NSE7_LED-7.0 Exam Questions - Online Test
NSE7_LED-7.0 Premium VCE File

150 Lectures, 20 Hours

Want to know Actualtests NSE7_LED-7.0 Exam practice test features? Want to lear more about Fortinet Fortinet NSE 7 - LAN Edge 7.0 certification experience? Study Downloadable Fortinet NSE7_LED-7.0 answers to Renewal NSE7_LED-7.0 questions at Actualtests. Gat a success with an absolute guarantee to pass Fortinet NSE7_LED-7.0 (Fortinet NSE 7 - LAN Edge 7.0) test on your first attempt.
Check NSE7_LED-7.0 free dumps before getting the full version:
NEW QUESTION 1
Refer to the exhibit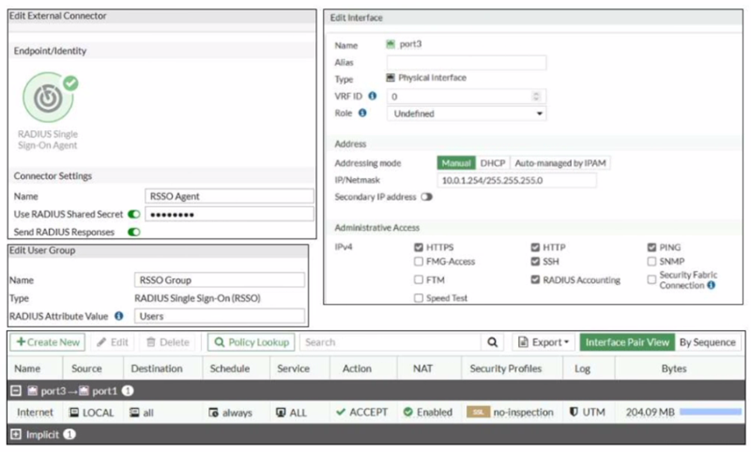
Examine the FortiGate RSSO configuration shown in the exhibit
FortiGate is configured to receive RADIUS accounting messages on port3 to authenticate RSSO users The users are located behind port3 and the internet link is connected to port1 FortiGate is processing incoming RADIUS accounting messages successfully and RSSO users are getting associated with the RSSO Group user group However all the users are able to access the internet, and the administrator wants to restrict internet access to RSSO users only
Which configuration change should the administrator make to fix the problem?
- A. Change the RADIUS Attribute Value selling to match the name of the RADIUS attribute containing the group membership information of the RSSO users
- B. Add RSSO Group to the firewall policy
- C. Enable Security Fabric Connection on port3
- D. Create a second firewall policy from port3 lo port1 and select the target destination subnets
Answer: B
Explanation:
According to the exhibit, the firewall policy from port3 to port1 has no user group specified, which means that it allows all users to access the internet. Therefore, option B is true because adding RSSO Group to the firewall policy will restrict internet access to RSSO users only. Option A is false because changing the RADIUS Attribute Value setting will not affect the firewall policy, but rather the RSSO user group membership. Option C is false because enabling Security Fabric Connection on port3 will not affect the firewall policy, but rather the communication between FortiGate and other Security Fabric devices. Option D is false because creating a second firewall policy from port3 to port1 will not affect the existing firewall policy, but rather create a redundant or conflicting policy.
NEW QUESTION 2
You are setting up an SSID (VAP) to perform RADlUS-authenticated dynamic VLAN allocation Which three RADIUS attributes must be supplied by the RADIUS server to enable successful VLAN
allocation'' (Choose three.)
- A. Tunnel-Private-Group-ID
- B. Tunnel-Pvt-Group-ID
- C. Tunnel-Preference
- D. Tunnel-Type
- E. Tunnel-Medium-Type
Answer: ADE
Explanation:
According to the FortiAP Configuration Guide, "To perform RADIUS-authenticated dynamic VLAN allocation, the RADIUS server must supply the following RADIUS attributes: Tunnel-Private-Group-ID, which specifies the VLAN ID to assign to the user. Tunnel-Type, which specifies the tunneling protocol used for the VLAN. The value must be 13 (VLAN). Tunnel-Medium-Type, which specifies the transport medium used for the VLAN. The value must be 6 (802). Therefore, options A, D, and E are true because they describe the RADIUS attributes that must be supplied by the RADIUS server to enable successful VLAN allocation.
