NSE4_FGT-6.2 Exam Questions - Online Test
NSE4_FGT-6.2 Premium VCE File

150 Lectures, 20 Hours

Master the NSE4_FGT-6.2 Fortinet NSE 4 - FortiOS 6.2 content and be ready for exam day success quickly with this Certleader NSE4_FGT-6.2 actual test. We guarantee it!We make it a reality and give you real NSE4_FGT-6.2 questions in our Fortinet NSE4_FGT-6.2 braindumps.Latest 100% VALID Fortinet NSE4_FGT-6.2 Exam Questions Dumps at below page. You can use our Fortinet NSE4_FGT-6.2 braindumps and pass your exam.
Check NSE4_FGT-6.2 free dumps before getting the full version:
NEW QUESTION 1
Which of the following statements about central NAT are true? (Choose two.)
- A. IP tool references must be removed from existing firewall policies before enabling central NAT.
- B. Central NAT can be enabled or disabled from the CLI only.
- C. Source NAT, using central NAT, requires at least one central SNAT policy.
- D. Destination NAT, using central NAT, requires a VIP object as the destination address in a firewall.
Answer: AB
NEW QUESTION 2
Examine the IPS sensor configuration shown in the exhibit, and then answer the question below.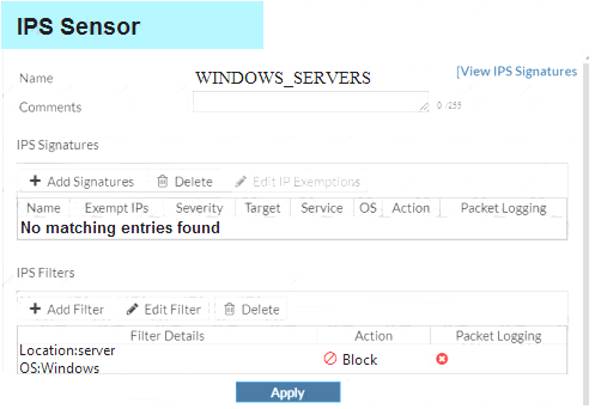
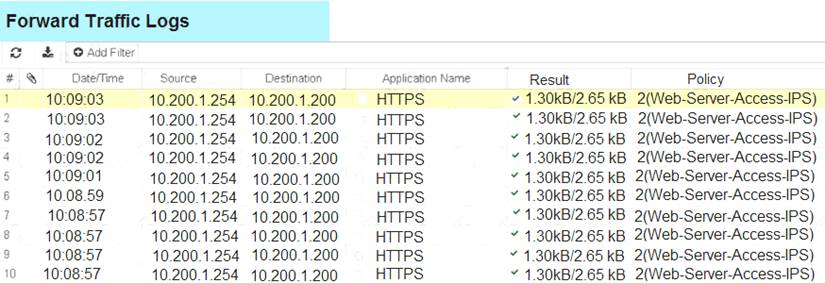
An administrator has configured the WINDOS_SERVERS IPS sensor in an attempt to determine
whether the influx of HTTPS traffic is an attack attempt or not. After applying the IPS sensor, FortiGate is still not generating any IPS logs for the HTTPS traffic.
What is a possible reason for this?
- A. The IPS filter is missing the Protocol: HTTPS option.
- B. The HTTPS signatures have not been added to the sensor.
- C. A DoS policy should be used, instead of an IPS sensor.
- D. A DoS policy should be used, instead of an IPS sensor.
- E. The firewall policy is not using a full SSL inspection profile.
Answer: E
NEW QUESTION 3
During the digital verification process, comparing the original and fresh hash results satisfies which security requirement?
- A. Authentication.
- B. Data integrity.
- C. Non-repudiation.
- D. Signature verification.
Answer: D
NEW QUESTION 4
NGFW mode allows policy-based configuration for most inspection rules. Which security profile’s configuration does not change when you enable policy-based inspection?
- A. Web filtering
- B. Antivirus
- C. Web proxy
- D. Application control
Answer: B
NEW QUESTION 5
Examine this FortiGate configuration: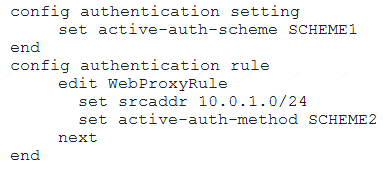
How does the FortiGate handle web proxy traffic coming from the IP address 10.2.1.200 that requires authorization?
- A. It always authorizes the traffic without requiring authentication.
- B. It drops the traffic.
- C. It authenticates the traffic using the authentication scheme SCHEME2.
- D. It authenticates the traffic using the authentication scheme SCHEME1.
Answer: D
Explanation:
“What happens to traffic that requires authorization, but does not match any authentication rule? The active and passive SSO schemes to use for those cases is defined under config authentication setting”
NEW QUESTION 6
Which is the correct description of a hash result as it relates to digital certificates?
