SY0-601 Exam Questions - Online Test
SY0-601 Premium VCE File

150 Lectures, 20 Hours

Act now and download your CompTIA SY0-601 test today! Do not waste time for the worthless CompTIA SY0-601 tutorials. Download Up to the minute CompTIA CompTIA Security+ Exam exam with real questions and answers and begin to learn CompTIA SY0-601 with a classic professional.
Also have SY0-601 free dumps questions for you:
NEW QUESTION 1
Which of the following will MOST likely adversely impact the operations of unpatched traditional programmable-logic controllers, running a back-end LAMP server and OT systems with human-management interfaces that are accessible over the Internet via a web interface? (Choose two.)
- A. Cross-site scripting
- B. Data exfiltration
- C. Poor system logging
- D. Weak encryption
- E. SQL injection
- F. Server-side request forgery
Answer: DF
NEW QUESTION 2
A workwide manufacturing company has been experiencing email account compromised. In one incident, a user logged in from the corporate office in France, but then seconds later, the same user account attempted a login from Brazil. Which of the following account policies would BEST prevent this type of attack?
- A. Network location
- B. Impossible travel time
- C. Geolocation
- D. Geofencing
Answer: D
NEW QUESTION 3
A company uses wireless tor all laptops and keeps a very detailed record of its assets, along with a comprehensive list of devices that are authorized to be on the wireless network. The Chief Information Officer (CIO) is concerned about a script kiddie potentially using an unauthorized device to brute force the wireless PSK and obtain access to the internal network. Which of the following should the company implement to BEST prevent this from occurring?
- A. A BPDU guard
- B. WPA-EAP
- C. IP filtering
- D. A WIDS
Answer: B
NEW QUESTION 4
Which of the following control sets should a well-written BCP include? (Select THREE)
- A. Preventive
- B. Detective
- C. Deterrent
- D. Corrective
- E. Compensating
- F. Physical
- G. Recovery
Answer: ADG
NEW QUESTION 5
An organization suffered an outage and a critical system took 90 minutes to come back online. Though there was no data loss during the outage, the expectation was that the critical system would be available again within 60 minutes Which of the following is the 60-minute expectation an example of:
- A. MTBF
- B. RPO
- C. MTTR
- D. RTO
Answer: D
NEW QUESTION 6
A RAT that was used to compromise an organization’s banking credentials was found on a user’s computer. The RAT evaded antivirus detection. It was installed by a user who has local administrator rights to the system as part of a remote management tool set. Which of the following recommendations would BEST prevent this from reoccurring?
- A. Create a new acceptable use policy.
- B. Segment the network into trusted and untrusted zones.
- C. Enforce application whitelisting.
- D. Implement DLP at the network boundary.
Answer: C
NEW QUESTION 7
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites. INSTRUCTIONS
Click on each firewall to do the following:  Deny cleartext web traffic.
Deny cleartext web traffic. Ensure secure management protocols are used.
Ensure secure management protocols are used.  Resolve issues at the DR site.
Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.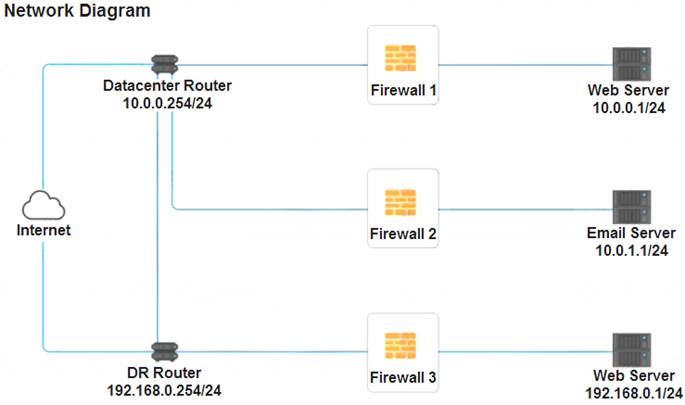