Option B is false because Tunnel-Pvt-Group-ID is not a valid RADIUS attribute name, but rather a typo for Tunnel-Private-Group-ID. Option C is false because Tunnel-Preference is not a required RADIUS attribute for dynamic VLAN allocation, but rather an optional attribute that specifies the priority of the VLAN.
NEW QUESTION 3
Refer to the exhibit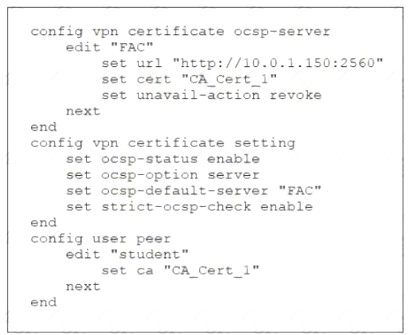
Examine the sections of the configuration shown in the output
What action will FortiGate take when verifying the student certificate through OCSP?
- A. Reject the student certificate if the OCSP server replies that the student certificate status is unknown
- B. Not verify the OCSP server certificate
- C. Use the OCSP URL included in the student certificate to verify the student certificate
- D. Consider the student certificate status as valid if the OCSP server is unreachable
Answer: C
Explanation:
According to the exhibit, the FortiGate configuration has ocsp-status enabled and ocsp-option set to certificate.
This means that FortiGate will use OCSP to verify the revocation status of certificates presented by
clients. According to the FortiGate Administration Guide2, “If you select certificate, FortiGate uses an OCSP URL included in a certificate to verify that certificate.” Therefore, option C is true because it describes what action FortiGate will take when verifying the student certificate through OCSP. Option A is false because FortiGate will not reject the student certificate if the OCSP server replies that the student certificate status is unknown, but rather accept it as valid. Option B is false because FortiGate will verify the OCSPserver certificate by default, unless strict-ocsp-check is disabled. Option D is false because FortiGate will not consider the student certificate status as valid if the OCSP server is unreachable, but rather reject it as invalid.
NEW QUESTION 4
Which CLI command should an administrator use to view the certificate verification process in real time?
- A. diagnose debug application foauthd -1
- B. diagnose debug application radiusd -1
- C. diagnose debug application authd -1
- D. diagnose debug application fnbamd -1
Answer: A
Explanation:
According to the FortiOS CLI Reference Guide, “The diagnose debug application foauthd command enables debugging of certificate verification process in real time.” Therefore, option A is true because it describes the CLI command that an administrator should use to view the certificate verification process in real time. Option B is false because diagnose debug application radiusd -1 enables debugging of RADIUS authentication process, not certificate verification process. Option C is false because diagnose debug application authd -1 enables debugging of authentication daemon process, not certificate verification process. Option D is false because diagnose debug application fnbamd -1 enables debugging of FSSO daemon process, not certificate verification process.
NEW QUESTION 5
Refer to the exhibit.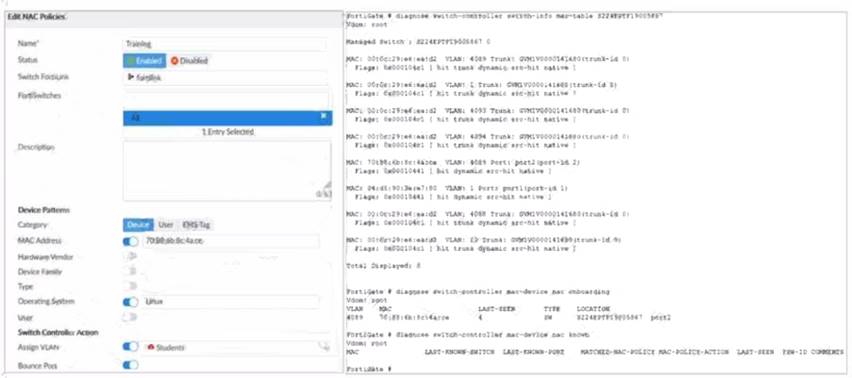
Examine the FortiManager configuration and FortiGate CLI output shown in the exhibit
An administrator is testing the NAC feature The test device is connected to a managed FortiSwitch device
{S224EPTF19"53€7)onpOrt2
After applying the NAC policy on port2 and generating traffic on the test device the test device is not matching the NAC policy therefore the test device remains m the onboarding VLAN
Based on the information shown in the exhibit which two scenarios are likely to cause this issue? (Choose two.)
