SY0-601 Exam Questions - Online Test
SY0-601 Premium VCE File

150 Lectures, 20 Hours

We provide real SY0-601 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass CompTIA SY0-601 Exam quickly & easily. The SY0-601 PDF type is available for reading and printing. You can print more and practice many times. With the help of our CompTIA SY0-601 dumps pdf and vce product and material, you can easily pass the SY0-601 exam.
Online SY0-601 free questions and answers of New Version:
NEW QUESTION 1
An organization has implemented a policy requiring the use of conductive metal lockboxes for personal electronic devices outside of a secure research lab. Which of the following did the organization determine to be the GREATEST risk to intellectual property when creating this policy?
- A. The theft of portable electronic devices
- B. Geotagging in the metadata of images
- C. Bluesnarfing of mobile devices
- D. Data exfiltration over a mobile hotspot
Answer: D
NEW QUESTION 2
The IT department at a university is concerned about professors placing servers on the university network in an attempt to bypass security controls. Which of the following BEST represents this type of threat?
- A. A script kiddie
- B. Shadow IT
- C. Hacktivism
- D. White-hat
Answer: B
NEW QUESTION 3
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 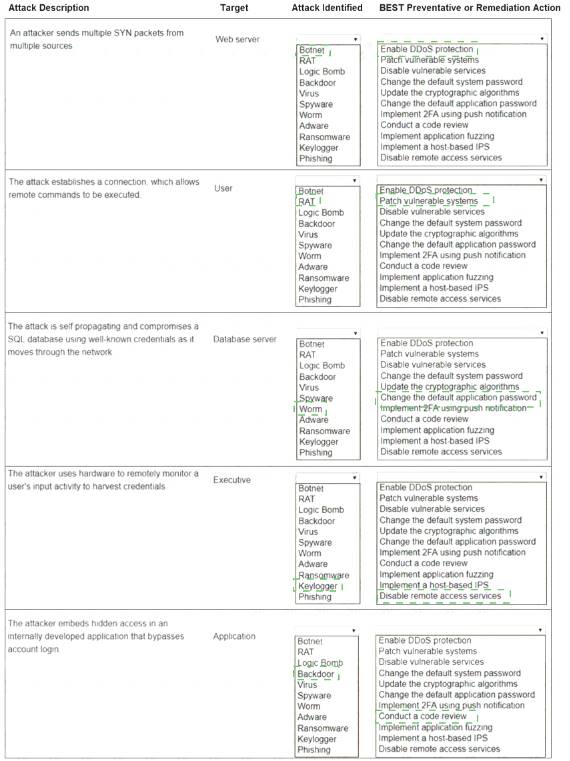
NEW QUESTION 4
A security analyst is performing a forensic investigation compromised account credentials. Using the Event Viewer, the analyst able to detect the following message, ‘’Special privileges assigned to new login.’’ Several of these messages did not have a valid logon associated with the user before these privileges were assigned. Which of the following attacks is MOST likely being detected?
- A. Pass-the-hash
- B. Buffer overflow
- C. Cross-site scripting
- D. Session replay
Answer: A
NEW QUESTION 5
A security analyst has been asked to investigate a situation after the SOC started to receive alerts from the SIEM. The analyst first looks at the domain controller and finds the following events: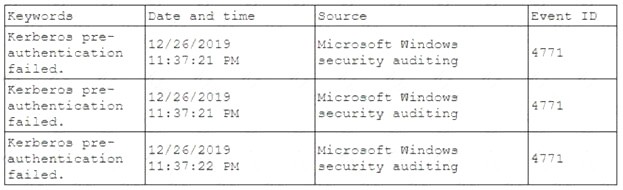
To better understand what is going on, the analyst runs a command and receives the following output:
Based on the analyst’s findings, which of the following attacks is being executed?
- A. Credential harvesting
- B. Keylogger
- C. Brute-force
- D. Spraying
Answer: D
NEW QUESTION 6
A security analyst reviews the datacenter access logs for a fingerprint scanner and notices an abundance of errors that correlate with users' reports of issues accessing the facility. Which of the following MOST likely the cause of the cause of the access issues?
- A. False rejection
- B. Cross-over error rate
- C. Efficacy rale
- D. Attestation
Answer: B
NEW QUESTION 7
Under GDPR, which of the following is MOST responsible for the protection of privacy and website user rights?
- A. The data protection officer
- B. The data processor
- C. The data owner
- D. The data controller
Answer: C
NEW QUESTION 8
A network administrator would like to configure a site-to-site VPN utilizing iPSec. The administrator wants the tunnel to be established with data integrity encryption, authentication and anti- replay functions Which of the following should the administrator use when configuring the VPN?
