SSCP Exam Questions - Online Test
SSCP Premium VCE File

150 Lectures, 20 Hours

Our pass rate is high to 98.9% and the similarity percentage between our SSCP study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the ISC2 SSCP exam in just one try? I am currently studying for the ISC2 SSCP exam. Latest ISC2 SSCP Test exam practice questions and answers, Try ISC2 SSCP Brain Dumps First.
ISC2 SSCP Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Communications devices must operate:
- A. at different speeds to communicate.
- B. at the same speed to communicate.
- C. at varying speeds to interact.
- D. at high speed to interact.
Answer: B
Explanation:
Communications devices must operate at the same speed to communicate.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 100.
NEW QUESTION 2
Complete the blanks. When using PKI, I digitally sign a message using my key. The recipient verifies my signature using my key.
- A. Private / Public
- B. Public / Private
- C. Symmetric / Asymmetric
- D. Private / Symmetric
Answer: A
Explanation:
When we encrypt messages using our private keys which are only available to us. The person who wants to read and decrypt the message need only have our public keys to do so.
The whole point to PKI is to assure message integrity, authentication of the source, and to provide secrecy with the digital encryption.
See below a nice walktrough of Digital Signature creation and verification from the Comodo web site:
Digital Signatures apply the same functionality to an e-mail message or data file that a handwritten signature does for a paper-based document. The Digital Signature vouches for the origin and integrity of a message, document or other data file.
How do we create a Digital Signature?
The creation of a Digital Signature is a complex mathematical process. However as the complexities of the process are computed by the computer, applying a Digital Signature is no more difficult that creating a handwritten one!
The following text illustrates in general terms the processes behind the generation of a Digital Signature:
1. Alice clicks 'sign' in her email application or selects which file is to be signed.
2. Alice's computer calculates the 'hash' (the message is applied to a publicly known mathematical hashing function that coverts the message into a long number referred to as the hash).
3. The hash is encrypted with Alice's Private Key (in this case it is known as the Signing Key) to create the Digital Signature.
4. The original message and its Digital Signature are transmitted to Bob.
5. Bob receives the signed message. It is identified as being signed, so his email application knows which actions need to be performed to verify it.
6. Bob's computer decrypts the Digital Signature using Alice's Public Key.
7. Bob's computer also calculates the hash of the original message (remember - the mathematical function used by Alice to do this is publicly known).
8. Bob's computer compares the hashes it has computed from the received message with the now decrypted hash received with Alice's message.
digital signature creation and verification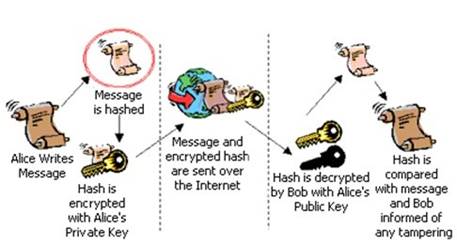
C:\Users\MCS\Desktop\1.jpg
If the message has remained integral during its transit (i.e. it has not been tampered with), when compared the two hashes will be identical.
However, if the two hashes differ when compared then the integrity of the original message has been compromised. If the original message is tampered with it will result in Bob's
computer calculating a different hash value. If a different hash value is created, then the original message will have been altered. As a result the verification of the Digital Signature will fail and Bob will be informed.
Origin, Integrity, Non-Repudiation, and Preventing Men-In-The-Middle (MITM) attacks
Eve, who wants to impersonate Alice, cannot generate the same signature as Alice because she does not have Alice's Private Key (needed to sign the message digest). If instead, Eve decides to alter the content of the message while in transit, the tampered message will create a different message digest to the original message, and Bob's computer will be able to detect that. Additionally, Alice cannot deny sending the message as it has been signed using her Private Key, thus ensuring non-repudiation.