- A. Management communication between FortiGate and FortiSwitch is down
- B. The MAC address configured on the NAC policy is incorrect
- C. The device operating system detected by FortiGate is not Linux
- D. Device detection is not enabled on VLAN 4089
Answer: AB
Explanation:
According to the FortiManager configuration, the NAC policy is set to match devices with the MAC address of 00:0c:29:6a:2b:3c and the operating system of Linux.However, according to the FortiGate CLI output, the test device has a different MAC address of 00:0c:29:6a:2b:3d. Therefore, option B is true. Option A is also true because the FortiSwitch device status is shown as down, which means that the management
communication between FortiGate and FortiSwitch is not working properly. This could prevent the NAC policy from being applied correctly. Option C is false because the device operating system detected by FortiGate is Linux, which matches the NAC policy. Option D is false because device detection is enabled on VLAN 4089, as shown by the command “config switch-controller vlan”.
NEW QUESTION 6
Refer to the exhibit.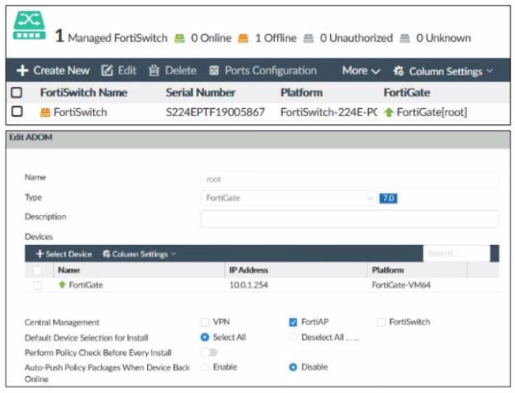
Examine the FortiManager information shown in the exhibit
Which two statements about the FortiManager status are true'' (Choose two)
- A. FortiSwitch manager is working in per-device management mode
- B. FortiSwitch is not authorized
- C. FortiSwitch manager is working in central management mode
- D. FortiSwitch is authorized and offline
Answer: CD
Explanation:
According to the FortiManager Administration Guide, “Central management mode allows you to manage all FortiSwitch devices from a single interface on the FortiManager device.” Therefore, option C is true because the exhibit shows that the FortiSwitch manager is enabled and the FortiSwitch device is managed by the FortiManager device. Option D is also true because the exhibit shows that the FortiSwitch device status is offline, which means that it is not reachable by the FortiManager device, but it is authorized, which means that it has been added to the FortiManager device. Option A is false because per-device management mode allows you to manage each FortiSwitch device individually from its own web-based manager or CLI, which is not the case in the exhibit. Option B is false because the FortiSwitch device is authorized, as explained above.
NEW QUESTION 7
Which two statements about MAC address quarantine by redirect mode are true? (Choose two)
- A. The quarantined device is moved to the quarantine VLAN
- B. The device MACaddress is added to the Quarantined Devices firewall address group
- C. It is the default mode for MAC address quarantine
- D. The quarantined device is kept in the current VLAN
Answer: BD
Explanation:
According to the FortiGate Administration Guide, “MAC address quarantine by redirect mode allows you to quarantine devices by adding their MAC addresses to a firewall address group called Quarantined Devices. The quarantined devices are kept in their current VLANs, but their traffic is redirected to a quarantine portal.” Therefore, options B and D are true because they describe the statements about MAC address quarantine by redirect mode. Option A is false because the quarantined device is not moved to the quarantine VLAN, but rather kept in the current VLAN. Option C is false because redirect mode is not the default mode for MAC address quarantine, but rather an alternative mode that can be enabled by setting mac-quarantine-mode to redirect.
https://docs.fortinet.com/document/fortiap/7.0.0/configuration-guide/734537/radius-authenticated-dynamic-vlan
: https://docs.fortinet.com/document/fortigate/7.0.0/administration-guide/734537/mac-address-quarantine
NEW QUESTION 8
Refer to the exhibit.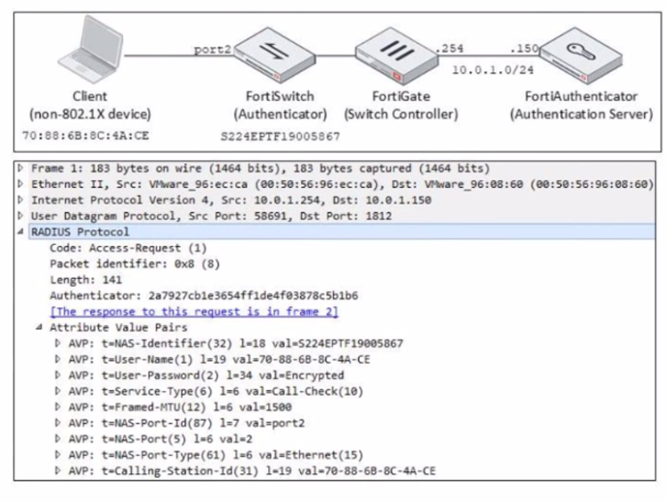
Examine the network diagram and packet capture shown in the exhibit
The packet capture was taken between FortiGate and FortiAuthenticator and shows a RADIUS Access-Request packet sent by FortiSwitch to FortiAuthenticator through FortiGate
Why does the User-Name attribute in the RADIUS Access-Request packet contain the client MAC address?
