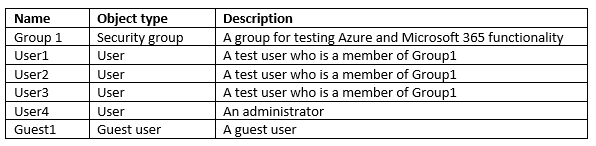
Planned Changes
Litware plans to implement the following changes: Migrate the email system to Microsoft Exchange Online Implement Azure AD Privileged Identity Management Security Requirements
Litware identities the following security requirements:
•Create a group named Group2 that will include all the Azure AD user accounts. Group2 will be used to provide limited access to Windows Analytics
•Create a group named Group3 that will be used to apply Azure Information Protection policies to pilot users. Group3 must only contain user accounts
•Use Azure Advanced Threat Protection (ATP) to detect any security threats that target the forest
•Prevent users locked out of Active Directory from signing in to Azure AD and Active Directory
•Implement a permanent eligible assignment of the Compliance administrator role for User1
•Integrate Windows Defender and Windows Defender ATP on domain-joined servers
•Prevent access to Azure resources for the guest user accounts by default
•Ensure that all domain-joined computers are registered to Azure AD
Multi-factor authentication (MFA) Requirements
Security features of Microsoft Office 365 and Azure will be tested by using pilot Azure user accounts. You identify the following requirements for testing MFA.
Pilot users must use MFA unless they are signing in from the internal network of the Chicago office. MFA must NOT be used on the Chicago office internal network.
If an authentication attempt is suspicious, MFA must be used, regardless of the user location Any disruption of legitimate authentication attempts must be minimized
General Requirements
Litware want to minimize the deployment of additional servers and services in the Active Directory forest.
NEW QUESTION 3
You have a Microsoft 365 Enterprise E5 subscription.
You use Windows Defender Advanced Threat Protection (Windows Defender ATP). You plan to use Microsoft Office 365 Attack simulator.
What is a prerequisite for running Attack simulator?
- A. Enable multi-factor authentication (MFA)
- B. Configure Advanced Threat Protection (ATP)
- C. Create a Conditional Access App Control policy for accessing Office 365
- D. Integrate Office 365 Threat Intelligence and Windows Defender ATP
Answer: A
Explanation:
Reference:
https://docs.microsoft.com/en-us/office365/securitycompliance/attack-simulator
NEW QUESTION 4
You configure several Advanced Threat Protection (ATP) policies in a Microsoft 365 subscription. You need to allow a user named User1 to view ATP reports in the Threat management dashboard. Which role provides User1with the required role permissions?
- A. Security reader
- B. Message center reader
- C. Compliance administrator
- D. Information Protection administrator
Answer: A
Explanation:
Reference:
https://docs.microsoft.com/en-us/office365/securitycompliance/view-reports-for-atp#what-permissions-areneeded-to-view-the-atp-reports
NEW QUESTION 5
You have a Microsoft 365 subscription.
You create and run a content search from the Security & Compliance admin center. You need to download the results of the content search.
What should you obtain first?
- A. an export key
- B. a password
- C. a certificate
- D. a pin
Answer: A
Explanation:
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/export-search-results
NEW QUESTION 6
You have a Microsoft 365 subscription.
You create an Advanced Threat Protection (ATP) safe attachments policy to quarantine malware. You need to configure the retention duration for the attachments in quarantine.
Which type of threat management policy should you create from the Security&Compliance admin center?
- A. ATP anti-phishing
- B. DKIM
- C. Anti-spam
- D. Anti-malware
Answer: D
NEW QUESTION 7
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some questions sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an on-premises Active Directory domain named contoso.com.
You install and run Azure AD Connect on a server named Server1 that runs Windows Server. You need to view Azure AD Connect events.
You use the Security event log on Server1. Does that meet the goal?
- A. Yes
- B. No
Answer: B
Explanation:
References:
https://support.pingidentity.com/s/article/PingOne-How-to-troubleshoot-an-AD-Connect-Instance
NEW QUESTION 8
HOTSPOT
Your company has a Microsoft 365 subscription that contains the users shown in the following table.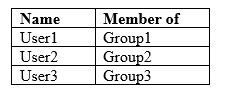
The company implements Windows Defender Advanced Threat Protection (Windows Defender ATP). Windows Defender ATP includes the roles shown in the following table:
Windows Defender ATP contains the machine groups shown in the following table:
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 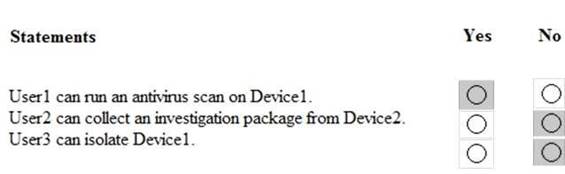
NEW QUESTION 9
You have a Microsoft 365 subscription.