creating and validating a digital signature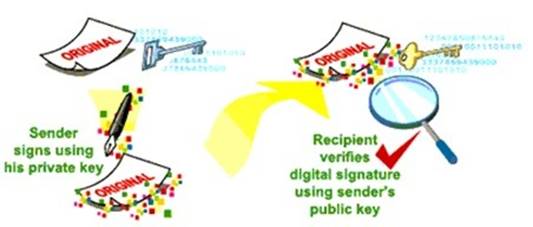
C:\Users\MCS\Desktop\1.jpg
Due to the recent Global adoption of Digital Signature law, Alice may now sign a transaction, message or piece of digital data, and so long as it is verified successfully it is a legally permissible means of proof that Alice has made the transaction or written the message.
The following answers are incorrect:
- Public / Private: This is the opposite of the right answer.
- Symmetric / Asymmetric: Not quite. Sorry. This form of crypto is asymmetric so you were almost on target.
- Private / Symmetric: Well, you got half of it right but Symmetric is wrong.
The following reference(s) was used to create this question:
The CCCure Holistic Security+ CBT, you can subscribe at: http://www.cccure.tv and
http://www.comodo.com/resources/small-business/digital-certificates3.php
NEW QUESTION 3
A momentary high voltage is a:
- A. spike
- B. blackout
- C. surge
- D. fault
Answer: A
Explanation:
Too much voltage for a short period of time is a spike. Too much voltage for a long period of time is a surge.
Not enough voltage for a short period of time is a sag or dip Not enough voltage for a long period of time is brownout
A short power interruption is a fault
A long power interruption is a blackout
You MUST know all of the power issues above for the purpose of the exam.
From: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, 3rd. Edition McGraw- Hill/Osborne, 2005, page 368.
NEW QUESTION 4
The RSA algorithm is an example of what type of cryptography?
- A. Asymmetric Key.
- B. Symmetric Key.
- C. Secret Key.
- D. Private Key.
Answer: A
Explanation:
The following answers are incorrect.
Symmetric Key. Is incorrect because RSA is a Public Key or a Asymmetric Key cryptographic system and not a Symmetric Key or a Secret Key cryptographic system.
Secret Key. Is incorrect because RSA is a Public Key or a Asymmetric Key cryptographic system and not a Secret Key or a Symmetric Key cryptographic system.
Private Key. Is incorrect because Private Key is just one part if an Asymmetric Key cryptographic system, a Private Key used alone is also called a Symmetric Key cryptographic system.
NEW QUESTION 5
Which backup method copies only files that have changed since the last full backup, but does not clear the archive bit?
- A. Differential backup method.
- B. Full backup method.
- C. Incremental backup method.
- D. Tape backup method.
Answer: A
Explanation:
One of the key item to understand regarding backup is the archive bit. The archive bit is used to determine what files have been backuped already. The archive bit is set if a file is modified or a new file is created, this indicates to the backup program that it has to be saved on the next backup. When a full backup is performed the archive bit will be cleared indicating that the files were backup. This allows backup programs to do an incremental or differential backup that only backs up the changes to the filesystem since the last time the bit was cleared
Full Backup (or Reference Backup)
A Full backup will backup all the files and folders on the drive every time you run the full backup. The archive bit is cleared on all files indicating they were all backuped.
Advantages:
All files from the selected drives and folders are backed up to one backup set.
In the event you need to restore files, they are easily restored from the single backup set.
Disadvantages:
A full backup is more time consuming than other backup options. Full backups require more disk, tape, or network drive space. Incremental Backup
An incremental backup provides a backup of files that have changed or are new since the last incremental backup.
For the first incremental backup, all files in the file set are backed up (just as in a full backup). If you use the same file set to perform a incremental backup later, only the files that have changed are backed up. If you use the same file set for a third backup, only the
files that have changed since the second backup are backed up, and so on.
Incremental backup will clear the archive bit. Advantages:
Backup time is faster than full backups.
Incremental backups require less disk, tape, or network drive space.