- A. AH
- B. EDR
- C. ESP
- D. DNSSEC
Answer: C
NEW QUESTION 9
Joe, an employee, receives an email stating he won the lottery. The email includes a link that requests a name, mobile phone number, address, and date of birth be provided to confirm Joe’s identity before sending him the prize. Which of the following BEST describes this type of email?
- A. Spear phishing
- B. Whaling
- C. Phishing
- D. Vishing
Answer: C
NEW QUESTION 10
A cybersecurity administrator has a reduced team and needs to operate an on-premises network and security infrastructure efficiently. To help with the situation, the administrator decides to hire a service provider. Which of the following should the administrator use?
- A. SDP
- B. AAA
- C. IaaS
- D. MSSP
- E. Microservices
Answer: D
NEW QUESTION 11
Which of the following relets to applications and systems that are used within an organization without consent or approval?
- A. Shadow IT
- B. OSINT
- C. Dark web
- D. Insider threats
Answer: A
NEW QUESTION 12
A manufacturer creates designs for very high security products that are required to be protected and controlled by the government regulations. These designs are not accessible by corporate networks or the Internet. Which of the following is the BEST solution to protect these designs?
- A. An air gap
- B. A Faraday cage
- C. A shielded cable
- D. A demilitarized zone
Answer: A
NEW QUESTION 13
An organization is concerned that is hosted web servers are not running the most updated version of the software. Which of the following would work BEST to help identify potential vulnerabilities?
- A. Hping3 –s comptia, org –p 80
- B. Nc -1 –v comptia, org –p 80
- C. nmp comptia, org –p 80 –aV
- D. nslookup –port=80 comtia.org
Answer: C
NEW QUESTION 14
The Chief Financial Officer (CFO) of an insurance company received an email from Ann, the company’s Chief Executive Officer (CEO), requesting a transfer of $10,000 to an account. The email states Ann is on vacation and has lost her purse, containing cash and credit cards. Which of the following social-engineering techniques is the attacker using?
- A. Phishing
- B. Whaling
- C. Typo squatting
- D. Pharming
Answer: B
NEW QUESTION 15
When used at the design stage, which of the following improves the efficiency, accuracy, and speed of a database?
- A. Tokenization
- B. Data masking
- C. Normalization
- D. Obfuscation
Answer: C
NEW QUESTION 16
Which of the following types of controls is a turnstile?
- A. Physical
- B. Detective
- C. Corrective
- D. Technical
Answer: A
NEW QUESTION 17
A cybersecurity analyst reviews the log files from a web server and sees a series of files that indicates a directory-traversal attack has occurred. Which of the following is the analyst MOST likely seeing?
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: B
NEW QUESTION 18
On which of the following is the live acquisition of data for forensic analysis MOST dependent? (Choose two.)
- A. Data accessibility
- B. Legal hold
- C. Cryptographic or hash algorithm
- D. Data retention legislation
- E. Value and volatility of data
- F. Right-to-audit clauses
Answer: EF
NEW QUESTION 19
An organization routes all of its traffic through a VPN Most users are remote and connect into a corporate datacenter that houses confidential information There is a firewall at the Internet border followed by a DIP appliance, the VPN server and the datacenter itself. Which of the following is the WEAKEST design element?
- A. The DLP appliance should be integrated into a NGFW.
- B. Split-tunnel connections can negatively impact the DLP appliance's performance
- C. Encrypted VPN traffic will not be inspected when entering or leaving the network
- D. Adding two hops in the VPN tunnel may slow down remote connections
Answer: C
NEW QUESTION 20
A company's Chief Information Office (CIO) is meeting with the Chief Information Security Officer (CISO) to plan some activities to enhance the skill levels of the company's developers. Which of the following would be MOST suitable for training the developers'?
- A. A capture-the-flag competition
- B. A phishing simulation
- C. Physical security training
- D. Baste awareness training
Answer: B
NEW QUESTION 21
......
Recommend!! Get the Full SY0-601 dumps in VCE and PDF From Allfreedumps.com, Welcome to Download: https://www.allfreedumps.com/SY0-601-dumps.html (New 218 Q&As Version)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (11-20)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (111-120)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (91-100)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (21-30)
- [2021-New] CompTIA LX0-104 Dumps With Update Exam Questions (51-60)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (611-620)
- [2021-New] CompTIA LX0-103 Dumps With Update Exam Questions (31-40)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (10-19)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (191-200)
- [2021-New] CompTIA N10-006 Dumps With Update Exam Questions (21-30)

