1Z0-821 Exam Questions - Online Test
1Z0-821 Premium VCE File

150 Lectures, 20 Hours

It is more faster and easier to pass the by using . Immediate access to the and find the same core area with professionally verified answers, then PASS your exam with a high score now.
Free demo questions for Oracle 1Z0-821 Exam Dumps Below:
NEW QUESTION 1
To help with your troubleshooting, you need to determine the version of the OBP. Which two commands will provide you with this information?
- A. printenv
- B. banner
- C. .version
- D. set-env
- E. show-devs
- F. value version
Answer: BC
Explanation: B: banner
Displays power-on banner.
The PROM displays the system banner. The following example shows a SPARCstation 2 banner. The banner for your SPARC system may be different.
SPARCstation 2, Type 4 Keyboard
ROM Rev. 2.0, 16MB memory installed, Serial # 289 Ethernet address 8:0:20:d:e2:7b, Host ID: 55000121 C: .version
Displays version and date of the boot PROM.
Note: OBP-OpenBootProm is a firmware which is placed on the sun machine's prom chip. It is a os independent user interface to deal with the sun machine's hardware components. The user interface provides one or more commands to display system information.
NEW QUESTION 2
You are installing the Solaris 11 OE by using the Interactive Text Installer. You have selected the option to automatically configure the primary network controller. Which three items will automatically be configured as a result of this selection?
- A. The IP address.
- B. The name service.
- C. The time zone.
- D. A default user account.
- E. The terminal type.
- F. The root password.
- G. The host name.
Answer: ABC
Explanation: IP address and name service (such as a DNS server) are provided by the DHCP server.
NEW QUESTION 3
This iron is displayed on the desktop of a laptop computer, which is running Oracle Solaris 11.
Which two statements describe the Information conveyed by this Icon?
- A. NWAM is disabled.
- B. NWAM is automatically configuring the network.
- C. The wireless network card is manually configured and operational.
- D. The wireless network card is manually configured but not operational.
- E. The wireless network card is automatically configured and operational.
- F. The wireless network card is automatically configured but not operational.
Answer: BC
Explanation: B: The Network Status notification icon is only displayed on the desktop if you are using NWAM to automatically configure your network.
C: All online (Wireless)
Indicates all manually enabled connections in the enabled network profile are online and that the required number of connections in the enabled profile group (if such a group exists) are online. The required number is the same as those described for the All online (Wired) status.
Note that at least one online connection is wireless.
NEW QUESTION 4
What determines which bits in an IP address represent the subnet, and which represent the host?
- A. Subnet
- B. unicast
- C. netmask
- D. multicast
- E. broadcast
Answer: C
Explanation: A subnetwork, or subnet, is a logically visible subdivision of an IP network. The practice of dividing a network into two or more networks is called subnetting.
The routing prefix of an address is written in a form identical to that of the address itself. This is called the network mask, or netmask, of the address. For example, a specification of the most-significant 18 bits of an IPv4 address, 11111111.11111111.11000000.00000000, is written as 255.255.192.0.
NEW QUESTION 5
Which three options accurately describe Oracle Solaris 11 zones?
- A. can be NFS servers
- B. are whole root type only
- C. cannot have their own time zone setting
- D. can execute z£s and zpool commands (from a non-global zone)
- E. are virtualized operating system environments, each with its own dedicated OS and kernel
- F. are virtualized operating system environments, created with a single instance of the OS shared kernel
Answer: ADF
Explanation: A: Zones can use Oracle Solaris 11 products and features such as the following: Oracle Solaris ZFS encryption
Network virtualization and QoS CIFS and NFS
C: Non-global zones cannot modify the system clock by default, but each zone can have a separate time zone setting.
F (not E): The Oracle Solaris Zones partitioning technology is used to virtualize operating system services and provide an isolated and secure environment for running applications. A zone is a virtualized operating system environment created within a single instance of the Oracle Solaris operating system.
NEW QUESTION 6
Which four can the SMF notification framework be configured to monitor and report?
- A. all service transition states
- B. service dependencies that have stopped or faulted
- C. service configuration modifications
- D. legacy services that have not started
- E. services that have been disabled
- F. service fault management events
- G. processes that have been killed
Answer: AEFG
Explanation: Note 1: State Transition Sets are defined as: to<state>
Set of all transitions that have <state> as the final state of the transition.
form-<state>
Set of all transitions that have <state> as the initial state of the transition.