You can keep several versions of the same files on different backup sets. Disadvantages:
In order to restore all the files, you must have all of the incremental backups available.
It may take longer to restore a specific file since you must search more than one backup set to find the latest version of a file.
Differential Backup
A differential backup provides a backup of files that have changed since a full backup was performed. A differential backup typically saves only the files that are different or new since the last full backup. Together, a full backup and a differential backup include all the files on your computer, changed and unchanged.
Differential backup do not clear the archive bits. Advantages:
Differential backups require even less disk, tape, or network drive space than incremental
backups.
Backup time is faster than full or incremental backups. Disadvantages:
Restoring all your files may take considerably longer since you may have to restore both the last differential and full backup.
Restoring an individual file may take longer since you have to locate the file on either the differential or full backup.
For more info see: http://support.microsoft.com/kb/136621
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 69.
NEW QUESTION 6
Which of the following statements pertaining to the maintenance of an IT contingency plan is incorrect?
- A. The plan should be reviewed at least once a year for accuracy and completeness.
- B. The Contingency Planning Coordinator should make sure that every employee gets an up-to-date copy of the plan.
- C. Strict version control should be maintained.
- D. Copies of the plan should be provided to recovery personnel for storage offline at home and office.
Answer: B
Explanation:
Because the contingency plan contains potentially sensitive operational and personnel information, its distribution should be marked accordingly and controlled. Not all employees would obtain a copy, but only those involved in the execution of the plan.
All other statements are correct.
NOTE FROM CLEMENT:
I have received multiple emails stating the explanations contradict the correct answer. It seems many people have a hard time with negative question. In this case the Incorrect choice (the one that is not true) is the correct choice. Be very carefull of such questions, you will get some on the real exam as well.
Reference(s) used for this question:
SWANSON, Marianne, & al., National Institute of Standards and Technology (NIST), NIST Special Publication 800-34, Contingency Planning Guide for Information Technology Systems
NEW QUESTION 7
Which type of attack involves hijacking a session between a host and a target by predicting the target's choice of an initial TCP sequence number?
- A. IP spoofing attack
- B. SYN flood attack
- C. TCP sequence number attack
- D. Smurf attack
Answer: C
Explanation:
A TCP sequence number attack exploits the communication session which was established between the target and the trusted host that initiated the session. It involves hijacking the session between the host and the target by predicting the target's choice of an initial TCP sequence number. An IP spoofing attack is used to convince a system that it is communication with a known entity that gives an intruder access. It involves modifying the source address of a packet for a trusted source's address. A SYN attack is when an attacker floods a system with connection requests but does not respond when the target system replies to those requests. A smurf attack occurs when an attacker sends a spoofed (IP spoofing) PING (ICMP ECHO) packet to the broadcast address of a large network (the bounce site). The modified packet containing the address of the target system, all devices on its local network respond with a ICMP REPLY to the target system, which is then saturated with those replies.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 77).
NEW QUESTION 8
Which of the following describes a technique in which a number of processor units are employed in a single computer system to increase the performance of the system in its application environment above the performance of a single processor of the same kind?
- A. Multitasking
- B. Multiprogramming
- C. Pipelining
- D. Multiprocessing
Answer: D
Explanation:
Multiprocessing is an organizational technique in which a number of processor units are employed in a single computer system to increase the performance of the system in its application environment above the performance of a single processor of the same kind. In order to cooperate on a single application or class of applications, the processors share a common resource. Usually this resource is primary memory, and the multiprocessor is called a primary memory multiprocessor. A system in which each processor has a private (local) main memory and shares secondary (global) memory with the others is a secondary memory multiprocessor, sometimes called a multicomputer system because of the looser coupling between processors. The more common multiprocessor systems incorporate only processors of the same type and performance and thus are called homogeneous multiprocessors; however, heterogeneous multiprocessors are also employed. A special case is the attached processor, in which a second processor module is attached to a first processor in a closely coupled fashion so that the first can perform input/output and operating system functions, enabling the attached processor to concentrate on the application workload.
