GSEC Exam Questions - Online Test
GSEC Premium VCE File

150 Lectures, 20 Hours

It is more faster and easier to pass the GIAC GSEC exam by using Download GIAC GIAC Security Essentials Certification questuins and answers. Immediate access to the Most recent GSEC Exam and find the same core area GSEC questions with professionally verified answers, then PASS your exam with a high score now.
GIAC GSEC Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Which of the following is an advantage of private circuits versus VPNs?
- A. Flexibility
- B. Performance guarantees
- C. Cost
- D. Time required to implement
Answer: B
NEW QUESTION 2
When should you create the initial database for a Linux file integrity checker?
- A. Before a system is patched
- B. After a system has been compromised
- C. Before a system has been compromised
- D. During an attack
Answer: C
NEW QUESTION 3
You work as a Network Administrator for McNeil Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest domain-based network. The company's management has decided to provide laptops to its sales team members. These laptops are equipped with smart card readers. The laptops will be configured as wireless network clients. You are required to accomplish the following tasks:
The wireless network communication should be secured.
The laptop users should be able to use smart cards for getting authenticated. In order to accomplish the tasks, you take the following steps:
Configure 802.1x and WEP for the wireless connections. Configure the PEAP-MS-CHAP v2 protocol for authentication. What will happen after you have taken these steps?
- A. The laptop users will be able to use smart cards for getting authenticate
- B. Both tasks will be accomplishe
- C. None of the tasks will be accomplishe
- D. The wireless network communication will be secure
Answer: D
NEW QUESTION 4
Which common firewall feature can be utilized to generate a forensic trail of evidence and
to identify attack trends against your network?
- A. NAT
- B. State Table
- C. Logging
- D. Content filtering
Answer: C
NEW QUESTION 5
You work as a Network Administrator for Net World Inc. The company has a Linux-based network. You are optimizing performance and security on your Web server. You want to know the ports that are listening to FTP. Which of the following commands will you use?
- A. netstat -a | grep FTP
- B. FTP netstat -r
- C. FTP netstat -a
- D. netstat -r | grep FTP
Answer: A
NEW QUESTION 6
During which of the following steps is the public/private key-pair generated for Public Key Infrastructure (PKI)?
- A. Key Recovery
- B. Initialization
- C. Registration
- D. Certification
Answer: B
NEW QUESTION 7
A new data center is being built where customer credit information will be processed and stored. Which of the following actions will help maintain the confidentiality of the data?
- A. Environmental sensors in the server room
- B. Access control system for physical building
- C. Automated fire detection and control systems
- D. Frequent off-site backup of critical databases
Answer: B
NEW QUESTION 8
What type of attack can be performed against a wireless network using the tool Kismet?
- A. IP spoofing
- B. Eavesdropping
- C. Masquerading
- D. Denial of Service
Answer: B
NEW QUESTION 9
Which of the following choices accurately describes how PGP works when encrypting email?
- A. PGP encrypts the message with the recipients public key, then encrypts this key with a random asymmetric ke
- B. PGP creates a random asymmetric key that it uses to encrypt the message, then encrypts this key with the recipient's public key
- C. PGP creates a random symmetric key that it uses to encrypt the message, then encrypts this key with the recipient's public key
- D. PGP encrypts the message with the recipients public key, then encrypts this key with a random symmetric ke
Answer: B
NEW QUESTION 10
Which of the following is the FIRST step in performing an Operational Security (OP5EC) Vulnerabilities Assessment?
- A. Assess the threat
- B. Assess vulnerabilities of critical information to the threat
- C. Conduct risk versus benefit analysis
- D. Implement appropriate countermeasures
- E. Identification of critical information
Answer: E
NEW QUESTION 11
When are Group Policy Objects (GPOs) NOT applied automatically to workstations?
- A. At 90-minute intervals
- B. At logon
- C. Every time Windows Explorer is launched
- D. At boot-up
Answer: C
NEW QUESTION 12
What are the two actions the receiver of a PGP email message can perform that allows establishment of trust between sender and receiver?
- A. Decode the message by decrypting the asymmetric key with his private key, then using the asymmetric key to decrypt the messag
- B. Decode the message by decrypting the symmetric key with his private key, then using the symmetric key to decrypt the messag
- C. Decode the message by decrypting the symmetric key with his public key, then using the symmetric key to decrypt the messag
- D. Decrypt the message by encrypting the digital signature with his private key, then using the digital signature to decrypt the messag
Answer: A
NEW QUESTION 13
One of your Linux systems was compromised last night. According to change management history and a recent vulnerability scan, the system's patches were up-to-date at the time of the attack. Which of the following statements is the Most Likely explanation?
