PT0-003 Exam Questions - Online Test
PT0-003 Premium VCE File

150 Lectures, 20 Hours

Proper study guides for Abreast of the times CompTIA CompTIA PenTest+ Exam certified begins with CompTIA PT0-003 preparation products which designed to deliver the Printable PT0-003 questions by making you pass the PT0-003 test at your first time. Try the free PT0-003 demo right now.
Online PT0-003 free questions and answers of New Version:
NEW QUESTION 1
Given the following statements:
✑ Implement a web application firewall.
✑ Upgrade end-of-life operating systems.
✑ Implement a secure software development life cycle.
In which of the following sections of a penetration test report would the above statements be found?
- A. Executive summary
- B. Attack narrative
- C. Detailed findings
- D. Recommendations
Answer: D
Explanation:
The given statements are actionable steps aimed at improving security. They fall under the recommendations section of a penetration test report. Here??s why option D is correct:
✑ Recommendations: This section of the report provides specific actions that should
be taken to mitigate identified vulnerabilities and improve the overall security posture. Implementing a WAF, upgrading operating systems, and implementing a secure SDLC are recommendations to enhance security.
✑ Executive Summary: This section provides a high-level overview of the findings
and their implications, intended for executive stakeholders.
✑ Attack Narrative: This section details the steps taken during the penetration test, describing the attack vectors and methods used.
✑ Detailed Findings: This section provides an in-depth analysis of each identified vulnerability, including evidence and technical details.
References from Pentest:
✑ Forge HTB: The report's recommendations section suggests specific measures to address the identified issues, similar to the given statements.
✑ Writeup HTB: Highlights the importance of the recommendations section in providing actionable steps to improve security based on the findings from the assessment.
Conclusion:
Option D, recommendations, is the correct section where the given statements would be found in a penetration test report.
=================
NEW QUESTION 2
A penetration tester is conducting reconnaissance for an upcoming assessment of a large corporate client. The client authorized spear phishing in the rules of engagement. Which of the following should the tester do first when developing the phishing campaign?
- A. Shoulder surfing
- B. Recon-ng
- C. Social media
- D. Password dumps
Answer: C
Explanation:
When developing a phishing campaign, the tester should first use social media to gather information about the targets.
✑ Social Media:
✑ Process:
✑ Other Options:
Pentest References:
✑ Spear Phishing: A targeted phishing attack aimed at specific individuals, using personal information to increase the credibility of the email.
✑ OSINT (Open Source Intelligence): Leveraging publicly available information to gather intelligence on targets, including through social media.
By starting with social media, the penetration tester can collect detailed and personalized information about the targets, which is essential for creating an effective spear phishing campaign.
=================
NEW QUESTION 3
During a security assessment, a penetration tester needs to exploit a vulnerability in a wireless network's authentication mechanism to gain unauthorized access to the network. Which of the following attacks would the tester most likely perform to gain access?
- A. KARMA attack
- B. Beacon flooding
- C. MAC address spoofing
- D. Eavesdropping
Answer: C
Explanation:
MAC address spoofing involves changing the MAC address of a network interface to mimic another device on the network. This technique is often used to bypass network access controls and gain unauthorized access to a network.
✑ Understanding MAC Address Spoofing:
✑ Purpose:
✑ Tools and Techniques:
Step-by-Step Explanationifconfig eth0 hw ether 00:11:22:33:44:55
✑ uk.co.certification.simulator.questionpool.PList@55bce337
✑ Impact:
✑ Detection and Mitigation:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups Top of Form
Bottom of Form
=================
NEW QUESTION 4
Which of the following is a term used to describe a situation in which a penetration tester bypasses physical access controls and gains access to a facility by entering at the same time as an employee?