The following were incorrect answers:
Multiprogramming: The interleaved execution of two or more programs by a computer, in which the central processing unit executes a few instructions from each program in succession.
Multitasking: The concurrent operation by one central processing unit of two or more processes.
Pipelining: A procedure for processing instructions in a computer program more rapidly, in which each instruction is divided into numerous small stages, and a population of instructions are in various stages at any given time. One instruction does not have to wait for the previous one to complete all of the stages before it gets into the pipeline. It would be similiar to an assembly chain in the real world.
References:
TIPTON, Hal, (ISC)2, Introduction to the CISSP Exam presentation. http://www.answers.com/QUESTION NO: /multiprocessing?cat=technology
http://www.answers.com/multitasking?cat=biz-fin http://www.answers.com/pipelining?cat=technology
NEW QUESTION 9
Which of the following statements pertaining to key management is incorrect?
- A. The more a key is used, the shorter its lifetime should be.
- B. When not using the full keyspace, the key should be extremely random.
- C. Keys should be backed up or escrowed in case of emergencies.
- D. A key's lifetime should correspond with the sensitivity of the data it is protecting.
Answer: B
Explanation:
A key should always be using the full spectrum of the keyspace and be extremely random. Other statements are correct.
Source: WALLHOFF, John, CBK#5 Cryptography (CISSP Study Guide), April 2002 (page 6).
NEW QUESTION 10
A code, as is pertains to cryptography:
- A. Is a generic term for encryption.
- B. Is specific to substitution ciphers.
- C. Deals with linguistic units.
- D. Is specific to transposition ciphers.
Answer: C
Explanation:
Historically, a code refers to a cryptosystem that deals with linguistic units: words, phrases, sentences, and so forth. Codes are only useful for specialized circumstances where the message to transmit has an already defined equivalent ciphertext word.
Source: DUPUIS, Cl?ment, CISSP Open Study Guide on domain 5, cryptography, April 1999.
NEW QUESTION 11
What type of cable is used with 100Base-TX Fast Ethernet?
- A. Fiber-optic cable
- B. Category 3 or 4 unshielded twisted-pair (UTP).
- C. Category 5 unshielded twisted-pair (UTP).
- D. RG-58 cable.
Answer: C
Explanation:
This is the type of cabling recommended for 100Base-TX networks.
Fiber-optic cable is incorrect. Incorrect media type for 100Base-TX -- 100Base-FX would denote fiber optic cabling.
"Category 3 or 4 unshielded twisted-pair (UTP)" is incorrect. These types are not recommended for 100Mbps operation.
RG-58 cable is incorrect. Incorrect media type for 100Base-TX. References
CBK, p. 428
AIO3, p. 455
NEW QUESTION 12
How can an individual/person best be identified or authenticated to prevent local masquarading attacks?
- A. UserId and password
- B. Smart card and PIN code
- C. Two-factor authentication
- D. Biometrics
Answer: D
Explanation:
The only way to be truly positive in authenticating identity for access is to base the authentication on the physical attributes of the persons themselves (i.e., biometric
identification). Physical attributes cannot be shared, borrowed, or duplicated. They ensure that you do identify the person, however they are not perfect and they would have to be supplemented by another factor.
Some people are getting thrown off by the term Masquarade. In general, a masquerade is a disguise. In terms of communications security issues, a masquerade is a type of attack where the attacker pretends to be an authorized user of a system in order to gain access to it or to gain greater privileges than they are authorized for. A masquerade may be attempted through the use of stolen logon IDs and passwords, through finding security gaps in programs, or through bypassing the authentication mechanism. Spoofing is another term used to describe this type of attack as well.
A UserId only provides for identification.
A password is a weak authentication mechanism since passwords can be disclosed, shared, written down, and more.