<state>
Set of all transitions that have <state> as the initial state of the transitional. Set of all transitions. (A)
Valid values of state are maintenance, offline (G), disabled (E), online and degraded. An example of a transitions set definition: maintenance, from-online, to-degraded.
F: In this context, events is a comma separated list of SMF state transition sets or a comma separated list of FMA (Fault Management Architecture) event classes. events cannot have a mix of SMF state transition sets and FMA event classes. For convenience, the tags problem- {diagnosed, updated, repaired, resolved} describe the lifecycle of a problem diagnosed by the FMA subsystem - from initial diagnosis to interim updates and finally problem closure.
Note 2:
SMF allows notification by using SNMP or SMTP of state transitions. It publishes Information Events for state transitions which are consumed by notification daemons like snmp-notify(1M) and smtp-notify(1M). SMF state transitions of disabled services do not generate notifications unless the final state for the transition is disabled and there exist notification parameters for that transition. Notification is not be generated for transitions that have the same initial and final state.
NEW QUESTION 7
Review the information taken from your server: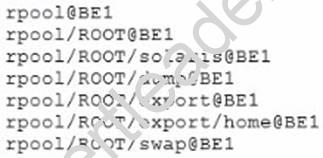
Which option describes the command used to create these snapshots of the root file system?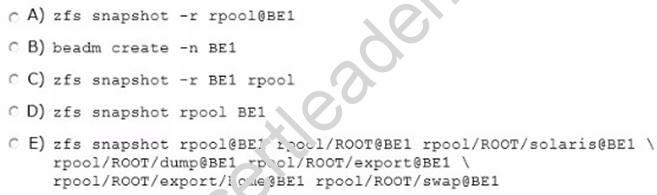
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: A
Explanation: zfs snapshot [-r] [-o property=value] ... filesystem@snapname|volume@snapname Creates a snapshot with the given name. All previous modifications by successful system calls to the file system are part of the snapshot. See the “Snapshots” section for details.
-r
Recursively create snapshots of all descendent datasets. Snapshots are taken atomically, so that all recursive snapshots correspond to the same moment in time.
NEW QUESTION 8
You are asked to troubleshoot networking issues on an unfamiliar system. Select the correct command to display what network devices are installed.
- A. ifconfig -a
- B. dladm show-dev
- C. dladm show-phys
- D. dladm show-ether
- E. netadm show-dev
- F. netadm show-ether
Answer: C
NEW QUESTION 9
Before booting testzone, a non-global zone, you want to connect to the zone's console so that you can watch the boot process.
Choose the command used xo connect to testzone's console.
- A. zoneadm – C testzone
- B. zoneadm – console testzone
- C. zlogin – z testzone console
- D. zlogin – z testzone – C
- E. zlogin – C testzone
- F. zoneadm – z testzone – C
Answer: E
NEW QUESTION 10
You have a process called bigscript, and you need to know the PID number for this process.
Which command will provide that information?
- A. pkill bigscript
- B. ps bigscript
- C. pgrep bigscript
- D. prstat bigscript
Answer: C
Explanation: Pgrep takes a process name and return a PID.
Note: pgrep looks through the currently running processes and lists the process IDs which matches the selection criteria to stdout. All the criteria have to match. For example, pgrep - u root sshd will only list the processes called sshd AND owned by root.
Incorrec answers:
ps bigscript: You can’t pass a name to ps, it interprets it as arguments.
NEW QUESTION 11
You need to install the solaris-desktop group package. Which command would you use to list the set of packages included in that software group?
- A. pkg search
- B. pkg info
- C. pkginfo
- D. pkg contents
Answer: A
Explanation: Use the pkg search command to search for packages whose data matches the specified pattern.
Like the pkg contents command, the pkg search command examines the contents of packages. While the pkg contents command returns the contents, the pkg search
command returns the names of packages that match the query.
NEW QUESTION 12
User jack logs in to host solar in and issues the following command:
jack@solaris:-$ ls .ssh
id_dsa id_dsa.pub id_rsa id_rsa.pub known_hosts authorized_keys Which two are true?