- A. Badge cloning
- B. Shoulder surfing
- C. Tailgating
- D. Site survey
Answer: C
Explanation:
✑ Understanding Tailgating:
✑ Methods to Prevent Tailgating:
✑ Examples in Penetration Testing:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 5
A penetration tester established an initial compromise on a host. The tester wants to pivot to other targets and set up an appropriate relay. The tester needs to enumerate through the compromised host as a relay from the tester's machine. Which of the following commands should the tester use to do this task from the tester's host?
- A. attacker_host$ nmap -sT <target_cidr> | nc -n <compromised_host> 22
- B. attacker_host$ mknod backpipe p attacker_host$ nc -l -p 8000 | 0<backpipe | nc<target_cidr> 80 | tee backpipe
- C. attacker_host$ nc -nlp 8000 | nc -n <target_cidr> attacker_host$ nmap -sT 127.0.0.1 8000
- D. attacker_host$ proxychains nmap -sT <target_cidr>
Answer: D
Explanation:
ProxyChains is a tool that allows you to route your traffic through a chain of proxy servers, which can be used to anonymize your network activity. In this context, it is being used to route Nmap scan traffic through the compromised host, allowing the penetration tester to pivot and enumerate other targets within the network.
✑ Understanding ProxyChains:
✑ Command Breakdown:
✑ Setting Up ProxyChains: Step-by-Step Explanationplaintext Copy code
socks4 127.0.0.1 1080
✑ Execution:
proxychains nmap -sT <target_cidr>
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 6
A penetration tester cannot find information on the target company's systems using common OSINT methods. The tester's attempts to do reconnaissance against internet- facing resources have been blocked by the company's WAF. Which of the following is the best way to avoid the WAF and gather information about the target company's systems?
- A. HTML scraping
- B. Code repository scanning
- C. Directory enumeration
- D. Port scanning
Answer: B
Explanation:
When traditional reconnaissance methods are blocked, scanning code repositories is an effective method to gather information. Here??s why:
✑ Code Repository Scanning:
✑ Comparison with Other Methods:
Scanning code repositories allows gathering a wide range of information that can be critical for further penetration testing effort
=================
NEW QUESTION 7
A penetration tester assesses an application allow list and has limited command-line access on the Windows system. Which of the following would give the penetration tester information that could aid in continuing the test?
- A. mmc.exe
- B. icacls.exe
- C. nltest.exe
- D. rundll.exe
Answer: C
Explanation:
When a penetration tester has limited command-line access on a Windows system, the choice of tool is critical for gathering information to aid in furthering the test. Here??s an explanation for each option:
✑ mmc.exe (Microsoft Management Console):
✑ icacls.exe:
✑ nltest.exe:
✑ rundll.exe:
Conclusion: nltest.exe is the best choice among the given options as it provides valuable information about the network, domain controllers, and trust relationships. This information is crucial for a penetration tester to plan further actions and understand the domain environment.
=================
NEW QUESTION 8
A penetration tester runs a vulnerability scan that identifies several issues across numerous customer hosts. The executive report outlines the following information:
Server High-severity vulnerabilities
* 1. Development sandbox server 32
* 2. Back office file transfer server 51
* 3. Perimeter network web server 14
* 4. Developer QA server 92
The client is con ble monitoring mode using Aircrack-ng ch of the following hosts should the penetration tester select for additional manual testing?
- A. Server 1
- B. Server 2
- C. Server 3
- D. Server 4
Answer: C
Explanation:
✑ Client Concern:
✑ Server Analysis:
✑ Pentest References:
By selecting Server 3 (the perimeter network web server) for additional manual testing, the penetration tester addresses the client's primary concern about the availability and security of the consumer-facing production application.
=================
NEW QUESTION 9
Which of the following tasks would ensure the key outputs from a penetration test are not lost as part of the cleanup and restoration activities?
- A. Preserving artifacts
- B. Reverting configuration changes
- C. Keeping chain of custody
- D. Exporting credential data
Answer: A
Explanation:
Preserving artifacts ensures that key outputs from the penetration test, such as logs,
screenshots, captured data, and any generated reports, are retained for analysis, reporting, and future reference.