- A. A unique value used to verify the input data
- B. An output value that is used to identify the person or deduce that authored the input data.
- C. An obfuscation used to mask the input data.
- D. An encrypted output value used to safe-guard the input data
Answer: A
NEW QUESTION 7
By default, when logging to disk, when does FortiGate delete logs?
- A. 30 days
- B. 1 year
- C. Never
- D. 7 days
Answer: D
NEW QUESTION 8
Which statements about antivirus scanning mode are true? (Choose two.)
- A. In proxy-based inspection mode antivirus buffers the whole file for scarring before sending it to the client.
- B. In flow-based inspection mode, you can use the CLI to configure antivirus profiles to use protocol option profiles.
- C. In proxy-based inspection mode, if a virus is detected, a replacement message may not be displayed immediately.
- D. In quick scan mode, you can configure antivirus profiles to use any of the available signature data bases.
Answer: AB
Explanation:
A: Buffers the whole file, packets sent to the client after scan finishes
B: When the antivirus profile is operating in flow-based inspection mode, two scanning mode options are available: full scan mode and quick scan mode.(Normal extended, or extreme-depending on what is configured in the CLI).
NEW QUESTION 9
You are configuring the root FortiGate to implement the security fabric. You are configuring port10 to communicate with a downstream FortiGate. View the default Edit Interface in the exhibit below: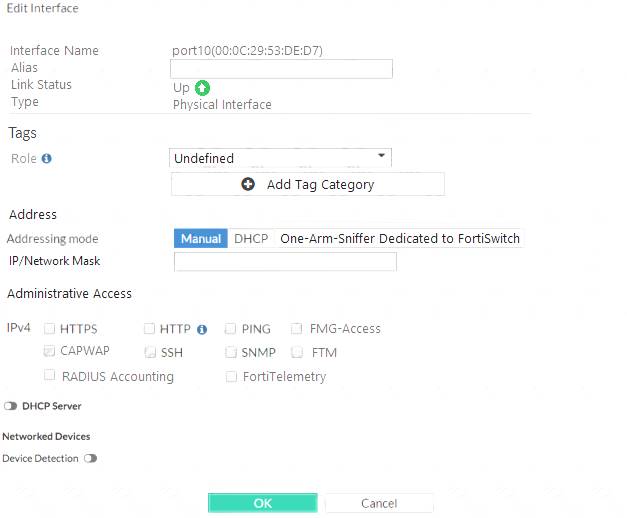
When configuring the root FortiGate to communicate with a downstream FortiGate, which settings are required to be configured? (Choose two.)
- A. Device detection enabled.
- B. Administrative Access: FortiTelemetry.
- C. IP/Network Mask.
- D. Role: Security Fabric.
Answer: BC
NEW QUESTION 10
If the Issuer and Subject values are the same in a digital certificate, which type of entity was the certificate issued to?
- A. A CRL
- B. A person
- C. A subordinate CA
- D. A root CA
Answer: D
NEW QUESTION 11
When override is enabled, which of the following shows the process and selection criteria that are used to elect the primary FortiGate in an HA cluster?
- A. Connected monitored ports > HA uptime > priority > serial number
- B. Priority > Connected monitored ports > HA uptime > serial number
- C. Connected monitored ports > priority > HA uptime > serial number
- D. HA uptime > priority > Connected monitored ports > serial number
Answer: C
NEW QUESTION 12
What FortiGate components are tested during the hardware test? (Choose three.)
- A. Administrative access
- B. HA heartbeat
- C. CPU
- D. Hard disk
- E. Network interfaces
Answer: CDE
NEW QUESTION 13
Which of the following services can be inspected by the DLP profile? (Choose three.)
- A. NFS
- B. FTP
- C. IMAP
- D. CIFS
- E. HTTP-POST
Answer: BCE
NEW QUESTION 14
How does FortiGate select the central SNAT policy that is applied to a TCP session?
- A. It selects the SNAT policy specified in the configuration of the outgoing interface.
- B. It selects the first matching central SNAT policy, reviewing from top to bottom.
- C. It selects the central SNAT policy with the lowest priority.
- D. It selects the SNAT policy specified in the configuration of the firewall policy that matches the traffic.
Answer: A
NEW QUESTION 15
Why must you use aggressive mode when a local FortiGate IPSec gateway hosts multiple dialup tunnels?
- A. In aggressive mode, the remote peers are able to provide their peer IDs in the first message.
- B. FortiGate is able to handle NATed connections only in aggressive mode.
- C. FortiClient only supports aggressive mode.
- D. Main mode does not support XAuth for user authentication.
Answer: A
NEW QUESTION 16
View the exhibit.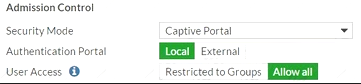
Which users and user groups are allowed access to the network through captive portal?
- A. Users and groups defined in the firewall policy.