- A.
Answer: A
Explanation:
See explanation below.
Explanation
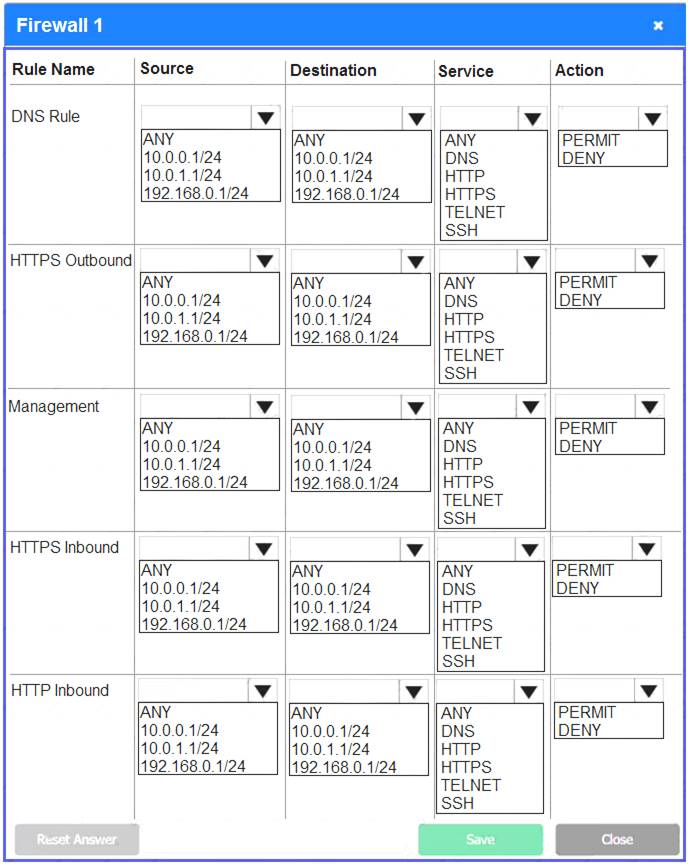
Firewall 1:

DNS Rule – ANY --> ANY --> DNS --> PERMIT
HTTPS Outbound – 10.0.0.1/24 --> ANY --> HTTPS --> PERMIT Management – ANY --> ANY --> SSH --> PERMIT
HTTPS Inbound – ANY --> ANY --> HTTPS --> PERMIT HTTP Inbound – ANY --> ANY --> HTTP --> DENY
Firewall 2: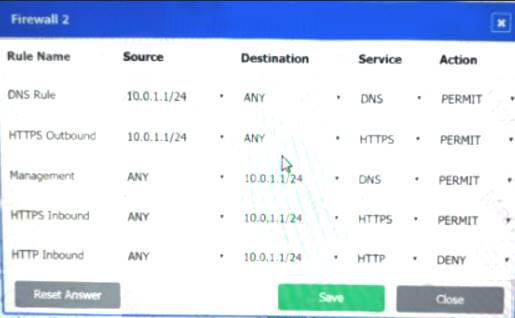

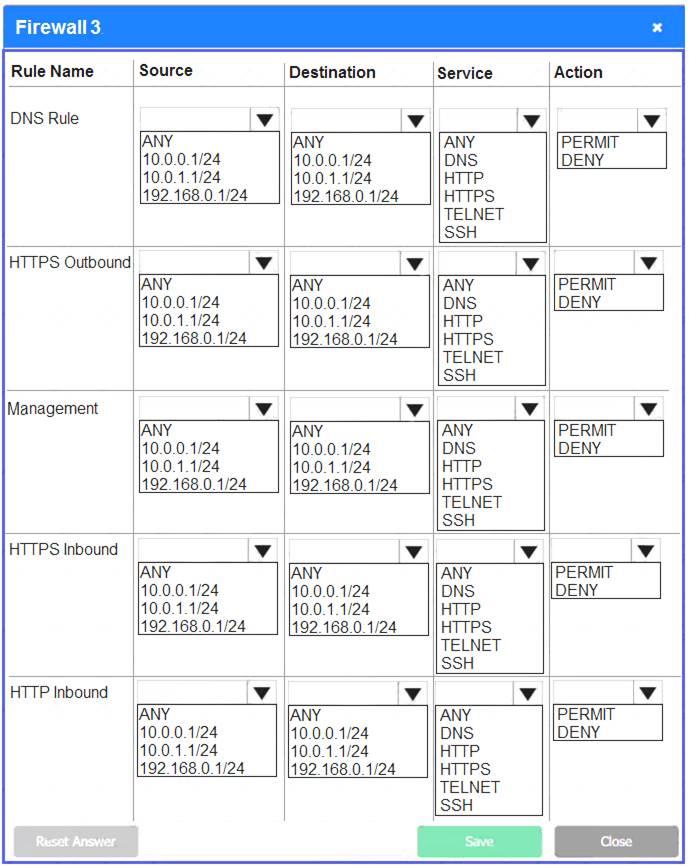
Firewall 3:

