NSE6_FNC-8.5 Exam Questions - Online Test
NSE6_FNC-8.5 Premium VCE File

150 Lectures, 20 Hours

100% Guarantee of NSE6_FNC-8.5 exam price materials and study guide for Fortinet certification for candidates, Real Success Guaranteed with Updated NSE6_FNC-8.5 pdf dumps vce Materials. 100% PASS Fortinet NSE 6 - FortiNAC 8.5 exam Today!
Check NSE6_FNC-8.5 free dumps before getting the full version:
NEW QUESTION 1
What would happen if a port was placed in both the Forced Registration and the Forced Remediation port groups?
- A. Only rogue hosts would be impacted.
- B. Both enforcement groups cannot contain the same port.
- C. Only al-risk hosts would be impacted.
- D. Both types of enforcement would be applied.
Answer: A
NEW QUESTION 2
Which two of the following are required for endpoint compliance monitors? (Choose two.)
- A. Persistent agent
- B. Logged on user
- C. Security rule
- D. Custom scan
Answer: CD
NEW QUESTION 3
By default, if more than 20 hosts are seen connected on a single port simultaneously, what will happen to the port?
- A. The port is switched into the Dead-End VLAN.
- B. The port becomes a threshold uplink.
- C. The port is disabled.
- D. The port is added to the Forced Registration group.
Answer: A
NEW QUESTION 4
With enforcement for network access policies and at-risk hosts enabled, what will happen if a host matches a network access policy and has a state of "at risk"?
- A. The host is provisioned based on the default access defined by the point of connection.
- B. The host is provisioned based on the network access policy.
- C. The host is isolated.
- D. The host is administratively disabled.
Answer: D
NEW QUESTION 5
Where do you look to determine when and why the FortiNAC made an automated network access change?
- A. The Event view
- B. The Port Changes view
- C. The Connections view
- D. The Admin Auditing view
Answer: A
NEW QUESTION 6
In a wireless integration, how does FortiNAC obtain connecting MAC address information?
- A. MAC notification traps
- B. Link traps
- C. End station traffic monitoring
- D. RADIUS
Answer: A
NEW QUESTION 7
Refer to the exhibit.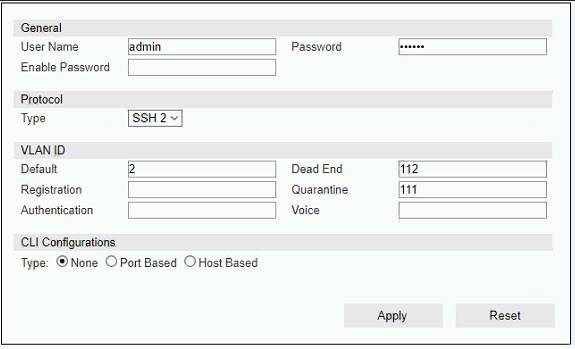
If you are forcing the registration of unknown (rogue) hosts, and an unknown (rogue) host connects to a port on the switch, what will occur?
- A. No VLAN change is performed
- B. The host is moved to a default isolation VLAN.
- C. The host is disabled.
- D. The host is moved to VLAN 111.
Answer: A
NEW QUESTION 8
Which command line shell and scripting language does FortiNAC use for WinRM?
- A. Linux
- B. Bash
- C. DOS
- D. Powershell
Answer: D
NEW QUESTION 9
How are logical networks assigned to endpoints?
- A. Through device profiling rules
- B. Through network access policies
- C. Through Layer 3 polling configurations
- D. Through FortiGate IPv4 policies
Answer: D
NEW QUESTION 10
......
100% Valid and Newest Version NSE6_FNC-8.5 Questions & Answers shared by Dumps-hub.com, Get Full Dumps HERE: https://www.dumps-hub.com/NSE6_FNC-8.5-dumps.html (New 30 Q&As)
- What 100% Correct NSE5_FCT-7.0 Study Guides Is
- [2021-New] Fortinet NSE5 Dumps With Update Exam Questions (11-20)
- Fortinet NSE4_FGT-6.2 Software 2021
- All About Free NSE4_FGT-7.0 Free Exam Questions
- [2021-New] Fortinet NSE4-5.4 Dumps With Update Exam Questions (1-10)
- [2021-New] Fortinet NSE4 Dumps With Update Exam Questions (11-20)
- [2021-New] Fortinet NSE5 Dumps With Update Exam Questions (131-140)
- [2021-New] Fortinet NSE4 Dumps With Update Exam Questions (61-66)
- A Review Of Guaranteed NSE6_FWB-6.0 Study Guides
- Up To The Immediate Present NSE4_FGT-6.4 Exam For Fortinet NSE 4 - FortiOS 6.4 Certification