- A. The id_rsa file contains the private key for rhosts-based host authentication.
- B. The id_dsa.pub file contains the Digital Signature Algorithm public key for the user jack.
- C. The id_rsa.pub file contains the Rivest Shamir Adelman public key for the host solaris.
- D. The authorized_keys file contains the private keys of remote users authorized to access jack’s account on solaris.
- E. The known_hosts file contains the verified public keys of remote hosts known to be trusted.
Answer: AE
Explanation: A: You will see two files starting with id_rsa. id_rsa is the private key and id_rsa.pub is public key.
E: The .ssh/known_hosts file
In order to use public-key secure connection with other hosts (ssh, scp, sftp) there is a special directory, ~/.ssh/, where passphrases and public keys are stored. Normally you wouldn't need to know the gory details, but from time to time a host will change its public key and then you have difficulty using ssh or scp with that host, and have to edit a file named known_hosts.
If you try to ssh to another computer, but get an error message that warns about a changed or incorrect public key, then it is probably just a case of that host changing its public key. (It is possible, though usually not the case, that malicious hacking is involved.) Unless you actually suspect hacker involvement, you can edit the file ~/.ssh/known_hosts using your usual text editor (vi, emacs, nedit, or pico) and delete any line with the name of that host.
Then when you try to ssh that host again, it will be like the first time ever; ssh will ask you if you want to accept a new public key, you type the whole word yes, and everything will proceed normally from there.
Here is what a typical ~/.ssh/known_hosts file might contain. Note that newton is represented on two different lines:
newton 1024 35
153438062610297067329638677441205712613292203533062535600064224677647442
245028855505387934431717435134842994423656065076260604296084868001730665
553662299156116414854701274715680961503198280525759778667306417179500370
189017139564144825610347509023078143132936185076849630461827976942220442
313116255293297021841
ucsub 1024 37
132170811640421742212085598383135714069016332111955003414250071326834884
018721183646445780180633494496866895830879394309011412231102757022090299
732775466435482517698989962531081214859205054227533597152962802400251809
883548442498002326460312850336779152617243800769119880843882425555806081
435017335194477605333
simpson 1024 41
840896920592494584403453622735282634536002054701576247765078766974814128
393752943151071629834843909016027026612791643752972116459602750267266908
365259665072736159491719667576217171370458928680504368847255632477925660
234893185547218857655484574619075125368470792976275806263534208879722192
77539015703446529603
newton, 128.138.249.8 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAIEA0d7Aoure0toNJ+YMYi61QP2ka8m5x5ZQlT7obP8C
K3eropfqsMPPY6uiyIh9vpiFX2r1LHcbx139+vG6HOtVvuS8+IfMDtawm3WQvRuOopz3vVy 5GtMwtaOgehsXoT930Ryev1bH5myPtWKlipITsOd2sX9k3tvjrmme4KCGGss=
NEW QUESTION 13
Your server has one zone named dbzone (hat has been configured, but not yet installed). Which command would you use to view all the options that were used to configure this zone?
- A. zoneadm list –icv dbzone
- B. zones tat –c summary dbzone
- C. zonecfg –z dbzone info
- D. zonecfg –icv dbzone info
Answer: C
Explanation: zonecfg info
Display information about the current configuration. If resource-type is specified, displays only information about resources of the relevant type. If any property-name value pairs are specified, displays only information about resources meeting the given criteria. In the resource scope, any arguments are ignored, and info displays information about the resource which is currently being added or modified.
Note: zonecfg –z
zonename. Specify the name of a zone. Zone names are case sensitive. Zone names must begin with an alphanumeric character and can contain alphanumeric characters, the underscore (_) the hyphen (-), and the dot (.). The name global and all names beginning with SUNW are reserved and cannot be used.
Incorrect Answer
A: The zoneadm utility is used to administer system zones. A zone is an application container that is maintained by the operating system runtime.
list option:
Display the name of the current zones, or the specified zone if indicated. B: No such command.
D: no such options zonecfg –icv
NEW QUESTION 14
A datalink can best be described as .
