210-255 Exam Questions - Online Test
210-255 Premium VCE File

150 Lectures, 20 Hours

are updated and are verified by experts. Once you have completely prepared with our you will be ready for the real 210-255 exam without a problem. We have . PASSED First attempt! Here What I Did.
Online 210-255 free questions and answers of New Version:
NEW QUESTION 1
Refer to the exhibit.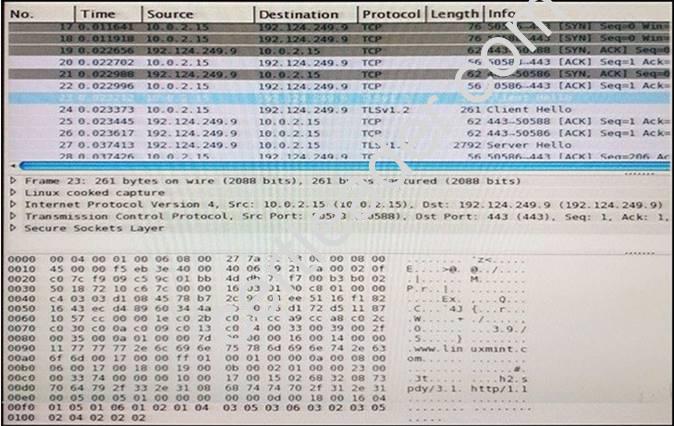
Refer to the exhibit. Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.
Answer:
Explanation: Source address, source port, destination port, destination address, transport protocol, network protocol, application protocol.
NEW QUESTION 2
In VERIS, an incident is viewed as a series of events that adversely affects the information assets of an organization. Which option contains the elements that every event is comprised of according to VERIS incident model'?
- A. victim demographics, incident description, incident details, discovery & response
- B. victim demographics, incident details, indicators of compromise, impact assessment
- C. actors, attributes, impact, remediation
- D. actors, actions, assets, attributes
Answer: D
NEW QUESTION 3
What attribute belonging VERIS schema?
- A. confidentiality/possession
- B. integrity/authenticity
- C. availability/utility
Answer: ABC
NEW QUESTION 4
Which option is a misuse variety per VERIS enumerations?
- A. snooping
- B. hacking
- C. theft
- D. assault
Answer: B
Explanation: Misuse is defined as the use of entrusted organizational resources or privileges for any purpose or manner contrary to that which was intended. Includes administrative abuse, use policy violations, use of non-approved assets, etc. These actions can be malicious or non-malicious in nature. Misuse is exclusive to parties that enjoy a degree of trust from the organization, such as insiders and partners.VERIS classification note: There is an action category for Hacking and for Misuse. Both can utilize similar vectors and achieve similar results; in Misuse, the actor was granted access/privileges (and used them inappropriately), whereas with Hacking, access/privileges are obtained illegitimately.
NEW QUESTION 5
Which option can be addressed when using retrospective security techniques?
- A. if the affected host needs a software update
- B. how the malware entered our network
- C. why the malware is still in our network
- D. if the affected system needs replacement
Answer: C
NEW QUESTION 6
Refer to exhibit.
Which option is the logical source device for these events?
- A. web server
- B. NetFlow collector
- C. proxy server
- D. IDS/IPS
Answer: A
NEW QUESTION 7
In Microsoft Windows, as files are deleted the space they were allocated eventually is considered available for use by other files. This creates alternating used and unused areas of various sizes. What is this called?
- A. network file storing
- B. free space fragmentation
- C. alternate data streaming
- D. defragmentation
Answer: B
Explanation: Free (unallocated) space fragmentation occurs when there are several unused areas of the file system where new files or meta data can be written to. Unwanted free space fragmentation is generally caused by deletion or truncation of files, but file systems may also intentionally insert fragments (“bubbles”) of free space in order to facilitate extending nearby files
NEW QUESTION 8
In the context of incident handling phases, which two activities fall under scoping? (Choose two.)
- A. determining the number of attackers that are associated with a security incident
- B. ascertaining the number and types of vulnerabilities on your network
- C. identifying the extent that a security incident is impacting protected resources on the network
- D. determining what and how much data may have been affected
- E. identifying the attackers that are associated with a security incident
Answer: CE
NEW QUESTION 9
Which command can be used to find open ports on a system?
- A. netstat -I
- B. netstat -v
- C. netstat -r
- D. netstat-g
Answer: A
NEW QUESTION 10
Which of the following is not an example of reconnaissance?
