P2150-870 Exam Questions - Online Test
P2150-870 Premium VCE File

150 Lectures, 20 Hours

Pass4sure P2150-870 Questions are updated and all P2150-870 answers are verified by experts. Once you have completely prepared with our P2150-870 exam prep kits you will be ready for the real P2150-870 exam without a problem. We have Updated IBM P2150-870 dumps study guide. PASSED P2150-870 First attempt! Here What I Did.
Online P2150-870 free questions and answers of New Version:
NEW QUESTION 1
Which types of software appliance are involved of an events is received by an Event Collector, and the event is then to an Event Processor and causes an Offense to be updated on the Console?
- A. 13xx to 17xx to 31xx
- B. 13xx to 18xxt o 21xx
- C. 13xx to 16xx to 31xx
- D. 15xx to 17xx to 21xx
Answer: C
NEW QUESTION 2
What does QRadar Incident Forensics do? QRadar Incident Forensics:
- A. analyzes event data for an incident that is discovered by QRadar SI EM.
- B. analyzes flow data for an incident that is discovered by a QRadar SI EM.
- C. brings in the vulnerability data relevant for an incident that is discovered by QRadar SIEM.
- D. aggregates the relevant network data for an incident that is discovered by QRadar SIEM.
Answer: A
NEW QUESTION 3
What is the unique benefit of moving to QRadar on Cloud? Customers can now:
- A. reduce future capital expense.
- B. take advantage of QRadar Apps.
- C. build much larger QRadar deployments
- D. have access to additional device support modules.
Answer: B
NEW QUESTION 4
What is the least secure of the five transmission types?
- A. Wireless
- B. Fiber Optic
- C. Coaxial Cable
- D. Shielded Twisted Pair
- E. Unshielded Twisted Pair
Answer: C
NEW QUESTION 5
Which is the most common formatused to send event data to a SIEM?
- A. JSON
- B. LEEF
- C. Syslog
- D. NetFlow
Answer: D
NEW QUESTION 6
Which is a valid use case for implementing QRadar reference data collections?
- A. Change all incoming events to add an additional field value.
- B. Provide an index for all data (events and flow data) in real time.
- C. Store hash values and test each incoming hash against this set
- D. Speed up dashboard functions due to caching common widget data sets
Answer: C
NEW QUESTION 7
What type of appliance is a 3105?
- A. Flow Collector
- B. Event Collector
- C. Event Processor
- D. All in One OR Console
Answer: A
NEW QUESTION 8
In this diagram, showing the Ariel Search Flow, what is the name of the components as ‘X’, running on the Console?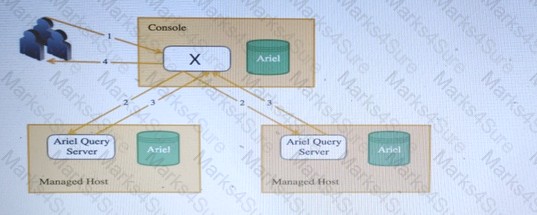
- A. AQL Processor
- B. Ariel Proxy Server
- C. Ariel Query Server
- D. REST -API endpoint
Answer: A
NEW QUESTION 9
What is the QRadar 14xx Data Node used for? It is used to:
- A. offload Offense management tasks from a multi-tenant 31 xx appliance.
- B. provide a long term data backup store for 16xx, 17xx, 18xx and 31 xx appliances.
- C. provide additional storage and processing for 16x
- D. 17xx, 18xx and 31 xx appliances.
- E. run complex 'Machine Learning' style applications in the QRadar application framework.
Answer: B
NEW QUESTION 10
Which is a valid use case for QRadar Network Insights (QN|)?
- A. Finding anomalies and behavior exceptions in event traffic volumes
- B. Analyzing network traffic and finding document hashes from email attachments.
- C. Discovering the network topology within the enterprise based on retrieving the firewall and router/switch rule sets.
- D. Doing after the factreconstruction of user web sessions, chat sessions, and documents, and finding relations between all these.
Answer: C
NEW QUESTION 11
Which is standard on a QRadar on Cloud deployment?
- A. High Availability
- B. Packet analysis
- C. Vulnerability Management
- D. Custom log source development
Answer: B
NEW QUESTION 12
Which question(s) con QRadar help customers answer concerning the security of their network?
- A. Who is attacking?
- B. What is being attacked?
- C. What is the security impact?
- D. When are the attacks taking place?
- E. All the above
Answer: D
NEW QUESTION 13
Which attributes would contribute to an effective demonstration of QRadar?
- A. Bring a whiteboard since prospect might not have on
- B. Show what each tab of the QRadar interface does.
- C. Show all analysis features on flow dat
- D. Focus on the functions that the prospect asked for
- E. Explain all extension options for add-ons to the prospec
- F. Explain QRadar's architecture and scalability.
- G. Tell a story on how QRadar solves an issue that is relevant to the prospec
- H. Talk about the benefits of QRadar in relation to the prospect's situation.
Answer: C
NEW QUESTION 14
To view flow data in QRadar, which tab should a user navigate to?
- A. Assets
- B. Log Activity
- C. User Analytics
- D. Network Activity
Answer: A
NEW QUESTION 15
Which case shows how approximately 1000 Events per second, using an encrypted channel, can be sent from a private cloud to a QRader processor?
- A. Place an event processor in the private cloud, and forward the events to another event collector.
- B. Place a risk manager appliance in the private cloud, and forward the events to another event collector.
- C. Place a packet capture appliance in the private cloud, and forward the events to a cloud events processor.
- D. Place an event collector in the private cloud, and forward the event to the customers event processor.
Answer: A
NEW QUESTION 16
Which categorizes a threat to a type of attack?
- A. Sniffin
- B. Interruption
- C. SQL injection, Interception
- D. Man in the middle, Fabrication
- E. Denial of Service, Modification
Answer: B
NEW QUESTION 17
What are thesystems called which send events to QRadar?
- A. Assets
- B. Firewalls
- C. Log Sources
- D. Data Backups
Answer: D
NEW QUESTION 18
Which is NOT an option for the deployment of the QRader sopftware?
- A. Cloud
- B. Virtual
- C. Live CD/DVD
- D. 3rdParty Appliance
Answer: A
NEW QUESTION 19
In which use case can QRadar Vulnerability Manager be used to detect a particular vulnerability and assist in remediating?
QRadar Vulnerability Manager:
- A. to patch systems for high risk vulnerabilities.
- B. to analyze events from and to a known Botnet site.
- C. to extract packets and reconstruct the network traffic session.
- D. for searching which systems are vulnerable to a particular exploit and what Intrusion Preventions systems can be used to remediate it.
Answer: D
NEW QUESTION 20
......
Recommend!! Get the Full P2150-870 dumps in VCE and PDF From Certshared, Welcome to Download: https://www.certshared.com/exam/P2150-870/ (New 40 Q&As Version)
- [2021-New] IBM C9550-412 Dumps With Update Exam Questions (21-30)
- [2021-New] IBM C5050-285 Dumps With Update Exam Questions (1-10)
- Top Tips Of Renew C2090-600 Free Download
- [2021-New] IBM C2090-320 Dumps With Update Exam Questions (2-11)
- The Rebirth Guide To C2150-606 Training Tools
- [2021-New] IBM C9010-022 Dumps With Update Exam Questions (91-100)
- [2021-New] IBM C5050-285 Dumps With Update Exam Questions (11-20)
- [2021-New] IBM C9510-401 Dumps With Update Exam Questions (11-20)
- IBM C1000-017 Dumps 2021
- [2021-New] IBM C9010-022 Dumps With Update Exam Questions (11-20)

