210-255 Exam Questions - Online Test
210-255 Premium VCE File

150 Lectures, 20 Hours

Master the content and be ready for exam day success quickly with this . We guarantee it!We make it a reality and give you real in our Cisco 210-255 braindumps. Latest 100% VALID at below page. You can use our Cisco 210-255 braindumps and pass your exam.
Free 210-255 Demo Online For Microsoft Certifitcation:
NEW QUESTION 1
Which of the following can be identified by correlating DNS intelligence and other security events? (Choose two.)
- A. Communication to CnC servers
- B. Configuration issues
- C. Malicious domains based on reputation
- D. Routing problems
Answer: AC
NEW QUESTION 2
Drag and drop the type of evidence from the left onto the correct deception(s) of that evidence on the right.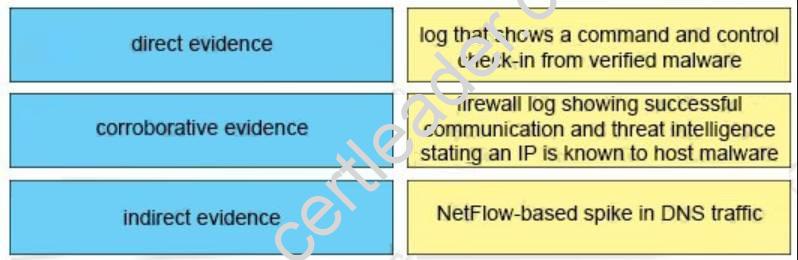
Answer:
Explanation: 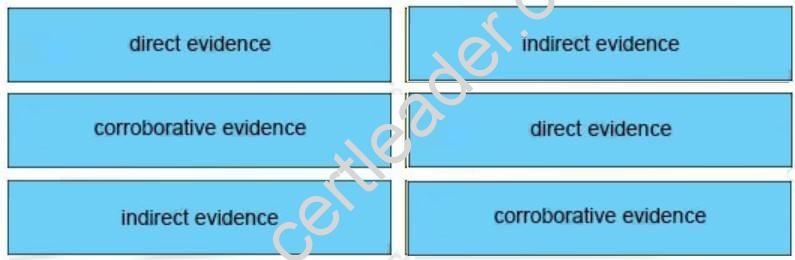
NEW QUESTION 3
Which of the following steps in the kill chain would come before the others?
- A. C2
- B. Delivery
- C. Installation
- D. Exploitation
Answer: B
NEW QUESTION 4
A user on your network receives an email in their mailbox that contains a malicious attachment. There is no indication that the file was run. Which category as defined in the Diamond Model of Intrusion does this activity fall under?
- A. reconnaissance
- B. weaponization
- C. delivery
- D. installation
Answer: C
NEW QUESTION 5
What is the process of remediation the system from attack so that responsible threat actor can be revealed?
- A. Validating the Attacking Host’s IP Address
- B. Researching the Attacking Host through Search Engines.
- C. Using Incident Databases.
- D. Monitoring Possible Attacker Communication Channels.
Answer: A
NEW QUESTION 6
Refer to the exhibit.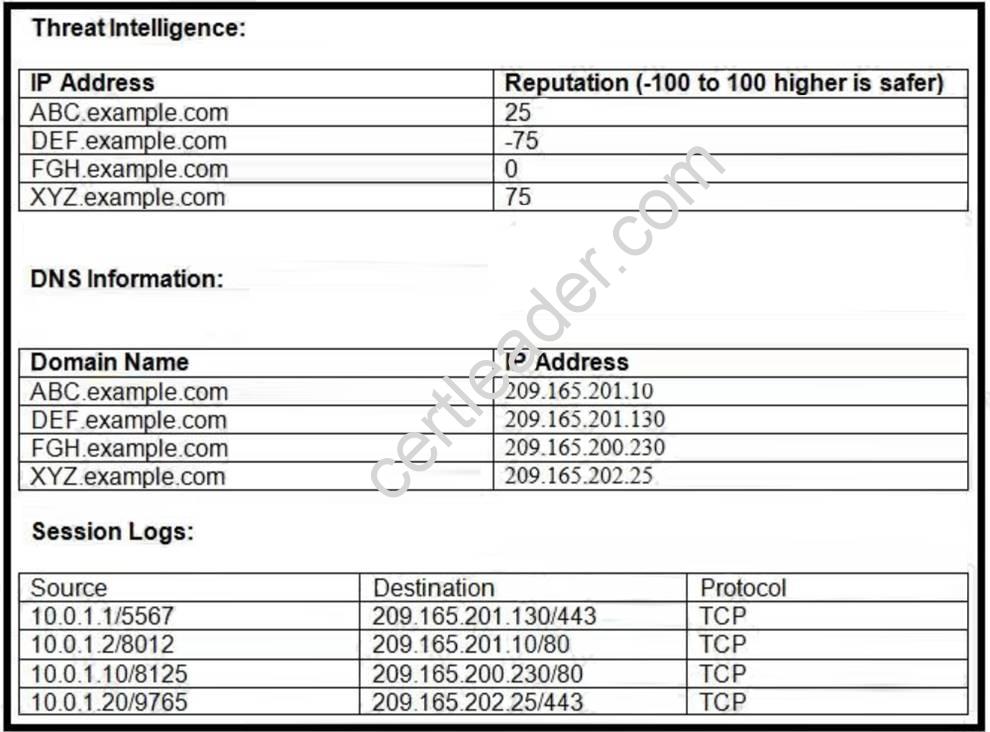
Which host is likely connecting to a malicious site?
- A. 10.0.1.10
- B. 10.0.1.20
- C. 10.0.12
- D. 10.0.1.1
Answer: D
NEW QUESTION 7
What define the roadmap for implementing the incident response capability?