- B. Only individual users – not groups – defined in the captive portal configuration
- C. Groups defined in the captive portal configuration
- D. All users
Answer: A
NEW QUESTION 17
Which of the following conditions are required for establishing an IPSec VPN between two FortiGate devices? (Choose two.)
- A. If XAuth is enabled as a server in one peer, it must be enabled as a client in the other peer.
- B. If the VPN is configured as route-based, there must be at least one firewall policy with the action set toIPSec.
- C. If the VPN is configured as DialUp User in one peer, it must be configured as either Static IP Address or Dynamic DNS in the other peer.
- D. If the VPN is configured as a policy-based in one peer, it must also be configured as policy-based in the other peer.
Answer: AC
NEW QUESTION 18
Which statement regarding the firewall policy authentication timeout is true?
- A. It is an idle timeou
- B. The FortiGate considers a user to be “idle” if it does not see any packets coming from the user’s source IP.
- C. It is a hard timeou
- D. The FortiGate removes the temporary policy for a user’s source IP address after this timer has expired.
- E. It is an idle timeou
- F. The FortiGate considers a user to be “idle” if it does not see any packets coming from the user’s source MAC.
- G. It is a hard timeou
- H. The FortiGate removes the temporary policy for a user’s source MAC address after this timer has expired.
Answer: A
NEW QUESTION 19
An administrator is investigating a report of users having intermittent issues with browsing the web. The administrator ran diagnostics and received the output shown in the exhibit.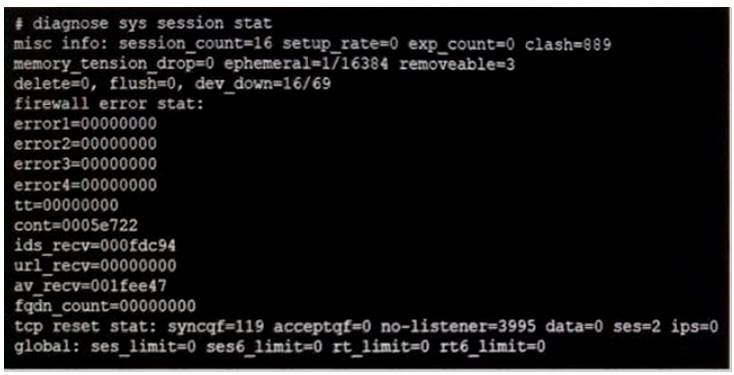
Examine the diagnostic output shown exhibit. Which of the following options is the most likely cause of this issue?
- A. NAT port exhaustion
- B. High CPU usage
- C. High memory usage
- D. High session timeout value
Answer: A
NEW QUESTION 20
Which of the following statements about converse mode are true? (Choose two.)
- A. FortiGate stops sending files to FortiSandbox for inspection.
- B. FortiGate stops doing RPF checks over incoming packets.
- C. Administrators cannot change the configuration.
- D. Administrators can access the FortiGate only through the console port.
Answer: AC
NEW QUESTION 21
An administrator needs to strengthen the security for SSL VPN access. Which of the following statements are best practices to do so? (Choose three.)
- A. Configure split tunneling for content inspection.
- B. Configure host restrictions by IP or MAC address.
- C. Configure two-factor authentication using security certificates.
- D. Configure SSL offloading to a content processor (FortiASIC).
- E. Configure a client integrity check (host-check).
Answer: BCE
NEW QUESTION 22
Which of the following statements are best practices for troubleshooting FSSO? (Choose two.)
- A. Include the group of guest users in a policy.
- B. Extend timeout timers.
- C. Guarantee at least 34 Kbps bandwidth between FortiGate and domain controllers.
- D. Ensure all firewalls allow the FSSO required ports.
Answer: AD
NEW QUESTION 23
......
P.S. Easily pass NSE4_FGT-6.2 Exam with 129 Q&As Certshared Dumps & pdf Version, Welcome to Download the Newest Certshared NSE4_FGT-6.2 Dumps: https://www.certshared.com/exam/NSE4_FGT-6.2/ (129 New Questions)
- How Many Questions Of NSE7_SDW-7.2 Actual Exam
- [2021-New] Fortinet NSE4 Dumps With Update Exam Questions (51-60)
- [2021-New] Fortinet NSE4 Dumps With Update Exam Questions (21-30)
- [2021-New] Fortinet NSE4-5.4 Dumps With Update Exam Questions (1-10)
- [2021-New] Fortinet NSE4-5.4 Dumps With Update Exam Questions (4-13)
- [2021-New] Fortinet NSE7 Dumps With Update Exam Questions (1-10)
- [2021-New] Fortinet NSE5 Dumps With Update Exam Questions (61-70)
- [2021-New] Fortinet NSE4 Dumps With Update Exam Questions (41-50)
- [2021-New] Fortinet NSE7 Dumps With Update Exam Questions (11-20)
- Top Tips Of Far Out NSE7_EFW-6.2 Testing Engine

