ECSAv10 Exam Questions - Online Test
ECSAv10 Premium VCE File

150 Lectures, 20 Hours

Testking offers free demo for ECSAv10 exam. "EC-Council Certified Security Analyst (ECSA) v10 : Penetration Testing", also known as ECSAv10 exam, is a EC-Council Certification. This set of posts, Passing the EC-Council ECSAv10 exam, will help you answer those questions. The ECSAv10 Questions & Answers covers all the knowledge points of the real exam. 100% real EC-Council ECSAv10 exams and revised by experts!
Online ECSAv10 free questions and answers of New Version:
NEW QUESTION 1
Michael works for Kimball Construction Company as senior security analyst. As part of yearly security audit, Michael scans his network for vulnerabilities. Using Nmap, Michael conducts XMAS scan and most of the ports scanned do not give a response. In what state are these ports?
- A. Filtered
- B. Stealth
- C. Closed
- D. Open
Answer: D
NEW QUESTION 2
You work as an IT security auditor hired by a law firm in Boston to test whether you can gain access to
sensitive information about the company clients. You have rummaged through their trash and found very little information.
You do not want to set off any alarms on their network, so you plan on performing passive foot printing against their Web servers. What tool should you use?
- A. Nmap
- B. Netcraft
- C. Ping sweep
- D. Dig
Answer: B
NEW QUESTION 3
Which one of the following scans starts, but does not complete the TCP handshake sequence for each port selected, and it works well for direct scanning and often works well through firewalls?
- A. SYN Scan
- B. Connect() scan
- C. XMAS Scan
- D. Null Scan
Answer: A
NEW QUESTION 4
The Web parameter tampering attack is based on the manipulation of parameters exchanged between client and server in order to modify application data, such as user credentials and permissions, price and quantity of products, etc.
Usually, this information is stored in cookies, hidden form fields, or URL Query Strings, and is used to increase application functionality and control. This attack takes advantage of the fact that many programmers rely on hidden or fixed fields (such as a hidden tag in a form or a parameter in a URL) as the only security measure for certain operations.
Attackers can easily modify these parameters to bypass the security mechanisms that rely on them.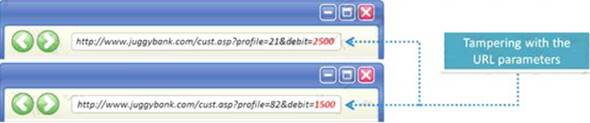
What is the best way to protect web applications from parameter tampering attacks?
- A. Validating some parameters of the web application
- B. Minimizing the allowable length of parameters
- C. Using an easily guessable hashing algorithm
- D. Applying effective input field filtering parameters
Answer: D
NEW QUESTION 5
When you are running a vulnerability scan on a network and the IDS cuts off your connection, what type of IDS is being used?
- A. Passive IDS
- B. Active IDS
- C. Progressive IDS
- D. NIPS
Answer: B
NEW QUESTION 6
Which type of vulnerability assessment tool provides security to the IT system by testing for vulnerabilities in the applications and operation system?
- A. Active/Passive Tools
- B. Application-layer Vulnerability Assessment Tools
- C. Location/Data Examined Tools
- D. Scope Assessment Tools
Answer: D
NEW QUESTION 7
Mason is footprinting an organization to gather competitive intelligence. He visits the company's website for contact information and telephone numbers but does not find any. He knows the entire staff directory was listed on their website 12 months. How can he find the directory?
- A. Visit Google’s search engine and view the cached copy
- B. Crawl and download the entire website using the Surfoffline tool and save them to his computer
- C. Visit the company's partners’ and customers' website for this information
- D. Use Way Back Machine in Archive.org web site to retrieve the Internet archive
Answer: D
NEW QUESTION 8
Hackers today have an ever-increasing list of weaknesses in the web application structure at their disposal, which they can exploit to accomplish a wide variety of malicious tasks.
New flaws in web application security measures are constantly being researched, both by hackers and by security professionals. Most of these flaws affect all dynamic web applications whilst others are dependent on specific application technologies.