- A. The client is performing AD machine authentication
- B. FortiSwitch is authenticating the client using MAC authentication bypass
- C. The client is performing user authentication
- D. FortiSwitch is sending a RADIUS accounting message to FortiAuthenticator
Answer: B
Explanation:
According to the exhibit, the User-Name attribute in the RADIUS Access-Request packet contains the client MAC address of 00:0c:29:6a:2b:3d. This indicates that FortiSwitch is authenticating the client using MAC authentication bypass (MAB), which is a method of authenticating devices that do not support 802.1X by using their MAC address as the username and password. Therefore, option B is true because it explains why the User-Name attribute contains the client MAC address. Option A is false because AD machine authentication uses a computer account name and password, not a MAC address. Option C is false because user authentication uses a user name and password, not a MAC address. Option D is false because FortiSwitch is sending a RADIUS Access-Request message to FortiAuthenticator, not a RADIUS accounting message.
NEW QUESTION 9
Refer to the exhibits.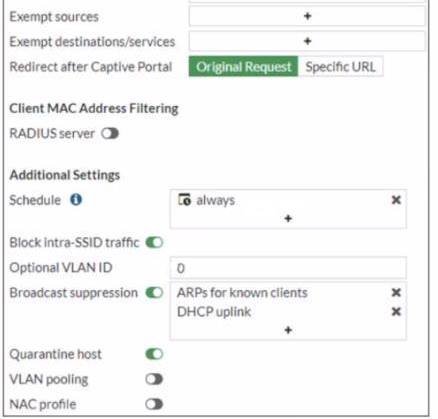
Firewall Policy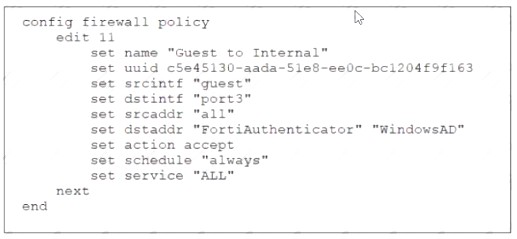
Examine the firewall policy configuration and SSID settings
An administrator has configured a guest wireless network on FortiGate using the external captive portal The administrator has verified that the external captive portal URL is correct However wireless users are not able to see the captive portal login page
Given the configuration shown in the exhibit and the SSID settings which configuration change should the administrator make to fix the problem?
- A. Disable the user group from the SSID configuration
- B. Enable the captivs-portal-exempt option in the firewall policy with the ID 11.
- C. Apply a guest.portal user group in the firewall policy with the ID 11.
- D. Include the wireless client subnet range in the Exempt Source section
Answer: C
Explanation:
According to the FortiGate Administration Guide, “To use an external captive portal, you must configure a user group that uses the external captive portal as the authentication method and apply it to a firewall policy.” Therefore, option C is true because it will allow the wireless users to be redirected to the external captive portal URL when they try to access the Internet. Option A is false because disabling the user group from the SSID configuration will prevent the wireless users from being authenticated by the FortiGate device. Option B is false because enabling the captive-portal-exempt option in the firewall policy will bypass the captive portal authentication for the wireless users, which is not the desired outcome. Option D is false because including the wireless client subnet range in the Exempt Source section will also bypass the captive portal authentication for the wireless users, which is not the desired outcome.