✑ Importance of Preserving Artifacts:
✑ Types of Artifacts:
✑ Best Practices:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 10
SIMULATION
SIMULATION
Using the output, identify potential attack vectors that should be further investigated.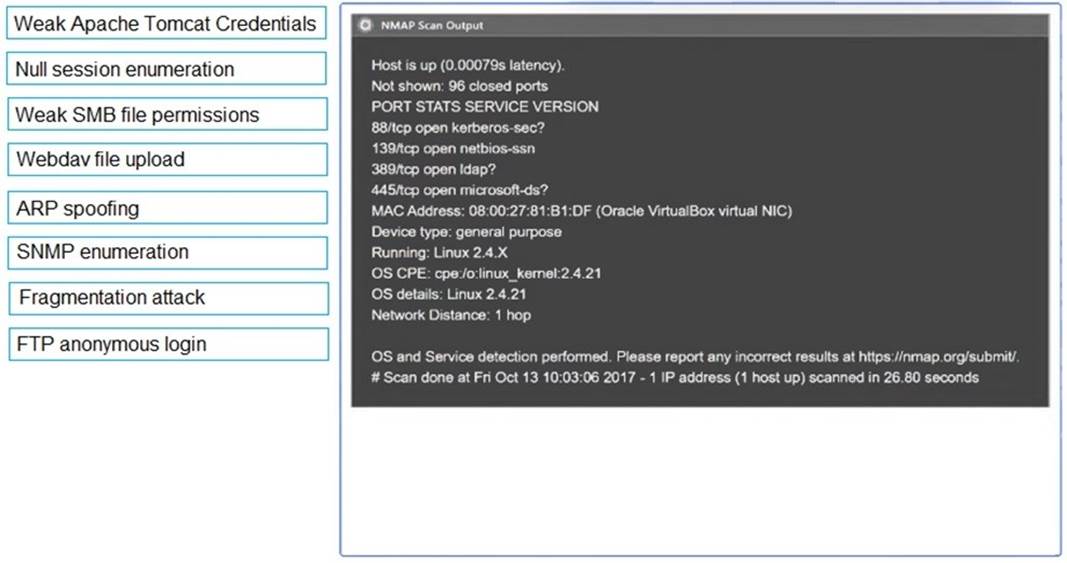
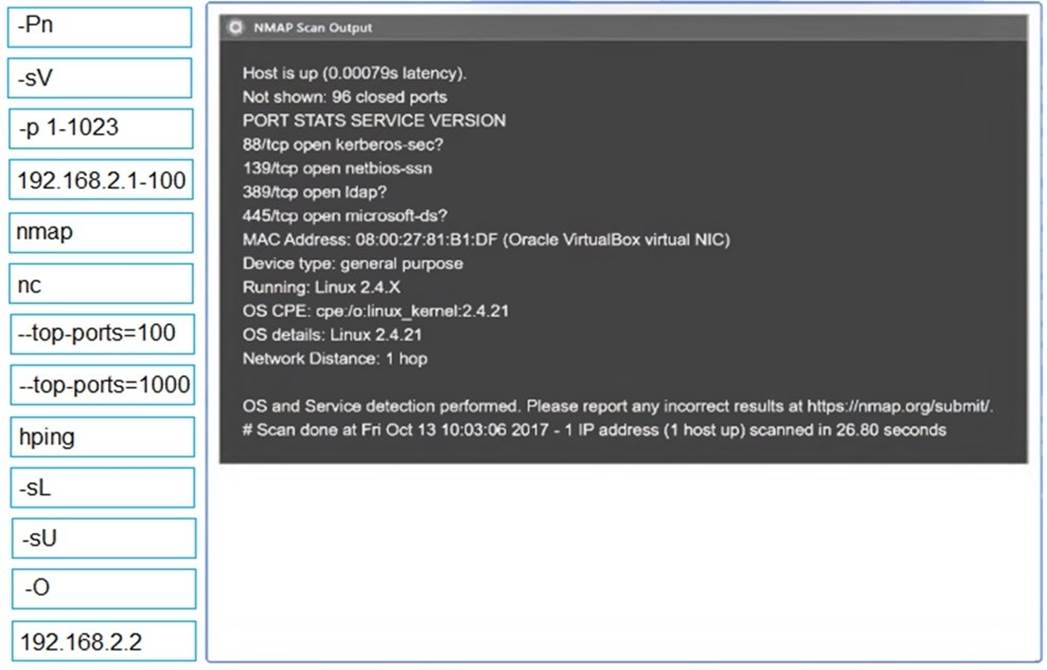
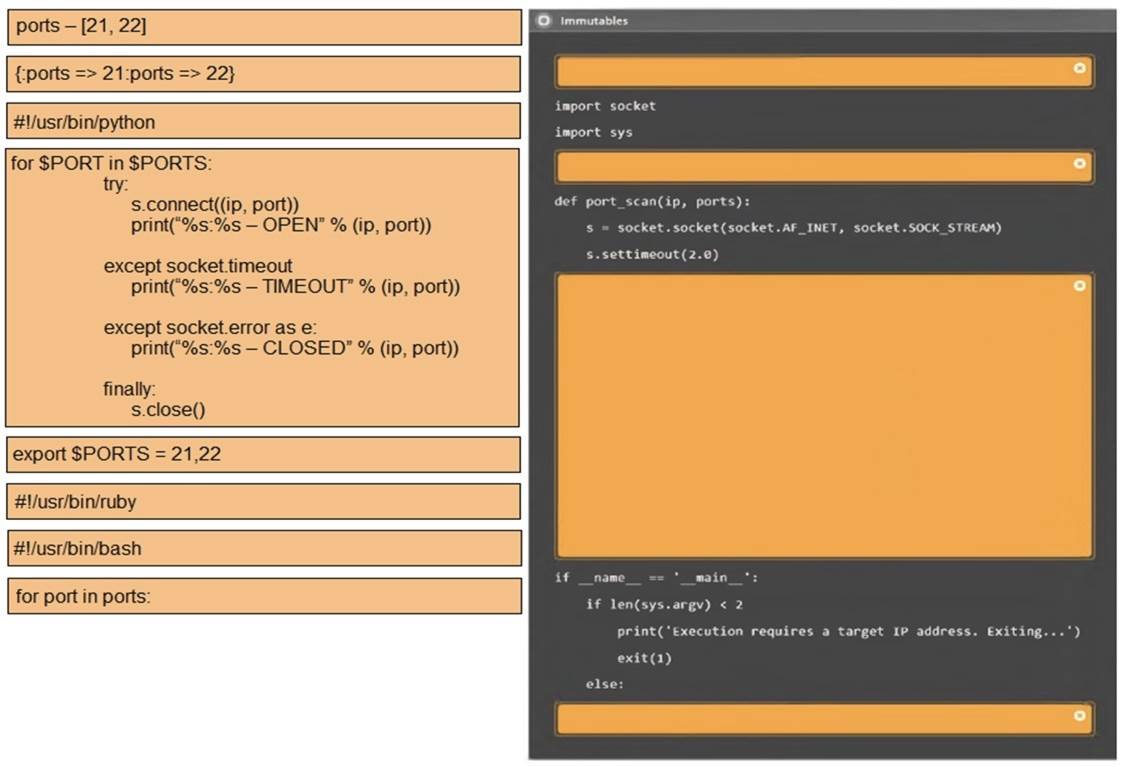
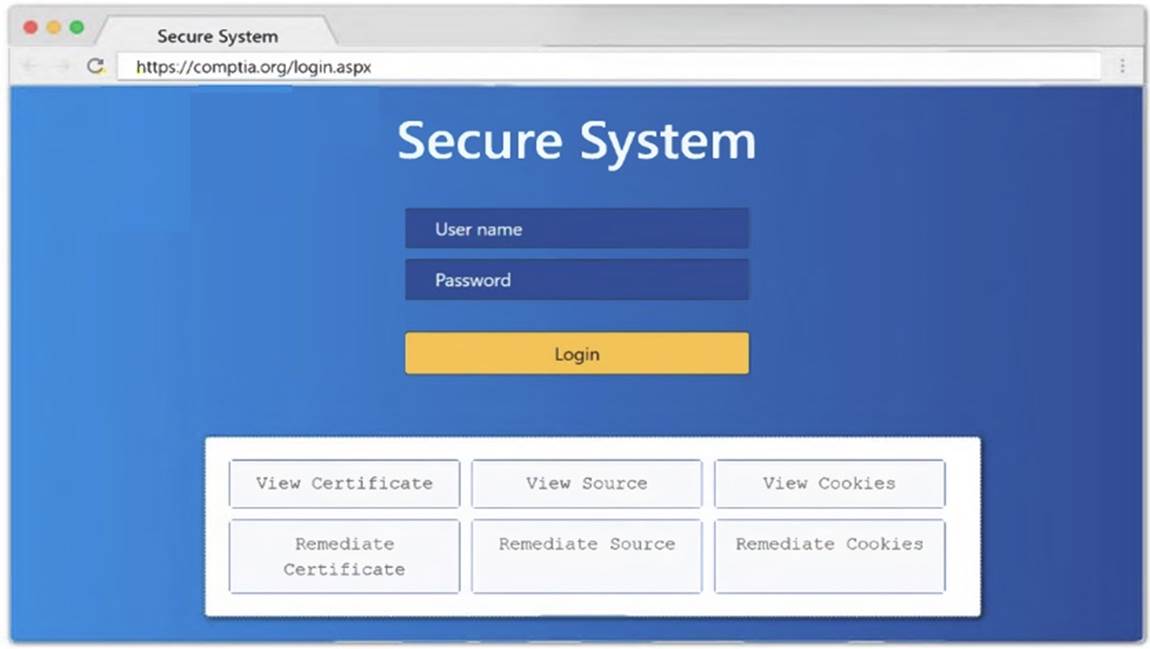
Solution:
1: Null session enumeration Weak SMB file permissions Fragmentation attack
2: nmap
-sV
-p 1-1023
: 192.168.2.2
3: #!/usr/bin/python export $PORTS = 21,22 for $PORT in $PORTS: try:
s.connect((ip, port))
print(??%s:%s – OPEN?? % (ip, port)) except socket.timeout
print(??%:%s – TIMEOUT?? % (ip, port)) except socket.error as e:
print(??%:%s – CLOSED?? % (ip, port)) finally