In both cases, one may observe how the evolution and refinement of web technologies also brings about new exploits which compromise sensitive databases, provide access to theoretically secure networks, and pose a threat to the daily operation of online businesses.
What is the biggest threat to Web 2.0 technologies?
- A. SQL Injection Attacks
- B. Service Level Configuration Attacks
- C. Inside Attacks
- D. URL Tampering Attacks
Answer: A
NEW QUESTION 9
Which of the following attributes has a LM and NTLMv1 value as 64bit + 64bit + 64bit and NTLMv2 value as 128 bits?
- A. Hash Key Length
- B. C/R Value Length
- C. C/R Key Length
- D. Hash Value Length
Answer: B
NEW QUESTION 10
John, a penetration tester from a pen test firm, was asked to collect information about the host file in a Windows system directory. Which of the following is the location of the host file in Window system directory?
- A. C:WindowsSystem32Boot
- B. C:WINNTsystem32driversetc
- C. C:WINDOWSsystem32cmd.exe
- D. C:WindowsSystem32restore
Answer: B
NEW QUESTION 11
You setup SNMP in multiple offices of your company. Your SNMP software manager is not receiving data from other offices like it is for your main office. You suspect that firewall changes are to blame.
What ports should you open for SNMP to work through Firewalls. (Select 2)
- A. 162
- B. 160
- C. 161
- D. 163
Answer: AC
NEW QUESTION 12
Which of the following are the default ports used by NetBIOS service?
- A. A.-135, 136, 139, 445B.134, 135, 136, 137C.137, 138, 139, 140D.133, 134, 139, 142
Answer: A
NEW QUESTION 13
During the process of fingerprinting a web application environment, what do you need to do in order to analyze HTTP and HTTPS request headers and the HTML source code?
- A. Examine Source of the Available Pages
- B. Perform Web Spidering
- C. Perform Banner Grabbing
- D. Check the HTTP and HTML Processing by the Browser
Answer: D
NEW QUESTION 14
Which of the following scan option is able to identify the SSL services?
- A. –sS
- B. –sV
- C. –sU
- D. –sT
Answer: B
NEW QUESTION 15
Which of the following acts is a proprietary information security standard for organizations that handle cardholder information for the major debit, credit, prepaid, e-purse, ATM, and POS cards and applies to all entities involved in payment card processing?
- A. PIPEDA
- B. PCI DSS
- C. Human Rights Act 1998
- D. Data Protection Act 1998
Answer: B
NEW QUESTION 16
You just passed your ECSA exam and are about to start your first consulting job running security audits for a financial institution in Los Angeles. The IT manager of the company you will be working for tries to see if you remember your ECSA class. He asks about the methodology you will be using to test the company's network.
How would you answer?
- A. IBM Methodology
- B. LPT Methodology
- C. Google Methodology
- D. Microsoft Methodology
Answer: B
NEW QUESTION 17
ARP spoofing is a technique whereby an attacker sends fake ("spoofed") Address Resolution Protocol (ARP) messages onto a Local Area Network. Generally, the aim is to associate the attacker's MAC address with the IP address of another host (such as the default gateway), causing any traffic meant for that IP address to be sent to the attacker instead.
ARP spoofing attack is used as an opening for other attacks.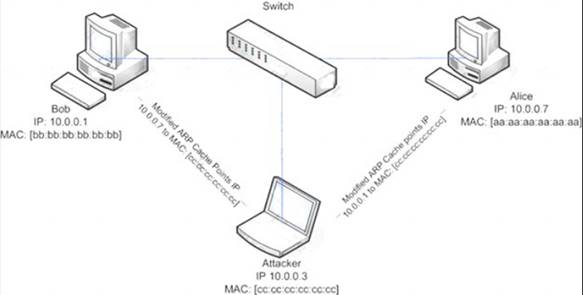
What type of attack would you launch after successfully deploying ARP spoofing?
- A. Parameter Filtering
- B. Social Engineering
- C. Input Validation
- D. Session Hijacking
Answer: D
NEW QUESTION 18
Which of the following reports provides a summary of the complete pen testing process, its outcomes, and recommendations?