- A. Searching the robots.txt file
- B. Redirecting users to a source and scanning traffic to learn about the target
- C. Scanning without completing the three-way handshake
- D. Communicating over social media
Answer: B
NEW QUESTION 11
What is the process of remediation the network and systems and/or reconstructing so the responsible threat actor can be revealed?
- A. Data analysis
- B. Assets distribution
- C. Evidence collection
- D. Threat actor distribution
Answer: A
NEW QUESTION 12
Which CVSSv3 Attack Vector metric value requires the attacker to physically touch or manipulate the vulnerable component?
- A. local
- B. physical
- C. network
- D. adjacent
Answer: B
Explanation: Attack Vector (AV): This metric reflects the context by which vulnerability exploitation is possible. This metric value and the base score will correlate with an attacker’s proximity to a vulnerable component. The score will be higher the more remote (logically and physically) an attacker is from the vulnerable
component.
Local: Exploiting the vulnerability requires either physical access to the target or a local (shell) account on the target.
Adjacent: Exploiting the vulnerability requires access to the local network of the target, and cannot be performed across an OSI Layer 3 boundary.
Network: The vulnerability is exploitable from remote networks. Such a vulnerability is often termed “remotely exploitable,” and can be thought of as an attack being exploitable one or more network hops away, such as across Layer 3 boundaries from routers.
Physical: A vulnerability exploitable with physical access requires the attacker to physically touch or manipulate the vulnerable component.
NEW QUESTION 13
When performing threat hunting against a DNS server, which traffic toward the affected domain is considered a starting point?
- A. HTTPS traffic
- B. TCP traffic
- C. HTTP traffic
- D. UDP traffic
Answer: D
NEW QUESTION 14
Which of the following is one of the main goals of the CSIRT?
- A. To configure the organization's firewalls
- B. To monitor the organization's IPS devices
- C. To minimize and control the damage associated with incidents, provide guidance for mitigation, and work to prevent future incidents
- D. To hire security professionals who will be part of the InfoSec team of the organization.
Answer: C
NEW QUESTION 15
According to NIST-SP800-61R2, which option should be contained in the issue tracking system?
- A. incidents related to the current incident
- B. incident unrelated to the current incident
- C. actions taken by nonincident handlers
- D. latest public virus signatures
Answer: A
NEW QUESTION 16
According to NIST 86, which action describes the volatile data collection?
- A. Collect data before rebooting
- B. Collect data while rebooting
- C. Collect data after rebooting
- D. Collect data that contains malware
Answer: A
NEW QUESTION 17
What information from HTTP logs can be used to find a threat actor?
- A. referer
- B. IP address
- C. user-agent
- D. URL
Answer: B
Explanation: https://www.sans.org/reading-room/whitepapers/malicious/user-agent-field-analyzing-detecting-abnorma s-organization-33874
NEW QUESTION 18
Which two potions about deterministic and probabilistic analysis are true? (Choose two.)
- A. probabilistic analysis uses data known beforehand and deterministic analysis is based off assumptions.
- B. Deterministic analysis uses data known beforehand and probabilistic analysis based off of assumptions.
- C. Deterministic analysis is based off of assumptions
- D. Probabilistic analysis result in a result that is definitive.
- E. probabilistic analysis results in a result that is not definitive.
Answer: BE
NEW QUESTION 19
Which type of intrusion event is an attacker retrieving the robots. txt file from target site?
- A. exploitation
- B. weaponization
- C. scanning
- D. reconnaissance
Answer: D
NEW QUESTION 20
Filtering ports in wireshark?
- A. tcp.port == 80
- B. tcp port equals 80
- C. tcp.port 80
- D. port 80
Answer: A
P.S. Surepassexam now are offering 100% pass ensure 210-255 dumps! All 210-255 exam questions have been updated with correct answers: https://www.surepassexam.com/210-255-exam-dumps.html (160 New Questions)
- [2021-New] Cisco 300-320 Dumps With Update Exam Questions (71-80)
- Refresh 300-180 Dumps 2021
- [2021-New] Cisco 210-060 Dumps With Update Exam Questions (31-40)
- Latest Supporting Cisco Routing & Switching Network Devices 100-490 Free Dumps
- [2021-New] Cisco 300-075 Dumps With Update Exam Questions (111-120)
- [2021-New] Cisco 400-101 Dumps With Update Exam Questions (10-19)
- [2021-New] Cisco 300-320 Dumps With Update Exam Questions (61-70)
- How Many Questions Of 350-601 Preparation Exams
- [2021-New] Cisco 300-320 Dumps With Update Exam Questions (71-80)
- [2021-New] Cisco 400-051 Dumps With Update Exam Questions (61-70)