- A. incident response plan
- B. incident response procedure
- C. incident handling guide
- D. incident response policy
Answer: A
NEW QUESTION 8
Refer to the exhibit.
Drag and drop the element name from the left onto the correct piece of the NetFlow v5 record from a security event on the right.
Answer:
Explanation: Source addressBytes transmittedSource portDestination addressnumber of packetsDestination port Protocol
NEW QUESTION 9
Drag and drop the elements of incident handling from the left into the correct order on the right.
Answer:
Explanation: 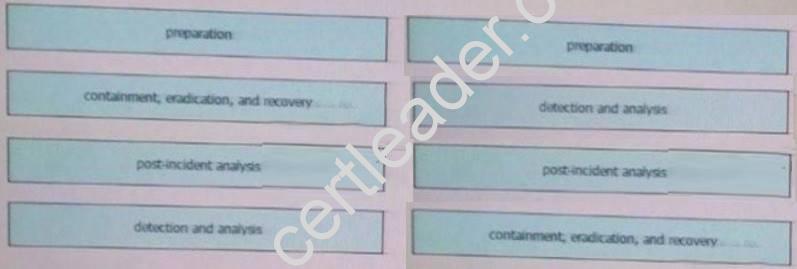
NEW QUESTION 10
Which of the following has been used to evade IDS and IPS devices?
- A. SNMP
- B. HTTP
- C. TNP
- D. Fragmentation
Answer: D
NEW QUESTION 11
Employees are allowed access to internal websites. An employee connects to an internal website and IDS reports it as malicious behavior. What is this example of?
- A. true positive
- B. false negative
- C. false positive
- D. true negative
Answer: C
NEW QUESTION 12
Which example of a precursor is true?
- A. An admin finds their password has been changed.
- B. A log indicating a port scan was run against a host.
- C. A notification that a host is infected with malware.
- D. A device configuration changed from the baseline without an audit log entry.
Answer: B
NEW QUESTION 13
Which CVSSv3 metric value increases when attacks consume network bandwidth, processor cycles, or disk space?
- A. confidentiality
- B. integrity
- C. availability
- D. complexity
Answer: C
Explanation: Availability Impact (A): This metric measures the impact to the availability of the impacted component resulting from a successfully exploited vulnerability. While the confidentiality and integrity impact metrics apply to the loss of confidentiality or integrity of data such as information and files used by the impacted component, this metric refers to the loss of availability of the impacted component itself, such as a networked service such as web, database, and email. Because availability refers to the accessibility of information resources, attacks that consume network bandwidth, processor cycles, or disk space all impact the availability of an impacted component.
NEW QUESTION 14
Which option creates a display filter on Wireshark on a host IP address or name?
- A. ip.address == <address> or ip.network == <network>
- B. [tcp|udp] ip.[src|dst] port <port>
- C. ip.addr == <addr> or ip.name == <name>
- D. ip.addr == <addr> or ip.host == <host>
Answer: D
NEW QUESTION 15
Which option is unnecessary for determining the appropriate containment strategy according to NIST.SP800-61 r2?
- A. effectiveness of the strategy
- B. time and resource needed to implement the strategy
- C. need for evidence preservation
- D. attack vector used to compromise the system
Answer: D
NEW QUESTION 16
Which technology is the leading industry approach used to automatically enforce NAC?
- A. SNMP
- B. port security
- C. IGMP
- D. 802.1x
Answer: D
NEW QUESTION 17
Which element is included in an incident response plan?
- A. organization mission
- B. junior analyst approval
- C. day-to-day firefighting
- D. siloed approach to communications
Answer: A
Explanation: The incident response plan should include the following elements:
– Mission– Strategies and goals– Senior management approval– Organizational approach to incident response– How the incident response team will communicate with the rest of the organization and with other organizations– Metrics for measuring the incident response capability and its effectiveness– Roadmap for maturing the incident response capability– How the program fits into the overall organization.
NEW QUESTION 18
Refer to the exhibit.
You notice that the email volume history has been abnormally high. Which potential result is true?
- A. Email sent from your domain might be filtered by the recipient.
- B. Messages sent to your domain may be queued up until traffic dies down.
- C. Several hosts in your network may be compromised.
- D. Packets may be dropped due to network congestion.
Answer: C
NEW QUESTION 19
Choose the option that best describes NIST data integrity
- A. use only sha-1
- B. use only md5
- C. you must hash data & backup and compare hashes
- D. no need to hash data & backup and compare hashes
Answer: C
NEW QUESTION 20
What mechanism does the Linux operating system provide to control access to files?
- A. privileges required
- B. user interaction
- C. file permissions
- D. access complexity
Answer: C
P.S. Easily pass 210-255 Exam with 160 Q&As Certleader Dumps & pdf Version, Welcome to Download the Newest Certleader 210-255 Dumps: https://www.certleader.com/210-255-dumps.html (160 New Questions)
- [2021-New] Cisco 300-101 Dumps With Update Exam Questions (6-15)
- [2021-New] Cisco 400-101 Dumps With Update Exam Questions (131-140)
- [2021-New] Cisco 300-115 Dumps With Update Exam Questions (11-20)
- 100% Correct 500-651 Braindumps 2021
- [2021-New] Cisco 300-209 Dumps With Update Exam Questions (101-110)
- [2021-New] Cisco 300-320 Dumps With Update Exam Questions (111-120)
- Far Out Automating And Programming Cisco Data Center Solutions (DCAUTO) 300-635 Free Practice Exam
- [2021-New] Cisco 300-075 Dumps With Update Exam Questions (81-90)
- Exact Cisco 350-901 Free Dumps Online
- [2021-New] Cisco 300-101 Dumps With Update Exam Questions (13-22)