You need to be notified by email whenever an administrator starts an eDiscovery search. What should you do from the Security & Compliance admin center?
- A. From Search & investigation, create a guided search.
- B. From Events, create an event.
- C. From Alerts, create an alert policy.
- D. From Search & Investigation, create an eDiscovery case.
Answer: C
Explanation:
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/alert-policies
NEW QUESTION 10
HOTSPOT
You have a Microsoft 365 subscription.
You are creating a retention policy named Retention1 as shown in the following exhibit.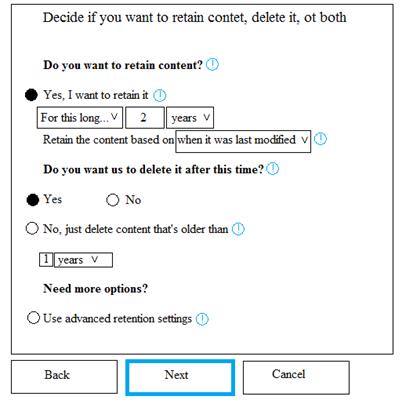
You apply Retention1 to SharePoint sites and OneDrive accounts.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.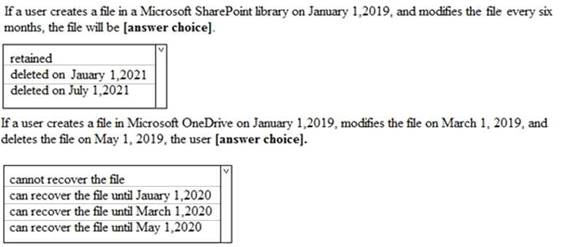
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 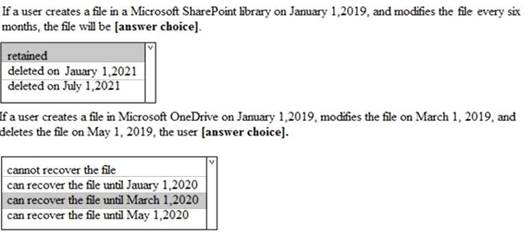
NEW QUESTION 11
You have a hybrid Microsoft 365 environment.
All computers run Windows 10 Enterprise and have Microsoft Office 365 ProPlus installed. All the
computers are joined to Active Directory.
You have a server named Server1 that runs Windows Server 2021. Server1 hosts the telemetry database. You need to prevent private details in the telemetry data from being transmitted to Microsoft.
What should you do?
- A. On Server1, run readinessreportcreator.exe
- B. Configure a registry on Server1
- C. Configure a registry on the computers
- D. On the computers, run tdadm.exe
Answer: C
NEW QUESTION 12
You recently created and published several labels policies in a Microsoft 365 subscription.
You need to view which labels were applied by users manually and which labels were applied automatically.
What should you do from the Security & Compliance admin center?
- A. From Search & investigation, select Content search
- B. From Data governance, select Events
- C. From Search & investigation, select eDiscovery
- D. From Reports, select Dashboard
Answer: B
NEW QUESTION 13
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some questions sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in Security & Compliance to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
You run the Set-AdminAuditLogConfig -AdminAuditLogEnabled $true-AdminAuditLogCmdlets *Mailbox* command. Does that meet the goal?
- A. Yes
- B. No
Answer: B
Explanation:
References:
https://docs.microsoft.com/en-us/powershell/module/exchange/policy-and-compliance-audit/setadminauditlogconfig?view=exchange-ps
NEW QUESTION 14
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some questions sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in Security & Compliance to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1. You run the Set-MailboxFolderPermission –Identity "User1"
-User User1@contoso.com –AccessRights Owner command. Does that meet the goal?
- A. Yes
- B. No
Answer: B
Explanation:
References:
https://docs.microsoft.com/en-us/powershell/module/exchange/mailboxes/set- mailbox?view=exchange-ps
NEW QUESTION 15
You have a Microsoft 365 subscription.
You need to enable auditing for all Microsoft Exchange Online users. What should you do?
- A. From the Exchange admin center, create a journal rule
- B. Run the Set-MailboxDatabase cmdlet
- C. Run the Set-Mailbox cmdlet
- D. From the Exchange admin center, create a mail flow message trace rule.
Answer: C
Explanation:
Reference:
https://docs.microsoft.com/en-us/office365/securitycompliance/enable-mailbox-auditing
NEW QUESTION 16
You have a Microsoft 365 E5 subscription and a hybrid Microsoft Exchange Server organization.
Each member of a group named Executive has an on-premises mailbox. Only the Executive group members have multi-factor authentication (MFA) enabled. Each member of a group named Research has a mailbox in Exchange Online.
You need to use Microsoft Office 365 Attack simulator to model a spear-phishing attack that targets the Research group members.