A smart card can be stolen and its corresponding PIN code can be guessed by an intruder. A smartcard can be borrowed by a friend of yours and you would have no clue as to who is really logging in using that smart card.
Any form of two-factor authentication not involving biometrics cannot be as reliable as a biometric system to identify the person.
Biometric identifying verification systems control people. If the person with the correct hand, eye, face, signature, or voice is not present, the identification and verification cannot take place and the desired action (i.e., portal passage, data, or resource access) does not occur.
As has been demonstrated many times, adversaries and criminals obtain and successfully use access cards, even those that require the addition of a PIN. This is because these systems control only pieces of plastic (and sometimes information), rather than people. Real asset and resource protection can only be accomplished by people, not cards and information, because unauthorized persons can (and do) obtain the cards and information.
Further, life-cycle costs are significantly reduced because no card or PIN administration system or personnel are required. The authorized person does not lose physical characteristics (i.e., hands, face, eyes, signature, or voice), but cards and PINs are continuously lost, stolen, or forgotten. This is why card access systems require systems and people to administer, control, record, and issue (new) cards and PINs. Moreover, the cards are an expensive and recurring cost.
NOTE FROM CLEMENT:
This question has been generating lots of interest. The keyword in the question is: Individual (the person) and also the authenticated portion as well.
I totally agree with you that Two Factors or Strong Authentication would be the strongest means of authentication. However the question is not asking what is the strongest mean of authentication, it is asking what is the best way to identify the user (individual) behind the technology. When answering questions do not make assumptions to facts not presented in the question or answers.
Nothing can beat Biometrics in such case. You cannot lend your fingerprint and pin to someone else, you cannot borrow one of my eye balls to defeat the Iris or Retina scan. This is why it is the best method to authenticate the user.
I think the reference is playing with semantics and that makes it a bit confusing. I have improved the question to make it a lot clearer and I have also improve the explanations attached with the question.
The reference mentioned above refers to authenticating the identity for access. So the distinction is being made that there is identity and there is authentication. In the case of physical security the enrollment process is where the identity of the user would be validated and then the biometrics features provided by the user would authenticate the user on a one to one matching basis (for authentication) with the reference contained in the database of biometrics templates. In the case of system access, the user might have to provide a username, a pin, a passphrase, a smart card, and then provide his biometric attributes.
Biometric can also be used for Identification purpose where you do a one to many match. You take a facial scan of someone within an airport and you attempt to match it with a large database of known criminal and terrorists. This is how you could use biometric for Identification.
There are always THREE means of authentication, they are: Something you know (Type 1)
Something you have (Type 2)
Something you are (Type 3)
Reference(s) used for this question:
TIPTON, Harold F. & KRAUSE, Micki, Information Security Management Handbook, 4th edition (volume 1) , 2000, CRC Press, Chapter 1, Biometric Identification (page 7).
and
Search Security at http://searchsecurity.techtarget.com/definition/masquerade
NEW QUESTION 13
Java is not:
- A. Object-oriented.
- B. Distributed.
- C. Architecture Specific.
- D. Multithreaded.
Answer: C
Explanation:
JAVA was developed so that the same program could be executed on multiple hardware and operating system platforms, it is not Architecture Specific.
The following answers are incorrect:
Object-oriented. Is not correct because JAVA is object-oriented. It should use the object- oriented programming methodology.
Distributed. Is incorrect because JAVA was developed to be able to be distrubuted, run on multiple computer systems over a network.
Multithreaded. Is incorrect because JAVA is multi-threaded that is calls to subroutines as is the case with object-oriented programming.
A virus is a program that can replicate itself on a system but not necessarily spread itself by network connections.
NEW QUESTION 14
In what type of attack does an attacker try, from several encrypted messages, to figure out the key used in the encryption process?