DNS Rule – ANY --> ANY --> DNS --> PERMIT
HTTPS Outbound – 192.168.0.1/24 --> ANY --> HTTPS --> PERMIT Management – ANY --> ANY --> SSH --> PERMIT
HTTPS Inbound – ANY --> ANY --> HTTPS --> PERMIT HTTP Inbound – ANY --> ANY --> HTTP --> DENY
NEW QUESTION 8
A security analyst needs to be proactive in understand the types of attacks that could potentially target the company's execute. Which of the following intelligence sources should to security analyst review?
- A. Vulnerability feeds
- B. Trusted automated exchange of indicator information
- C. Structured threat information expression
- D. Industry information-sharing and collaboration groups
Answer: D
NEW QUESTION 9
To reduce costs and overhead, an organization wants to move from an on-premises email solution to a cloud-based email solution. At this time, no other services will be moving. Which of the following cloud models would BEST meet the needs of the organization?
- A. MaaS
- B. laaS
- C. SaaS
- D. PaaS
Answer: D
NEW QUESTION 10
Company engineers regularly participate in a public Internet forum with other engineers throughout the industry. Which of the following tactics would an attacker MOST likely use in this scenario?
- A. Watering-hole attack
- B. Credential harvesting
- C. Hybrid warfare
- D. Pharming
Answer: A
NEW QUESTION 11
Phishing and spear-phishing attacks have been occurring more frequently against a company’s staff. Which of the following would MOST likely help mitigate this issue?
- A. DNSSEC and DMARC
- B. DNS query logging
- C. Exact mail exchanger records in the DNS
- D. The addition of DNS conditional forwarders
Answer: C
NEW QUESTION 12
After reading a security bulletin, a network security manager is concerned that a malicious actor may have breached the network using the same software flaw. The exploit code is publicly available and has been reported as being used against other industries in the same vertical. Which of the following should the network security manager consult FIRST to determine a priority list for forensic review?
- A. The vulnerability scan output
- B. The IDS logs
- C. The full packet capture data
- D. The SIEM alerts
Answer: A
NEW QUESTION 13
A security analyst needs to complete an assessment. The analyst is logged into a server and must use native tools to map services running on it to the server's listening ports. Which of the following tools can BEST accomplish this talk?
- A. Netcat
- B. Netstat
- C. Nmap
- D. Nessus
Answer: B
NEW QUESTION 14
A well-known organization has been experiencing attacks from APIs. The organization is concerned that custom malware is being created and emailed into the company or installed on USB sticks that are dropped in parking lots. Which of the following is the BEST defense against this scenario?
- A. Configuring signature-based antivirus io update every 30 minutes
- B. Enforcing S/MIME for email and automatically encrypting USB drives upon insertion.
- C. Implementing application execution in a sandbox for unknown software.
- D. Fuzzing new files for vulnerabilities if they are not digitally signed
Answer: C
NEW QUESTION 15
After a ransomware attack a forensics company needs to review a cryptocurrency transaction between the victim and the attacker. Which of the following will the company MOST likely review to trace this transaction?
- A. The public ledger
- B. The NetFlow data
- C. A checksum
- D. The event log
Answer: A
NEW QUESTION 16
A recently discovered zero-day exploit utilizes an unknown vulnerability in the SMB network protocol to rapidly infect computers. Once infected, computers are encrypted and held for ransom. Which of the following would BEST prevent this attack from reoccurring?
- A. Configure the perimeter firewall to deny inbound external connections to SMB ports.
- B. Ensure endpoint detection and response systems are alerting on suspicious SMB connections.
- C. Deny unauthenticated users access to shared network folders.
- D. Verify computers are set to install monthly operating system, updates automatically.
Answer: A
NEW QUESTION 17
An enterprise has hired an outside security firm to conduct penetration testing on its network and applications. The firm has only been given the documentation available to the customers of the applications. Which of the following BEST represents the type of testing that will occur?
- A. Bug bounty
- B. Black-box
- C. Gray-box
- D. White-box
Answer: A
NEW QUESTION 18
A company has determined that if its computer-based manufacturing is not functioning for 12 consecutive hours, it will lose more money that it costs to maintain the equipment. Which of the following must be less than 12 hours to maintain a positive total cost of ownership?
- A. MTBF
- B. RPO
- C. RTO
- D. MTTR
Answer: C
NEW QUESTION 19
A security analyst sees the following log output while reviewing web logs:
Which of the following mitigation strategies would be BEST to prevent this attack from being successful?
- A. Secure cookies
- B. Input validation
- C. Code signing
- D. Stored procedures
Answer: B
NEW QUESTION 20
A security analyst receives the configuration of a current VPN profile and notices the authentication is only applied to the IP datagram portion of the packet. Which of the following should the analyst implement to authenticate the entire packet?
- A. AH
- B. ESP
- C. SRTP
- D. LDAP
Answer: B
NEW QUESTION 21
......
Thanks for reading the newest SY0-601 exam dumps! We recommend you to try the PREMIUM Certleader SY0-601 dumps in VCE and PDF here: https://www.certleader.com/SY0-601-dumps.html (218 Q&As Dumps)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (1-10)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (11-20)
- [2021-New] CompTIA LX0-104 Dumps With Update Exam Questions (41-50)
- What Tested PT0-003 Pdf Is
- Rebirth PT0-001 Discount Pack 2021
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (81-90)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (611-620)
- Regenerate PT0-002 Free Dumps For CompTIA PenTest+ Certification Exam Certification
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (131-140)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (2-11)