The email address that you intend to spoof belongs to the Executive group members. What should you do first?
- A. From Azure ATP admin center, configure the primary workspace settings
- B. From the Microsoft Azure portal, configure the user risk settings in Azure AD Identity Protection
- C. Enable MFA for the Research group members
- D. Migrate the Executive group members to Exchange Online
Answer: C
Explanation:
Reference:
https://docs.microsoft.com/en-us/office365/securitycompliance/attack-simulator
NEW QUESTION 17
You have a Microsoft 365 subscription that includes a user named User1.
You have a conditional access policy that applies to Microsoft Exchange Online. The conditional access policy is configured to use Conditional Access App Control.
You need to create a Microsoft Cloud App Security policy that blocks User1 from printing from Exchange
Online.
Which type of Cloud App Security policy should you create?
- A. an app permission policy
- B. an activity policy
- C. a Cloud Discovery anomaly detection policy
- D. a session policy
Answer: D
NEW QUESTION 18
Note: This question is part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription that is associated to a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You use Active Directory Federation Services (AD FS) to federate on-premises Active Directory and the tenant. Azure AD Connect has the following settings:
•Source Anchor: objectGUID
•Password Hash Synchronization: Disabled
•Password writeback: Disabled
•Directory extension attribute sync: Disabled
•Azure AD app and attribute filtering: Disabled
•Exchange hybrid deployment: Disabled
•User writeback: Disabled
You need to ensure that you can use leaked credentials detection in Azure AD Identity Protection. Solution: You modify the Password Hash Synchronization settings.
Does that meet the goal?
- A. Yes
- B. No
Answer: A
Explanation:
References:
https://docs.microsoft.com/en-us/azure/security/azure-ad-secure-steps
NEW QUESTION 19
Your company has a Microsoft 365 subscription.
The company forbids users to enroll personal devices in mobile device management (MDM). Users in the sales department have personal iOS devices.
You need to ensure that the sales department users can use the Microsoft Power BI app from iOS devices to access the Power BI data in your tenant.
The users must be prevented from backing up the app’s data to iCloud. What should you create?
- A. a conditional access policy in Microsoft Azure Active Directory (Azure AD) that has a device state condition
- B. an app protection policy in Microsoft Intune
- C. a conditional access policy in Microsoft Azure Active Directory (Azure AD) that has a client apps condition
- D. a device compliance policy in Microsoft Intune
Answer: B
NEW QUESTION 20
HOTSPOT
You are evaluating which devices are compliant in Intune.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.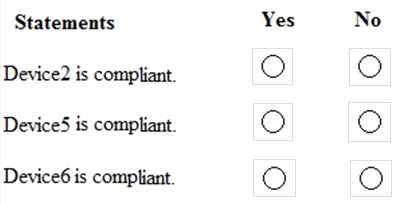
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 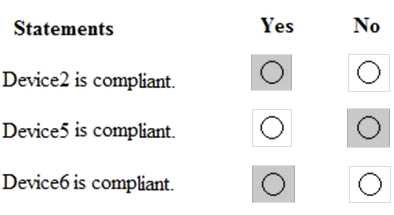
NEW QUESTION 21
HOTSPOT
You are evaluating which finance department users will be prompted for Azure MFA credentials. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.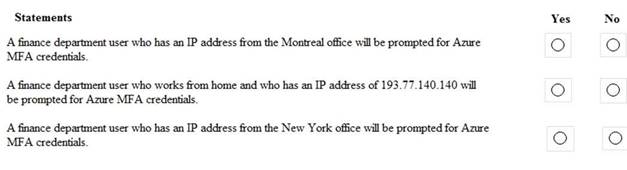
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 
NEW QUESTION 22
......
P.S. Certleader now are offering 100% pass ensure MS-500 dumps! All MS-500 exam questions have been updated with correct answers: https://www.certleader.com/MS-500-dumps.html (114 New Questions)
- [2021-New] Microsoft 70-744 Dumps With Update Exam Questions (21-30)
- [2021-New] Microsoft 70-332 Dumps With Update Exam Questions (71-80)
- [2021-New] Microsoft 70-417 Dumps With Update Exam Questions (151-160)
- [2021-New] Microsoft 70-480 Dumps With Update Exam Questions (41-50)
- [2021-New] Microsoft 70-499 Dumps With Update Exam Questions (31-40)
- [2021-New] Microsoft 70-384 Dumps With Update Exam Questions (111-120)
- The Secret Of Microsoft SC-100 Exam Dumps
- [2021-New] Microsoft 70-535 Dumps With Update Exam Questions (2-11)
- [2021-New] Microsoft 70-497 Dumps With Update Exam Questions (21-30)
- [2021-New] Microsoft 70-331 Dumps With Update Exam Questions (71-80)