- A. Known-plaintext attack
- B. Ciphertext-only attack
- C. Chosen-Ciphertext attack
- D. Plaintext-only attack
Answer: B
Explanation:
In a ciphertext-only attack, the attacker has the ciphertext of several messages encrypted with the same encryption algorithm. Its goal is to discover the plaintext of the messages by figuring out the key used in the encryption process. In a known-plaintext attack, the attacker has the plaintext and the ciphertext of one or more messages. In a chosen-ciphertext attack, the attacker can chose the ciphertext to be decrypted and has access to the resulting plaintext.
Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw- Hill/Osborne, 2002, Chapter 8: Cryptography (page 578).
NEW QUESTION 15
Which of the following steps is NOT one of the eight detailed steps of a Business Impact Assessment (BIA):
- A. Notifying senior management of the start of the assessment.
- B. Creating data gathering techniques.
- C. Identifying critical business functions.
- D. Calculating the risk for each different business function.
Answer: A
Explanation:
Source: HARRIS, S., CISSP All- In-One Exam Guide, 3rd. Edition, 2005, Chapter 9, Page 701.
There have been much discussion about the steps of the BIA and I struggled with this before deciding to scrape the question about "the four steps," and re-write the question using the AIO for a reference. This question should be easy.... if you know all eight steps.
The eight detailed and granular steps of the BIA are:
1. Select Individuals to interview for the data gathering.
2. Create data gathering techniques (surveys, questionnaires, qualitative and quantitative approaches).
3. Identify the company's critical business functions.
4. Identify the resources that these functions depend upon.
5. Calculate how long these functions can survive without these resources.
6. Identify vulnerabilities and the threats to these functions.
7. Calculate risk for each of the different business functions.
8. Document findings and report them to management. Shon goes on to cover each step in Chapter 9.
NEW QUESTION 16
Which of the following is most affected by denial-of-service (DOS) attacks?
- A. Confidentiality
- B. Integrity
- C. Accountability
- D. Availability
Answer: D
Explanation:
Denial of service attacks obviously affect availability of targeted systems. Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 61).
NEW QUESTION 17
Secure Shell (SSH) is a strong method of performing:
- A. client authentication
- B. server authentication
- C. host authentication
- D. guest authentication
Answer: A
Explanation:
Secure shell (SSH) was designed as an alternative to some of the insecure protocols and allows users to securely access resources on remote computers over an encrypted tunnel. The Secure Shell Protocol (SSH) is a protocol for secure remote login and other secure network services over an insecure network. The SSH authentication protocol runs on top of the SSH transport layer protocol and provides a single authenticated tunnel for the SSH connection protocol.
SSH??s services include remote log-on, file transfer, and command execution. It also supports port forwarding, which redirects other protocols through an encrypted SSH tunnel. Many users protect less secure traffic of protocols, such as X Windows and VNC (virtual network computing), by forwarding them through a SSH tunnel.
The SSH tunnel protects the integrity of communication, preventing session hijacking and
other man-in-the-middle attacks. Another advantage of SSH over its predecessors is that it supports strong authentication. There are several alternatives for SSH clients to authenticate to a SSH server, including passwords and digital certificates.
Keep in mind that authenticating with a password is still a significant improvement over the other protocols because the password is transmitted encrypted.
There are two incompatible versions of the protocol, SSH-1 and SSH-2, though many servers support both. SSH-2 has improved integrity checks (SSH-1 is vulnerable to an insertion attack due to weak CRC-32 integrity checking) and supports local extensions and additional types of digital certificates such as Open PGP. SSH was originally designed for UNIX, but there are now implementations for other operating systems, including Windows, Macintosh, and OpenVMS.
Is SSH 3.0 the same as SSH3?
The short answer is: NO SSH 3.0 refers to version 3 of SSH Communications SSH2 protocol implementation and it could also refer to OpenSSH Version 3.0 of its SSH2 software. The "3" refers to the software release version not the protocol version. As of this writing (July 2013), there is no SSH3 protocol.
"Server authentication" is incorrect. Though many SSH clients allow pre-caching of server/host keys, this is a minimal form of server/host authentication.