NEW QUESTION 10
Exhibit.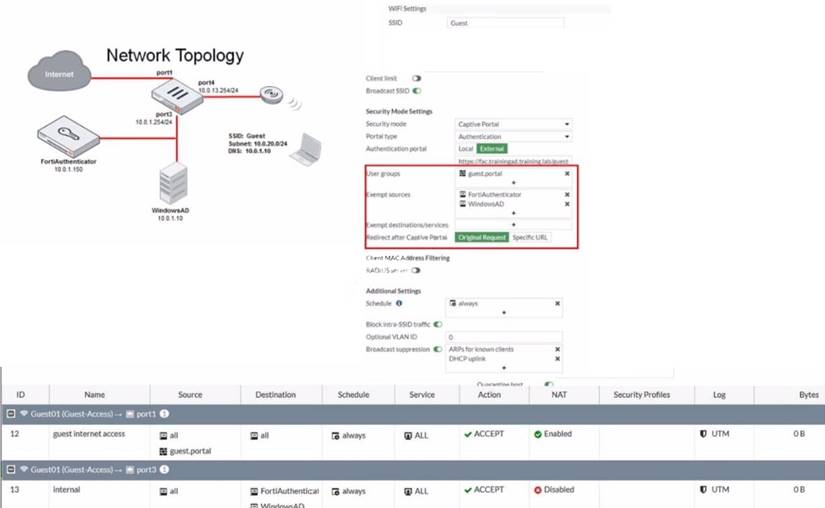
Refer to the exhibit showing a network topology and SSID settings.
FortiGate is configured to use an external captive portal However wireless users are not able to see the captive portal login page
Which configuration change should the administrator make to fix the problem?
- A. Enable NAT in the firewall policy with the ID 13.
- B. Add the FortiAuthenticator and WindowsAD address objects as exempt destinations services
- C. Enable the captive-portal-exempt option in the firewall policy with the ID 12
- D. Remove the guest.portal user group in the firewall policy with the ID 12
Answer: B
Explanation:
According to the exhibit, the network topology and SSID settings show that FortiGate is configured to use an external captive portal hosted on FortiAuthenticator, which is connected to a Windows AD server for user authentication. However, wireless users are not able to see the captive portal login page, which means that they are not redirected to the external captive portal URL. Therefore, option B is true because adding the FortiAuthenticator and WindowsAD address objects as exempt destinations services will allow the wireless users to access the external captive portal URL without being blocked by the firewall policy. Option A is false because enabling NAT in the firewall policy with the ID 13 will not affect the redirection to the external captive portal URL, but rather the source IP address of the wireless traffic. Option C is false because enabling the captive-portal-exempt option in the firewall policy with the ID 12will bypass the captive portal authentication for the wireless users, which is not the desired outcome. Option D is false because removing the guest.portal user group in the firewall policy with the ID 12 will prevent the wireless users from being authenticated by FortiGate, which is required for accessing the external captive portal.
NEW QUESTION 11
Where can FortiGate learn the FortiManager IP address or FQDN for zero-touch provisioning'?
- A. From an LDAP server using a simple bind operation
- B. From a TFTP server
- C. From a DHCP server using options 240 and 241
- D. From a DNS server using A or AAAA records
Answer: D
Explanation:
According to the FortiGate Administration Guide, “FortiGate can learn the FortiManager IP address or FQDN for zero-touch provisioning from a DNS server using A or AAAA records. The DNS server must be configured to resolve the hostname fortimanager.fortinet.com to the IP address or FQDN of the FortiManager device.” Therefore, option D is true because it describes the method for FortiGate to learn the FortiManager IP address or FQDN for zero-touch provisioning. Option A is false because LDAP is not used for zero-touch provisioning. Option B is false because TFTP is not used for zero-touch provisioning. Option C is false because DHCP options 240 and 241 are not used for zero-touch provisioning.
NEW QUESTION 12
......
P.S. Easily pass NSE7_LED-7.0 Exam with 37 Q&As 2passeasy Dumps & pdf Version, Welcome to Download the Newest 2passeasy NSE7_LED-7.0 Dumps: https://www.2passeasy.com/dumps/NSE7_LED-7.0/ (37 New Questions)
- [2021-New] Fortinet NSE4 Dumps With Update Exam Questions (41-50)
- [2021-New] Fortinet NSE5 Dumps With Update Exam Questions (121-130)
- All About Free NSE4_FGT-7.0 Free Exam Questions
- The Secret Of Fortinet FortiADC Practice
- Up To The Immediate Present NSE4_FGT-6.4 Exam For Fortinet NSE 4 - FortiOS 6.4 Certification
- All About Realistic NSE6_FAC-6.4 Free Samples
- The Rebirth Guide To NSE7_LED-7.0 Exam Topics
- Fortinet NSE4_FGT-6.2 Software 2021
- [2021-New] Fortinet NSE4 Dumps With Update Exam Questions (51-60)
- What 100% Correct NSE5_FCT-7.0 Study Guides Is