- A. Vulnerability Report
- B. Executive Report
- C. Client-side test Report
- D. Host Report
Answer: B
NEW QUESTION 19
A penetration test will show you the vulnerabilities in the target system and the risks associated with it. An educated valuation of the risk will be performed so that the vulnerabilities can be reported as High/Medium/Low risk issues.
What are the two types of ‘white-box’ penetration testing?
- A. Announced testing and blind testing
- B. Blind testing and double blind testing
- C. Blind testing and unannounced testing
- D. Announced testing and unannounced testing
Answer: D
NEW QUESTION 20
What are the security risks of running a "repair" installation for Windows XP?
- A. There are no security risks when running the "repair" installation for Windows XP
- B. Pressing Shift+F1 gives the user administrative rights
- C. Pressing Ctrl+F10 gives the user administrative rights
- D. Pressing Shift+F10 gives the user administrative rights
Answer: D
NEW QUESTION 21
Harold is a security analyst who has just run the rdisk /s command to grab the backup SAM file on a computer. Where should Harold navigate on the computer to find the file?
- A. %systemroot%LSA
- B. %systemroot%repair
- C. %systemroot%system32driversetc
- D. %systemroot%system32LSA
Answer: B
NEW QUESTION 22
You work as an IT security auditor hired by a law firm in Boston. You have been assigned the responsibility to audit the client for security risks. When assessing the risk to the clients network, what step should you take first?
- A. Analyzing, categorizing and prioritizing resources
- B. Evaluating the existing perimeter and internal security
- C. Checking for a written security policy
- D. Analyzing the use of existing management and control architecture
Answer: C
NEW QUESTION 23
What sort of vulnerability assessment approach starts by building an inventory of protocols found on the machine?
- A. Inference-based Assessment
- B. Service-based Assessment Solutions
- C. Product-based Assessment Solutions
- D. Tree-based Assessment
Answer: A
NEW QUESTION 24
In the context of penetration testing, what does blue teaming mean?
- A. A penetration test performed with the knowledge and consent of the organization's IT staff
- B. It is the most expensive and most widely used
- C. It may be conducted with or without warning
- D. A penetration test performed without the knowledge of the organization's IT staff but with permission from upper management
Answer: A
NEW QUESTION 25
Windows stores user passwords in the Security Accounts Manager database (SAM), or in the Active Directory database in domains. Passwords are never stored in clear text; passwords are hashed and the results are stored in the SAM.
NTLM and LM authentication protocols are used to securely store a user's password in the SAM database using different hashing methods.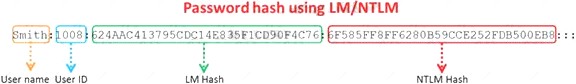
The SAM file in Windows Server 2008 is located in which of the following locations?
- A. c:windowssystem32configSAM
- B. c:windowssystem32driversSAM
- C. c:windowssystem32SetupSAM
- D. c:windowssystem32BootSAM
Answer: D
NEW QUESTION 26
DNS information records provide important data about:
- A. Phone and Fax Numbers
- B. Location and Type of Servers
- C. Agents Providing Service to Company Staff
- D. New Customer
Answer: B
NEW QUESTION 27
......
P.S. Easily pass ECSAv10 Exam with 201 Q&As 2passeasy Dumps & pdf Version, Welcome to Download the Newest 2passeasy ECSAv10 Dumps: https://www.2passeasy.com/dumps/ECSAv10/ (201 New Questions)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (1-10)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (151-160)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (91-100)
- [2021-New] EC-Council 312-50v10 Dumps With Update Exam Questions (1-10)
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (91-100)
- How Many Questions Of 312-50v12 Exam Topics
- Refined 412-79v10 Dumps 2021
- [2021-New] EC-Council 312-50 Dumps With Update Exam Questions (191-200)
- EC-Council 412-79v10 Braindumps 2021
- How Many Questions Of 312-50v11 Sample Question