"Host authentication" is incorrect. Though many SSH clients allow pre-caching of server/host keys, this is a minimal form of server/host authentication.
"Guest authentication" is incorrect. The general idea of "guest" is that it is unauthenticated access.
Reference(s) used for this question: http://www.ietf.org/rfc/rfc4252.txt
Hernandez CISSP, Steven (2012-12-21). Official (ISC)2 Guide to the CISSP CBK, Third
Edition ((ISC)2 Press) (Kindle Locations 7080-7088). Auerbach Publications. Kindle Edition.
NEW QUESTION 18
Which xDSL flavour delivers both downstream and upstream speeds of 1.544 Mbps over two copper twisted pairs?
- A. HDSL
- B. SDSL
- C. ADSL
- D. VDSL
Answer: A
Explanation:
High-rate Digital Subscriber Line (HDSL) delivers 1.544 Mbps of bandwidth each way over two copper twisted pairs. SDSL also delivers 1.544 Mbps but over a single copper twisted pair. ADSL and VDSL offer a higher bandwidth downstream than upstream. Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 115).
NEW QUESTION 19
Which of the following exemplifies proper separation of duties?
- A. Operators are not permitted modify the system time.
- B. Programmers are permitted to use the system console.
- C. Console operators are permitted to mount tapes and disks.
- D. Tape operators are permitted to use the system console.
Answer: A
Explanation:
This is an example of Separation of Duties because operators are prevented from modifying the system time which could lead to fraud. Tasks of this nature should be performed by they system administrators.
AIO defines Separation of Duties as a security principle that splits up a critical task among two or more individuals to ensure that one person cannot complete a risky task by himself.
The following answers are incorrect:
Programmers are permitted to use the system console. Is incorrect because programmers should not be permitted to use the system console, this task should be performed by operators. Allowing programmers access to the system console could allow fraud to occur so this is not an example of Separation of Duties..
Console operators are permitted to mount tapes and disks. Is incorrect because operators should be able to mount tapes and disks so this is not an example of Separation of Duties.
Tape operators are permitted to use the system console. Is incorrect because operators should be able to use the system console so this is not an example of Separation of Duties.
References:
OIG CBK Access Control (page 98 - 101) AIOv3 Access Control (page 182)
NEW QUESTION 20
Which of the following would assist the most in Host Based intrusion detection?
- A. audit trails.
- B. access control lists.
- C. security clearances
- D. host-based authentication
Answer: A
Explanation:
To assist in Intrusion Detection you would review audit logs for access violations.
The following answers are incorrect:
access control lists. This is incorrect because access control lists determine who has access to what but do not detect intrusions.
security clearances. This is incorrect because security clearances determine who has access to what but do not detect intrusions.
host-based authentication. This is incorrect because host-based authentication determine who have been authenticated to the system but do not dectect intrusions.
NEW QUESTION 21
......
P.S. Easily pass SSCP Exam with 1074 Q&As Downloadfreepdf.net Dumps & pdf Version, Welcome to Download the Newest Downloadfreepdf.net SSCP Dumps: https://www.downloadfreepdf.net/SSCP-pdf-download.html (1074 New Questions)
- The Secret Of ISC2 HCISPP Study Guide
- High value CISSP-ISSEP Exam Questions and Answers 2021
- What Downloadable SSCP Test Question Is
- [2021-New] ISC2 CISSP Dumps With Update Exam Questions (131-140)
- Validated CISSP-ISSEP Free Practice Questions 2021
- [2021-New] ISC2 CISSP Dumps With Update Exam Questions (151-160)
- ISC2 CISSP-ISSEP Exam Dumps 2021
- [2021-New] ISC2 CISSP Dumps With Update Exam Questions (101-110)
- [2021-New] ISC2 CISSP Dumps With Update Exam Questions (91-100)
- [2021-New] ISC2 CISSP Dumps With Update Exam Questions (151-160)

