210-255 Exam Questions - Online Test
210-255 Premium VCE File

150 Lectures, 20 Hours

are updated and are verified by experts. Once you have completely prepared with our you will be ready for the real 210-255 exam without a problem. We have . PASSED First attempt! Here What I Did.
Free 210-255 Demo Online For Microsoft Certifitcation:
NEW QUESTION 1
Which option is generated when a file is run through an algorithm and generates a string specific to the contents of that file?
- A. URL
- B. hash
- C. IP address
- D. destination port
Answer: B
NEW QUESTION 2
When incident data is collected, it is important that evidentiary cross-contamination is prevented. How is this accomplished?
- A. by allowing unrestricted access to impacted devices
- B. by not allowing items of evidence to physically touch
- C. by ensuring power is removed to all devices involved
- D. by not permitting a device to store evidence if it is the evidence itself.
Answer: D
NEW QUESTION 3
Which kind of evidence can be considered most reliable to arrive at an analytical assertion?
- A. direct
- B. corroborative
- C. indirect
- D. circumstantial
- E. textual
Answer: A
NEW QUESTION 4
Which identifies both the source and destination location?
- A. IP address
- B. URL
- C. ports
- D. MAC address
Answer: A
Explanation: The IP Address is used to uniquely identify the desired host we need to contact. This information is not shown in the above packet because it exists in the IP header section located right above the TCP header we are analysing. If we were to expand the IP header, we would (certainly) find the source and destination IP Address fields in there.
NEW QUESTION 5
Which statement about the collected evidence data when performing digital forensics is true?
- A. it must be preserved and its integrity verified.
- B. It must be copied to external storage media and immediately distributed to the CISO.
- C. It must be stored in a forensics lab only by the data custodian.
- D. It must be deleted as soon as possible due to PCI compliance.
Answer: A
NEW QUESTION 6
Which signature type results in a legitimate alert being dismissed?
- A. True negative
- B. False negative
- C. True Positive
- D. False Positive
Answer: B
NEW QUESTION 7
Which netstat command show ports? (Choose two)
- A. netstat –a
- B. netstat -l
- C. netstat -v
- D. netstat -g
Answer: AB
NEW QUESTION 8
What can be addressed when using retrospective security techniques?
- A. if the affected host needs a software update
- B. what system are affected
- C. if the affected system needs replacement
- D. why the malware is still in our network
Answer: D
NEW QUESTION 9
Which statement about threat actors is true?
- A. They are any company assets that are threatened.
- B. They are any assets that are threatened.
- C. They are perpetrators of attacks.
- D. They are victims of attacks.
Answer: C
Explanation: A threat actor is an individual or a group of individuals who are responsible for a malicious incident that negatively impacts the security posture of an organization. Threat actors can be further categorized by a combination of skill level, type of activity within the network, and their pursuing motivations.
NEW QUESTION 10
Which Linux file system allows unlimited folder subdirectory structure
- A. ext4
- B. ext3
- C. ext2
- D. NTFS
Answer: A
NEW QUESTION 11
Which of the following is not true about listening ports?
- A. A listening port is a port held open by a running application in order to accept inbound connections.
- B. Seeing traffic from a known port will identify the associated service.
- C. Listening ports use values that can range between 1 and 65535.
- D. TCP port 80 is commonly known for Internet traffic.
Answer: B
NEW QUESTION 12
The united State CERT provides cybersecurity protection to Federal, civilian, and executive branch agencies through intrusion detection and prevention capabilities. Which type of incident response team is this an example of?
- A. Federal PSIRT
- B. National PSIRT
- C. National CSIRT
- D. Federal CSIRT
Answer: B
NEW QUESTION 13
Which function does an internal CSIRT provide?
- A. incident handling services across various CSIRTs
- B. incident handling services for a country’s government
- C. incident handling services for a parent organizationD incident handling services as a service for other organization
Answer: C
NEW QUESTION 14
You see confidential data being exfiltrated to an IP address that is attributed to a known Advanced Persistent Threat group. Assume that this is part of a real attach and not a network misconfiguration. Which category does this event fall under as defined in the Diamond Model of Intrusion?
- A. reconnaissance
- B. weaponization
- C. delivery
- D. action on objectives
Answer: D
Explanation: It is an Advanced Persistent Threat group that being exfiltrated confidential data, and Action and Objectives says that adversary is inside the network and starting to achieve his or her objective for launching the attack. An adversary could use this opportunity to steal data.
NEW QUESTION 15
Which value in profiling servers in a system is true?
- A. it can identify when network performance has decreased
- B. it can identify servers that have been exploited
- C. it can identify when network ports have been connected
- D. it can protect the address space of critical hosts.
Answer: A
NEW QUESTION 16
Refer to the exhibit.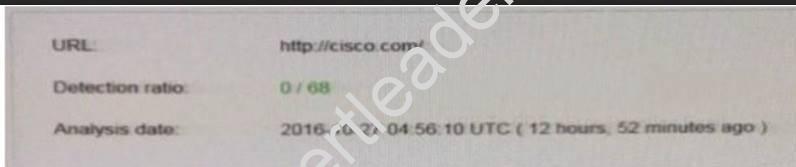
We have performed a malware detection on the Cisco website. Which statement about the result is true?
- A. The website has been marked benign on all 68 checks.
- B. The threat detection needs to run again.
- C. The website has 68 open threats.
- D. The website has been marked benign on 0 checks.
Answer: A
Explanation: https://www.virustotal.com/en/url/df05d8e27bd760c33dc709951a5840cc6578d78d544d869890b7b94ea21e46b0
NEW QUESTION 17
Refer to the exhibit.
Which type of log is this an example of?
- A. IDS log
- B. proxy log
- C. NetFlow log
- D. syslog
Answer: C
NEW QUESTION 18
Which description of a retrospective malware detection is true?
- A. You use Wireshark to identify the malware source.
- B. You use historical information from one or more sources to identify the affected host or file.
- C. You use information from a network analyzer to identify the malware source.
- D. You use Wireshark to identify the affected host or file.
Answer: B
NEW QUESTION 19
Which feature is used to find possible vulnerable services running on a server?
- A. CPU utilization
- B. security policy
- C. temporary internet files
- D. listening ports
Answer: D
NEW QUESTION 20
Which CSIRT category provides incident handling services to their parent organization such as a bank, a manufacturing company, a university, or a federal agency?
- A. internal CSIRT
- B. national CSIRT
- C. coordination centers
- D. analysis centers
- E. vendor teams
- F. incident response providers
Answer: A
100% Valid and Newest Version 210-255 Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/210-255-dumps.html (New 160 Q&As)
- [2021-New] Cisco 200-125 Dumps With Update Exam Questions (161-168)
- [2021-New] Cisco 400-201 Dumps With Update Exam Questions (61-70)
- [2021-New] Cisco 400-251 Dumps With Update Exam Questions (51-60)
- [2021-New] Cisco 400-101 Dumps With Update Exam Questions (41-50)
- [2021-New] Cisco 300-075 Dumps With Update Exam Questions (121-130)
- [2021-New] Cisco 300-320 Dumps With Update Exam Questions (31-40)
- [2021-New] Cisco 642-998 Dumps With Update Exam Questions (31-40)
- [2021-New] Cisco 100-105 Dumps With Update Exam Questions (5-14)
- [2021-New] Cisco 300-320 Dumps With Update Exam Questions (14-23)
- Leading Cisco Mobile Backhaul For Field Engineers 500-240 Test Engine

