GCIA Exam Questions - Online Test
GCIA Premium VCE File

150 Lectures, 20 Hours

Our pass rate is high to 98.9% and the similarity percentage between our GCIA study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the GIAC GCIA exam in just one try? I am currently studying for the GIAC GCIA exam. Latest GIAC GCIA Test exam practice questions and answers, Try GIAC GCIA Brain Dumps First.
Online GCIA free questions and answers of New Version:
NEW QUESTION 1
Which of the following tools can be used for passive OS fingerprinting?
- A. dig
- B. nmap
- C. ping
- D. tcpdump
Answer: D
NEW QUESTION 2
Which of the following firewalls depends on the three-way handshake of the TCP protocol?
- A. Stateful firewall
- B. Endian firewall
- C. Proxy-based firewall
- D. Packet filter firewall
Answer: A
NEW QUESTION 3
Which of the following is not a function of the Snort utility?
- A. Routing messages
- B. Packet sniffing
- C. Packet logging
- D. Intrusion detection
Answer: A
NEW QUESTION 4
Which of the following tools in Helix Windows Live is used to reveal the database password of password protected MDB files created using Microsoft Access or with Jet Database Engine?
- A. Asterisk logger
- B. Access Pass View
- C. FAU
- D. Galleta
Answer: B
NEW QUESTION 5
A firewall is a combination of hardware and software, used to provide security to a network. It is used to protect an internal network or intranet against unauthorized access from the Internet or other outside networks. It restricts inbound and outbound access and can analyze all traffic between an internal network and the Internet. Users can configure a firewall to pass or block packets from specific IP addresses and ports. Which of the following tools works as a firewall for the Linux 2.4 kernel?
- A. Stunnel
- B. IPTables
- C. IPChains
- D. OpenSSH
Answer: B
NEW QUESTION 6
Which of the following Windows XP system files handles memory management, I/O operations, and interrupts?
- A. Ntoskrnl.exe
- B. Advapi32.dll
- C. Kernel32.dll
- D. Win32k.sys
Answer: C
NEW QUESTION 7
Which of the following tools performs comprehensive tests against web servers for multiple items, including over 6100 potentially dangerous files/CGIs?
- A. Dsniff
- B. Snort
- C. Nikto
- D. Sniffer
Answer: C
NEW QUESTION 8
Which of the following is an open-source Web server scanner that tests Web servers for dangerous files/CGIs, outdated server software?
- A. Nmap
- B. Internet bot
- C. Dsniff
- D. Nikto
Answer: D
NEW QUESTION 9
Which of the following is not a Denial of Service (DoS) attack?
- A. Smurf attack
- B. Code injection attack
- C. Ping of Death attack
- D. Teardrop attack
Answer: B
NEW QUESTION 10
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 domainbased network. The network has three Windows Server 2008 member servers and 150 Windows Vista client computers. According to the company's security policy, you apply Windows firewall setting to the computers on the network. Now, you are troubleshooting a connectivity problem that might be caused by Windows firewall. What will you do to identify connections that Windows firewall allows or blocks?
- A. Configure Internet Protocol Security (IPSec).
- B. Disable Windows firewall loggin
- C. Enable Windows firewall loggin
- D. Configure Network address translation (NAT).
Answer: C
NEW QUESTION 11
Which of the following commands in MQC tool matches IPv4 and IPv6 packets when IP parameter is missing?
- A. Match access-group
- B. Match fr-dlci
- C. Match IP precedence
- D. Match cos
Answer: C
NEW QUESTION 12
Which of the following conclusions can be drawn from viewing the given output generated by the PING command-line utility?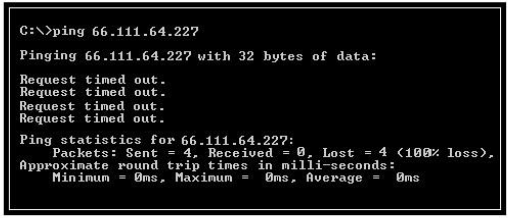
- A. The network bandwidth is heavily utilize
- B. The IP address of the destination computer is not resolve
- C. There is no connectivity between the source and the destination compute
- D. The hub is not workin
Answer: C
NEW QUESTION 13
Which of the following statements is NOT true about the file slack spaces in Windows operating system?
- A. File slack is the space, which exists between the end of the file and the end of the last clust e
- B. Large cluster size will decrease the volume of the file slac
- C. File slack may contain data from the memory of the syste
- D. It is possible to find user names, passwords, and other important information in slac
Answer: B
NEW QUESTION 14
Which of the following tools is used to detect wireless LANs using the 802.11b, 802.11a, and 802.11g WLAN standards on the Windows platform?
- A. Cain
- B. AiroPeek
- C. NetStumbler
- D. Snort
Answer: C
NEW QUESTION 15
Which of the following algorithms produces a digital signature which is used to authenticate the bit-stream images?
- A. MD6
- B. MD5
- C. BOINIC
- D. HashClash
Answer: B
NEW QUESTION 16
What is the size of a subnet in IPv6?
- A. 264 addresses
- B. 232 addresses
- C. 262 addresses
- D. 2128 addresses
Answer: A
NEW QUESTION 17
Which of the following tools allows an attacker to intentionally craft the packets to gain unauthorized access?
Each correct answer represents a complete solution. Choose two.
- A. Fragroute
- B. Ettercap
- C. Mendax
- D. Tcpdump
Answer: AC
NEW QUESTION 18
......
Thanks for reading the newest GCIA exam dumps! We recommend you to try the PREMIUM Dumps-hub.com GCIA dumps in VCE and PDF here: https://www.dumps-hub.com/GCIA-dumps.html (508 Q&As Dumps)
- Avant-garde GIAC Certified Incident Handler GCIH Exam Prep
- Validated GIAC GISF Practice Question Online
- Highest Quality GIAC GCIH Dump Online
- The Secret Of GIAC GSNA Training
- How Many Questions Of GCIA Exam Question
- Renew GIAC Certified Incident Handler GCIH Samples
- All About Download GCIH Preparation Labs
- Best Quality GIAC GSNA Free Demo Online
- Rebirth GIAC Certified Intrusion Analyst GCIA Free Practice Questions
- How Many Questions Of GISF Exam Prep