s.close() port_scan(sys.argv[1], ports)
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 11
A penetration tester would like to leverage a CSRF vulnerability to gather sensitive details from an application's end users. Which of the following tools should the tester use for this task?
- A. Browser Exploitation Framework
- B. Maltego
- C. Metasploit
- D. theHarvester
Answer: A
Explanation:
Cross-Site Request Forgery (CSRF) vulnerabilities can be leveraged to trick authenticated users into performing unwanted actions on a web application. The right tool for this task would help in exploiting web-based vulnerabilities, particularly those related to web browsers and interactions.
✑ Browser Exploitation Framework (BeEF) (Answer: A):
✑ Maltego (Option B):
✑ Metasploit (Option C):
✑ theHarvester (Option D):
Conclusion: The Browser Exploitation Framework (BeEF) is the most suitable tool for leveraging a CSRF vulnerability to gather sensitive details from an application's end users. It is specifically designed for browser-based exploitation, making it the best choice for this task.
NEW QUESTION 12
A penetration tester is conducting a wireless security assessment for a client with 2.4GHz and 5GHz access points. The tester places a wireless USB dongle in the laptop to start capturing WPA2 handshakes. Which of the following steps should the tester take next?
- A. Enable monitoring mode using Aircrack-ng.
- B. Use Kismet to automatically place the wireless dongle in monitor mode and collect handshakes.
