GCIA Exam Questions - Online Test
GCIA Premium VCE File

150 Lectures, 20 Hours

High value of GCIA free practice questions materials and exam guide for GIAC certification for candidates, Real Success Guaranteed with Updated GCIA pdf dumps vce Materials. 100% PASS GIAC Certified Intrusion Analyst exam Today!
GIAC GCIA Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
John works as a Professional Ethical Hacker for NetPerfect Inc. The company has a Linux-based network. All client computers are running on Red Hat 7.0 Linux. The Sales Manager of the company complains to John that his system contains an unknown package named as tar.gz and his documents are exploited. To resolve the problem, John uses a Port scanner to enquire about the open ports and finds out that the HTTP server service port on 27374 is open. He suspects that the other computers on the network are also facing the same problem. John discovers that a malicious application is using the synscan tool to randomly generate IP addresses. Which of the following worms has attacked the computer?
- A. Ramen
- B. LoveLetter
- C. Code red
- D. Nimda
Answer: A
NEW QUESTION 2
Which of the following attacks is based on the concept that IDSs cannot recognize Unicode encoded malicious data?
- A. DoS attack
- B. Fragmentation overlap attack
- C. Obfuscating attack payload
- D. Polymorphic shell code attack
Answer: C
NEW QUESTION 3
Which of the following partitions contains the system files that are used to start the operating system?
- A. Secondary partition
- B. Boot partition
- C. Primary partition
- D. System partition
Answer: B
NEW QUESTION 4
Which of the following tools can be used to view active telnet sessions?
- A. Juggernaut
- B. Cgichk
- C. Nikto
- D. Hackbot
Answer: A
NEW QUESTION 5
You work as a Network Administrator for McRobert Inc. You want to know the NetBIOS name of your computer. Which of the following commands will you use?
- A. NETSTAT -n
- B. NETSTAT -s
- C. NBTSTAT -n
- D. NBTSTAT -s
Answer: C
NEW QUESTION 6
Adam works as a Security Administrator for Umbrella Inc. A project has been assigned to him to secure access to the network of the company from all possible entry points. He segmented the network into several subnets and installed firewalls all over the network. He has placed very stringent rules on all the firewalls, blocking everything in and out except ports that must be used.
He does need to have port 80 open since his company hosts a website that must be accessed from the Internet. Adam is still worried about programs like Hping2 that can get into a network through covert channels.
Which of the following is the most effective way to protect the network of the company from an attacker using Hping2 to scan his internal network?
- A. Block ICMP type 13 messages
- B. Block all outgoing traffic on port 21
- C. Block all outgoing traffic on port 53
- D. Block ICMP type 3 messages
Answer: A
NEW QUESTION 7
Which of the following ports is the default port for IMAP4 protocol?
- A. TCP port 143
- B. TCP port 25
- C. TCP port 443
- D. TCP port 80
Answer: A
NEW QUESTION 8
John works as a Network Security Administrator for NetPerfect Inc. The manager of the company has told John that the company's phone bill has increased drastically. John suspects that the company's phone system has been cracked by a malicious hacker. Which attack is used by malicious hackers to crack the phone system?
- A. War dialing
- B. Sequence++ attack
- C. Phreaking
- D. Man-in-the-middle attack
Answer: C
NEW QUESTION 9
The following output is generated by running the show ip route command:
RouterA#show ip route
< - - Output Omitted for brevity - -> 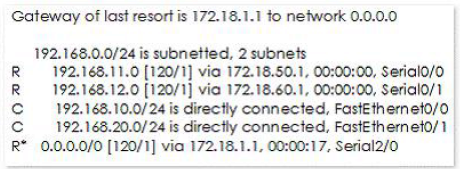
Which next hop address will RouterA use in forwarding traffic to 10.10.100.0/24?
- A. 172.18.50.1
- B. 192.168.10.0
- C. 172.18.1.1
- D. 172.18.60.1
Answer: C
NEW QUESTION 10
Mark works as the Network Administrator of a Windows 2000 based network. The network has a DNS server installed. He experiences host name resolution problems on the network. In order to rectify the situation, he wants to troubleshoot DNS name resolution problems on the network.
Which of the following tools will he use to do this?
- A. NSLOOKUP
- B. IPCONFIG
- C. NBTSTAT
- D. NETSTAT
Answer: A
NEW QUESTION 11
Which of the following are well-known ports?
Each correct answer represents a complete solution. Choose two.
- A. 443
- B. 21
- C. 1024
- D. 8080
Answer: AB
NEW QUESTION 12
Which of the following files in LILO booting process of Linux operating system stores the location of Kernel on the hard drive?
- A. /boot/boot.b
- B. /boot/map
- C. /sbin/lilo
- D. /etc/lilo.conf
Answer: B
NEW QUESTION 13
Which of the following DNS records is used for host name to IPv6 address resolution?
- A. PTR
- B. SOA
- C. A
- D. AAAA
- E. CNAME
Answer: D
NEW QUESTION 14
John works as a Security Administrator for NetPerfect Inc. The company uses Windows-based systems. A project has been assigned to John to track malicious hackers and to strengthen the company's security system. John configures a computer system to trick malicious hackers into thinking that it is the company's main server, which in fact is a decoy system to track hackers.
Which system is John using to track the malicious hackers?
- A. Honeypot
- B. Honeytokens
- C. Intrusion Detection System (IDS)
- D. Bastion host
Answer: A
NEW QUESTION 15
Which of the following is included in a memory dump file?
- A. List of loaded drivers
- B. Security ID
- C. Stop message and its parameters
- D. The kernel-mode call stack for the thread that stopped the process from execution
Answer: ACD
NEW QUESTION 16
In the DNS Zone transfer enumeration, an attacker attempts to retrieve a copy of the entire zone file for a domain from a DNS server. The information provided by the DNS zone can help an attacker gather user names, passwords, and other valuable information. To attempt a zone transfer, an attacker must be connected to a DNS server that is the authoritative server for that zone. Besides this, an attacker can launch a Denial of Service attack against the zone's DNS servers by flooding them with a lot of requests. Which of the following tools can an attacker use to perform a DNS zone transfer?
Each correct answer represents a complete solution. Choose all that apply.
- A. Dig
- B. Host
- C. NSLookup
- D. DSniff
Answer: ABC
NEW QUESTION 17
You work as a Network Administrator for McRobert Inc. Your company has a Windows NT 4.0 TCP/IP-based network. You want to list the cache of NetBIOS names and IP addresses. Which of the following utilities will you use?
- A. TELNET
- B. NBTSTAT
- C. TRACERT
- D. NETSTAT
Answer: B
NEW QUESTION 18
......
P.S. Allfreedumps.com now are offering 100% pass ensure GCIA dumps! All GCIA exam questions have been updated with correct answers: https://www.allfreedumps.com/GCIA-dumps.html (508 New Questions)
- Highest Quality GIAC GCIH Dump Online
- A Review Of Guaranteed GCIH Pdf Exam
- Top Tips Of Rebirth GSNA Exam Question
- The Secret Of GIAC GSEC Exam Prep
- How Many Questions Of GSNA Braindumps
- Avant-garde GIAC Certified Incident Handler GCIH Exam Prep
- How Many Questions Of GISF Exam Prep
- All About Download GCIH Preparation Labs
- Best Quality GIAC GSNA Free Demo Online
- All About Download GCIA Exam Guide