- A. It was a zero-day exploi
- B. It was a Trojan Horse exploi
- C. It was a worm exploi
- D. It was a man-in-middle exploi
Answer: A
NEW QUESTION 14
What does an attacker need to consider when attempting an IP spoofing attack that relies on guessing Initial Sequence Numbers (ISNs)?
- A. These attacks work against relatively idle server
- B. These attacks rely on a modified TCP/IP stack to functio
- C. These attacks can be easily traced back to the sourc
- D. These attacks only work against Linux/Unix host
Answer: A
NEW QUESTION 15
Included below is the output from a resource kit utility run against local host.
Which command could have produced this output? 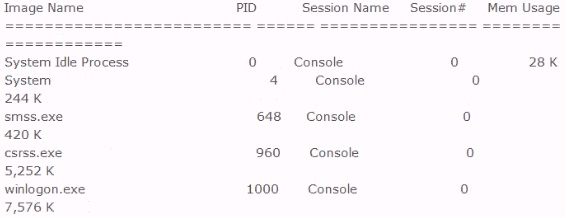
- A. Schtasks
- B. Task kill
- C. SC
- D. Task list
Answer: D
NEW QUESTION 16
You are doing some analysis of malware on a Unix computer in a closed test network. The IP address of the computer is 192.168.1.120. From a packet capture, you see the malware is attempting to do a DNS query for a server called iamabadserver.com so that it can connect to it. There is no DNS server on the test network to do name resolution. You have another computer, whose IP is 192.168.1.115, available on the test network that you would like for the malware connect to it instead. How do you get the malware to connect to that computer on the test network?
- A. You modify the HOSTS file on the computer you want the malware to connect to and add an entry that reads: 192.168.1.120 iamabadserver iamabadserver.com
- B. You modify the HOSTS file on the Unix computer your malware is running on and add an entry that reads: 192.168.1.115 iamabadserveriamabadserver.com
- C. You modify the HOSTS file on the Unix computer your malware is running on and add an entry that reads: 192.168.1.120 iamabadserver iamabadserver.com
- D. You modify the HOSTS file on the computer you want the malware to connect to and add an entry that reads: 192.168.1.115 iamabadserver iamabadserver.com
Answer: B
NEW QUESTION 17
You have been hired to design a TCP/IP-based network that will contain both Unix and Windows computers. You are planning a name resolution strategy. Which of the following services will best suit the requirements of the network?
- A. APIPA
- B. LMHOSTS
- C. DNS
- D. DHCP
- E. WINS
Answer: C
NEW QUESTION 18
In order to capture traffic for analysis, Network Intrusion Detection Systems (NIDS) operate with network cards in what mode?
- A. Discrete
- B. Reporting
- C. Promiscuous
- D. Alert
Answer: C
NEW QUESTION 19
Which of the following statements about Network Address Translation (NAT) are true? Each correct answer represents a complete solution. Choose two.
- A. It reduces the need for globally unique IP addresse
- B. It allows external network clients access to internal service
- C. It allows the computers in a private network to share a global, ISP assigned address to connect to the Interne
- D. It provides added security by using Internet access to deny or permit certain traffic from the Bastion Hos
Answer: AC
NEW QUESTION 20
......
P.S. Easily pass GSEC Exam with 279 Q&As DumpSolutions.com Dumps & pdf Version, Welcome to Download the Newest DumpSolutions.com GSEC Dumps: https://www.dumpsolutions.com/GSEC-dumps/ (279 New Questions)
- Rebirth GIAC Certified Intrusion Analyst GCIA Free Practice Questions
- Validated GIAC GISF Practice Question Online
- Highest Quality GIAC GCIH Dump Online
- What 100% Guarantee GSEC Practice Question Is
- Avant-garde GIAC Certified Incident Handler GCIH Exam Prep
- Leading GIAC Systems And Network Auditor GSNA Braindumps
- How Many Questions Of GSNA Braindumps
- The Secret Of GIAC GISF Dump
- How Many Questions Of GCIA Exam Question
- Best Quality GIAC GSNA Free Demo Online