- C. Run KARMA to break the password.
- D. Research WiGLE.net for potential nearby client access points.
Answer: A
Explanation:
✑ Monitoring Mode:
✑ Aircrack-ng Suite: airmon-ng start wlan0
This command starts the interface wlan0 in monitoring mode.
✑ Steps to Capture WPA2 Handshakes: airodump-ng wlan0mon
Pentest References:
✑ Wireless Security Assessments: Understanding the importance of monitoring mode for capturing data during wireless penetration tests.
✑ Aircrack-ng Tools: Utilizing the suite effectively for tasks like capturing WPA2 handshakes, deauthenticating clients, and cracking passwords.
By enabling monitoring mode with Aircrack-ng, the tester can capture the necessary WPA2 handshakes to further analyze and attempt to crack the Wi-Fi network's password.
=================
NEW QUESTION 13
A penetration tester identifies an exposed corporate directory containing first and last names and phone numbers for employees. Which of the following attack techniques would be the most effective to pursue if the penetration tester wants to compromise user accounts?
- A. Smishing
- B. Impersonation
- C. Tailgating
- D. Whaling
Answer: A
Explanation:
When a penetration tester identifies an exposed corporate directory containing first and last names and phone numbers, the most effective attack technique to pursue would be smishing. Here's why:
✑ Understanding Smishing:
✑ Why Smishing is Effective:
✑ Alternative Attack Techniques:
=================
NEW QUESTION 14
While conducting a reconnaissance activity, a penetration tester extracts the following information:
Emails: - admin@acme.com - sales@acme.com - support@acme.com
Which of the following risks should the tester use to leverage an attack as the next step in the security assessment?
- A. Unauthorized access to the network
- B. Exposure of sensitive servers to the internet
- C. Likelihood of SQL injection attacks
- D. Indication of a data breach in the company
Answer: A
Explanation:
When a penetration tester identifies email addresses during reconnaissance, the most immediate risk to leverage for an attack is unauthorized access to the network. Here??s why:
✑ Phishing Attacks:
✑ Spear Phishing:
✑ Comparison with Other Risks:
Email addresses are a starting point for phishing attacks, making unauthorized access to the network the most relevant risk.
=================
NEW QUESTION 15
A penetration tester is testing a power plant's network and needs to avoid disruption to the grid. Which of the following methods is most appropriate to identify vulnerabilities in the network?
- A. Configure a network scanner engine and execute the scan.
- B. Execute a testing framework to validate vulnerabilities on the devices.
- C. Configure a port mirror and review the network traffic.
- D. Run a network mapper tool to get an understanding of the devices.
Answer: C
Explanation:
When testing a power plant's network and needing to avoid disruption to the grid, configuring a port mirror and reviewing the network traffic is the most appropriate method to identify vulnerabilities without causing disruptions.
✑ Port Mirroring:
✑ Avoiding Disruption:
✑ Other Options:
Pentest References:
✑ Passive Monitoring: Passive techniques such as port mirroring are essential in environments where maintaining operational integrity is critical.
✑ Critical Infrastructure Security: Understanding the need for non-disruptive methods in critical infrastructure penetration testing to ensure continuous operations.
By configuring a port mirror and reviewing network traffic, the penetration tester can identify vulnerabilities in the power plant's network without risking disruption to the grid.
=================
NEW QUESTION 16
......
100% Valid and Newest Version PT0-003 Questions & Answers shared by Certshared, Get Full Dumps HERE: https://www.certshared.com/exam/PT0-003/ (New 131 Q&As)
- Top Quality CompTIA SY0-701 Exams Online
- [2021-New] CompTIA SY0-501 Dumps With Update Exam Questions (1-10)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (1-10)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (331-340)
- What Tested PT0-003 Pdf Is
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (31-40)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (101-110)
- Renovate Jn0-361 Pdf Exam For Service Provider Routing And Switching, Specialist Exam Certification
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (111-120)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (21-30)