- A. a driver for a Network Interface Card
- B. the software connecting the Internet Layer and the Physical Layer
- C. a device that provides Classless Inter-Domain Routing
- D. a logical object used for IP Multipathing
Answer: D
Explanation: The command dladm is used to configure data-link interfaces in Sun Solaris. A configured data-link is represented in the system as interface that can be used for TCP/IP. Each data- link relies on either a single network device or an link aggregation device to send & recieve packets.
Network interfaces provide the connection between the system and the network. These interfaces are configured over data links, which in turn correspond to instances of hardware devices in the system.
In the current model of the network stack, interfaces and links on the software layer build on the devices in the hardware layer. More specifically, a hardware device instance in the
hardware layer has a corresponding link on the data-link layer and a configured interface on the interface layer. This one-to-one relationship among the network device, its data link, and the IP interface is illustrated in the figure that follows.
Network Stack Showing Network Devices, Links, and Interfaces: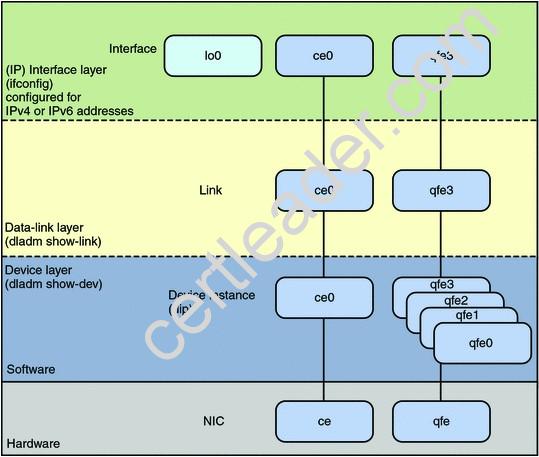
NEW QUESTION 15
Which network protocol is responsible for routing packets from one network to another?
- A. TCP
- B. UDP
- C. IP
- D. ICMP
- E. Ethernet
Answer: C
Explanation: The Internet Protocol (IP) is the principal communications protocol in the Internet protocol suite for relaying datagrams across network boundaries. Its routing function enables internetworking, and essentially establishes the Internet.
NEW QUESTION 16
You are attempting to edit your crontab file in the bash shell. Instead of getting your usual vi interface, you are presented with an unfamiliar interface. In order to have your editor of choice-vi- what command must you type after exiting the unfamiliar editor?
- A. EDITOR=vi
- B. crontab=vi
- C. crontab – e vi
- D. env
Answer: A
Explanation: Set the EDITOR variable to vi.
Commands like `crontab -e` will use ed per default. If you'd like to use some better editor (like vi) you can use the environment variable EDITOR:
# EDITOR=vi; crontab –e will open the users crontab in vi. Of course you can set this variable permanently.
Incorrect answers
C: -e Edits a copy of the current user's crontab file, or creates an empty file to edit if crontab does not exist. When editing is complete, the file is installed as the user's crontab file. If a username is given, the specified user's crontab file is edited, rather than the current user's crontab file; this can only be done by a user with the solaris.jobs.admin authorization. The environment variable EDITOR determines which editor is invoked with the -e option. The default editor is ed(1). All crontab jobs should be submitted using crontab. Do not add jobs by just editing the crontab file, because cron is not aware of changes made this way.
P.S. 2passeasy now are offering 100% pass ensure 1Z0-821 dumps! All 1Z0-821 exam questions have been updated with correct answers: https://www.2passeasy.com/dumps/1Z0-821/ (243 New Questions)
- [2021-New] Oracle 1Z0-062 Dumps With Update Exam Questions (71-80)
- A Review Of High Quality 1z0-1023 Exam Answers
- Refresh 1Z0-053 Exams For Oracle Database 11g: Administration II Certification
- Update Java SE 11 Developer 1Z0-819 Testing Software
- [2021-New] Oracle 1z0-808 Dumps With Update Exam Questions (91-100)
- [2021-New] Oracle 1z0-047 Dumps With Update Exam Questions (71-80)
- [2021-New] Oracle 1Z0-897 Dumps With Update Exam Questions (21-30)
- Precise 1Z0-435 Braindumps 2021
- Breathing 1Z0-067 Exam Questions and Answers 2021
- [2021-New] Oracle 1Z0-052 Dumps With Update Exam Questions (91-100)

